Playlist
To watch a webinar recording you need to log in or create an account, if you don't have one yet.
Show more
582 videos in this playlist

Webinar Recording
Data Governance Is So Much More Than Good Housekeeping
Apr 25, 2024
In today’s data driven and AI generated world making sense of the data will do so much more than keep the auditors at bay. It could transform your business and this webinar will tell you how!

Webinar Recording
Road to EIC 2024: Generative AI
Apr 18, 2024
Prepare to unlock the transformative power of Generative AI in our preparatory webinar for the "Constructing the Future" bootcamp. This essential primer is designed to equip you with the foundational knowledge necessary for a profound understanding and engagement in our intensive 4-hour workshop.

Webinar Recording
The Right Foundation for Your Identity Fabric
Apr 16, 2024
In this webinar, Martin Kuppinger, Principal Analyst at KuppingerCole Analysts, will look at the status and future of Identity Fabrics, on what to consider when defining the own approach for an Identity Fabric, and how the vendor landscape looks like. He will discuss different approaches, from unified solutions to integrating / orchestrating different best-of-breed solutions. He also will look at the best approach for defining your own Identity Fabric.

Webinar Recording
Revolutionizing Secure PC Fleet Management
Apr 12, 2024
Many organizations are battling with effectively managing their PC fleet. These challenges range from hybrid work, temporary staff, and edge computing, especially when it comes to topics like data security and asset management. HP has come up with a way to overcome these challenges through Protect and Trace with Wolf Connect. Connect integrated into their E2E Security and Fleet Management Stack.
Webinar Recording
Navigating Security Silos: Identity as a New Security Perimeter
Apr 10, 2024
Companies are grappling with countless challenges in the realm of identity security. These challenges range from dealing with the dynamic nature of identities, the rise of insider threats, the ever-evolving threat landscapes, handling the complexity of identity ecosystems to insufficient visibility into identity posture. This webinar explores the fundamental role of Identity Threat Detection & Response (ITDR) and Identity Security Posture Management in fortifying defenses against these challenges.

Webinar Recording
Modern IAM builds on Policy Based Access
Apr 05, 2024
In this webinar, Martin Kuppinger, Principal Analyst at KuppingerCole Analysts, will look at the status and future of PBAM and the various types of solutions that are available in the market. He will look at the overall ratings for this market segment and provide concrete recommendations on how to best select the vendor, but also will discuss strategic approaches for PBAM.

Webinar Recording
Road to EIC: Leveraging Reusable Identities in Your Organization
Apr 04, 2024
In the realm of customer onboarding, the prevailing challenges are manifold. Traditional methods entail redundant data collection and authentication hurdles, contributing to inefficiencies and frustrations for both customers and businesses. Moreover, siloed systems exacerbate the issue, leading to fragmented user experiences that impede smooth onboarding processes and hinder operational agility.

Webinar Recording
Navigating Identity Security: Integrating SAP Into an Identity Fabric
Mar 27, 2024
SAP customers are shifting away from SAP Identity Management (IDM), which will no longer be supported after 2027, as they are adopting newer SAP solutions. They need to find effective ways of dealing with the technical challenges, while at the same time ensuring secure access control and management of digital identities.
Join identity and security experts from KuppingerCole Analysts, One Identity, and SAP as they discuss the significance of and key considerations for integrating and complementing the SAP identity security model across various SAP solutions, including SAP Identity...

Webinar Recording
IAM Meets Data Management: A Recipe for Peak Performance
Mar 22, 2024
In today's competitive landscape, organizations need to unlock the full potential of their data by ensuring the data management and identity and access Management (IAM) are tightly linked. However, this can be challenging due to factors such as disconnected data, inadequate tooling, and concerns about security and compliance risks. An integrated approach is essential.
Join experts from KuppingerCole Analysts and IndyKite to explore real-world challenges and solutions, including the integration of data management and IAM. Discover how organizations can overcome obstacles to harnessing the...

Webinar Recording
Road to EIC: eIDAS 2.0 – The Way to "Trusted, Voluntary, and User-Controlled" Digital Identity
Mar 21, 2024
The regulation on electronic identification and trust services (eIDAS) is designed to increase trust and security in electronic transactions within the EU's internal market. One of eIDAS’ aims is to make it possible for individuals and businesses to use their own national e-Identification systems to access public services in other EU countries. EIDAS 2.o focuses on expanding the availability and usage of digital wallets, whereby member states provide citizens with secure and privacy-preserving digital wallets to manage digital credentials, aiming for 80% EU resident adoption by 2030.

Webinar Recording
Decentralized Identity – a Key to Reusing Identity for Improved Security and User Experiences
Mar 15, 2024
Decentralized identity has earned a place in identity management for its capacity to increase privacy and security, while improving the user experience. It is fundamental to creating a reusable verified identity which enables numerous use cases such as reusable KYC, proof of employment, remote onboarding and passwordless authentication.

Webinar Recording
Unlocking Zero Trust Network Access
Mar 14, 2024
Zero Trust Network Access (ZTNA) is becoming increasingly essential as organizations adapt to remote work, cloud adoption, and the growing sophistication of cyber threats. As a result, ZTNA solutions play a critical role in today's cybersecurity landscape by providing a holistic approach to secure access to business applications and resources regardless of user location. These solutions fundamentally align with the principles of Zero Trust, extending its influence across devices, networks, systems, applications, and data. This webinar provides a comprehensive overview of ZTNA solutions,...

Webinar Recording
Mastering CIAM: Advanced Techniques for Designing a Resilient CIAM Program
Mar 13, 2024
In today's digital landscape, mastering CIAM is crucial for IT professionals. Challenges like imperfect client touchpoints, high abandonment rates, and limited system insights hinder best practices. Join us to explore and overcome these hurdles, enhancing user experiences through strategic CIAM implementation.
Explore advanced CIAM techniques in our webinar. From implementing best practices to deploying APIs for user insights, discover strategies to reduce abandonment rates. Unlock techniques for enhancing end-user engagement and revenue, supported by real-world testimonials. Learn to...

Webinar Recording
Proactive Cyber Defense with Intelligent SIEM Platforms
Mar 08, 2024
Security information and event management (SIEM) solutions have dominated the enterprise security market for nearly two decades, but due to high operating costs, a shortage of skilled security experts, and the rapid pace of change in the business IT and cyber threat environments, traditional SIEMs are no longer effective. A new generation of SIEMs has emerged.

Webinar Recording
Road to EIC: Exploring the Power of Decentralized Identity Solutions
Mar 07, 2024
Decentralized Identity is pivotal in the digital era, offering a secure, privacy-centric identity solution. In contrast to traditional systems, which are centralized and prone to breaches, Decentralized Identity is built on blockchain technology. With Decentralized Identity, users have control over their data, reducing the risk of identity theft. Interoperability is enhanced, enabling secure authentication across platforms without a central authority. Decentralized Identity aligns with privacy regulations like the EU’s GDPR, emphasizing user consent and data control in a self-sovereign...

Webinar Recording
Supercharge Your Business with Cloud-Based Data Modernization
Mar 06, 2024
Data modernization is critical for businesses to remain competitive in today’s data-driven world, and while the cloud is an important enabler of data modernization, migrating sensitive data to the cloud is challenging. However, it is possible, with the right approach.

Webinar Recording
Cloud Alphabet Soup - CNAPP
Mar 01, 2024
Organizations are using cloud services to develop and deploy new and existing applications. However, the responsibilities for security and compliance are shared between the CSP (Cloud Service Providers) and the cloud customer. The cloud user is responsible for implementing controls to meet their security and compliance obligations.

Webinar Recording
The Rise of Identity as a Service (IDaaS) as the Cornerstone of Modern Cybersecurity
Feb 23, 2024
Cybersecurity professionals face similar challenges. They must safeguard their organizations against the escalating sophistication of cyber threats and attack vectors, while at the same time administering and securing identities in the context of a dispersed and remote workforce. They strive to strike a balance between stringent security measures and a seamless end-user experience. Furthermore, compliance with regulatory requirements and industry standards for data protection and privacy poses a critical concern, as does the management of identities across an expanding array of applications...

Webinar Recording
Road to EIC: What’s Next in Digital Identity Standards?
Feb 22, 2024
As the digital realm evolves rapidly, the importance of robust and secure identity verification mechanisms becomes paramount. Standards in digital identity help establish secure authentication methods and protocols to safeguard user information by offering frameworks that respect individual privacy rights, while still enabling effective identity verification. In an era dominated by online interactions and transactions, the significance of digital identity standards cannot be overstated. In this “Road to EIC” virtual fireside chat we explore the current state of digital identity standards...

Webinar Recording
Zero Trust Unveiled: Securing Critical Data in SAP, CAD, and PLM Systems
Feb 02, 2024
In an era of escalating cyber threats, securing critical and commercially sensitive data becomes paramount. Join us for an informative webinar exploring the challenges posed by sophisticated cyber threats and the complexities introduced by the shift to remote working.
Discover the heightened risks in sharing and storing SAP, computer-aided design (CAD), and product lifecycle management (PLM) data and learn why zero trust is essential for compliance with regulations like GDPR, NIS2, ISO27001, and CMMC 2.0.

Webinar Recording
The Impact of Expanding Attack Surfaces on Enterprise Cybersecurity and Why You Need a Strong IAM Posture
Jan 31, 2024
Enterprise attack surfaces are constantly evolving and expanding due to the integration of cloud-based infrastructure, interconnected devices, and third-party solutions. New vulnerabilities are skillfully exploited by proactive cybercriminals every day. In this context, a strong Identity and Access Management (IAM) posture is vital to manage risks. However, maintaining this IAM strategy can be a complex task given the multitude of requirements and tools involved.

Webinar Recording
Beyond Secrets Management: Transforming Security in the Digital Age
Jan 26, 2024
In the ever-expanding digital landscape, the proliferation of secrets and cryptographic keys poses a risk and a challenge, with many organizations struggling to maintain control. Relying on secrets management is no longer sufficient. A new comprehensive approach is needed, with more than 40% of data breaches involving stolen credentials.
Join security and identity experts from KuppingerCole Analysts and Entrust to reveal the intrinsic and symbiotic relationship between key management and secrets, offering visibility, compliance assurance, and effective risk management. Learn the...

Webinar Recording
SAP IDM End of Life: Die IGA-Migration souverän meistern
Jan 19, 2024
Die Abkündigung von SAP Identity Management (SAP IDM) stellt Unternehmen vor eine kritische Herausforderung. Die bisherige Lösung erreicht das Ende ihres Lebenszyklus, und Organisationen müssen sich nun die Frage stellen: Wie kann trotzdem weiterhin Compliance aufrechterhalten werden? Die Gewährleistung der Identitätsverwaltung unter Berücksichtigung der gesetzlichen Bestimmungen entwickelt sich zu einem zentralen Anliegen für Fachleute im Bereich Informationstechnologie.
In diesem Kontext suchen Unternehmen nach effektiven Wegen, um die bisherigen Ansätze und Verfahren aus dem SAP...

Webinar Recording
Sicherung Ihrer digitalen Grenze: Navigieren durch die sich ständig weiterentwickelnde Bedrohungslandschaft
Jan 17, 2024
In einer Zeit, in der die digitale Transformation die Art und Weise, wie wir Geschäfte machen, revolutioniert, ist die Sicherung der digitalen Grenzen Ihres Unternehmens von größter Bedeutung. Die Bedrohungen entwickeln sich ständig weiter.
Nehmen Sie mit Sicherheitsexperten von KuppingerCole Analysts und Palo Alto Networks an einem aufschlussreichen und spannenden Webinar teil, das sich mit der dynamischen Welt des Angriffsflächen- und Bedrohungsmanagements befasst. Sie werden die Herausforderungen erörtern, mit denen Organisationen aller Größenordnungen - von kleinen Unternehmen bis...

Webinar Recording
Securing Your Digital Frontier: Navigating the Ever-Evolving Threat Landscape
Jan 12, 2024
In an era where digital transformation is revolutionizing the way we do business, securing your organization's digital frontier is paramount. Threats are constantly evolving

Webinar Recording
IGA and LoB Application Access Management: What We’ll See in 2024
Dec 15, 2023
IGA (Identity Governance & Administration) is changing. We see functional changes and enhancements such as embedded AI/ML features including the use of generative AI, as well as increasingly integration with Application Access Management. The latter is about solutions that manage access to LoB (Line of Business Applications) such as SAP, Oracle eBusiness Suite, JD Edwards, Salesforce, SuccessFactors, and many others in depth. They help in enforcing the least privilege principle, managing correct implementation and execution of SoD (Segregation of Duties) controls, managing critical...

Webinar Recording
Become Cybersecurity Proactive With Attack Surface Management
Dec 14, 2023
The cyber threat landscape that organizations face today continues to evolve at an alarming pace, making it difficult for cyber defenders to stay a step ahead of adversaries. Attack surface management (ASM) enables proactive cybersecurity strategies, but understanding the discipline and choosing the right solution can be challenging.
With the expansion of the attack surface due to the adoption of cloud-based and mobile computing, all organizations need to understand where and how they are exposed to cyberattacks. Therefore, adoption a proactive cybersecurity capability and choosing the...

Webinar Recording
Modernizing IGA: A Guide for IAM Leaders
Dec 13, 2023
Modern CISOs are typically agents of change, but many are discovering that modernizing the governance of identities is not something that can be achieved by IT alone because it impacts so much of the business. A different approach is needed to introduce modern identity governance and administration (IGA) capabilities.

Webinar Recording
Mastering Global IAM for Cybersecurity Excellence: From Zero Trust Principles to Identity Threat Detection & Response (ITDR)
Dec 08, 2023
In today's interconnected global landscape, the role of Identity and Access Management (IAM) has never been more crucial in shaping cybersecurity strategies. As businesses expand across borders, the demand for robust authentication and authorization mechanisms is at an all-time high. Join us in this insightful webinar as we delve into the world of global IAM, exploring key concepts, challenges, and solutions that will empower you to take your cybersecurity to the next level.

Webinar Recording
Navigating the Future of API Security: Trends, Challenges, and Innovations
Dec 07, 2023
Today, APIs can be found everywhere — at home and in mobile devices, in corporate networks and in the cloud, even in industrial environments. The emerging era of Generative AI is also entirely dependent on APIs to implement integrations with existing business applications. They are now powering the logistics of delivering digital products to partners and customers.
In this webinar, we delve into the realm of API security and management, exploring the rapid evolution from technical tools to the backbone of digital business. Discover the growing challenges in safeguarding APIs, the rise of...
Webinar Recording
Navigating the Access Control Maze
Dec 06, 2023
This KuppingerCole webinar offers a comprehensive exploration of access control challenges, the limitations of traditional RBAC and PBAC, some innovative policy-driven solutions, a demonstration of policy-driven RBAC in MidPoint, and actionable insights for enhancing access control strategies.

Webinar Recording
Supercharge Your Access Control Capabilities With a New Approach
Dec 01, 2023
Are you ready to revolutionize your understanding of Access Control? We invite you to a game-changing webinar that will illuminate the vital distinctions between policy-based, attribute-based, and role-based access control – the three pillars of modern access control. Prepare to embark on a journey that will empower you to secure your digital universe like never before!
Join experts from KuppingerCole Analysts and Tuebora as they discuss how to make sense of the different approaches to access to control, the pros and cons of each, and how to make good decisions about managing access...
Webinar Recording
The Anatomy of Insider Threats: Understanding the Risks in Financial Institutions
Nov 30, 2023
In the high-stakes world of financial institutions, safeguarding sensitive data is paramount. The enemy, however, may lurk within. Join us for an eye-opening webinar as we delve deep into the world of insider threats, their definitions, types, and most importantly, how to protect your institution from them.
Discover the anatomy of insider threats specific to financial institutions. Understand what constitutes an insider threat, and gain insights into the different personas that pose a risk. Explore the real-world impact of insider threats on financial institutions through riveting...
Webinar Recording
Are You Prepared for the True AD Disaster?
Nov 24, 2023
Have you ever experienced a major IT outage caused by issues with directory services such as Microsoft Active Directory? If not, you surely have heard about others that came into trouble here. Directory Services, with the Microsoft Active Directory still forming an essential part of the IT backbone in about 90% of medium-sized to large organizations, are critical for a working IT. If they fail, authentication fails (or, at best, stumbles). If data gets “corrupted”, this even can lead to the propagation of erroneous changes to other systems. SAP systems not working anymore because mass...

Webinar Recording
A Foundational Data Layer: The Key to Value in Identity
Nov 08, 2023
The world’s largest tech companies have been born under a simple notion: “content is king.” Google, Apple, Netflix, Oracle, and many others have labored under this primary notation to capture as much of the world’s content into their services. But identity data differs from any other kind of content, which makes handling it properly challenging, even for global services.
What are the emerging services that will become the titans of identity data? This webinar will explore this question in depth with the latest company from ForgeRock founder Lasse Andresen, IndyKite, which aims to make...

Webinar Recording
The Future of Identity Security: PAM+CIEM+ITDR
Nov 03, 2023
Digital transformation is creating huge opportunities for business, but it is also introducing new vulnerabilities that can be exploited by cyber attackers by massively and rapidly expanding the potential attack surface of organizations embracing new technologies.

Webinar Recording
Achieving Security and Compliance Across Hybrid Multi-Cloud Environments
Nov 01, 2023
Most enterprises have a multi-cloud strategy for strong operational resiliency, minimizing concentration risk, and containing overall IT security and compliance risk. But governance and compliance remain a top challenge. Finding a way to manage risk and compliance is essential.

Webinar Recording
Passwordless Authentication: What, Why, and How
Oct 27, 2023
Passwords are quickly and easily compromised, they are costly and difficult to manage, and they result in poor user experiences. Many organizations are looking for alternatives, but find it challenging to identify appropriate passwordless authentication solutions that are secure, cost-effective, and user-friendly.
Webinar Recording
Cloud Security Early Warning Systems: From CSPM to CNAPP
Oct 20, 2023
Cloud computing delivers the benefits of accelerated development without the hardware costs. But the dynamic nature of cloud services and the proprietary security features offered by different cloud service providers make it challenging for customers to manage the risks and to be sure they are meeting security and compliance obligations. Most organizations need some form of guardrails.

Webinar Recording
The Evolution of Secure Access in Critical Infrastructure
Oct 13, 2023
Cyberattacks are putting increased pressure on all organizations, especially those running operational technology (OT), industrial control systems (ICS), and critical infrastructure systems (CIS) with high availability requirements. Secure remote access (SRA) for the maintenance of such systems is critical, but challenging.

Webinar Recording
Innovation Never Rests - a New SOC Blueprint for Tomorrow's Threats
Sep 29, 2023
The traditional approach to building a security operations center (SOC) is no longer valid or able to keep up with the rate of change in business IT environments and in the cyber threat landscape. A new approach using the latest technologies is required.

Webinar Recording
Harness IGA and GRC Synergies for Effective ID Management and Access Control
Sep 22, 2023
In today's dynamic business landscape, organizations face mounting challenges in managing identity and access risks, while at the same time complying with a growing number of industry sector, national, regional, and international regulations. An integrated approach is essential.

Webinar Recording
Digital Transformation in Financial Services Using Biometrics
Sep 20, 2023
High-value, high-risk transactions that used to be in-person only, have moved online as part of the accelerated digital transformation of financial services providers in the wake of the pandemic. But delivering high levels of identity verification is challenging, leading to the adoption of new methods.

Webinar Recording
Perfecting Privileged Access Management (PAM)
Sep 15, 2023
Stolen credentials provide a popular and easy route for attackers into any organization, so protecting them is crucial. But protecting credentials for every device, application, and system, while at the same time making it easy for people to access the resources they need, is extremely challenging.

Webinar Recording
Unleashing the Power of Modernized Authorization
Sep 13, 2023
As businesses become more reliant on IT and undergo digital transformation in pursuit of greater productivity and efficiency, securing digital assets has never been more critical or more challenging.
However, traditional role-based (RBAC) and attribute-based (ABAC) access controls are failing to meet modern security and business needs. Another approach is needed.

Webinar Recording
Beyond Just SAP: The Need for Cross-LoB Access Controls
Sep 07, 2023
The market for solutions that support in application access control, application risk management, and SoD (Segregation of Duties) management in a heterogeneous LoB (Line of Business) applications landscape is changing. Most organizations already have a hybrid, multi-vendor LoB landscape, consisting of solutions ranging from SAP ECC to SAP S/4HANA, SAP SaaS applications, and other vendors’ (Oracle, Salesforce, Workday,…) LoB applications.

Webinar Recording
Schon perfekt vorbereitet für NIS2? Wenn nicht: warum Identity Governance so wichtig ist
Sep 06, 2023
Bis Oktober 2024 müssen die EU-Mitgliedsstaaten die Network-and-Information-Security-Richtlinie 2.0 (NIS2-Richtlinie) in geltendes Landesrecht umsetzen, deren Ziel es ist, EU-weit ein hohes gemeinsames Level an Cybersecurity zu gewährleisten. In Deutschland wurde hierzu bereits im Mai ein Referentenentwurf des Innenministeriums vorgelegt. Demnach könnten bereits Unternehmen ab 50 Beschäftigten umsetzungspflichtig werden.

Webinar Recording
Using Data Security Platforms in a Modern, Hybrid World
Aug 18, 2023
Data is the lifeblood of any modern business organization. It is therefore critical to maintain data security and integrity by protecting it appropriately depending on what the data is, what it is used for, who is accessing it, and how it is used. But implementing consistent and comprehensive data protection across an enterprise, on premises and in the cloud, can be challenging.

Webinar Recording
Fight Fraud With Fraud Reduction Intelligence Platforms (FRIP)
Aug 16, 2023
In today's digital landscape, businesses face an increasing threat of fraud that can lead to significant financial losses and damage to their reputation. To effectively combat fraud, businesses need Fraud Reduction Intelligence Platforms (FRIPs). These advanced technologies leverage multiple data sources, data analytics, and ML detection models to proactively detect and prevent fraudulent activities in real-time. FRIPs empower organizations to stay ahead of fraudsters by uncovering hidden patterns, identifying anomalies, and generating alerts. By implementing FRIPs, businesses can mitigate...

Webinar Recording
IGA Essentials: Embracing Trends and Amplifying Core Capabilities
Aug 11, 2023
The market for Identity Governance and Administration (IGA) is undergoing further development with the incorporation of more integrated solutions for Identity Lifecycle Management and Access Governance, which are now being enhanced by intelligent features. However, organizations still face the challenge of understanding the key functions to consider when choosing an IGA solution. Join KuppingerCole Analysts in this webinar to gain insights into the fundamental functionalities of an IGA (Identity Governance and Administration) solution. Additionally, learn about the prevailing market trends...

Webinar Recording
Shut the Door to Cyber Attackers Permanently
Jul 26, 2023
Stolen credentials are one of the easiest and most popular way for cyber criminals to gain access to targeted IT systems, but longer and stronger passwords together with first-generation multi-factor authentication (MFA) have failed to make a difference. Fortunately, there is a more effective way.

Webinar Recording
Identity Assurance Using Biometrics
Jul 21, 2023
Access controls all too often rely on things such as passwords, security questions, and physical tokens that can be shared or stolen, making such systems vulnerable to abuse. However, security can be improved by using biometrics that measure the physical and behavioral characteristics of the person seeking to gain access to something.

Webinar Recording
Effective Application Access Controls in the Modern Business IT Landscape
Jul 19, 2023
As business reliance on IT increases, so does the number of critical applications in use. Controlling access to those applications is essential, but challenging to do with traditional IGA and IAM systems in today’s hybrid, heterogenous and multi-cloud business IT environments. Organizations need a more flexible and scalable approach to application access management.

Webinar Recording
Ensuring a Proper Fit: Trends in CIAM and Strategies for Effective Solution Selection
Jun 30, 2023
KuppingerCole would like to invite you to an upcoming webinar on Consumer Identity and Access Management (CIAM). Join us for an enlightening session where we will delve into the world of CIAM, exploring its significance in today's digital landscape and the best practices to ensure a seamless user experience while safeguarding consumer data.

Webinar Recording
Simplify Identity Management With User Centric Personas and PBAC
Jun 23, 2023
As customers, employees, partners, suppliers, and other parties become increasingly intertwined, companies face the challenge of managing access for multiple overlapping identities, leading to complexity on the backend, security and compliance risks, and suboptimal user experiences. But Role-Based and Attribute-Based Access Controls are failing to deliver. Another approach is needed.

Webinar Recording
Delivering True B2B Identity Management in the Modern Era
Jun 21, 2023
In today’s digital-first world, managing the identities of a large number of different business partners remains a challenge for many organizations against a backdrop of ever-increasing cyber risks. A new approach is needed to address modern B2B and B2B2C IAM use cases.

Webinar Recording
Achieve Effective Risk and Vulnerability Management With a Platform Approach
Jun 16, 2023
Effective cyber security is essentially about identifying and remediating vulnerabilities across the entire IT estate quickly to reduce the risk of cyber attack and data loss. However, a proliferation of disparate tools often makes this difficult to achieve. Companies need to find a better approach.

Webinar Recording
3rd Party Identity Risk – Der Feind Im Eigenen Haus (?)
Jun 14, 2023
Unternehmen verwalten heute eine Vielzahl von Identitäten, die über die eigene Belegschaft hinausgehen. Auftragnehmer, Partner, Saisonarbeiter, Lieferanten und sogar nicht-menschliche Mitarbeiter wie RPAs (Robotic Process Automation) und Servicekonten machen einen großen Prozentsatz der Identitäten vieler moderner Unternehmen aus. Das Management dieser Identitäten und des Zugriffs, den sie erhalten, ist komplex, und es ist wichtig, sie unter Kontrolle zu behalten.

Webinar Recording
Why Network Detection & Response (NDR) Is Central to Modern Cyber Architecture
May 26, 2023
Cybercriminals are constantly refining their attack techniques, which renders traditional and static security approaches insufficient to detect cyber incidents. Therefore, organizations must adopt more dynamic and adaptive strategies to identify and respond to novel attack attempts across their networks.

Webinar Recording
Speeding Up Zero Trust Delivery Using Managed Services
May 24, 2023
The attack surface of business IT is expanding rapidly, demanding a modern approach to cybersecurity. Many organizations seek to achieve this by adopting a Zero Trust security model or signing up to managed services for Identity & Access Management (IAM). While both these approaches are effective, they are also extremely complementary, but tackling both at the same time can be as challenging as it is rewarding.

Webinar Recording
Optimize Security With Security Orchestration, Automation, & Response
May 05, 2023
Business IT environments are getting increasing complex and cyber criminals are rapidly adapting to exploit the growing attack surface. While most organizations have invested in security controls, many are struggling to respond quickly and efficiently to attacks. Finding the right solution to coordinate and automate incident response and forensic analysis is crucial.

Webinar Recording
Maximizing Cyber Security Investments in Economically Turbulent Times
Apr 28, 2023
Mitigating digital risk and protecting your organizations from cyber attacks and data breaches is all the more challenging with shrinking IT budgets in a volatile economic environment. The ability to communicate technology and cyber risk and map that against direct and indirect business impact is key.

Webinar Recording
Phishing-Resistant MFA: The Next Evolution for Strong Authentication
Apr 26, 2023
Using stolen credentials is one of the most popular and effective ways for cyber-attacks to infiltrate the IT systems of targeted organizations. Most cybersecurity teams are implementing multi-factor authentication (MFA), but not all MFA systems are created equal or implemented effectively, leaving organizations vulnerable to attack.
Webinar Recording
Take Invisible MFA to the Next Level With Passwordless Continuous Authentication
Apr 21, 2023
Credential theft is the top enabler of cybercrime. In response, many organizations are turning to multifactor authentication (MFA), but not all MFA solutions are hacker resistant. Some approaches are more effective than others, but finding the right approach can be challenging.

Webinar Recording
Welcome to the Pamocracy!
Apr 19, 2023
As the business world embraces cloud, continuous infrastructure development and a revolution in software procurement and deployment, what was once confined to the few is now open to many. We are talking of course about privileged access which has spread from traditional IT roles into the embrace of regular employees, third party users and millions and millions of non-human identities!

Webinar Recording
The Business Value of Cloud-Based Identity Security
Mar 31, 2023
Identity Governance and Administration (IGA) is crucial for security and compliance. But legacy IGA systems are costly and time consuming to maintain, and most companies are looking to improve identity security, lower costs, and tap into AI-driven automation. Many are considering migrating to the cloud, but don’t know if that’s right or where to begin.

Webinar Recording
Pioneering Zero Trust Network Access With Intelligent Microsegmentation
Mar 29, 2023
Working from anywhere and the adoption of cloud services from multiple providers have become increasingly common in the post-pandemic era, but this has created new opportunities for cyber attackers to enter and move across networks. A modern approach to network security is essential.

Webinar Recording
Best of Both Worlds: Combining Multi-Factor and Passwordless Authentication
Mar 24, 2023
Most organizations realize that passwords are no longer fit for purpose. They are costly and difficult to maintain, and they are easily compromised, enabling a high proportion of cyber-attacks. Many organizations are looking to Multi-Factor Authentication (MFA) and Passwordless Authentication as solutions, but this can be challenging.

Webinar Recording
Urgent: Find and Block Identity-Centric Security Threats Today
Mar 22, 2023
The inability to deal with identity-centric cyber threats is one of the most critical issues facing modern enterprises. Attackers are increasingly targeting digital identities to gain unauthorized access to systems and data. Action is essential, but detecting unauthorized access is challenging.

Webinar Recording
Bringing Data Back Under Control
Mar 15, 2023
Data is your organization’s most important asset, and yet it is increasingly held and processed outside of your control. Data security, resilience and storage is becoming increasingly challenging and costly. A new approach is needed to adapt quickly and bring these things under control amid increasing geopolitical uncertainty and risk.

Webinar Recording
Re-Imagining Identity Management for the Digital Era
Mar 10, 2023
An explosion of digital identities, coupled with multi-cloud adoption and the trend of working from anywhere, is adding complexity to managing identities and access rights. An innovative strategy is needed to enable organizations to support business and security needs in the digital era.

Webinar Recording
Cyber Resilience Through SOC Automation
Mar 08, 2023
Cyber resilience is now essential for the survival of every business, but identifying and responding to cyber threats quickly is challenging. Staff at many Security Operations Centers (SOCs) are struggling due to the high volume of security alerts, coupled with a shortage of cybersecurity talent. To address these issues, many companies are turning to automation.

Webinar Recording
Mehr Widerstandsfähigkeit Gegen Cyberangriffe: Das Automatisierte SOC
Mar 03, 2023
Cybersicherheit ist zu einer zentralen Herausforderung für jedes Unternehmen geworden. Die Widerstandsfähigkeit, also die Cyber Resilience, ist inzwischen elementar für die Überlebensfähigkeit von Unternehmen. Die automatisierte Analyse und Reaktion von sicherheitsrelevanten Informationen und Ereignissen wird dabei von sogenannten SOAR-Lösungen (Security Operations and Automated Response) unterstützt, die nicht nur Informationen vergleichen und analysieren, sondern direkt „operational“ machen und automatisierte Reaktionen und nachgelagerte Prozesse wie die Incident Response anstoßen können.

Webinar Recording
Understanding the Privacy Evolution to Get Ahead of the Curve
Mar 01, 2023
In the age of big data, AI, multi-cloud and hybrid IT environments, and ever closer links between customers, third parties and organizations, businesses need to think more carefully about privacy. But this can be challenging, with rapidly evolving technology and increased regulatory complexity.

Webinar Recording
The Future of Privileged Access Management
Feb 15, 2023
PAM is an established and essential discipline within IAM. Traditional PAM is primarily focused on securing privileged access, for instance of administrators, to servers and systems. In today’s dynamic IT environments, the need for just-in-time access and for supporting agile workloads in IaaS environments is growing. PAM must support these emerging needs. There also is a growing need for integration with other areas of IAM such as Access Management solutions.

Webinar Recording
Access Governance für SAP-Systeme – Direkt aus dem IGA-System
Feb 10, 2023
SAP-Systeme sind zentrale Komponenten der Business-Anwendungen in vielen Unternehmen. Mit der vermehrten Nutzung von anderen Cloud-Lösungen für Teile der Geschäftsprozesse sind sie aber längst nicht mehr die einzigen Lösungen, in denen kritische Informationen gehalten werden.
Damit stellt sich immer mehr die Frage, welche Systeme die Zugriffskontrolle und Risikoanalyse für SAP übernehmen. IGA-Lösungen können hier eine zentrale Funktion übernehmen, um Audit- und Sicherheitsanforderungen effizient und integriert umzusetzen.

Webinar Recording
Unlock the Potential of Passwordless Authentication
Feb 09, 2023
The idea of passwords becoming obsolete has been discussed by the IT industry for years, if not decades. In recent years, Passwordless Authentication has become a popular and catchy term. It is used to describe a set of identity verification solutions that remove the password from all aspects of the authentication flow, and from the recovery process as well. Some passwordless options have been around for a while but are starting to be implemented more by enterprises and even consumer-facing businesses.

Webinar Recording
Debunking Common Myths about XDR
Jan 25, 2023
Cyber attacks are continually evolving and so are cyber defense technologies. In a few decades we have moved from anti-virus protection through an alphabet soup of acronyms, including EPP, EDR, EPDR, NDR, CWPP, SIEM, SOAR, and now XDR. It is therefore important for businesses to get a good understanding what combination of defense technologies to choose and why.

Webinar Recording
Championing Privileged Access Management With Zero Trust Security
Jan 20, 2023
In the age of hybrid working, global organizations urgently need a unified approach towards securing their privileged identities, such as user accounts, devices, admins , and more, against abuse and insider threats. If one or more of these privileged identities were compromised, the consequences for organizations could be devastating, especially when looking at critical infrastructures.

Webinar Recording
Evolving Identity and Access Management for the Digital Era
Jan 18, 2023
Businesses are undergoing digital transformations and adopting new technologies to become as flexible and agile as possible to remain competitive. But ensuring that only authorized entities have access to critical business data and applications is essential. Modern IT demands modern IAM that supports cloud adoption and business process optimization.

Webinar Recording
Implementing Zero Trust With Privileged Access Management Platforms
Dec 16, 2022
There is no debate about the fact that ransomware is the fastest-growing kind of cybercrime. Due to their wide range of access rights and thus potential ransom leverage, privileged accounts are at the top of the target list for cybercriminals. Therefore, organizations need to pay special attention to securing these kinds of accounts.

Webinar Recording
Unify Identity and Security to Block Identity-Based Cyber Attacks
Dec 07, 2022
Compromised credentials are a top cyber-attack method. Identity-based attacks are on the rise, it is therefore vital that businesses can detect the misuse of enterprise identities to block attackers from getting unfettered insider access to IT systems and data. But that can be challenging in today’s distributed, hybrid, and multi-cloud business IT environment.

Webinar Recording
Secure DevOps: Key to Software Supply Chain Security
Nov 30, 2022
In the modern world of flexible and remote working, it is useful for software engineers to be able to access and update source code from anywhere using any device, but the SolarWinds supply chain attack showed that it is essential to track every change for security and compliance reasons.

Webinar Recording
Don’t Delay, Get Ready for a New Digital World Today
Nov 25, 2022
Like many other countries, digitization is a strategic priority in Germany, where there is a concerted effort to digitize public services. German banks and insurance companies are also digitalizing their customer journeys. Other organizations need to do the same, or risk losing competitive advantage in the digital era.

Webinar Recording
You Deserve a Better Security Testing Experience
Nov 23, 2022
To remain competitive, businesses are embracing digital transformation, adopting cloud services and agile software development. But this is creating opportunities for attackers because most organizations lack the skills, knowledge, and expertise to match attackers’ ability to find and exploit vulnerabilities. There needs to be a shift in the way organizations conduct security testing.

Webinar Recording
Effective IAM in the World of Modern Business IT
Nov 18, 2022
Digital Transformation promises lower costs, and increased speed and efficiency. But it also leads to a mix of on-prem and cloud-based IT infrastructure, and a proliferation of identities that need to be managed in a complex environment. Organizations adopting a Zero Trust approach to security must find a way to overcome these challenges.

Webinar Recording
Making Passwordless Authentication a Reality: The Hitchhiker’s Guide
Nov 16, 2022
In this webinar, Bojan Simic, founder and CEO at HYPR, and Martin Kuppinger, Principal Analyst at KuppingerCole Analysts, will share their insights and experience on what to consider when moving towards passwordless authentication, and making this a reality.

Webinar Recording
Protecting Web Applications Amid Severe Staff Shortages
Nov 03, 2022
Organizations are more dependent than ever on web applications for doing business with partners and customers, which means that protecting web applications has become business critical. But many companies are facing severe skills shortages exacerbated by the “Great Resignation”, and web application security is particularly hard hit. Automation is key to overcoming this challenge.

Webinar Recording
Better Business With Smooth and Secure Onboarding Processes
Oct 28, 2022
In the modern world of working, organizations need to digitally verify and secure identities at scale. But traditional IAM and CIAM strategies can’t identity-proof people in a meaningful way in the digital era. Finding an automated digital identity proofing system that is passwordless and provides strong authentication, is essential.

Webinar Recording
Advanced Authorization in a Web 3.0 World
Oct 26, 2022
Business and just about every other kind of interaction is moving online, with billions of people, connected devices, machines, and bots sharing data via the internet. Consequently, managing who and what has access to what in what context, is extremely challenging. Business success depends on finding a solution.

Webinar Recording
Why Data Resilience Is Key to Digital Transformation
Oct 21, 2022
As companies pursue digital transformation to remain competitive, they become more dependent on IT services. This increases the potential business impact of mistakes, natural disasters, and cyber incidents. Business continuity planning, therefore, is a key element of digital transformation, and must cover business-critical data and applications.

Webinar Recording
A Winning Strategy for Consumer Identity & Access Management
Oct 19, 2022
Success in digital business depends largely on meeting customers’ ever-increasing expectations of convenience and security at every touchpoint. Finding the best strategy to achieve the optimal balance between security and convenience without compromising on either is crucial, but can be challenging.

Webinar Recording
Implementing Modern and Future-Proof PAM Solutions
Oct 14, 2022
Privilege Access Management (PAM) is changing, driven by the move of most businesses from on-prem IT applications and infrastructure to the cloud, resulting in a multi-could, multi-hybrid IT environment. This has resulted in a proliferation of privileged identities that need to be managed.

Webinar Recording
A Zero Trust Approach to Cyber Resilience
Oct 13, 2022
Security in many organizations is not evolving fast enough to keep up with business transformation, including migration to the cloud and to Industry 4.0. These changes, while essential to remain competitive, bring fresh security risks. A new approach is needed to ensure cyber resilience.

Webinar Recording
A DevSecOps Maturity Model for Secrets Management
Oct 07, 2022
Recent high-profile software supply chain attacks have highlighted the importance of security in the DevOps environment. But this can be challenging because DevOps teams are at the forefront of digital transformation and use agile techniques to deliver applications quickly, often not following traditional paths of identity management.

Webinar Recording
Breaking the Ransomware Attack Chain
Oct 05, 2022
At some point, any business connected to the internet is likely to become a victim of a ransomware because they are relatively easy and inexpensive to carry out, but potentially yield large payouts for cybercriminals. The best way of tackling this threat is to know how to break the attack chain.

Webinar Recording
Taking the Risk Out of Key Digital Business Enablers: APIs
Sep 30, 2022
Application Programming Interfaces (APIs) are among the foundations of modern digital business. APIs are found everywhere due to a rapid growth in demand to expose and consume APIs to enable new business models and connect with partners and customers, but APIs are also a security risk that businesses can’t afford to ignore.

Webinar Recording
Ensuring the Security of Microsoft Active Directory and Azure AD
Sep 28, 2022
In the face of increasing cyber-attacks by cybercriminals and nation-states, most organizations are investing in filling in the gaps in their cyber defenses, but as the landmark SolarWinds supply chain breach showed, securing Microsoft Active Directory (AD) is vital, but often overlooked.

Webinar Recording
A Comprehensive Approach to Solving SaaS Complexity
Sep 23, 2022
As businesses adopt cloud-based services as part of digital transformation programs to enable flexible working, boost productivity, and increase business agility to remain competitive, many IT and security teams are finding it challenging to gain oversight and control over the multitude of Software as a Service (SaaS) applications.

Webinar Recording
Cybersecurity-Teams mit Managed Detection Response stärken
Sep 21, 2022
Organisationen, die die Digitalisierung ihrer Businessprozesse versäumen, werden es in naher Zukunft schwer haben, wettbewerbsfähig zu bleiben. Mit zunehmender Digitalisierung steigen aber auch die Cyberrisiken, weil die Verlagerung von Dienstleistungen in die Cloud und die zunehmende Unterstützung von mobilem und dezentralem Arbeiten die Bedrohungsflächen rapide vergrößert. IT-Sicherheitsteams haben nicht zuletzt wegen geringer Budgets und mangelndem Know-How Mühe, Bedrohungen zu erkennen, darauf zu reagieren und sie einzudämmen, zumal diese zunehmend von staatlicher Seite ausgehen und mit...

Webinar Recording
Zero Trust Is Driving the Evolution of Authorization
Sep 16, 2022
Verifying what specific applications, files, and data that a human or non-human entity has access to, is at the heart of cybersecurity in the face of increasing theft of data for espionage or other criminal purposes. Authorization, therefore, is extremely important to security, but it is also key to boosting brand trust and improving user experience.

Webinar Recording
Managing Cyber Risk in a Hybrid Multi-Cloud IT Environment
Sep 14, 2022
Today’s IT environments blend applications and services from multiple public cloud networks, private clouds and on-prem networks, making it difficult to view and inventory assets deployed across complex hybrid networks, and keep track of the security risks. Organizations need to find a way to improve visibility, identify and prioritize risks, and maintain cyber resiliency.

Webinar Recording
Security and Compliance Benefits of Endpoint Privilege Management
Jul 29, 2022
As IT applications and endpoints proliferate, and enterprises shift to hybrid IT and hybrid working models, managing end user privileges is becoming very challenging, resulting in breaches, fraud, and undetected risky behavior. Enterprises need a way of governing end users wherever they are working and protecting a growing number of endpoints.

Webinar Recording
Multi-Cloud Permissions Management
Jul 27, 2022
Most businesses are adopting cloud services from multiple providers to remain flexible, agile, efficient, and competitive, but many do not have enterprise-wide control over and visibility of tens of thousands of cloud access permissions, exposing the enterprise to risk of security breaches.

Webinar Recording
You Can Only Protect and Govern the Data You Know About
Jul 15, 2022
Data is widely recognized as the lifeblood of the modern enterprise. However, the exponential rate at which it is being generated means that it is crucial that organizations have the capability to manage it effectively to ensure its confidentiality, integrity, and availability.

Webinar Recording
Multi-Cloud Identity Governance 101
Jul 13, 2022
In an effort to cut costs, improve efficiencies, and cater for a mobile and remote workforce, businesses are adopting cloud services from multiple providers. This has created a host of challenges in managing identity and access across multiple clouds, and has introduced several risks that need to be addressed urgently.

Webinar Recording
DevOps Tools: Securing the Software Supply Chain
Jul 08, 2022
Following the SolarWinds and Kaseya supply chain attacks, security of the DevOps tools chain with all the related components has shifted to the center of attention. There is a lot to do around securing code and CI/CD tools, as well as the execution environments. But it all starts with protecting secrets such as keys, certificates, and even passwords.- each one of these can provide access to large amounts of critical information.

Webinar Recording
Erfolgreiche IAM-Projekte: Von Best Practices Lernen
Jul 06, 2022
Häufig beginnt die Suche nach einer Identity-Lösung mit einem ganz konkreten Schmerzpunkt im Unternehmen. Ein nicht bestandener Compliance-Audit wegen überhöhter Zugriffsberechtigungen, technische Probleme, wegen komplexer Systeme frustrierte User und eine Überforderung des Helpdesk mit Berechtigungsanforderungen und Passwort-Resets sind nur einige der vielen möglichen Ursachen. Selbst nach einer erteilten Budgetfreigabe für die Anpassung der IAM-Landschaft sind die Hürden vielfältig.

Webinar Recording
Maximizing the Benefits of Customer Identity & Access Management
Jul 01, 2022
CIAM solutions often come packed with features that could be used to improve consumer experiences, which is key to success in the digital era. However, in most cases, organizations that deploy CIAM products or use cloud-hosted CIAM services are under-utilizing the capabilities, which leads to poor customer experiences.

Webinar Recording
Dealing Effectively with Modern, Industrialized Cyber Threats
Jun 30, 2022
The cyber threat landscape has become very complex, with state-of-the-art intrusion, ransomware, and cryptocurrency mining tools now readily available through online stores and service providers, and an expanding attack surface due to increased cloud computing and remote working. Keeping data secure while ensuring its availability to legitimate users has become extremely challenging.

Webinar Recording
Effective Threat Detection for Enterprises Using SAP Applications
Jun 29, 2022
Determined cyber attackers will nearly always find a way into company systems and networks using tried and trusted techniques. It is therefore essential to assume breach and have the capability to identify, analyze, and neutralize cyber-attacks before they can do any serious damage.

Webinar Recording
IAM Projects Done Right
Jun 22, 2022
Delivering effective IAM is not always easy, and around half of IAM projects run into difficulties and stall. While opting for IAM that is delivered as a service is a potential solution, not all offerings are equal. Finding a service with the right combination of well-integrated capabilities is crucial to success.

Webinar Recording
The Changing Scope of the NIS 2 EU Directive
Jun 15, 2022
The NIS Directive aimed at achieving a common standard of network and information security across all EU Member States, with a focus on operators of essential services, is scheduled for an update. Suppliers of utilities, healthcare, transport, communications, and other services need to know what changes are coming and what they need to do to comply.

Webinar Recording
Effective Cyber Risk Quantification Through Automation
Jun 07, 2022
Continual high-profile cyber incidents demonstrate beyond a doubt that cyber risks exist, but most organizations struggle to quantify cyber risk in a useful way. There is an urgent need for IT security leaders to find a common way to express cyber risk in monetary terms, that business leaders understand to enable effective risk management and security investment.

Webinar Recording
Why Architects Should Rethink Authorizations
Jun 02, 2022
In the digital era, organizations are increasingly interacting online with contractors, partners, and customers. Traditional role-based authorization frameworks are not designed to provide these external identities with the right access to resources, services, and apps. A new approach is required.

Webinar Recording
Fixing the Way the World Logs In
Jun 01, 2022
Passwords are quickly and easily compromised, they are costly and difficult to manage, and they result in poor user experiences. Many organizations are looking for alternatives, but find it challenging to identify appropriate passwordless and phishing resistant authentication solutions that are simple, effective, and secure.

Webinar Recording
Effective Identity Access Governance in Hybrid SAP Environments
May 27, 2022
Increased cyber threats and regulatory requirements for privacy and security make staying on top of user roles and access rights in hybrid IT environments more important and challenging than ever, which means it’s important to understand the real risks and how to mitigate them effectively with modern GRC capabilities.

Webinar Recording
Making Zero Trust a Reality: Basing Decisions on Valid Identity Data
May 20, 2022
Cloud computing and mobile workforces have resulted in an expanding attack surface and a complex web of identify information. This means that traditional perimeter-based security models are no longer effective. A Zero Trust model of strict access control for every user and device enables businesses to be connected and secure, but an effective identity-focused approach is essential.

Webinar Recording
Modern Identity Management: Security Without Compromising Usability
May 04, 2022
In the digital age, effective customer, partner, and employee identity and access management (IAM) is essential to enable secure online transactions, collaboration, and other interactions. But finding the right balance between security and usability has traditionally been challenging and required compromise. However, this is changing.

Webinar Recording
The Machine Monitoring Mandate
Apr 27, 2022
Governments world-wide are increasingly worried about the social unrest that could result from a cybersecurity compromise of critical infrastructure. This has highlighted the fact that the underlying operational technology (OT) is often inadequately protected, and that this must change.

Webinar Recording
Passwords: Dead, but Not Gone
Apr 22, 2022
Organizations are looking to eliminate passwords because they are costly and difficult to manage, they result in poor user experiences, and they are easily compromised, enabling 81% of breaches. But despite these efforts, many passwords remain unsecured. These passwords can still be compromised, and must be managed to mitigate the risk.

Webinar Recording
Passwordless Customer Authentication: Reduce Friction and Increase Security
Apr 19, 2022
Acquiring and retaining customers is key in the modern world of e-commerce, but this can be challenging if creating and accessing accounts is difficult. Online traders need to find ways of turning authentication into a competitive edge by reducing friction and improving security.

Webinar Recording
Policy Based Access Control for Cloud-Native Applications
Apr 13, 2022
As companies shift to cloud-native applications, the complexity of a microservices framework can be daunting. When applications are built in a cloud-native stack, authorization is also infinitely more complex. Crucially, Open Policy Agent (OPA) decouples policy from code, enabling the release, analysis, and review of policies without impacting availability or performance.

Webinar Recording
Protecting the Business From Software Supply Chain Threats
Apr 08, 2022
Recent events such as the SolarWinds and Kaseya compromises by malicious actors have demonstrated the need to focus significantly more on software supply chain security. According to a report from ENISA, supply chain attacks are increasing, with 66% of attacks focusing on source code and 62% exploiting customer trust in suppliers. This is a risk organizations can’t afford to ignore.

Webinar Recording
Understanding the Unified Endpoint Management (UEM) Market
Mar 31, 2022
Business IT environments continue to undergo rapid and continual change as businesses seek to improve productivity and efficiency by adopting cloud-based services and enabling employees to work on a wide range of mobile devices. But this has in turn created opportunities for attackers.

Webinar Recording
An Agile Approach to Customer Identity and Access Management (CIAM)
Mar 25, 2022
Business success in the digital era depends on delivering seamless and secure customer experiences. Failure to do so can easily result in abandoned shopping carts, fraudulent transactions, and regulatory fines. However, delivering exceptional experiences and keeping pace with the speed of business is challenging.

Webinar Recording
Zero Trust: Putting Theory Into Practice
Mar 18, 2022
Now is the time to implement the Zero Trust security model because the traditional model of enforcing security at the network perimeter is no longer effective. However, moving from theory into practice can be challenging unless you start with a key element like effective endpoint management.

Webinar Recording
Eliminate Passwords With Invisible Multi-Factor Authentication
Mar 11, 2022
A high proportion of data breaches and ransomware attacks exploit stolen credentials. Eliminating passwords with multifactor authentication is an effective way to reduce the risk of unauthorized access to company networks, systems, SaaS applications, cloud infrastructure, and data. But not all MFA systems are created equal.

Webinar Recording
Enabling Full Cybersecurity Situational Awareness With NDR
Mar 02, 2022
Effective cyber defense depends on detecting, preventing, and mitigating threats not only on desktops, laptops and servers, but also on the network, in the cloud, and in OT, ICS and IoT, which is where Network Detection & Response (NDR) solutions come into play. Support for a security operations (SecOps) approach is essential as remote working becomes commonplace.

Webinar Recording
Die Rolle von Identity Security bei Zero Trust
Feb 25, 2022
„Zero Trust“ ist heute für die meisten CISOs ein regelmäßiges Gesprächsthema. Im Kern geht es bei Zero Trust um das Prinzip der kontinuierlichen und sorgfältigen Zugriffskontrolle an mehreren Stellen für alle Benutzer beim Zugriff auf Netzwerk- und Systemressourcen ebenso wie Daten. Das ist erst einmal nichts Neues, bringt jedoch eine neue Fokussierung für die Frage, was und wie man IT-Sicherheit und Identity Security umsetzt. Zugriff muss mehr, detaillierter und besser gesteuert und kontrolliert werden.

Webinar Recording
Zero Trust: Now Is the Time and PBAC Is Key
Feb 11, 2022
Now is the time to implement the Zero Trust security model because the traditional model of enforcing security at the network perimeter is no longer effective with users, devices and workloads moving outside the corporate network, but success depends on understanding the essential components of a Zero Trust Architecture.

Webinar Recording
A Delegated Model for B2B Access Management
Jan 26, 2022
In the digital age, collaboration is becoming more dynamic and integrated than ever before. External partners often require specific information, and therefore need access to internal systems. Providing efficient processes to manage partners is key to building a strong partner network.

Webinar Recording
New Methods to Accelerate Endpoint Vulnerability Remediation
Jan 21, 2022
IT endpoints are no longer just workstations and servers confined to corporate headquarters, branch offices, customer sites, and data centers, they can now be just about anything located anywhere, from employee homes to airports, hotels and in the cloud. But every endpoint represents a potential entry point for cyber attackers, and needs to be managed.

Webinar Recording
Are You Ready for Security Automation?
Jan 14, 2022
Security Orchestration, Automation & Response (SOAR) tools are the latest in the evolution of automated cyber defenses and are set to become the foundation of modern Security Operations Centers (SOCs). But SOAR is not only for large enterprises. The benefits for smaller organizations should not be overlooked.

Webinar Recording
Identity & Access Management Predictions 2022
Dec 21, 2021
Increased remote working, a dramatically increased digital customer interaction landscape, the hyperconnected industry 4.0 enterprise, an increasingly complex multi-cloud multi-hybrid infrastructure - much of what we based our past strategic assumptions on has developed faster and with a different emphasis.

Webinar Recording
Prediction #1 - Passwordless Authentication: Killing the Undead will become Mainstream in 2022
Dec 21, 2021
The increased importance of a frictionless user experience as a digital business success factor on the one side, and a big wave of ransomware and similar attacks with user credentials as a main entry point are forcing us to rethink authentication and finally get rid of the password. Interview guests of this session will be KC Analyst Martin Kuppinger, Paul Fisher and Jochen Koehler from HYPR.

Webinar Recording
Prediction #2 - The Convergence of IAM and how to Manage Complexity in a Multi Cloud, Multi Hybrid, Multi Identity World
Dec 21, 2021
It is the same set of drivers – first and foremost remote workforce requirements and seamless customer interaction, that make our infrastructure and service even more complex as they used to be, with multiple public and private clouds, on-site IT, all of them with identity silos. In this session, KuppingeCole´s Analyst Martin Kuppinger and Paul Fisher, will talk with André Priebe from iC Consult on how to leave silos behind and take advantage of global identity proofing networks, Decentralized (DID/SSI) or chain-agnostic (GAIN etc.) and how CIEM/DREAM can help...
Webinar Recording
Prediction #3 - Identity Proofing & Fraud Reduction Everywhere
Dec 21, 2021
The pandemic has dramatically accelerated the shift to online transactions in most industries, with the financial industry as an example for a heavily regulated sector being in the forefront of a movement to establish a global standard that leverages the assurance level of online identity vetting (the onboarding process of a digital identity) with traditional face-to-face methods. In this session, KuppingerCole Analysts Martin Kuppinger and Paul Fisher together with ForgeRock's Eve Maler will discuss the relevance of identity proofing for your enterprise and why it will be one of the key...

Webinar Recording
Prediction #4 - Identity & Access: The Big Efficiency Push
Dec 21, 2021
Workflows, integration, automation, low & no code – whatever reduces complexity and manual workload will be an even hotter topic in 2022. KuppingerCole Analysts Martin Kuppinger and Paul Fisher will discuss with Clear Skye´s Jackson Shaw on the new era of platform services and how they will help automating Identity & Access Management.
Webinar Recording
Prediction #5 - Zero Trust: The Next Level
Dec 21, 2021
Zero Trust will continue to play a crucial role in cybersecurity and identity management. In this session, KuppingerCole Analysts Martin Kuppinger and Paul Fisher will discuss with Sergej Epp from Palo Alto Networks on how to apply Zero Trust thinking to converge IAM, UEM, MDM, XDR, SIEM, SOAR to a seamless and holistic cybersecurity infrastructure.

Webinar Recording
Identity Security: A Top Priority for the Modern Enterprise
Dec 15, 2021
Accelerated digital transformation has led to an explosion of digital identities, which means any user can have some level of privileged access at some time. Cyber attackers are targeting this rapidly expanding attack surface. This means identity security, has never been more important or challenging.

Webinar Recording
Mitigate Risks, Cut Cost, and Achieve Compliance With AI-Driven IGA
Dec 10, 2021
Effective Identity Governance and Administration (IGA) is becoming increasingly important as digital transformation, cloud computing, and remote working increase the scope and complexity of Identity and Access Management (IAM) to new levels. But legacy role-based access control (RBAC) solutions alone are unable to meet the changing and dynamic IGA requirements of modern enterprises.

Webinar Recording
Lessons From a Journey Into a Real-World Ransomware Attack
Dec 08, 2021
Ransomware Attacks have become the biggest single cyber risk for enterprises of any size and industry. Research indicates a steep rise not only in the number of attacks, but as well in the average damage per incident. It is therefore essential that organizations are prepared for these attacks.

Webinar Recording
Urgent Need to Protect the Most Critical Business Assets: Data & People
Dec 03, 2021
Data is widely considered the “new oil" because data has great value and provides direct and secondary revenue streams. But, also like oil, data can leak from organizations that depend on it. Therefore, data security and the prevention of data leakage is imperative for business as well as regulatory compliance reasons.

Webinar Recording
Combatting Fraud Proactively With Behavioral Biometrics
Nov 26, 2021
Digital businesses are facing an increasing onslaught of fraud enabled by malware, social engineering, and other cyber criminal activities. Strong authentication is essential, especially in the context of PSD2, but it can be challenging to achieve without adding friction to the user experience.

Webinar Recording
Engineering Successful IAM Projects to Support Digital Business
Nov 24, 2021
In the digital era, traditional approaches to Identity and Access Management (IAM) are ineffective. IAM is no longer just about managing employee identities, but about managing all kinds of identities across a wide variety of use cases. This requires a comprehensive and agile approach.

Webinar Recording
Delivering on the Promise of an Identity Fabric in a Modern Enterprise
Nov 05, 2021
Identity sprawl is a challenge facing most modern enterprises as a result of inorganic growth, piecemeal identity solutions, and more recently, a loss of control due to unplanned remote work. This sprawl leads to tremendous technical debt and has turned identity and access management into a roadblock for many organizations.

Webinar Recording
Sicherheit für SAP und mehr: Wie IGA-Systeme unterstützen können
Oct 29, 2021
Access Governance-Tools sind in der heutigen Business-IT ein unverzichtbares Element. Sie dienen dem Management von Benutzer- und Berechtigungsworkflows, der Vergabe von Zugangsrechten, der Durchführung von Kampagnen zur Zugriffszertifizierung und der Implementierung und Prüfung von Controls für die Funktionstrennung (SOD). Mit einer wachsenden Zahl von Business-Applikationen, gerade auch aus der Cloud, und ihrer Vernetzung wächst die Herausforderung, Access Governance übergreifend und automatisiert umzusetzen.

Webinar Recording
Why Continuous API Security Is Key to Protecting Your Digital Business
Oct 22, 2021
In the era when data has replaced oil as the most valuable commodity, APIs have become an important logistical foundation of modern digital business. As a result, APIs have also become a popular target for cyber attackers, and therefore effective API security is essential. However, focusing only on the operational aspects is no longer enough.

Webinar Recording
Meeting the Identity and Access Challenges in a Multi-Cloud World
Oct 20, 2021
Multi-cloud deployments are becoming increasingly common as organizations seek to remain competitive in the digital economy and address demands for increased remote working. But while cloud migration is enabling business success, it is not without its identity and access challenges.

Webinar Recording
Understanding the Privileged Access Management (PAM) Market
Oct 19, 2021
Privileged Access Management (PAM) solutions are critical cybersecurity controls that address the security risks associated with the use of privileged access in organizations and companies. To reduce the risk of privileged accounts being hijacked or used fraudulently, and to uphold regulatory compliance, a strong PAM solution is essential. But finding the right PAM solution can be challenging.

Webinar Recording
Managing Risk in Ever-Changing As-a-Service Environments
Oct 15, 2021
In the infrastructure and platform-as-a-service worlds, application developers are the new infrastructure superstars. With concepts ranging from containers to infrastructure-as-code, we are experiencing a paradigm shift in how tightly coupled application code and the related infrastructure are. Often security is under-represented in this formula, and for good reason.

Webinar Recording
Verifiable Credentials: A Fresh Approach to Identity in the Digital Era
Oct 13, 2021
Establishing a verified digital identity is crucial to successful business collaboration and customer engagement in the digital economy. Verifiable Credentials provide a highly secure way of establishing digital identity. However, knowing exactly how to begin using this approach can be challenging.

Webinar Recording
Uncovering the Truth About SAP Identity & Access Management
Oct 08, 2021
Ensuring everyone has access to the right systems and data is critical for security and compliance, but often the management of identity and access in SAP is siloed. A survey by SailPoint Technologies and Turnkey Consulting uncovers the extent to which this is true and points to potential solutions.

Webinar Recording
API Management & Security Key to Digital Business Success
Oct 04, 2021
Application Programming Interfaces (APIs) have evolved into one of the foundations of modern digital business. APIs are found everywhere because they are key to creating new business models and connecting with business partners and customers. But opening up APIs is risky without the right security strategy and infrastructure in place.

Webinar Recording
Understanding the IGA-Focused Identity-as-a-Service (IDaaS) Market
Oct 01, 2021
The IDaaS market combines Access Management functions with Identity and Access Governance capabilities, and delivers them as a cloud-based managed service designed to meet the common IAM requirements of hybrid IT environments, but finding the right IDaaS solution with a focus on Identity Governance and Administration (IGA) can be challenging.

Webinar Recording
A Customer-First Approach to Identity-Based Authentication
Sep 30, 2021
Even though passwords can be compromised easily and are generally considered unsafe, they are still ubiquitous in a time when multi-factor authentication and biometrics are easily available. There’s little doubt that eliminating passwords improves security, but to effect fundamental change you must start with the customer experience and ask yourself where it’s possible to take it.

Webinar Recording
Disaster Planning Made Simple
Sep 29, 2021
In the digital era, as businesses become increasingly reliant on IT, a potentially devastating cyber-attack or other type of disruptive cyber incident is inevitable. Being prepared is the single most effective action that those responsible for information security can take.

Webinar Recording
Adding Certainty to Your Cyber-Attack Detection Capabilities
Sep 28, 2021
There is growing interest in deception as a methodology and as an integral part of cybersecurity architecture, as organizations seek more effective approaches for detecting and responding to threats in real time. Distributed Deception Platforms have made this approach practical and affordable for the first time, but choosing the right solution can be challenging.

Webinar Recording
Making IAM Agile and a Business Enabler
Sep 08, 2021
In the digital era, IAM is no longer just about employees. To become truly digital and tap into the new business benefits, organizations need IAM systems that can cater to partners, consumers and even things, as well as support IAM capabilities across all target systems, regardless of their deployment model.

Webinar Recording
Trust No One: Zero Trust Strategy and Design
Aug 25, 2021
With workloads moving to the cloud and remote working increasing, traditional perimeter-based security strategies are no longer practical. A Zero Trust model of strict access control for every user or device offers an alternative that secures data while ensuring it is accessible to those who need it. But the shift to treating both internal and external users as untrusted can be challenging.

Webinar Recording
Zero Trust Through Dynamic Authorization and Policy Driven Access
Aug 20, 2021
As workers become more mobile and workloads move into the cloud, the traditional model of enforcing security at the network perimeter becomes ineffective. A Zero Trust model of strict access control for every user or device protects your organization from advanced security threats enabling you to stay connected, productive and secure.

Webinar Recording
Zero Trust Through Identity-Based Segmentation
Jul 21, 2021
As workers become more mobile and workloads move into the cloud, the traditional model of enforcing security at the network perimeter becomes ineffective. A Zero Trust model of strict identity verification and access control for every user or workload offers an alternative that secures data while ensuring it is accessible to those who need it.

Webinar Recording
Identity Verification: Why It Is Needed and How It Can Benefit the Business
Jul 16, 2021
The COVID-19 pandemic has transformed the way customers engage with brands and led to increased digital interaction. But this has increased the incidence of fraud during the account creation process. As a result, businesses now face the challenge of verifying customer identity and verifying that those entities interacting with their brand are human and who they claim to be.

Webinar Recording
IT-Herausforderungen in der Digitalen Transformation
Jul 15, 2021
Die Digitale Transformation und die Notwendigkeit, von überall aus arbeiten zu können, nehmen massiven Einfluss auf die Unternehmensinfrastruktur. Das Ergebnis: Anwender, Applikationen und Daten sind nun überall und fordern bestehende Sicherheitslösungen heraus, sowohl einen umfassenden und konsistenten Schutz als auch eine performante User Experience zu bieten.

Webinar Recording
Zero Trust Means Zero Blind Spots
Jul 09, 2021
The traditional model of enforcing security at the network perimeter is no longer effective. The nature of the corporate network is changing with mobile and cloud computing. A Zero Trust model offers an alternative that secures data while ensuring it is accessible to employees, regardless of where they are working. But deciding how best to adopt Zero Trust can be challenging.

Webinar Recording
The Path to Going Passwordless
Jul 07, 2021
Password-based authentication is no longer fit for purpose. Passwords are costly and difficult to manage, they result in poor user experiences, and they are easily compromised. This has been widely recognized for some time, but going passwordless is also challenging and continues to be elusive for many organizations.

Webinar Recording
The IAM Cloud Journey
Jul 02, 2021
In the digital era, IT is increasingly being provided and consumed as cloud-based services, including Identity and Access Management (IAM). As more workloads and IT services move to the cloud, it makes sense to move IAM to the cloud as well. The most common path is to opt for an Identity as a service (IDaaS) solution, but this is not without its risks and challenges.

Webinar Recording
A Unified Approach to Modern Data Protection
Jul 01, 2021
Data is the lifeblood of business and government. Therefore, data breaches can be devastating in terms of disruption, damage to reputation, remediation costs, and data protection fines. But the ongoing high number of breaches shows that what many organizations are doing to protect their data is not working.

Webinar Recording
Accelerate Your Digital Transformation Through Identity
Jun 30, 2021
Employee Identity & Access Management (IAM) and Consumer Identity & Access Management (CIAM) are typically separate in terms of governance, processes, and technology. But, by leveraging the synergy between the two, businesses can achieve better sales opportunities as well as faster digital transformation, better customer journeys, and improved security, privacy, and compliance.

Webinar Recording
Access Risk Management for SAP and Beyond
Jun 28, 2021
Organizations are increasingly under pressure to deliver security, identity, compliance, governance, and risk management for all types of business applications. This challenge is exacerbated by the fact that most organizations have a heterogeneous landscape of business applications both in terms of vendors and deployment models.

Webinar Recording
A Fresh Look at the Business Value of PAM in the Work-From-Anywhere World
Jun 23, 2021
As businesses continue their digital transformation journey, managing privileged users has taken on a new and greater importance. Privileged Access Management (PAM) has never been more important, with increased remote working and employees increasingly getting privileged access to data and services.

Webinar Recording
Technological Approaches to a Zero Trust Security Model
Jun 18, 2021
The traditional model of enforcing security at the network perimeter is no longer valid as employees, devices and workloads move outside the corporate network. A Zero Trust model offers an alternative that secures data while ensuring it is accessible from wherever employees are working. But finding the right technological approaches to Zero Trust is challenging.

Webinar Recording
Does Increased Security Still Mean Added Complexity?
Jun 18, 2021
We’re all accessing more goods and services online than we ever thought possible, which has presented a huge opportunity for cyber criminals. Rapid digital transformation has left some businesses exposed, and fraudsters are looking to exploit new weaknesses. Strong digital identity verification and authentication is essential, but has traditionally come with increased complexity at the expense of a good user experience. But is this still true?

Webinar Recording
Privileged Access Management: Cloud Delivery Without Compromise
Jun 16, 2021
Privileged Access Management (PAM) solutions are critical cybersecurity and risk management tools for just about every business to address the security risks associated with privileged users and privileged access, but not everyone can afford expensive on-prem deployments.

Webinar Recording
Smart IAM Services for the Modern Digital Enterprise
Jun 09, 2021
The identities of employees, appropriate authorizations in processes and systems, and a permanent control and monitoring of access to prove compliance are becoming increasingly important for organizations. However, the management of these things remains less than optimal.

Webinar Recording
Digital Trust: Critical to Digital Business Success
Jun 02, 2021
2020 pushed the notion of trust to the forefront of all our lives. It made customer trust in brands acutely important to the bottom line amidst a severe economic recession. It also forced many organisations to overcome long-standing reservations about trusting their employees to work from home and placing their faith in digital channels to serve customers.

Webinar Recording
Remote-Angestellte mit starker Authentifizierung schützen
May 25, 2021
Hacker schlagen Kapital aus Unsicherheit, Angst, Ablenkung, Isolation und Verwirrung. Die Verlagerung auf Remote-Arbeit hat viele dieser Eigenschaften, daher ist es entscheidend, das Vertrauen der Benutzer wiederherzustellen. Die Schulung der Mitarbeiter ist unerlässlich, schützt aber nicht zuverlässig vor Angriffen, eine Lösung kann die Integration starker MFA in die Sicherheitsinfrastruktur.

Webinar Recording
Finding Your Path to Zero Trust
May 20, 2021
As users, devices and application workloads move outside the corporate network, the traditional model of enforcing security at the network perimeter is no longer effective. A Zero Trust model offers an alternative that secures data while ensuring it is accessible to employees, regardless of where they are working. But the path to achieving Zero Trust is unclear for many organizations.

Webinar Recording
Die Angriffsfläche Ihres Unternehmens aus den Augen eines Hackers
May 07, 2021
Mit zunehmender Digitalisierung und der Nutzung von Cloud-Services steigt das Angriffspotenzial auf die digitale Infrastruktur von Unternehmen. Hacker nutzen neuste Technologien, um Schwachstellen ausfindig zu machen und starten mit diesem Wissen Ihre Angriffe.

Webinar Recording
Are You Ready for Security Automation?
May 06, 2021
Security Orchestration, Automation & Response (SOAR) tools are the latest in the evolution of automated cyber defenses and are set to become the foundation of modern Security Operations Centers (SOCs). But SOAR is not only for large enterprises. The benefits for smaller organizations should not be overlooked.

Webinar Recording
Consumer Identity Management Evolution
Apr 20, 2021
Consumer Identity & Access Management (CIAM) is about managing access to customer-facing systems. While organizations have typically focused on using CIAM to collect, store, and analyze consumer data to create sales opportunities and inspire brand loyalty, other potential business benefits are being overlooked.

Webinar Recording
Identity ist kein Selbstzweck – Unternehmenskritische Applikationen mit Identity Security absichern
Mar 26, 2021
Die Corona-Pandemie hat die Digitalisierungsbemühungen in der DACH-Region angetrieben, aber auch Grenzen aufgezeigt. Die digitale Identität von Angestellten steht immer häufiger im Fokus des Interesses – sowohl von Sicherheitsbeauftragten als auch von Hackern. Identity Security ermöglicht Compliance über Plattformen und Anwendungen hinweg; sie hilft Komplexität und Kosten in den Griff zu bekommen.

Webinar Recording
Maturing a Zero-Trust Strategy for the Extended Enterprise
Mar 19, 2021
In the digital era, a 20th century perimeter-based approach to security is no longer appropriate or effective in securing the modern extended enterprise. Instead, a more flexible, identity-based approach is required that can be implemented at every layer of IT, from devices and networks to applications and data.

Webinar Recording
IT-Sicherheitsberatung hinter den Kulissen: Die Top 5 Herausforderungen, die Cloud Modelle mit sich bringen
Jan 28, 2021
Der Bedarf nach Cloud-Lösungen ist heute so stark wie nie zuvor. In den letzten Monaten konnten wir weltweit eine steigende Akzeptanz von Cloud Plattformen und Cloud-Diensten beobachten. Sogar die Deutsche Bahn verlagert ihre komplette IT in die Cloud.

Webinar Recording
The Evolution of Access Control
Jan 27, 2021
The purpose of an identity management system is to support access control to an organization’s sensitive systems and protected resources. Contemporary access control has progressed from static entitlements, still used in many organisations. Not only manual interventions are necessary to change roles, also provisioning, reconciliation, recertification and auditing are laborious tasks, which complicate each business process.

Webinar Recording
Accelerating Your Digital Transformation: Secure and Successful Cloud Migrations
Jan 21, 2021
The use of cloud services is one of the key enablers of digital transformation - accelerating time to value, providing more access to powerful IT resources in a more cost-effective manner and removing the management costs associated with commodity services. However, these benefits come with some risks. Migrating your business applications to the cloud without creating security vulnerabilities, unnecessary risks to your data and ensuring compliance, is critical for a successful digital transformation.

Webinar Recording
Effective Endpoint Security With Automatic Detection and Response Solutions
Jan 15, 2021
The realization that cyber-attacks are inevitable has led the cybersecurity industry to shift some of its focus to detection and response rather than prevention in recent years. Therefore, the market for solutions designed to detect attacks on endpoints and respond accordingly has grown significantly. These Endpoint Detection & Response (EDR) solutions look for evidence and effects of malware that may have slipped past Endpoint Protection (EPP) products. EDR tools also perform evaluation of threat intelligence, event correlation, and often allow interactive querying, live memory analysis,...

Webinar Recording
Making Zero Trust Work With the NIST Framework
Dec 17, 2020
There’s lots of hype around Zero Trust Security in the context of our changing mobile and cloud-centric working environments. Moving towards a modern and agile Zero Trust security concept is essential in today's mobile first, work-securely-from-anywhere world.

Webinar Recording
Entering the Virtual World With Identity Verification
Dec 16, 2020
The way consumers access products and services across sectors has changed forever as interactions move from physical to digital engagement. What started as a change born from convenience, is now a necessity and solidifying into a long-term behavioural shift. As consumers choose to access more goods and services digitally than ever before, it is essential that organisations meet users’ expectations of instant and convenient transactions, or risk losing customers to more customer centric online competitors.

Webinar Recording
Identität ist das neue Perimeter: Sichern Sie Zugriff und Nutzung von Cloud-Anwendungen
Dec 10, 2020
Da mittlerweile mehr als zwei Drittel aller Beschäftigten remote arbeiten, möchten Unternehmen Ihren Nutzern sichere und flexible Arbeitsmöglichkeiten über alle Plattformen und Geräte hinweg anbieten. Und da sich 85% Ihres Datenverkehrs bereits in der Cloud befindet, schützen Sie Ihre Nutzer und Daten am besten mit Security aus der Cloud. Aber wie?

Webinar Recording
The 3 Pillars of Access Control Optimization: IAM, GRC and User Monitoring
Dec 10, 2020
Identity & Access Management (IAM) tools are used to automate processes of user lifecycle management and control user access permissions from a single point. We can improve these processes by using conditions and policies, and eventually implementing rule-based access controls (RBAC) and policy-based access controls (PBAC). However, allocating these authorizations might expose the organization to risk if compliance is not taken into account. It is imperative to combine IAM and governance, risk management, and compliance (GRC) in order to verify that access is granted correctly, without...

Webinar Recording
Explore the Cutting Edge of Data-Driven Customer Experience
Dec 09, 2020
To accomplish complex and critical missions, market leaders are turning to a new generation of customer data platforms (CDPs). They uncover hidden revenue opportunities by unifying all sources of customer data into comprehensive and actionable profiles.

Webinar Recording
There Is No Successful Digital Transformation Without Strong Identity Management
Dec 04, 2020
2020 will go down in history as the year in which many companies gave their stagnating digital transformation initiatives a big new push. Due to the pandemic, organizations were forced to rapidly scale up their remote working facilities, secure employee-owned devices (Bring Your Own Devices (BYODs) , and maintain a secure environment for enterprise and customer identities . However, when it comes to their identity architecture, the picture is typically fragmented. They may have a general Identity and Access Management (IAM) platform from one company, a Privileged Access Management (PAM)...

Webinar Recording
Managing Azure AD – Regardless of How You Use It
Dec 03, 2020
Microsoft Azure Active Directory (Azure AD) has gained widespread adoption. Coming with Microsoft Azure Cloud as well as Microsoft 365 (i.e. Office 365), it appears in many organizations just because of decisions made outside of the IAM team.

Webinar Recording
Zero Trust for the Workforce
Dec 02, 2020
While the concept of zero-trust networking is nearly a decade old, the last few years have seen its popularity in industry discussions grow exponentially.

Webinar Recording
Zugriffsmanagement mit künstlicher Intelligenz neu erfinden
Nov 25, 2020
Unternehmen müssen in der modernen IT-Welt eine Vielzahl von Angestelltenidentitäten, Benutzerrollen, Zugangspunkten und Endgeräten verwalten. Diese Verwaltung von digitalen Identitäten und den entsprechenden Zugriffsrechten ist für die meisten Firmen nicht nur kompliziert, sondern auch zeitaufwändig. Wenn Unbefugte fälschlicherweise Zugriff zu sensiblen Unternehmens- und Kundendaten erhalten, kann dies zu Compliance-Problemen, Bußgeldern und Reputationsverlusten führen.

Webinar Recording
Privacy Compliance That Empowers Instead of Hinders
Nov 20, 2020
Protecting user privacy has become much more complicated as of late. Organizations must optimize consent rates while ensuring compliance with ever-changing global regulations and frameworks. They must look critically at their own processes to identify gaps or failures to meet privacy regulations. And organizations must find ways to effectively manage consumer requests, meticulously document processing activities and data transfers, and stay on top of a rapidly evolving regulatory landscape. Challenging, yes. But absolutely necessary.

Webinar Recording
The Role of Customer Identity & Access Management in Digital Transformation
Nov 13, 2020
Companies and organizations have strategic decisions to make at the Customer Identity & Access Management (CIAM) front. First, they have to decide whether to invest into a dedicated CIAM solution or to build on existing infrastructure. If there is already a foundation, what should be their next steps to have a mature CIAM strategy in place? If they do not have a CIAM solution, where do they start? Applications, systems, identities tend to be siloed while as a business grows, it’s imperative they are cohesive and well-integrated in order to provide a superior customer experience.

Webinar Recording
Choosing the Right Fraud Reduction Intelligence Tool in a Digitally Evolving Economy
Nov 06, 2020
Fraud is a major cost to businesses worldwide and it is on the rise. In it’s 2019 annual report, the Internet Crime Complaint Center (IC3) put a specific focus on methods such as elder fraught, credit card fraud and confidence/romance fraud, emphasizing the growing occurrence of intentional deception in cybercrime. Companies of all industries face the same challenge: The complex and constantly changing world of fraud detection.

Webinar Recording
Operationalizing Least Privilege
Nov 05, 2020
Striking the balance between enabling users and administrators to be productive whilst protecting your sensitive systems and data is becoming ever more challenging. Attackers are often one step ahead of organizations, and even those with the most comprehensive security systems and controls in place find that an attacker will discover and exploit their Achilles’ heel.

Webinar Recording
Decoding Advanced Privileged Access Management for Digital Environments - A conversation with Paul Fisher and Anil Bhandari
Nov 04, 2020
Did you know that privileged accounts are a major source of data leaks? These powerful administrative accounts provide access to business-critical information stored in applications and servers. A single instance of privileged password abuse can bring down the entire IT infrastructure. Therefore, enterprises are rethinking the access control mechanism to harden authentication.

Webinar Recording
What’s Really Going on in Your Microsoft Active Directory and Azure AD Infrastructure
Oct 30, 2020
Most small and mid-sized businesses rely on Microsoft technology in their IT infrastructure. For the vast majority of larger organizations, solutions such as Microsoft Active Directory also form a vital part of their IT infrastructure. Understanding what is going on in these infrastructures thus is essential. Only then, organizations will be able to react quickly and focused.

Webinar Recording
Using Deception for Early and Efficient Threat Detection
Oct 29, 2020
Most organizations are benefiting from the scalability, flexibility, and convenience of modern cloud services and new, highly distributed hybrid corporate networks. Unfortunately, many have also learned the hard way that defense of these systems and the assets they contain continue to remain prone to and the victim of cyberattacks and other security risks.

Webinar Recording
Reduce Dependency on Active Directory With Cloud Identity
Oct 28, 2020
When it comes to identity management many companies depend heavily on Microsoft Active Directory (AD). This high degree of dependency on one service can become a problem when this service faces an outage. Also, respective of the requirements companies have, all services have certain limitations which are sometimes necessary to overcome. Many cyberattacks are perpetrated via staff endpoint devices (computers, smartphones or even printers). This necessitates a fine-mesh risk management approach with a centralized solution, called Identity Fabric at KuppingerCole.

Webinar Recording
Policy-Based Access Control – Consistent Across the Enterprise
Oct 15, 2020
The evolution of cybersecurity protection demands a more nuanced response to providing access to a company’s sensitive resources. Policy-based access control (PBAC) combines identity attributes and context variables to enable sophisticated granting of access to corporate systems and protected resources based on centrally managed policies that ensure consistent access control decisions across the enterprise. Advancement in both business requirements and technology (such as growing use of micro-services), require a better way to control access. In a way that is consistent across all silos,...

Webinar Recording
2020 Is the Year of the Identity Management Revolution
Oct 14, 2020
2020 has been the year of dispersed workforces and working environments. The impact on existing infrastructure, strategies and legacy technology has been unprecedented. As a result, we embarked on a revolution for Identity & Access Management and a mind-set change for organizations big and small, global or local. Never before has IAM been more present and upfront. In this new world, trusted identities need to be the starting point for all organizational strategies and driving organizational change.

Webinar Recording
How to Hunt Threats Effectively With Network Detection & Response Solutions
Oct 09, 2020
The number of cyber-attacks globally continue to rise. Attacks are growing increasingly sophisticated. The tactics, techniques and procedures that were once only used by well-funded state actors are being commoditized by cybercriminals. State actors sometimes employ tools that were formerly mostly used by cybercriminals. The threat landscape evolves continuously.

Webinar Recording
Techniques for Securing Transactions With Identity Verification and Verifiable Claims
Oct 08, 2020
Consumer and Workforce identities are under assault. Cybercrime and fraud are pervasive problems that have only escalated during the pandemic. Even as the number of online and mobile transactions increases, businesses, government agencies, and other organizations are actively searching for solutions to help them minimize fraud and other kinds of cybercrime.

Webinar Recording
Multicloud und Digitalisierung: Wie Sie die Nutzung im Griff behalten
Oct 07, 2020
Die Rolle der Cloud für die Digitalisierung kann kaum überbewertet werden. Doch mit zunehmender Cloud-Nutzung sind Organisationen bezüglich der Zugriffskontrolle für Cloud-Plattformen wie AWS, Microsoft Azure und Google Cloud Platform in Verzug geraten. Zwar bieten diese Plattformen Unternehmen Agilität und beschleunigen Innovation durch neue Services wie Sprachverarbeitung oder konfigurierbare Dialogsysteme, doch oft fehlt es an der erforderlichen Kontrolle, um den Zugriff auf all diese Cloud-Ressourcen ordnungsgemäß zu regeln.

Webinar Recording
How Security and Identity Fabrics Work to Help Improve Security
Oct 01, 2020
Many organizations struggle or even fail because they overcomplicate the implementation and extension of their cybersecurity toolset. Most do not have a central approach on security, and often use a set of tools that are not well-integrated with each other.

Webinar Recording
The Evolution of Encryption: Getting Ready for the Quantum Watershed
Sep 30, 2020
The relentless move towards the digital transformation seems unstoppable. Organizations must secure their trust and reputation in the face of increasing attacks, advances in technology, increased regulation and compliance, and the continued shift to the cloud and cloud services. Unfortunately, not a single week goes by without another large-scale data breach or leak reported by the media – it seems that a company of any size or industry can fall victim to insufficient or ineffective data protection controls.

Webinar Recording
The Role of Data-Centric Security in the Cloud
Sep 29, 2020
As modern businesses across all verticals continue their rapid digitalization, the need to store, process and exchange data securely is becoming an essential factor for any company. However, this is particularly challenging for high-tech companies dealing with highly-sensitive R&D data.

Webinar Recording
Application Access Governance for SAP Environments and Beyond
Sep 25, 2020
For many enterprises, SAP systems are an essential part of their corporate IT infrastructure, storing critical business information and employee data. SAP systems have traditionally been a major focus area for auditors. It is therefore essential that all existing SAP systems are covered by an effective solution for managing risks, including managing access controls and SoD controls, and implementing adequate Access Governance.

Webinar Recording
Seamless Connectivity: Why You Need It and How to Get It Right
Sep 24, 2020
Businesses are increasingly embracing new technologies to enhance existing processes and enable new business models and revenue streams through Digital Transformation. Service-based business IT, however, is not without challenges, particularly around access governance and control. Digital Transformation is all about enabling everyone and everything to connect seamlessly to new digital services, to facilitate value exchange while still ensuring regulatory compliance, faster product innovation, secure remote working capabilities, and multi-channel consumer access despite ever-tightening budgets.

Webinar Recording
Information Protection in Cloud Services
Sep 23, 2020
Today’s economy is clearly driven by data. The most successful companies are those that can use this data to create useful information that enables them to get closer to their customers, to create new products and be more efficient. Cloud services are a key enabler in this, they allow the capture, storage, and exploitation of vast amounts of data without the need for capital expenditure. They enable the rapid development and deployment of new applications as well as the modernization of existing one.

Webinar Recording
In an Age of Digital Transformation Managing Vendor and Partner Identity Is Critical
Sep 18, 2020
Organizations have been managing the identity and access of employees for many years to protect data and the overall security of the enterprise. However, the onset of digital transformation has driven a need for faster, cost-effective innovation and with it the increased utilization of third-party resources. Consequently, organizations have a greater need to manage third-party access to data, systems, and facilities. This includes contractors, vendors but also partners, affiliates, volunteers, and even service accounts and bots. Modern organizations are much more collaborative and open...

Webinar Recording
Zugriffsschutz für sensible Daten – mit Data Access Governance und Identity Governance
Sep 17, 2020
Ein Großteil der geschäftlichen Dokumente in Unternehmen ist in Dateiordnern auf Microsoft SharePoint, Box, Dropbox und Google Drive gespeichert. Da ist es keine Überraschung, dass diese Daten zu den neuen Zielen von Hackern geworden sind. Mit zunehmenden Compliance-Anforderungen wie DSGVO, TISAX oder PCI ist der Zugriffsschutz auf diese Dateien längst nicht mehr nur eine Option, sondern Vorschrift. Auch die Erfüllung der Vorgaben der ISO 270xx-Normen ebenso wie von KRITIS erfordert entsprechende Maßnahmen.

Webinar Recording
The Fast Track to Optimized Operations With IAM-as-a-Service
Sep 15, 2020
When IAM projects stall it is usually due to budget or timeline constraints as well as a lack of automation that can be leveraged by operations team to accelerate IAM processes and IAM modernization. Also, IAM operations and administration teams are often too busy with low-value tasks or lack the skills and expertise for rapid planning and implementation of IAM initiatives. In the long run, this puts overall digital initiatives of the company on hold. But the rapidly evolving digital landscape requires IAM teams to be productive and agile.

Webinar Recording
Die Demokratisierung der Cybersicherheit
Sep 11, 2020
Im Laufe der vergangenen Jahrzehnte haben Unternehmen vielen Anstrengungen auf sich genommen, um ihre IT-Sicherheit zu verbessern und so ihre Daten und Netzwerke zu schützen. Eine Konsequenz daraus wird immer deutlicher sichtbar: CISOs und ihre Teams müssen sich um eine (zu) große Zahl an Produkten und Lösungen kümmern, die der Unternehmenssicherheit dienen sollen. Oft sorgt schon die schiere Masse an Lösungen für eine hohe Komplexität und jährlich steigende Gesamtbetriebskosten (TCO), wobei der Mehrwert für die Sicherheit durch eine immer höhere Zahl an Tools fraglich ist.

Webinar Recording
Identity for All – Not for the Few
Sep 10, 2020
While digitalization is a major challenge for all kinds of enterprises, it is particularly hard for medium sized enterprises. For many years, medium sized enterprises have struggled to deploy Identity Management as well as Identity Governance (IGA) solutions and show true business value and a return on investment. This is largely due to the complexity of implementation and the level of configuration and customization to fulfill the requirements. As a result, many companies have deployed Access Management solutions like single sign-on only to find that while great for user convenience, they...

Webinar Recording
Identity and Access Management Strategies That Grow With Your Business
Sep 10, 2020
For companies that don’t need a complex Identity Governance & Administration solution (IGA), account and group administration is still a priority. Every company needs a solution for at least baseline IAM (Identity and Access Management), that fits their current state but can also equip them to expand to Identity Governance and Privileged Access Management (PAM) when they are ready.

Webinar Recording
Remote Workforce: How to Protect Yourself From Emerging Threats?
Sep 03, 2020
The outbreak of the COVID-19 pandemic has served as a catalyst for digitization in many companies and led to an increase in remote work and adoption of the bring your own device (BYOD) policy. Every device and digital service that employees use is a potential gateway into company networks and thus poses a security risk. The risks are magnified even more when privileged accounts enter the equation because they enable access to critical data. Given the immediacy and speed with which companies had to shift from office to remote work, security concerns were often neglected leading to an...

Webinar Recording
Designing and Establishing a Mature PAM Ecosystem for Reducing Risk in Your Organisation
Sep 02, 2020
What makes a PAM strategy different from enterprise password management or Identity Access Management? What are the first actions you should take to protect your privileged accounts in the shortest amount of time? And, how has the definition of “PAM Basics” changed as the industry and cyber risks have evolved?

Webinar Recording
The 3 Steps to Secure IAM Modernization
Aug 26, 2020
When organizations modernize their Identity and Access Management (IAM), they have three fundamental requirements: an understanding of current capabilities, a migration strategy to transform the IAM infrastructure and finally, the staff with the expertise to execute the plan. The challenges on the way from legacy IAM to a modern IAM infrastructure are manifold and should be considered beforehand.

Webinar Recording
Four Key Components Critical to the Future of Privileged Access Management
Aug 06, 2020
Privileged Access Management (PAM) has assumed a critical role in protecting the most valuable data and services within organizations from theft, loss, and unauthorized access. But as companies and other organizations have become more complex and embrace digital transformation, PAM is also taking on a core operational function to achieve better insight into data usage and contribute to agile working processes.

Webinar Recording
We Need to Talk About Passwords – Urgently!
Jul 29, 2020
Passwords have been used for authentication for decades and continue to proliferate. Yet we know they create friction for users, slow down business productivity, and are a weak form of user authentication. Users are always forgetting them or use weak passwords that are easily cracked by hackers. Many organizations would love to lessen reliance on passwords but many passwordless solutions only provide a partial solution and do not solve the inherent weakness of passwords. Modern enterprises cannot cover the myriad of access use cases today with a passwordless solution alone.

Webinar Recording
Remote Work and IAM – A Unique Opportunity for Security Leaders
Jul 27, 2020
Nowadays, Identity and Access Management (IAM) is undeniably the first line of defense for organizations worldwide. It enables employees to securely access applications while enhancing control and transparency. But IAM is also on the change. It is already more than just the traditional employee IAM. Digital business requires advanced identity services, well beyond the human identities.

Webinar Recording
Security Fabric: Building a Secure Future With a Flexible IT Architecture
Jul 23, 2020
IT security is of central importance to companies. There are many requirements that must be met so that users with different roles and rights can use the various computers and networks securely and efficiently.

Webinar Recording
Endpoint Protection Made Easy With Privilege Management
Jul 16, 2020
Endpoint detection and response (EDR) solutions monitor endpoint and network events and record the information in a central database. There, the information is subjected to further analysis, detection, investigation, reporting, and alerting. While EDR solutions may be a good start to protect endpoints, they are by no means sufficient. Instead, Endpoint Privilege Management (EPM) solutions must be integrated to protect the systems from within.

Webinar Recording
Working From Home Is Not Secure Without an Effective IAM
Jul 10, 2020
The past few months have not only been disruptive to business models, but also to the way many people work. Working from Home (WfH) is the new normal for many of us, but it comes with many challenges, for workers, for their managers, for the IT teams. One of the biggest challenges is finding the right balance between enabling WfH and security.

Webinar Recording
Identity Für Alle – Nicht Nur Für Wenige: Identity Management Für Den Mittelstand
Jul 03, 2020
Die digitale Transformation ist eine globale Herausforderung für Unternehmen jeder Größe. Im Gegensatz zu großen Konzernen fehlt es kleinen und mittelständischen Unternehmen aber oft an Fachpersonal und finanziellen Ressourcen, um Transformationsprozessen und den notwendigen technischen Voraussetzungen ausreichend Aufmerksamkeit zu widmen.

Webinar Recording
Workforce Continuity in a Time of Crisis
Jul 01, 2020
It is not only in times of crisis like the current coronavirus pandemic that companies need to adapt and respond quickly to changing circumstances to provide workers with remote access and deal with onboarding and deprovisioning contingent workers.

Webinar Recording
Minimizing Security Impacts of a Growing Remote Workforce
Jun 26, 2020
Many organisations are implementing remote working policies and need to quickly support an unprecedented increase in the number of remote employees.

Webinar Recording
Agile GRC: Adapting to the Pace of Change in the Digital Era
Jun 24, 2020
In the digital era, the rapid rate of change in business, IT and regulatory environments is continually accelerating, making it extremely challenging for organizations to keep pace in terms of their governance, risk and compliance (GRC) capability without the right mindset and tools.

Webinar Recording
The Future of Privileged Access Management and Reducing Risk for Modern Digital Enterprises
Jun 19, 2020
While Privileged Access Management (PAM) must still fulfill its core function of protecting privileged accounts, the next generation of PAM solutions can do so much more for your organization. As organizations embrace cloud, hybrid-IT, DevOps, remote working, digital workplaces, RPA and other transformational technologies the role of PAM has changed to secure these trends at zero point. Privileged accounts are no longer the domain of administrators or super users but for users right across the organization – including non-human entities such as applications and machines.

Webinar Recording
Gain a Unified Business View With Enterprise Identity Management
Jun 18, 2020
Identity Governance and Administration (IGA) is continuing to evolve through more integrated Identity and Access Governance solutions. IGA products are often required to give deep integrations with other enterprise products and applications to deliver the expected business value, as well as a need for having one interface for IGA across the range of applications and services.

Webinar Recording
Redefining IAM: Harnessing AI to Identify Risk at the Speed of Change
May 29, 2020
In an increasingly complex and rapidly changing business, IT and regulatory environment, traditional approaches to identity governance must evolve to keep up with the rate of change. Given the dynamic nature of today’s business, managing entitlements and conducting access reviews have become particularly challenging, for example.

Webinar Recording
Protect, Detect, Respond, Mitigate: A Modern Security Paradigm for Modern Enterprises
May 27, 2020
The Antivirus has been proclaimed dead years ago – you’ve probably heard those stories many times. But did you realize that the EDR (Endpoint Detection and Response), which was once supposed to address all its shortcomings, isn’t doing well either? After all, with the sheer number and complexity of modern cyber threats, what’s the point of detecting each one if you have neither time nor qualified manpower to analyze and mitigate them before they turn into major disruptions?

Webinar Recording
Beating Fraudsters at Their Own Game With Fraud Reduction Intelligence Platforms
May 14, 2020
Fraud continues to be a major challenge for many organizations today. Industries such as finance, banks, payments, insurance, gaming, telecommunications, health care, etc. are dealing with increasing amounts of fraud and escalating sophistication of attacks. Account Takeovers (ATOs), synthetic fraud, and bots are a pervasive problem and continue to drain revenue from many businesses.

Webinar Recording
Digital Identities & Healthcare IAM: Balancing Efficiency in Clinical Workflows and the Need for Security & Privacy
May 08, 2020
IAM infrastructure is becoming increasingly critical to the business success of healthcare providers. This is driven in the first instance by digitization and connectivity of everything and the inevitable efforts of cyber-criminals to compromise the newly connected assets. At the same time, and especially in sectors like healthcare, whose business is based on the collection and use of lots of valuable consumer data, the public and governments are demanding more accountability for safeguarding and appropriate use of personal information.

Webinar Recording
Access all Apps with Azure AD: A Single Identity Solution for Secure Access
Apr 30, 2020
Most businesses already rely on Azure Active Directory for secure, seamless access to Microsoft services like Office 365 and Azure. But with more applications being used than ever before, organizations are asking themselves what bigger role Azure Active Directory can play in securing their entire application ecosystem.

Webinar Recording
The Security & Identity Challenges of Modern IT: Agile IT & DevOps Done Right & Secure
Apr 29, 2020
Security and identity must evolve in order to support today’s IT. While traditional IT appears being rather simple to secure, current security risks necessitate a greater degree of agility: shifting to DevOps paradigms, implementing a CI/CD chain, running services in hybrid cloud environments (or wherever else). This requires a security angle on DevOps, which you might name DevSecOps.

Webinar Recording
Managing a Crisis: Prepare for Weathering the Next Storm to Come
Apr 24, 2020
While the Covid-19 crisis is still in full effect, many businesses have mastered the first phase of disruption. Now, the time starts to plan for the future, at many levels – financials, business models, product strategies, and more.

Webinar Recording
Die Krise bewältigen: So überstehen Sie den nächsten Sturm
Apr 23, 2020
Während die Covid-19-Krise noch in vollem Gange ist, haben viele Unternehmen die erste Phase des Umbruchs gemeistert. Jetzt ist es an der Zeit, auf vielen Ebenen – Finanzen, Geschäftsmodelle, Produktstrategien und mehr – für die Zukunft zu planen.

Webinar Recording
AI Governance From a Practical Perspective
Apr 21, 2020
How can you ensure that your Artificial Intelligence project does not become a liability? An improper implementation, a socially insensitive data label, or negligent data management can easily lead to an auditing nightmare. What are the best practices to safely utilize and govern AI?

Webinar Recording
A Compass for Choosing the Right Fraud Reduction Intelligence Platform
Apr 17, 2020
Companies are turning to Fraud Reduction Intelligence Platforms to reduce account takeover (ATO), synthetic fraud, bots, and other forms of fraud, which continue to be a pervasive and revenue-draining problem across many industries.

Webinar Recording
Data Sovereignty in Public Clouds
Mar 27, 2020
Just a few years ago, IT infrastructures resembled medieval fortresses: Firewalls, intrusion prevention systems and anti-virus programs were supposed to ward off attacks even before the attacker could enter.

Webinar Recording
The Perils of Today’s Approach on Access Governance: Start Protecting Data at Source
Mar 11, 2020
Protecting sensitive, valuable data is a must for every organization. Ever-increasing cyber-attacks and ever-tightening regulations mandate businesses to take action. Unfortunately, the common approaches of IGA (Identity Governance and Administration) that focus on managing static entitlements for systems and applications fall short in really securing the data at risk. They fail in managing data in motion. They are static. They don’t manage the usage of data well. Not to speak of all the challenges in role management projects and around regular access reviews.

Webinar Recording
What Does the Future Hold for Passwordless Authentication and Zero Trust?
Mar 06, 2020
Enterprises of all types face a growing number of cyber threats today. Studies show that most data breaches begin with compromised passwords. Moreover, password management is expensive and not user-friendly. Enterprise workforce users are driving the consumerization of IT. They want the same kind of flexibility and ease-of-use from the authentication systems at work that they use at home; often, this means using mobile devices.

Webinar Recording
Solving Problems in Privileged Access Management with Automation
Mar 04, 2020
While businesses race ahead with digital transformation, security and identity management are often being left behind. The complexity of modern organizations of all sizes has undermined the traditional concepts of privileged access management (PAM) and privileged account usage. Help desks and IT security teams are often too busy and understaffed to be able to give PAM the attention it deserves.

Webinar Recording
Holen Sie sich das SIEM, das Sie schon immer wollten: intelligent, automatisiert, mit unbegrenzter Kapazität
Feb 18, 2020
Vor 15 Jahren wurden Security-Information-and-Event-Management-Produkte (SIEM) als die ultimative Lösung für alle Sicherheitsprobleme in Unternehmen gefeiert, und das nicht ohne Grund: Schließlich ist die zentrale Erfassung und Verwaltung sicherheitsrelevanter Daten über alle IT-Systeme eines Unternehmens hinweg eine wichtige Voraussetzung für eine schnelle Analyse und Reaktion auf Cyber-Bedrohungen.

Webinar Recording
Cybersecurity Trends and Challenges 2020
Feb 03, 2020
Digitalization evolves with the increased use of microcomputers in everyday objects like cars and smart fridges, but also in industrial applications. Therefore, communication between devices is growing accordingly. While connecting devices is supposed to make our lives easier, it poses a great challenge from a security standpoint. Every connection opens a potential backdoor for attackers to slip inside your network.

Webinar Recording
Improve Security With Critical Infrastructures Requirements
Jan 24, 2020
Organizations or institutions that are essential for the public are called Critical Infrastructures (KRITIS = “Kritische Infrastrukturen”). As such, they are subject to comprehensive and strict legal regimes consisting of laws and regulations.

Webinar Recording
API Management and Security: Don’t Trade Protection for Convenience
Jan 17, 2020
Once a purely technical concept created to make developers’ lives easier, Application Programming Interfaces (APIs) have evolved into one of the foundations of modern digital business. As companies are struggling to maintain their business agility, to react to the ever-changing market demands and technology landscapes, the need to deliver a new application or service to customers as quickly as possible often trumps all other considerations.

Webinar Recording
Upgrade your IAM with IDaaS IGA
Dec 18, 2019
The Identity-as-a-Service (IDaaS) market continues to develop with a significant push from organizations looking to adopt cloud-based delivery of security services including IAM. While IDaaS Access Management solutions, providing SSO (Single Sign-On) for the users and access to a variety of services are already established, IDaaS IGA is not as widely used yet. However, shifting IGA (Identity Governance and Administration) capabilities, e.g. Identity Lifecycle Management and Access Governance, to the cloud might provide significant benefits regarding time and cost of deploying and operating...

Webinar Recording
Identity Fabrics for True Digital Transformation
Dec 11, 2019
Business models are changing, customer relationships are changing, and business partnerships are far more volatile than ever before. Workloads are shifting to the cloud and to as-a-service models. Businesses are looking to provide more and more digital services to their customers and consumers via apps and integrate with devices and things. Digital Identity is at the center of these digital transformations.

Webinar Recording
Extending Beyond the Limits of Multi-Factor Authentication With Continuous Adaptive Trust
Dec 04, 2019
The Identity and Access Management (IAM) market is undergoing rapid and at times transformative change. A steady progression from on-premises to API and cloud platforms is visible as vendors innovate, but authentication tools are under attack from determined adversaries.

Webinar Recording
On the Way to Becoming a Cognitive Enterprise
Dec 03, 2019
The digitalization has resulted in the "digital enterprise". It aims at leveraging previously unused data and the information hidden in it for the benefit of the enterprise. The “cognitive enterprise” comes with the promise to use this information to do something productive, profitable and highly innovative for the enterprise. The cognitive enterprise is the application of cognitive technologies in critical areas of a company.

Webinar Recording
Fighting Fraud With Strong Authentication
Nov 25, 2019
Strong authentication is one cornerstone of web security. However, account enrollment and account recovery processes are leaving gaps in the credential management lifecycle that allow bad actors to perform account takeover and get into our networks. Increasingly, these bad actors aren’t even real. Stolen identity information that is used to create new fake IDs, known as synthetic identity fraud, is a fast-growing form of fraud.

Webinar Recording
6 Myths of Privileged Access Management Busted
Nov 20, 2019
Industry thought leaders have stated that if there is only one project you can tackle to improve the security of your organization it should be Privileged Access Management (PAM). But successfully securing and managing privileged access is a tough task and is only getting harder to solve.

Webinar Recording
Legacy IAM System vs. Modern IAM Platforms - Should You Stay or Should You Go?
Nov 08, 2019
Application and infrastructure architectures are continuously changing in order to mirror the demands and challenges of organizational needs. A common problem with legacy systems is the inability to understand and adapt to the new business models in an ever-changing world.

Webinar Recording
KuppingerCole Identifies Leaders in Consumer Authentication
Nov 07, 2019
Password-based authentication is insecure, leads to a poor customer experience, and is costly for businesses to maintain. Knowledge-based authentication, often used for password resets, is even more insecure given that the answers to individuals’ security questions are often found online. Consumer-facing online businesses are looking for stronger authentication options to reduce the risk of fraud and provide more pleasant user experiences.

Webinar Recording
Getting a Grip on Your AI: Know What It Does. Understand the Risks and Rewards. Be Compliant
Nov 05, 2019
The case for integrating AI into business processes is ever stronger. Now it’s time to assess realistically what it can do for you. Existing successes and failures of AI beta-phase testing show how to resist the survivorship bias when implementing your own AI programs. Clarify the characteristics of AI data that may be problematic, and discover where investment should be concentrated on further customizing your AI solutions.

Webinar Recording
Complying With PSD2: Everything You Need to Know
Oct 30, 2019
With the Revised Payment Service Directive (PSD2) coming into full effect this fall, banks and online retailers need to adapt to changes that carry with them many regulatory and technical challenges. Acknowledging these extensive changes, Germany’s Federal Financial Supervisory Authority (BaFin) recently granted a period of grace for online retailers to implement the element of strong customer authentication (SCA), thus following the lead of other European financial regulatory authorities.

Webinar Recording
KuppingerCole’s Evaluation of Leading Vendors in the Identity API Platforms Market
Oct 24, 2019
Many different factors are driving Digital Transformation in the market today. One factor is the change in how businesses interact with their customers. Another factor is more on the technical side that addresses the implementation of new Digital Services that have become more complex due to the different environments and the many integration points to consider.

Webinar Recording
Facilitating Business with State-of-the-Art Identity Proofing Solutions
Oct 18, 2019
For traditional or Business-to-Employee (B2E) IAM, HR departments are responsible for gathering documentation from employees to determine their suitability for employment. For Business-to-Consumer (B2C) or CIAM, identity proofing can be more difficult. Depending on the nature of the business, the attributes that need to be collected and verified can differ widely. For example, Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations govern the kinds of attributes and authoritative attributes that must be collected in the finance industry.

Webinar Recording
Onboarding Your Business Partners to Your Services: B2B IAM in Practice
Oct 11, 2019
Virtually any business needs to grant business partners access to certain IT services. While employee IAM is a well-established discipline, where HR frequently delivers the information about joiners, movers, and leavers, and while Consumer IAM (CIAM) commonly relies on self-registration, B2B IAM comes with different challenges.

Webinar Recording
How Leading Brands Build Trust With CIAM
Oct 02, 2019
In the age of digital transformation, consumers tend to have multiple digital identities across several devices deploying a variety of services. In this environment, digital trust is what sets brands apart from their competitors. Taking and storing customer data is a duty of care, and brands cannot afford data breaches or compromises.

Webinar Recording
Cybersecurity Budgeting 2020: Set Your Priorities Right
Sep 26, 2019
For the majority of businesses, the budgeting season is about to start. Some are done, some will be later, if the fiscal year differs from the calendar year. But usually, in September and October, this process is kicked off.

Webinar Recording
The Compelling Case for Risk-Based Adaptive Authentication
Sep 25, 2019
Consumers and employees are increasingly on-the-go, and that means that more transactions and more work originates from the mobile phone. Fraud and data loss rates have also been rising. A plethora of mobile-based digital identity technologies have entered the market over the last few years to help businesses and other organization meet these challenges.

Webinar Recording
The Globalization of IAM for Manufacturing Businesses
Sep 18, 2019
Globalization has given many companies the opportunity to run factories and other operations in various countries. In doing so, manufacturers are faced with challenging regulations they have to comply with and that may differ in the U.S., EMEA, Russia, China, and other countries. IAM is an essential element for operating business, when it comes to employees, business partners such as suppliers, and customers.

Webinar Recording
How to Stop Attacker Movement in Your Network Before They Reach your “Crown Jewels”
Sep 12, 2019
Nearly all high-impact cyberattacks have a phase in which the attacker must conduct lateral movement from their initial landing point to their ultimate target. To do this, the attacker needs a combination of credentials and available connections between one system and another. This is the evasive process of “living off the land” using the connectivity native to the organization.

Webinar Recording
Regaining Control With IGA Solutions
Sep 11, 2019
Role management remains a pivotal challenge in many companies. Regulations (such as BAIT and VAIT in Germany) require companies not only to implement an IGA solution (Identity Governance & Administration), but also a uniform authorization concept and its regular review, including the assignment of access rights to the individual authorized persons.

Webinar Recording
It’s Time to Forget Your Password and Settle for Multi-Factor Authentication
Sep 06, 2019
The majority of security breaches and attacks can be traced back to stolen and compromised passwords. Mobile devices are often particularly vulnerable because many users tend to avoid long passwords and special characters.

Webinar Recording
KuppingerCole’s Evaluation of Leading Vendors in the IDaaS Access Management Market
Sep 04, 2019
Identity-as-a-Service Access Management (IDaaS AM) has emerged as one of the fastest-growing markets of IAM, characterized by cloud-based delivery of traditional IAM services. KuppingerCole estimates the global IDaaS market will continue to grow at a CAGR of 24% in 2019.

Webinar Recording
Privileged Access Management Needs a New Approach
Jul 17, 2019
As organizations accelerate their digitalization efforts to stay relevant and competitive in the marketplace, they must evaluate and embrace technologies that can not only support the enablement of their digitalization efforts but can also support the speed, scale and security required for such digitalization efforts.

Webinar Recording
The Passwordless Enterprise: Building A Long-Term Zero Trust Strategy
Jul 12, 2019
“The password is dead.” We have heard this statement for at least a decade, yet even in 2019, data breaches based on stolen user credentials continue to dominate the headlines. Why do passwords so stubbornly refuse to die?

Webinar Recording
Security in the Age of the Hybrid Multi Cloud Environment
Jul 05, 2019
The way is clear for the hybrid multi-cloud environment! With an increase in cloud services, the mitigation of cyber risks within such environments becomes paramount. The value of traditional security tools for cloud applications is very limited and the misconfiguration of cloud platforms is a key threat to their security.

Webinar Recording
Challenges for Managed Service Providers Offering Privileged Account Management as a Service
Jul 03, 2019
Insufficiently protected privileged accounts pose high risks to any given company today. Therefore, Privileged Account Management (PAM) is of paramount importance to a functional insider threat program, which is at the core of any modern cybersecurity strategy. While utilizing a variety of IaaS, PaaS and SaaS offerings, organizations often face difficulties in controlling the management of their privileged accounts due to a lack of time, budget and other resources.

Webinar Recording
Under Pressure From the Auditor: Rapid Response by Rapid Access Reviews
Jun 28, 2019
Most organizations are aching under the pressure the feel from auditors in delivering information. A large portion of that is based on access reviews, i.e. demonstrating that the least privilege principle and related regulatory requirements are met.

Webinar Recording
Mit Access-Governance-Projekten neue Vorschriften erfüllen, ohne das Rad neu zu erfinden
Jun 27, 2019
IGA-Projekte (Identity Governance & Administration) bergen aufgrund ihrer Komplexität diverse Risiken. Diese ergeben sich meistens in der Vernetzung einer komplexen, heterogenen IT-Infrastruktur sowie durch den bereichsübergreifenden Charakter von IGA-Projekten. Wenn man nicht bei jedem Projekt immer wieder von Null anfangen möchte, und auf Erfahrungswerte zurückgreift, können viele Risiken sehr leicht vermieden werden.

Webinar Recording
The Dark Side of the API Economy
Jun 25, 2019
In a single decade, Application Programming Interfaces (APIs) have evolved from a purely technical concept into one of the foundations of modern digital business, delivering operational efficiency, scalability and profitability to companies from various industries. Nowadays, everything is API-enabled: corporate data is the product and APIs are the logistics of delivering it to customers and partners.

Webinar Recording
Getting Rid of the Password – How to Increase Safety Affordably
Jun 19, 2019
Despite compromised passwords being the leading cause of data breaches, most online businesses still rely on solely using passwords for logins. While getting rid of password authentication is desirable from a security standpoint, organizations fear that it is a costly endeavor that can also affect user experience.

Webinar Recording
Fine-Tuning ICS Threat Models to Prioritize Mitigations of the Most Vulnerable Devices
Jun 14, 2019
When discussing the matters of industrial cybersecurity with IT experts, lamenting the historical divide between OT and IT seems to be a popular topic: you would often hear that the OT engineers are stubbornly ignoring the latest cyberthreats and do not see security as a priority in general.

Webinar Recording
Leverage Enterprise Architecture to Achieve GDPR Compliance
Jun 06, 2019
Several measures have been undertaken by Organizations at various levels to comply with GDPR, most of which remain reactive, fragmented and largely ad-hoc. These controls are also not continuous in nature and therefore fail to satisfy ongoing compliance requirements. Organizational leaders (CISOs, CIOs, CDPOs or CROs) felt the need for better data controls that should be baked into organizational processes to ensure compliance by design.

Webinar Recording
The Compelling Need for Privileged IT Process Automation
May 31, 2019
IT processes can often be repetitive and many of these tasks can take companies a lot of time and costs, putting pressure on highly skilled IT staff. By automating IT processes, companies can not only become more productive and efficient but also relieve the load on their IT department.

Webinar Recording
All the Roads Lead to the C, Paved with B2B
May 29, 2019
More and more organizations use CIAM for B2B use cases as such combination can help companies position themselves on the market. While no one argues that user experience journey for the B2B Customer is just as important as any other customer, they most certainly need a relatively different set of features.

Webinar Recording
Is Multilayered Cyber-Defense Out Already? Against Rising Breaches and Vulnerabilities, Data-Centric Security to the Rescue!
May 24, 2019
As the growing number of high-profile data breaches indicates, even the largest companies are still struggling with implementing consistent enterprise-wide information security measures. Setting up various security tools for numerous different applications, services, and heterogeneous systems and then making them work together efficiently is a massive challenge.

Webinar Recording
The No. 1 Rule of Secure Cloud Migration: Know Your Unstructured and Dark Data and Where It Is Located
May 22, 2019
With a huge amount of data around, cloud migration is the ideal solution today. A necessary stage in migrating data to the cloud is putting it in order. This is particularly important when it comes to unstructured, so-called dark data: files and documents that are undermanaged (excel files of budget estimates, PDFs containing important patents, Word documents containing personal employee or customer information), in general the data that is not managed in an orderly fashion such as structured database which is easily governed. Usually, this kind of data that tends to be misplaced, misused,...

Webinar Recording
Next-Gen Identity Analytics and Access Governance Approach
May 10, 2019
Identity Governance and Administration (IGA) is undoubtedly one of the most valued but complex and lengthy technology implementations. While IAM leaders are still trying to figure out the complexities of IGA, the massive cloud uptake with the advent of machine learning accelerates identity analytics and access governance for creation of Next-Gen IGA solutions. Machine Learning inspired IGA offers significant improvements to enhance identity analytics and access governance processes to enable IAM leaders support the business better by helping them make more informed decisions.

Webinar Recording
Identity Governance - the Value of Leveraging IGA Functions from the Cloud
May 08, 2019
Even though companies need to implement Identity Governance & Administration (IGA) solutions in order to stay compliant and support their security, the deployment of IGA solutions still poses a challenge to many of them. Delivering a frictionless experience for users and employees while efficiently managing identities and access entitlements are key to a successful deployment.

Webinar Recording
Artificial Intelligence: Disruption Ahead?
May 03, 2019
When AI comes to mind, many people, maybe in Europe a bit more than in other parts of the world, fear some kind of terrestrial robot overlords taking over control, forcing us humans to surrender and devote our freedom to their understanding of a well-organized society without all those things that make our lives worth living.

Webinar Recording
Adding Depth to Your IAM: Automating Microsoft Active Directory and Azure AD Administration
May 02, 2019
IAM and therein IGA (Identity Governance & Administration) focuses on managing identities and their access across a variety of systems.

Webinar Recording
Secure Login for Highly-Regulated Hybrid Environments: Avoid Being Forced Into the Cloud
Apr 26, 2019
The march of the cloud is unstoppable. Eager to outsource the tedious and expensive maintenance of their IT infrastructures to a reliable 3rd party, most companies would dream of becoming cloud-native, at least in the long term. Needless to say, letting someone else run your identity management out there sounds like a great idea as well, hence the rising popularity of Identity-as-a-Service solutions that combine the latest technology achievements with the flexibility of the cloud.

Webinar Recording
The Fast Track to Regulatory Compliance: Lean, Efficient, and User-Centric Access Governance
Apr 10, 2019
Various regulations mandate businesses not only to implement an IGA (Identity Governance & Administration) solution, but as part of that to regularly review their access entitlements across the entire IT landscape, starting with an initial clean-up. This can result in complex projects with multi-year initiatives on defining business roles and cumbersome access review (recertification) processes, which annoy the business users. Factually, such approaches even might fail in fulfilling the regulatory requirements, just because they never get done and used.

Webinar Recording
The Foundation for GDPR Compliance and PI/PII Protection: Understand Where Data Resides and Who Processes It
Apr 03, 2019
The EU GDPR requires covered organizations to be able to account for and document how personal data is collected, processed and shared. What many companies often fail to realize is that this data is not only stored in specialized and appropriately secured silos such as databases. In fact, the vast majority of their business information is in unstructured and semi-structured formats, distributed across multiple systems an services. Without consistent visibility into whose data is processed across these environments, organizations cannot adequately account for how personal data is processed...

Webinar Recording
Privileged Access Management - the Focal Point for Your IAM Today
Mar 28, 2019
PAM (Privileged Access Management) has grown over these years to become a crucial set of technologies that addresses some urgent cybersecurity issues today.

Webinar Recording
Mitigate Identity-Related Breaches in the Era of Digital Transformation
Mar 22, 2019
Cyber attackers continue to be successful in gaining access to many different organizations, often by exploiting identities and weak authentication. To ensure they are protected, organizations should consider modern Adaptive Authentication techniques to increase identity security and thwart attacks.

Webinar Recording
API Security: Separating Truth from Fiction
Mar 15, 2019
APIs (application programming interfaces) have undergone a truly amazing transformation in recent years. From an obscure technical term only software developers were familiar with, they have developed into one of the foundations of today’s digital business. Nowadays, APIs are everywhere – they enable business communications with partners and customers, make applications from different vendors work together seamlessly, power large IoT networks and the whole cloud. For many companies, APIs have even become the very foundation of their business models and the primary source of income.

Webinar Recording
CCPA vs. GDPR: An Overview on Similarities and Differences
Feb 14, 2019
Over the last few years, the world has witnessed an increasing number of data breaches involving the credentials and PII of employees, citizens, and consumers. We've all experienced breach fatigue and/or been impacted by these losses.

Webinar Recording
IDaaS: Your Identity Fabric. Connecting Every User to Every Service, Seamlessly
Jan 30, 2019
Making your service available to everyone, everywhere, without losing control. On their digital journey, businesses are constantly launching new digital services, chased by competitive and innovative pressure.

Webinar Recording
Solving New Authentication Challenges While Finding Parity Between User Experience and Security
Jan 16, 2019
In an increasingly hostile world, where you don't know who to trust, companies still need to be able to deliver trusted, personalized experiences for users, without making them jump through hoops to prove who they are.

Webinar Recording
Online Forms Are Out of Date – There Are New Ways to Sign Up Customers
Dec 20, 2018
An extreme lack of innovation has led to online forms dominating online buying for over two decades. The latest identity platforms use fast, easy, and secure technology to streamline customer sign-ups and simplify data.

Webinar Recording
Five Steps to Building an Effective Insider Threat Program
Dec 14, 2018
The greatest cybersecurity threat an organization faces is no longer the malicious outsider hacking from beyond network firewalls. It is the insiders - the contractors, third-party vendors, and even your own privileged employees who already have full access to your company's systems and sensitive data. Any of those can cause substantial damage to your business by leaking confidential information, disrupting access to a critical system or simply draining your bank account. The most privileged users in this regard are no longer the IT administrators, but the CEO or CFO, and the number of new...

Webinar Recording
The Power of Identity Context: How to Get the Right Context and How AI will Help
Dec 12, 2018
How did the phrase “Russian trolls” manage to take over the news? If anyone knew at the time that these were not actually American citizens, they would have had no power to influence. That’s what a lack of identity context will do to you.

Webinar Recording
Modern Endpoint Protection – Automating Prevention, Detection, and Response
Dec 07, 2018
“Antivirus is dead!” - we’ve heard talks like this for years. Some experts would point out that traditional signature-based products cannot detect zero-day attacks or sophisticated advanced threats. Others would even recommend getting rid of any 3rd party antimalware products because the one built into Windows is good enough. But can we really take these claims at face value?

Webinar Recording
Security vs. Innovation: Why Not Choose Both?
Dec 05, 2018
In a world where businesses compete and succeed on the basis of application-driven innovation, enterprises are challenged to deliver software to market faster than ever before. Simultaneously, they're grappling with insider and outsider cybersecurity threats, as well as stringent data privacy regulations such as GDPR.

Webinar Recording
Identity Verification & Authentication Made Easy
Dec 03, 2018
Business is undergoing change. The Digital Transformation affects business models and changes the way businesses interact with their customers. A seamless customer journey is a key success factor for the digital business. This journey starts with attracting the customer and includes steps such as registration, Identity Verification and the authentication of customers when they return.

Webinar Recording
Blockchain ID for the Enterprise: A Single ID? A Good Complement? Or Irrelevant?
Nov 23, 2018
Blockchain and the underlying concept of “Distributed Ledger Technologies” (DLT) have well passed the peak of initial hype. As always, focus is now shifting to real-world applications that allow companies to improve their business. It is less about cryptocurrencies and concepts with a global impact, but more about process and supply chain optimizations as well as better identity (ID) concepts. Blockchain IDs are being heavily discussed as the number of concrete product offerings is increasing in the marketplace. With organizations facing an ever-growing ID problem in their Digital...

Webinar Recording
Zero Trust Reality Check: Secure Access for Hybrid IT
Nov 16, 2018
Workforce mobility and widespread adoption of distributed data center and cloud environments have introduced significant access control complexities and threats. Organizations are questioning the efficacy of conventional, perimeter-based defenses and are now evaluating a “trust but verify” model. What are key enterprise considerations when deploying Zero Trust to enable seamless access, ensure business compliance and mitigate risk?

Webinar Recording
An Overview of the Leadership Compass: Adaptive Authentication and Cloud-Based Multi-Factor Authentication
Nov 09, 2018
KuppingerCole has published two related Leadership Compasses on Adaptive Authentication and Cloud-based Multi-Factor Authentication solutions. We define adaptive authentication (AA) as the on-premises deployments, whereas Cloud-based MFA is SaaS-delivered.

Webinar Recording
How to Handle Consent to Be Compliant With the GDPR and the Upcoming ePrivacy Regulation
Nov 07, 2018
GDPR is here to stay and the new ePrivacy regulation is on the horizon, but many organizations are still not yet in full state of compliance. A core requirement for compliance with GDPR is the concept of “consent,” which is fairly new for most data controllers. Now, with the GDPR regulation in force, parties processing personally identifiable information need to ask the user for his/her consent to do so and let the user revoke that consent any time and as easily as it was given.

Webinar Recording
Fine-Grained Policy-Based Access Control: Why & How?
Oct 19, 2018
Mastering authorization is critical for modern organizations with multiple user constituencies, applications, and data types. Authorization has become a crucial part of security infrastructures and can no longer be considered just another feature of existing IAM solutions. Instead, authorization control infrastructures have developed their own segment in the security market.

Webinar Recording
Assuring and Implementing Cybersecurity and Data Protection for Public Clouds
Oct 17, 2018
Just a few years ago, IT infrastructures resembled medieval fortresses: Firewalls, intrusion prevention systems and anti-virus programs were supposed to ward off attacks even before the enemy could enter.

Webinar Recording
Buying Into Zero Trust? What You Need to Consider to Be Successful
Oct 12, 2018
As organizations take on the digital transformation, trends such as mobility, proliferation of SaaS applications and cloud infrastructure are driving up the number of connected entities and devices increasing the attack surface. With the spate of recent acquisitions in the market looking to change the way we approach security, we need to think beyond the technology and focus on the gaps we need to consider.

Webinar Recording
Customer Identity Access Management (CIAM): Creating the Foundations for User Focused Digital Business, GDPR Compliant
Oct 04, 2018
Digital Business Transformation is a continuous process that affects all areas of doing business, with technology finally getting the right focus: The customer and his/her experience with your business. It is now all about providing that ultimate Frictionless CX (customer experience) so that users don't do that “one-click” towards your competitors.

Webinar Recording
Making Sense of the Top 5 Latest Cybersecurity Trends
Sep 27, 2018
Let’s face it: with each passing year, the CISO’s job is not becoming any easier. As companies continue embracing the Digital Transformation, the growing complexity and openness of their IT infrastructures mean that the attack surface for hackers and malicious insiders is increasing as well. Combined with the recent political developments such as the rise of state-sponsored attacks, new surveillance laws, and harsh privacy regulations, security professionals now have way too many things on their hands that sometimes keep them awake at night.

Webinar Recording
Access Control From an Userbase to Agency Applications in the Education Sector
Sep 26, 2018
The Ministry of Education in New Zealand can now control access from a wide user base to agency applications in the education sector.

Webinar Recording
Digital Identities in the Internet of Things - Securely Manage Devices at Scale
Sep 26, 2018
The Internet of Things is disrupting all industries and use cases; from customer IoT, to Industrial IoT. Companies are forced to become more innovative with their products whilst their services are being, or will be, digitized. Top drivers of this digitization are eroding margins and changing customer behaviour, whereas new market disruptors face security challenges. The question now becomes: where do companies decide to focus their money and efforts, in order to capitalize on this disruption?
Either on business optimization, by doing things better and more efficiently, or focusing on a...

Webinar Recording
Prepare for PSD2 with Strong Customer Authentication, Fraud Risk Management and Open Banking APIs
Sep 13, 2018
Banks will soon have to comply with the Revised Payment Service Directive, commonly called "PSD2." The directive will introduce massive changes to the payments industry and radically alter the user experience for customers of European banks by allowing third party payment service providers (TPP) to access their account information to provide various innovative financial services. But to mitigate risk, banks and TPPs must address the core regulatory technical requirements outlined by PSD2.

Webinar Recording
Consumer Identity & Access Management (CIAM), Big Data and the Internet of Things (IoT)
Sep 12, 2018
It is all about providing your customer a great experience so that they return to you and not to your competitor, who has never before been that close to your business. Anticipating, maybe even in advance, your customer's needs has on the one hand become a must. On the other hand, GDPR is significantly limiting the way how to create such intelligence through collecting personally identifiable data.

Webinar Recording
Privilege Management From the Cloud: Go or No-Go?
Sep 07, 2018
The digital transformation is changing the way we do business, and it is also changing the way we have to keep our increasingly complex IT infrastructure agile and flexible yet secure and compliant. Managing geographically dispersed cloud/hybrid environments and the privileged access to servers and other systems therein is a challenging task.

Webinar Recording
Security and Governance in the Hybrid Multi-Cloud
Sep 05, 2018
Most organizations now use multiple cloud services as well as retaining some IT services on-premises, this multi-cloud hybrid environment creates many challenges for security and governance.

Webinar Recording
Active Directory Disaster Recovery
Jul 13, 2018
Active Directory has grown both in importance and complexity in recent years, with businesses have become increasingly dependent on AD for authentication and authorization of mobile workforce and cloud-based applications. The new AD usage landscape has introduced greater complexity to the enterprise IT environment, raising the risk of AD disasters tied to human error and cyberattack. More and more frequently, attackers are using AD as an attack vector to compromise enterprises and, in some severe cases, wiping out the entire IT environment.

Webinar Recording
Patients, People and Things - Managing Identities in Healthcare
Jul 05, 2018
Digital transformation is a game changer in the health sector and a core requirement is better identity management. The need for improved security in modern medical facilities, the growing reliance on monitoring devices and support for millennials in their health outcome management, all require improved healthcare IAM. This will eliminate administrative expense, implement up-to-date governance and facilitate the exploitation of known trends in healthcare.

Webinar Recording
Securing your Hybrid IT Environment with Privileged Access Management
Jul 02, 2018
As your business grows, so does your IT footprint – both on-premises and in the cloud. This adds to the overall complexity of managing access to the newly acquired IT assets and applications in addition to existing ones. The conventional approaches of managing privileged access using controls native to the individual operating systems, and other internal access policies, are not only cumbersome to manage but add to the security risks in today’s hybrid IT environment.

Webinar Recording
Identity is Security: Avoiding the Pitfalls of an Authentication-Centric Security Architecture
Jun 27, 2018
The security landscape has changed in the recent decade, and the methods we used to protect our enterprise networks are no longer working. The network perimeter has dissipated, the adversary has become increasingly skilled at alternative methods to gain entry, and enterprise applications and data are spread across multiple environments, on-premises and in the cloud. With more sensitive information getting out of our control every day, a data breach is just waiting to occur, and the consequences, if successful, can be disastrous for your business.

Webinar Recording
Closing the Loop Between Audit and Action: Meet Compliance Needs With Privileged Access Management
Jun 27, 2018
Privilege Management has been a key element of both IAM (Identity & Access Management) and cybersecurity programs for years. However, increased complexity of modern corporate IT infrastructures and mounting pressure from compliance regulators force privilege management solutions to constantly expand their scope into new functional areas. From simple password vaults to advanced monitoring and behavior analytics to governance and compliance – a modern PxM solution permeates every corner of your enterprise IT infrastructure.

Webinar Recording
Managing Authentication and Access for Different Identities in Hybrid Environments
Jun 22, 2018
The Digital Transformation is driving enterprises in all geographies and throughout most verticals to become open and connected. These enterprises need to digitally engage with their customers, to technologically empower and mobilize their employees, to optimize their current business processes and to ultimately transform their products. At the same time, large-scale cyberattacks and wrongful exploitation of personal data has reached an all-time high and the associated risks are further increasing.

Webinar Recording
Best Practices of Privileged Identity Management
Jun 21, 2018
Security and risk management leaders need to balance the significant security risks associated with unmanaged privileged access against the administrative and other operational efficiencies achieved by conventional privileged access management practices.

Webinar Recording
Datendiebstahl, Malware, DSGVO - Unstrukturierte Daten Zwischen Kollaboration & Compliance
Jun 19, 2018
Die Mengen an digitalen Daten, die Organisationen nun speichern und verarbeiten müssen, wachsen exponentiell. Dabei geht es nicht nur um die Digitalisierung bestehender Geschäftsprozesse - für viele Unternehmen sind die Daten selbst zum wertvollsten Gut geworden, das sie vor Lecks und unberechtigtem Zugriff schützen müssen.

Webinar Recording
Wie Sie mit der Kombination aus Technologie und Awareness eine zukunftsfähige Cybersecurity-Strategie entwerfen
Jun 15, 2018
Mehr Cyberangriffe, mehr Investitionen – aber zahlt sich das für Ihr Unternehmen aus? Die richtige Cybersecurity-Strategie und die richtigen Tools helfen, Ihre Budgets gezielt einzusetzen, den Erfolg zu messen und insbesondere die Risiken durch die stetig wachsende Zahl von Angriffen und deren immer raffinierteren Methoden zu reduzieren.

Webinar Recording
Cloud IGA: Built for Hybrid Reality
Jun 12, 2018
Conventionally, Identity Governance and Administration (IGA) products have been developed and deployed with a focus on on-premise IT systems and applications. While IAM leaders were still struggling with IGA solutions to deliver effective identity administration and access governance, the move to cloud with a need to support an increasingly mobile workforce has entirely changed the IAM priorities for organizations.

Webinar Recording
Classification - the Intelligent Way to Ensure Strong Data Protection
Jun 12, 2018
As businesses are increasingly embracing the digital transformation, the volumes of information that a typical company has to collect, keep, transport and process is growing exponentially. Massive amounts of digital data are now being stored in various structured and unstructured formats across multiple environments – both on-premises and in the cloud – and businesses are struggling to keep up with the demands generated from the increasingly globalized regulatory environment.

Webinar Recording
Policy-Based Access Management – A Reliable Foundation for Your Next-Generation Unified IAM
Jun 07, 2018
As companies adopt numerous new technologies and establish new communications channels with their partners, suppliers or even customers, the amounts of sensitive information that’s stored across on-premises systems and cloud services are growing exponentially, and the task of managing secure access to this data by numerous third parties is quickly getting out of control. Hence, instead of managing access to individual systems with separate technology stacks, many companies are looking for more universal and future-proof alternatives, aiming for establishing granular, centrally-managed...

Webinar Recording
Zero Trust: Solving IT Security’s Identity Crisis
May 04, 2018
Although companies are constantly increasing their cybersecurity budgets, this does not seem to help much: each day we learn about new large-scale data breaches. Considering that over 80% of hacking-related breaches leverage compromised user credentials, it’s mindboggling why so many organizations are still focusing on securing their network perimeters.

Webinar Recording
Access Management Leading the Cloud Transformation Drive
Apr 27, 2018
To survive the fierce market competition in the era of Digital Transformation, businesses strive to be as agile as possible, to quickly adjust to constantly changing customer demands, industry regulations and modern technologies. Driven by cloud transformation and digitalization, modern companies are becoming increasingly open and interconnected, with massive numbers of people, devices and applications forming millions of relationships across geographically and technologically diverse environments.

Webinar Recording
An overview of the Leadership Compass: Endpoint Security Anti-Malware
Apr 25, 2018
Malware has been on the rise. Ransomware continues to grab the headlines. New malware variants proliferate by the millions. Old style manual malware analysis can't keep pace. But organizations are increasingly under attack. Fortunately, vendors have been enhancing and improving their products to help their customer successfully defend against these attacks.

Webinar Recording
Privileged Attack Vectors: Verständnis und Minimierung interner und externer Cyber-Risiken
Apr 20, 2018
Eine der unglücklichen Folgen des fortschreitenden Digitaltransformationsprozesses ist die ständig steigende Komplexität der IT-Infrastrukturen von Unternehmen. Die Einführung von Cloud-Technologien, der Ausbau der mobilen Arbeitskräfte und die zunehmende Abhängigkeit von ausgelagerten IT-Mitarbeitern haben dazu geführt, dass der sichere Unternehmensbereich nahezu vollständig verschwunden ist und die Überwachung und Kontrolle privilegierter Zugänge sehr komplex und teuer geworden ist.

Webinar Recording
Cloud Data Protection Done Right: When Bringing Your Own Key Just Isn’t Enough
Apr 13, 2018
As companies continue to expand their adoption of cloud services for such benefits as improved flexibility and scalability, reduced time to market, and cost savings, protecting their sensitive data across a large number of SaaS platforms is becoming increasingly complicated. For heavily regulated industries, security and data protection have been the largest barriers to cloud adoption for years, but with the upcoming General Data Protection Regulation (GDPR)’s significantly tightened compliance controls and massive penalties for violations, protecting sensitive data in the cloud is becoming...

Webinar Recording
Acing the Upcoming GDPR Exam
Apr 11, 2018
With only weeks to go until the EU GDPR (General Data Protection Regulation) takes effect on May 25th, global businesses are scrambling to figure out how to avoid the hefty fines that loom for companies failing to achieve compliance. Sanctions for non-compliance are very severe with penalties of up to 4% of annual worldwide turnover.

Webinar Recording
Holistic Approach to Cyber Risk Governance in the GDPR Era
Mar 16, 2018
As we are getting closer to the dreaded May 25th deadline, when the General Data Protection Regulation will come into force, many companies are still struggling with implementing effective risk assurance programs that constitute a key requirement for any sensible cybersecurity and compliance strategy.

Webinar Recording
Faktor Mensch: Wie man das schwächste Glied der IT-Infrastruktur Ihres Unternehmens schützt
Mar 14, 2018
Um im hart umkämpften und sich ständig verändernden globalen Markt bestehen zu können, sind Unternehmen gezwungen, ständig neue Technologien und Plattformen einzuführen, die unweigerlich zu einer erheblichen Erhöhung der Komplexität ihrer IT-Infrastrukturen führen. Da sensible Geschäftsdaten über mehrere geografische Standorte verteilt sind, wird die Anzahl der Angriffsvektoren, die vor Cyberangriffen geschützt werden müssen, immer größer.

Webinar Recording
Best Practices and Essential Tools for GDPR Compliance
Mar 09, 2018
With just over three months until the General Data Protection Regulation (GDPR) comes into force in the European Union, many organizations are still struggling to prepare for the new regulation.

Webinar Recording
How to Make Your IAM Program a Success
Feb 23, 2018
Identity and Access Management (IAM) is one of the most important and challenging disciplines, involving multiple departments and systems across the enterprise and requiring constant communication between the business and IT. Without IAM, it is difficult to mitigate access risks, to comply with regulations and to deliver a consistent and frictionless user experience.

Webinar Recording
The Evolution of Identity Governance: From Basic Compliance to Federated Security Assurance
Feb 21, 2018
Whenever people are talking about the Digital Transformation, they usually think about modern technologies like cloud computing. However, although adopting new technologies is important for staying relevant and competitive in the rapidly changing market, this transformation primarily reflects the growing volume of digital information that is powering key business processes and unlocking new business models. In many cases, digital data even becomes a company’s primary product and most valuable asset.

Webinar Recording
Step-by-Step Guide to GDPR Compliance
Dec 13, 2017
With less than 250 days left till the dreaded EU General Data Protection Regulation (GDPR) comes into force, organizations around the world are feeling increasingly uneasy. Any company, both large and small, that wants to continue doing business in the European Union must comply with GDPR or face harsh penalties.
Webinar Recording
Redefining Access Governance for Security and Fraud Prevention in Critical Applications
Dec 08, 2017
Continued digitalization of modern organizations, supported by the growing adoption of cloud computing, big data and other innovative information technologies, shows no signs of slowing down. Critical business data such as corporate intellectual property, financial documents or sensitive personal information, which traditionally have been kept in the most secure on-premises systems, must now be made accessible to the outside world: remote offices, mobile workforce, business partners, sometimes even the whole Internet.

Webinar Recording
Authentication & Authorization for the Microservices World
Dec 06, 2017
As businesses are expanding their presence in the cloud, they are increasingly looking into innovative approaches towards software development and operations that allow them to bring their applications to the market faster, to make them more adaptable and scalable to the ever-changing business requirements.

Webinar Recording
Identity and Access Management for Microsoft Azure and SharePoint Online
Dec 01, 2017
As Microsoft’s cloud solutions – including Microsoft Azure, Microsoft Office 365, and Microsoft SharePoint Online – are gaining more market share, integrating these platforms into existing enterprise IAM environments becomes essential. As more and more sensitive corporate data is moved to the cloud, ensuring strong information protection, secure access for employees, partners or customers, and, last but not least, compliance with the stringent regulations like GDPR, is impossible without a unified IAM across all on-premises and cloud systems.

Webinar Recording
Understanding the GDPR Impact on Corporate IT
Nov 29, 2017
The upcoming General Data Protection Regulation (GDPR) can be a major challenge for any organization established or just doing business in the European Union. Soon, failing to properly protect personal information of EU residents may lead to harsh financial penalties, so organizations are scrambling to understand the impact of GDPR on their processes, applications and systems and to adapt to the new requirements accordingly.

Webinar Recording
Revised Payment Service Directive: Understanding Its Technical Requirements for a Smooth and Secure Customer Experience
Nov 17, 2017
In less than 24 months, banks will have to comply with the Revised Payment Service Directive, commonly called "PSD2". The directive will introduce massive changes to the payments industry, removing the banks’ monopoly on their customer’s data. It will radically alter the user experience for customers of European banks by allowing third party payment service providers (TPP) to access their account information to provide various innovative financial services. But to achieve this, banks and TPPs must put the technical requirements in place in a secure way.

Webinar Recording
Connected Car: Putting Digital Identity Behind the Wheel
Nov 15, 2017
The Internet of Things comprises of a diverse range of devices – from industrial sensors controlling critical manufacturing processes all the way to home devices like smart TVs and fridges. The idea of connecting a car to the internet started as an upgrade to the vehicle’s onboard entertainment system. The concept quickly evolved and branched into numerous market segments including navigation systems, safety and diagnostics, toll payments, and fleet management.

Webinar Recording
Industrial Control Systems: Understanding the Access Risks and Security Challenges
Nov 10, 2017
For decades, Industrial Control Systems have evolved completely separately from traditional IT, with their own business drivers, requirements and regulations and proprietary hardware designs and network protocols. Needless to say, security from cyberattacks was never a priority for operational technology units responsible for managing those systems: after all, they weren’t even connected to office networks.

Webinar Recording
Improving Agility and Reducing Cyber Risks with Business-Driven Security Policy Management and Automation
Nov 03, 2017
Today’s enterprises are under continuous pressure to support new digital transformation initiatives, to adopt modern technologies like the cloud and software-defined data centers (SDDC) and, of course, to stay protected from external and internal cyberthreats. With the increasing pace of business, achieving greater agility and efficiency through automation of business processes is becoming one of the key challenges for IT. Unfortunately, the resulting dramatic increase in complexity of heterogeneous IT infrastructures combined with growing sophistication of modern cyberthreats has made...

Webinar Recording
Compliance als Vorteil: Technische Anforderungen der GDPR für moderne digitale Unternehmen
Oct 25, 2017
Ohne Zweifel ist der 25. Mai 2018 im Kalender jedes IT-Spezialisten rot angestrichen. Denn an diesem Tag tritt die neue Datenschutz-Grundverordnung (General Data Protection Regulation, GDPR) in Kraft, welche die Art und Weise, in der personenbezogene Daten von in der EU ansässigen Unternehmen oder anderen Unternehmen, die in der Europäischen Union geschäftlich tätig sein möchten, behandelt werden, grundsätzlich verändert. Nachhaltig beeindruckt von den strengen Strafen, die im Rahmen der neuen Verordnung vorgesehen sind, sind Unternehmen eilig bemüht, sich auf die neuen rechtlichen,...

Webinar Recording
Security Management im digitalen Unternehmen: Business-orientiert, agil, effektiv
Oct 20, 2017
Wie schön waren die Zeiten, in denen man die physische wie digitale Sicherheit in seinem Unternehmen als eine Art Ritterburg mit umlaufendem Wassergraben („Perimeter“) abbilden konnte. Nur wenige, gut bewehrte und streng bewachte Zugänge („Firewalls“) sorgten dafür, dass der Austausch zwischen drinnen und draussen kontrolliert erfolgte und Raubritter wenig Möglichkeiten hatten, sich unberechtigt Zugang zu verschaffen.

Webinar Recording
GDPR: The Six Critical Steps to Compliance and Brand Differentiation
Oct 19, 2017
From May 2018 when the upcoming EU GDPR (General Data Protection Regulation) comes into force, the requirements for managing personal data will change. Companies collecting such information from their customers will have to adapt to fundamental changes both in the very definition of personal data and in technical requirements around its secure and privacy-enhanced processing, including topics like consent management, data portability and the right to be forgotten. You will also understand why leading companies, however, will look beyond compliance to how they can enhance their customers’...

Webinar Recording
Knowing Your Customer Well: The Importance of Assurance and Identity Governance for CIAM
Oct 18, 2017
Consumer Identity and Access Management is a fast-growing market. Emerging just a few years ago, it has quickly evolved to become an indispensable tool for many organizations to improve the reach and targeting of their marketing activities, increase the number of new customer registrations and to provide frictionless user experience. CIAM solutions allow businesses and public-sector agencies to gather more information about the consumers while maintaining compliance with the current and upcoming data protection regulations like the EU GDPR and PSD2.

Webinar Recording
The 8 Critical Areas of Consumer Identity and Access Management to Prepare for in 2018
Oct 13, 2017
Consumer Identity and Access Management (CIAM) is the fastest growing specialty in Identity and Access Management (IAM) that has emerged in the last few years to meet evolving business requirements. Many businesses and public-sector organizations are finding that they must provide better digital experiences for and gather more information about the consumers who are using their services. Enterprises want to collect, store, and analyze data on consumers to create additional sales opportunities and increase brand loyalty.

Webinar Recording
Top Considerations for Selecting an Identity and Access Management as a Service Vendor
Oct 06, 2017
As organizations continue to move their data and application functions into the cloud for obvious business reasons like improved flexibility and scalability, reduced time to market and cost savings, protecting their sensitive data across both on-premises and the cloud is becoming increasingly complicated. To ensure consistent and secure access management to for these data and applications across a heterogeneous IT landscape from any device and location is a massive challenge, further complicated by new compliance regulations such as GDPR, which makes the cost of a mistake extremely high.

Webinar Recording
Dynamic Externalized Authorization for the Evolution of the Service-Oriented Architecture - Using ABAC for APIs and Microservices
Sep 29, 2017
In the Digital Transformation era, businesses must be more agile than ever to adapt to constantly changing technology and regulatory landscapes and to meet the newest customer-centric initiatives. Constantly bombarded with new business requirements, software development and DevOps teams are increasingly looking into new approaches to make their applications more flexible, scalable and easier to maintain and modernize. In recent years, service-oriented architectures and microservices in particular have become the preferred method for many developers to create modular and adaptable enterprise...

Webinar Recording
The Crucial Role of Identity in Securing Industrial IoT
Sep 27, 2017
As more and more consumers, businesses, public sector companies and even whole countries are embracing the Digital Transformation, smart devices of all types are proliferating in all areas of our daily lives. It is safe to say, however, that, after the initial rush of making every device in the world smart and connected, the Internet of Things has already passed the peak of inflated expectations, with both vendors and users of the technology finally starting to care more about such things as interoperability and security.

Webinar Recording
Unstructured Data – A Blind Spot for GDPR Compliance
Sep 22, 2017
While many (but not enough) organizations have finally begun preparing for GDPR compliance, there are still important steps to take. When in May 2018 the upcoming EU GDPR (General Data Protection Regulation) comes into force, the requirements for managing personal data will change.

Webinar Recording
The New Role of IAM in the Age of Digital Transformation
Sep 21, 2017
Organizations are under pressure to change in the current age of Digital Transformation. One of the key differentiators of innovative digital business models and thus new revenue streams is the profoundly changed relationship to customers and consumers. Creating innovative consumer services, collecting and managing better customer information and even just optimizing the reach of everyday marketing activities – all this depends on the ability to manage consumer identities in a flexible, scalable and secure way.

Webinar Recording
Database Security: Protecting Your Company’s Core Competence in the Age of Digital Transformation
Sep 20, 2017
Relational databases are still the most widespread technology for storing and managing business-critical digital information. Manufacturing process parameters, sensitive financial transactions or confidential customer records - all this most valuable corporate data must be protected against compromises of their integrity and confidentiality without affecting their availability for business processes. The number of security risks databases are open to is also substantial, covering the information itself stored and processed in databases, underlying computing and network infrastructures, as...

Webinar Recording
Cognitive Technologies and the Future of Identity & Access Management
Sep 15, 2017
Like any other field of information technology, identity and access management has been rapidly evolving to meet new business challenges created by the Digital Transformation. As modern businesses are becoming increasingly open and interconnected, IAM solutions now need to cover not just employees, but customers, partners and smart IoT devices. They must be able to handle the growing complexity of managing and monitoring access to the company’s most valuable digital assets, regardless of their format, location or scale, while still maintaining compliance and protecting them from cyber risks.

Webinar Recording
Consent Lifecycle Management: Consumer IAM’s Core Capability?
Sep 13, 2017
2018 is going to be a hell of a year for nearly every organization operating within the European Union. Not only the dreaded General Data Protection Regulation (GDPR) will finally take effect next May, introducing massive changes to the way companies will have to deal with personal information (not to mention hefty fines for violations), January 2018 also marks the implementation date of the revised Payment Service Directive (PSD2), which will break the banks’ monopoly on their customers’ account information.

Webinar Recording
GDPR Compliance Countdown to Adequacy – Minimum Preparation to be Compliant
Sep 08, 2017
With less than a year to go before EU GDPR (General Data Protection Regulation) comes into force your organization needs to be ready to comply with these requirements that demand better controls over how it uses and manages the personal data that it holds.

Webinar Recording
Security Benefits of Cloud Solutions
Sep 05, 2017
While organizations are becoming increasingly eager to embrace the cloud for multiple business benefits, for CISOs and CIOs these efforts bring new challenges to understand and evaluate security and privacy impacts by introducing cloud solutions to their enterprises. Adopting cloud services can dramatically improve flexibility and scalability of critical business applications, reduce time-to-market for new products and even unlock completely new business models.

Webinar Recording
Customer Identity Management (CIAM) - Building the Foundations for a Next-Level User Experience
Jul 20, 2017
Digital Transformation is all about following the connected consumer into the new world of digital services, throughout all available channels, highly individualized, privacy aware, compliant and value driven "by design". CIAM describes the underlying infrastructure enabling your business to do so.

Webinar Recording
Interoperability and Intelligence: Two Keys to a Successful Privilege Management Deployment
Jun 29, 2017
As businesses are becoming increasingly digital, their IT infrastructures are continuously growing in scale and complexity, with vast numbers of previously disparate systems and platforms woven together by new communications channels. Many of these systems are no longer located within the corporate perimeter, having partially or completely migrated to the cloud. Even those which still remain on.premises, must be constantly accessible to mobile workers, external contractors or support engineers.

Webinar Recording
How Advanced Identity and API Management Helps You Meeting the Security Challenges of Digital Transformation
Jun 28, 2017
The new business environment is increasingly reliant on web and open source applications, with external partners and customers accessing resources via web browsers and social media channels.

Webinar Recording
Delegate the Task, Not the Privilege: How to Simplify and Secure Your Privileged Accounts
Jun 23, 2017
Privilege Management has been a key element of both IAM (Identity & Access Management) and cyber security programs for years. However, increased the complexity of modern corporate IT infrastructures with growing reliance on outsourced IT staff and mounting pressure from compliance regulators forcing privilege management solutions to expand their scope into new functional areas constantly. From password vaults and privileged SSO to advanced monitoring and behavior analytics to governance and compliance – managing a PxM solution can become as complicated as the infrastructure it is designed...

Webinar Recording
(Big) Data Security: Protecting Information at the Source
Jun 02, 2017
The ongoing Digital Transformation has profoundly changed not just IT infrastructures, but in many cases, entire business models and processes for many organizations. Digital information has become one of the most precious assets of nearly every company, and for many, it is no longer just another means of improving their business process efficiency – data has become their core competence and most valuable intellectual property.

Webinar Recording
Identity 2.0: The Next Generation of Customer Identity
May 31, 2017
Consumer identity and access management solutions have emerged in the recent years to meet evolving business requirements. CIAM is bringing value to the organizations regarding higher numbers of successful registrations, customer profiling, authentication variety, identity analytics, and marketing insights. Companies and public sector organizations with deployed CIAM solutions can provide better digital experiences for and gather more information about the consumers who are using their services.

Webinar Recording
Getting Identity and Access Management Right – Even If SAP Is Involved
May 24, 2017
Implementing Identity and Access Management universally across multiple IT infrastructures and software platforms is a major challenge for any organization. To do their daily job successfully, users today expect to get access to information they need from anywhere at any time, regardless of the target system or application.

Webinar Recording
Architecting a Digital Strategy for PSD2 and Open Banking
May 18, 2017
PSD2 and the Open Banking Standard are regulatory mandates being applied to the banking industry by the European Banking Authority (EBA) and Competition & Markets Authority (CMA) across Europe and in the UK respectively. The regulations require that banks operating across the region expose open APIs to allow other banks and third parties to access the data they hold on customers, when the customer has given their explicit consent. Designed to improve choice for customers, create more competition and stimulate innovation in the finance sector, the introduction of 'open banking' in the UK and...

Webinar Recording
Rollenmanagement erfolgreich etablieren sowie sicher und effizient betreiben
Apr 28, 2017
Das Management des sicheren Zugangs zu Ressourcen innerhalb einer Organisation ist eine der zentralen Aufgaben im Bereich des Identity und Access Managements. Die Aufgliederung existierender organisatorischer Komplexität durch deren Abbildung in handhabbare Rollen ist eine kontinuierliche Herausforderung und bedarf angemessener Prozesse und Technologien.

Webinar Recording
Making the Cloud a Secure and Easy to Use Environment
Apr 07, 2017
Most of today’s organizations store even their sensitive data in the cloud. Moving workloads to the cloud results in improved flexibility, elasticity, and reduced time to market for organizations. Nevertheless, companies have to realize these benefits painlessly, while keeping sensitive data secure. Applying an on-premises security model for infrastructure and apps in the cloud can achieve this.

Webinar Recording
Digital Transformation in Government
Apr 06, 2017
Digital transformation is increasingly affecting all types of organisations including Governments. In order to encourage citizens to adopt digital services, the least expensive channel for governments, it is necessary to support modern connection methodologies and provide user-focussed services. This webinar will investigate the challenges facing government and the opportunity digital transformation affords.

Webinar Recording
Managing the User's Consent Life Cycle: Challenges, GDPR Compliance and (Business) Rewards
Apr 05, 2017
Companies that manage consumer identities and personal profiles have a bit more than one year left to comply with the new European General Data Protection Regulation (EU-GDPR).

Webinar Recording
Reducing Risk with User Behavior Analytics (UBA)
Mar 31, 2017
Business landscape is changing rapidly where most organizations, irrespective of the vertical, are transforming themselves into technology organizations. With the adoption of Internet of Things (IoT), the number of connected entities has increased significantly. Managing identities of people, things and other objects in an automated and predictive manner is becoming the new norm. Simultaneously, the burgeoning number of identities exposes a broader attack surface posing a big challenge to these organizations and their growth plans.

Webinar Recording
Creating Secure and Unified Next Generation Workspaces
Mar 30, 2017
A key challenge in every organization is making sure that the right tools are available, in the right place, at the right time, for the right people. The continual on and off boarding of large groups of employees, external workforces or partners creates increased pressure on administrative teams within an organization. An overall change towards diverse end-user devices, both corporate and privately owned, adds a new dimension of complexity, while compliance and security requirements challenge IT, CISOs and executive management.

Webinar Recording
Personal data breach and the GDPR – Prevention, Detection and Notification
Mar 24, 2017
The general data protection regulation (GDPR) as issued by the European Union will be a major challenge for literally any organisation doing business in Europe. In roughly 15 months from now it will reach legally binding status in every country within the European Union. And beyond: Probably one of the most striking characteristics of the new regulation that is constantly underestimated is the scope of its applicability. It actually applies in all cases where the data controller or the data processor or the data subject is based in the EU. This includes all data processors (e.g. cloud...

Webinar Recording
Blockchain - How to Separate the Hype from Reality
Mar 23, 2017
Blockchain has taken the world by storm since the inception of Bitcoin. While the primary interest has been in the financial and insurance industry sector Blockchain technology has wider application. This webinar will describe the technology and separate the hype from reality, looking at some innovative Blockchain applications from identity management to the Internet of Things.

Webinar Recording
GDPR as opportunity to build trusted relationships with consumers
Mar 20, 2017
The new regulations of the EU GDPR apply not only to companies in the EU but every organization dealing with the personally identifiable information of EU citizens. This means most enterprises across the world will be impacted when compliance is required on May 25, 2018.

Webinar Recording
Privileged User Monitoring as Key Element of Counter-Measures
Feb 22, 2017
The IT landscape is undergoing its biggest change at least since the introduction of the PC. Cloud services and mobile devices stand for the hyper-connected enterprise, where everyone has access to everything, and where services reside somewhere, in the organization and in the cloud. This extends the risk surface. It is no longer about protecting some centralized servers in a well-secured data center, but about a sprawl of systems and services.

Webinar Recording
Improving Your SOC Efficiency with Advanced Security Analytics
Jan 25, 2017
Today, the Security Operations Center (SOC) is at the heart of enterprise security management. Security analysts in most SOCs are still relying on traditional SIEM systems as a core platform for their daily operations. These are the primary tools to monitor and analyze security alerts coming from the various systems across the enterprise and to take actions against detected threats. However, the rapidly growing number and sophistication of modern advanced cyber-attacks make running a SOC an increasingly challenging task even for the largest enterprises with their fat budgets for IT security.

Webinar Recording
Identity Assurance - the Art of Knowing Your Customers
Dec 16, 2016
To conduct online business, users need to be able to identify themselves remotely and reliably. In most cases, however, it is not sufficient for the user to simply assert "I am who I say I am - believe me." When doing digital business, you will never meet your customers face-to-face, and there is a need to establish certainty and proof of the customers' identity. Digital on-boarding must be simple for the user, while at the same time give the business enough information to ensure trust. This webinar will take a look at methods for digital customer on-boarding, to ensure that reasonable...

Webinar Recording
Cloud IAM – Get the Full Picture to Make a Real Win out of a Quick Win!
Dec 14, 2016
Cloud IAM, or IDaaS, is a rapidly growing market segment. This growth is driven by a variety of business cases, ranging from operational advantages and better support for employees accessing cloud services to the flexible integration of business partners and consumers in the age of digital transformation. Organizations need to understand their challenges, the potential of Cloud IAM, and what Cloud IAM must provide in functionality for addressing these challenges.

Webinar Recording
The Future of Privilege Management – Understanding the Bigger Picture
Dec 09, 2016
Privilege Management, the management of accounts with elevated privileges and, in particular, shared accounts, is changing drastically. Providing shared account password management, a privileged Single Sign-On, or restrictions for elevated privileges is no longer sufficient.

Webinar Recording
Prevent Data Breaches - Moving to a Modern Approach to Breach Avoidance in Three Steps
Dec 07, 2016
The history of IT Security is only a generation old, yet the direction of the arms race has already changed completely several times. Initially, perimeter-based security – firewalls and anti-virus software – played the most important role at organizations. By the beginning of the new millennium the focus of security turned to identity-based solutions but IAM has also been shown not to be a silver bullet to protect against breaches.

Webinar Recording
Sicherheit in den operativen Systemen der Industrie 4.0
Nov 18, 2016
Unter dem Begriff Operational Technology werden die Technologien zusammengefasst, die die Transformation von Waren und Dienstleistungen betreffen, etwa in produzierenden Unternehmen oder bei Energieversorgern (ICS: Industrial Control Systems & SCADA: Supervisory Control and Data Acquisition).

Webinar Recording
Enabling Cloud Access While Ensuring Security and Compliance
Nov 16, 2016
The cloud and mobile revolutions have changed the way we work and the very nature of IT. But these advances have also created immense new challenges and risks to security, data protection and compliance.

Webinar Recording
Beyond Usernames and Passwords: 3 Steps to Modern Authentication
Nov 11, 2016
There are three simple steps for moving to modern, more secure authentication. Make it convenient. Make it smart. Make it mobile.

Webinar Recording
Reinventing Smart Cards for the Modern Agile, Connected Enterprise
Nov 04, 2016
Smart cards have been a key part of any IT department’s security and identity management toolkit for over two decades. They are widely used for such operations like two-factor authentication, digital signatures, data encryption or single sign-on. Smart cards are an integral part of every enterprises’ Public Key Infrastructure.

Webinar Recording
Securing and Proving your Digital Self
Oct 28, 2016
We are all living in the era of digitalization, where nearly all processes, business and private, accelerate at an enormous speed. For example, employees are today located in different places on the globe, they use different devices, and do so at any time they need to. For access to sensitive data, they need to be able to authenticate themselves reliably.

Webinar Recording
How to easily expand Identity & Access Management to the Cloud
Oct 26, 2016
Trying to find the right access security solution has always been a complex task. It is, however, even more challenging when the existing web access management solution is not sufficient anymore.

Webinar Recording
Cloud-Risiken jederzeit rundum mit zentralen Dashboards kontrollieren
Oct 24, 2016
Organisationen weltweit stehen vor den gleichen Sicherheitsherausforderungen. Sie müssen Mitarbeitern ermöglichen, mit einer Vielzahl von Endgeräten über die Cloud auf Dienste zuzugreifen, um auch außerhalb der Unternehmensmauern überall und jederzeit produktiv ihren Aufgaben nachgehen zu können, ohne dass Anforderungen an die Compliance darunter leiden.

Webinar Recording
The Future of Data-Centric Security
Oct 19, 2016
Business boundaries are dissolving as the ability to share information improves. For example, in agile and collaborative working environments, information has to be shared efficiently and securely between various internal and external business partners, mainly via cloud services and with mobile devices. This requires extensive access to what is often critical content, stored in well-protected databases. Sharing then presents a challenge: How can sensitive data be masked from people who are not permitted to see it and deliver it securely to those who are? And how can this be done...

Webinar Recording
Big Data – Bigger Risks?
Oct 14, 2016
Organizations are using Big Data to better understand their customers, to improve their products and to optimize their operations. However, Big Data technologies were conceived and designed for scalability and performance rather than security. You need to take steps to secure your Smart Information infrastructure.

Webinar Recording
Rising to the Security Challenge of Heavy Cloud Adoption
Oct 13, 2016
Many enterprises have decided on a “cloud first” strategy, or have seen heavy cloud adoption evolve spontaneously as their business units embrace cloud for cost savings, agility or other competitive imperatives. In the course of this development, security teams face difficult challenges controlling, influencing or enabling cloud adoption.

Webinar Recording
State-of-the-Art Privilege Management by Design
Oct 07, 2016
The challenges for securely managing and monitoring access to administrative accounts are changing continuously. This is true for business processes, job profiles, legal and regulatory requirements and the underlying IT infrastructure. And it is true for the changing threat landscape.

Webinar Recording
Cloud Access Security and Enterprise Mobility - Better Together
Sep 30, 2016
Let’s face it: cloud services have already become an integral part of every company’s IT infrastructure. They provide immense benefits, helping adopt new business models and emerging technologies quickly, addressing constantly changing customer demands and reducing costs and administration burden. More and more of corporate information assets are now kept and managed outside of the company’s digital perimeter.

Webinar Recording
You Thought Shadow IT Was Bad? Meet Your Company's Shadow Administrators
Sep 02, 2016
Despite being over 20 years old, Secure Shell (SSH) is still one of the most commonly used methods for both network encryption and secure user authentication. Nearly every server from distributed platforms to mainframes and the majority of network devices include an SSH server as a standard component. Many workstations come equipped with an SSH client, making it one of the most widely available tools for IT professionals. In every organization, SSH is used daily to access remote systems, run automated processes or transfer data over the network.

Webinar Recording
Identity Relationship Management: Kommunikation und Kollaboration mit Partnern und Kunden sicher steuern
Jun 28, 2016
Mit der steigenden Nachfrage von Unternehmen nach engerer Kommunikation und Kollaboration mit externen Partnern und Kunden wächst auch der Bedarf an professionellem Web Access Management und Identity Federation. Geeignete Lösungen ermöglichen sichere Zugänge von und auf externe Systeme, auch aus der Cloud. Um die Vielzahl an Anforderungen für eine sichere Kommunikation und Kollaboration erweiterter und vernetzter Unternehmen nahezu lückenlos mit IT abzudecken und gleichzeitig agil zu bleiben, sind Standardinfrastrukturen notwendig.

Webinar Recording
Managing Risk through Cloud App Authentication and 360° Control
Jun 24, 2016
The easy availability of IT services delivered as cloud services together with the revolution in the range of devices that are used to access these services has created challenges for organizations in the areas of security and compliance. Employees and associates can use their personal cloud services to perform their jobs without reference to their employer. Line of business managers can acquire cloud services without performing risk assessment or considering the impact of these on compliance. To compound the problem mobile devices can be used to access these services from outside of the...

Webinar Recording
No Real Security Without Multi-Factor Authentication Everywhere
Jun 17, 2016
Clearly, there is a trend towards approaches for strong, simple, and flexible authentication, beyond passwords. The benefits fall largely under the categories of an improved customer experience, since with Multi-Factor Authentication (MFA) channels, the reduced dependence on passwords allows password policies to be more user friendly.

Webinar Recording
Authentication, Access, Assets: The Triple A of Securing Sensitive Systems and Information
Jun 14, 2016
In more than two thirds of all cyber breaches, a misused privileged account serves as the entrance gate. Historically, managing privileged access focused on protecting privileged accounts by securing and managing passwords. But today, simply rotating passwords isn’t enough to defend against increasingly sophisticated cyberattacks. When it comes to securing privileged systems and data, organizations need to broaden their focus on controlling Authentication, Access and Assets.

Webinar Recording
Data Loss Prevention Best Practice
Jun 09, 2016
The first step in protecting intellectual property and sensitive information is to classify it. This can be accomplished manually via author classification or automatically via content filtering. Some tools simplify the process and provide greater governance.

Webinar Recording
Transforming Governance, Security and Compliance
May 24, 2016
The number of companies investing in modern “Big Data”-type SAP products and cloud-based SAP deployment models is growing constantly. Having formerly been stored in standalone database silos, SAP information from CRM, ERP etc. for Big Data deployments is now being migrated to a central high-volume and high-performance database. Deploying traditional SAP environments in the cloud and leveraging new cloud-based SAP applications introduce new groups of customers to SAP services and shift the focus of existing SAP users.

Webinar Recording
Ensuring Compliance Through Automation
May 21, 2016
The definition, implementation and maintenance of an adequate set of policies is a major task for many areas of today’s organizations. However, continuously ensuring compliance to these policies and providing adequate documentation of evidence is even more challenging. Keeping computer security definitions in compliance with your corporate security policy and with mandatory regulations is overly complex when done the conventional way.

Webinar Recording
The Future of Mobile Authentication: Strong, Adaptive, Intelligent
May 17, 2016
The unstoppable march of cloud, mobile and social computing in the recent years has made a profound impact on our society. Exponential growth of corporate digital assets combined with the overwhelming proliferation of mobile devices put enormous pressure on modern businesses to become increasingly connected. To stay competitive, they must be able to adapt their business models to constantly changing customer demands, technology innovations and ever-increasing number of communications channels with their current and future customers, business partners, suppliers and, of course, their own...

Webinar Recording
Digital Transformation: Why Security and Privacy Matter
May 04, 2016
Amazon, Uber, Netflix, the Kindle etc.: Digital technology has changed our society in an appreciable way. Just as our personal lives are being transformed digitally, the same happens in corporations and with our traditional technology solutions. The digital transformation affects everything from customer experience andoperational processes to business models and IT focus. Even software development is being digitally transformed. This leads to new security and privacy challenges: In IoT and digital transformation, organizations have to deal with more identities and relations than ever...

Webinar Recording
Enforcing Fine Grained Access Control Policies to Meet Legal Requirements
Apr 29, 2016
Attribute Based Access Control (ABAC) solutions provide an organization with the power to control access to protected resources via a set of policies. These policies express the increasingly complicated legal and business environments in which companies operate these days. However, due to the number of moving parts, it becomes harder to understand the effect a policy change might have in a complex policy set. These moving parts include the policies themselves, attribute values and the specific queries under consideration.

Webinar Recording
Customer-centric Identity Management
Apr 27, 2016
While most organizations are at least good enough in managing their employee identities, dealing with millions of consumer and customer identities imposes a new challenge. Many new identity types, various authenticators from social logins to device-related authenticators in smartphones, risk mitigation requirements for commercial transactions, the relationship with secure payments, customer retention, new business models and thus new requirements for interacting with customers: The challenge has never been that big.

Webinar Recording
Alles zu Consumer Identity Management
Apr 22, 2016
Mittlerweile sind die meisten Unternehmen in der Lage, sicher mit den Identitäten ihrer Mitarbeiter umzugehen. Doch die Handhabung von Kundenidentitäten, deren Anzahl oft in die Millionen geht, stellt noch immer eine Herausforderung für die meisten Unternehmen dar. Mehr Identitäten, der Zugang über Social Logins, mehr Flexibilität bei der Authentifizierung beispielsweise über die in Smartphones integrierten Funktionen, die Anforderungen zur Risikominderung beim eCommerce, die Integration mit sicheren Bezahlsystemen, Kundenbindung, neue Geschäftsmodelle sowie neue Anforderungen für die...

Webinar Recording
Fueling Digital Innovation with Customer Identities
Apr 20, 2016
Identity management has become far more than a key component for defining security and access controls. Understanding customers’ identities through all of their interactions with an organization is key to developing strong and enduring relationships across multiple channels. Combining information from various sources (registration forms, devices, social accounts, etc.) to provide optimal user experiences is now a prerequisite for customer-facing enterprises.

Webinar Recording
Consumer-Focused Identity Management
Apr 14, 2016
Consumer expectations of Identity and Access Management (IAM) - even if they don't know what it is - are evolving and growing ever higher. The ability to use social media accounts to gain access to various services has revolutionised the way consumers see the space. Increasingly, banks and telcos and other traditional businesses with large user bases are finding it hard to grapple with the IAM needs of the services they deliver. What's worse, these organisations are missing out on opportunities to build deep, engaging relationships with their customers through an archipelago-like siloed...

Webinar Recording
Easy and Secure User Access to Sensitive Information
Apr 13, 2016
In the first part of this webinar, Martin Kuppinger, Founder and Principal Analyst at KuppingerCole, will describe the concept of adaptive authentication and Adaptive Policy-based Access Management (APAM). He will also explain why it is crucial for proper access to information that authentication is dynamically changed and adjusted to the circumstances.
In the second part, Reinier van der Drift, former President and CEO at Authasas, now a part of Micro Focus, will present a one-stop-solution that provides users with consistent, easy-to-use and secure access from various devices to...

Webinar Recording
Detecting the Hand Still in the Cookie Jar
Apr 05, 2016
SAP systems contain the most precious assets of an enterprise. They can however get lost, manipulated or destroyed in less than a minute. Examples are a) theft of sensitive customer data on a large scale by simple download, b) illegitimately elevated access rights: A user creates fictive other users, carries out illegal activities and deletes these users afterwards again, c) system take over by manipulating files on the level of the operating system which gives full access to all data on the SAP system.

Webinar Recording
The Blockchain and Information Security
Mar 31, 2016
What new risks and solutions will blockchain technologies bring to user identification and authentication, the Internet of Things (IoT), Digital Rights Management and Life Management Platforms (LMP)? Is the use of blockchain technologies always appropriate?

Webinar Recording
Digitale Transformation: Risiken kontrollieren und Compliance-Anforderungen erfüllen
Mar 22, 2016
Informations- und Entscheidungsprozesse von Kunden haben sich dramatisch verändert. Dies hat in Unternehmen zu einem gesteigerten Interesse an digitaler Transformation von Geschäftsprozessen geführt. Beziehungen und Vernetzung sind heute Kern jedes Geschäftsmodells. Sie fließen in zentrale Expansions- und Profitabilitätsstrategien ein, da sie neue Ideen, Wachstum und Chancen fördern.

Webinar Recording
Whitelisting und darüber hinaus
Mar 15, 2016
Nicht Server und Cloud, sondern die Arbeitsplatzrechner von Unternehmensmitarbeitern stellen die große Masse der Unternehmens-IT dar. Damit steht jeder Arbeitsplatzrechner im Fokus potentieller Angreifer und muss nachhaltig vor einer Vielzahl von internen wie externen Angriffen und Fehlbenutzungen geschützt werden. Firewalls und Virenscanner stellen heute akzeptierte und weitgehend implementierte Sicherheitsmaßnahmen dar. Der Schutz des klassischen Desktops, aber auch von Server-Systemen, vor der Ausführung unerwünschter Software durch Anwender wie Administratoren ist eine kontinuierliche...

Webinar Recording
How Digital Transformation Meets Risk Governance and Compliance Demands
Mar 10, 2016
Customer's information and decision making processes have changed dramatically. This has contributed to the increase in companies turning to Digital and Business Transformation. Relationships and connections are at the heart of any business. They foster new ideas, growth and opportunities, thus they move into the center of growth and profitability strategies.
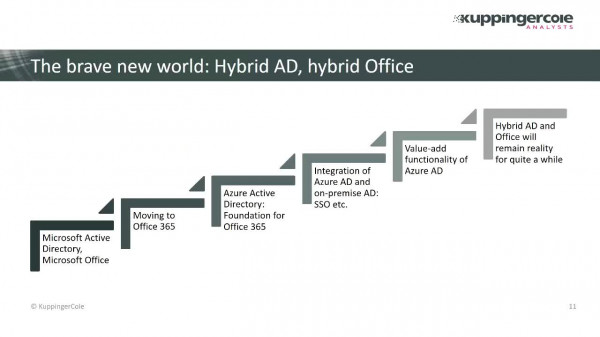
Webinar Recording
How to Manage Your Azure AD and Office 365
Mar 08, 2016
Regulatory compliance does not end at your perimeter. Moving to the Cloud will not get you rid of implementing Access Governance and a well thought-out reporting. Furthermore, moving to the Cloud might make administration more complex, not easier. Proven and established tools in your AD (Active Directory) environment don’t work anymore and, when ending up hybrid for the foreseeable period of time, you will have to manage both the on-premise and Cloud environments. Native tools specifically for the Cloud solutions won’t solve the challenge in hybrid environments. There are far too many...

Webinar Recording
Lifecycle Journey: How Digital Documents Optimize Contract Processes
Mar 02, 2016
This webinar follows the lifecycle of a document: Digital contracts go through many phases throughout their existence. From the production of the document, through presentation, revisions, and then being signed by the involved parties. But the journey doesn't end there. If the contract is valid for a long time, periodic re-sealing is also required, to ensure its validity as well in the future.

Webinar Recording
Identitätsmanagement im Mittelpunkt der digitalen Transformation
Jan 29, 2016
Die erste Hype-Welle um das Internet of Things (IoT) hat an vielen Stellen die Privatsphäre und das Dateneigentum unberücksichtigt gelassen. IoT Implementierungen müssen die Beziehung von Nutzern, Nutzerdaten, Dingen und Diensten (Services) berücksichtigen. Nur dann können sie erfolgreich sein. Nutzer wollen entscheiden, mit wem sie die Daten teilen. Ein hochskalierendes Identitäts- und Accessmanagement ist hierfür Voraussetzung. Insbesondere müssen die Verfahren, mit denen der Zugriff auf Daten oder Geräte gesteuert wird, einheitlichen Protokollen folgen (Autorisierungsprotokolle),...

Webinar Recording
How to Ensure the Success of Your Privileged Access Management Projects
Jan 20, 2016
The majority of 2015's high profile security breaches can be attributed to lost or stolen credentials and nowhere are the stakes higher than with those distributed to “super users”. It’s no surprise, therefore, that many organisations looking to shore up their defences start with privileged access management (PAM).

Webinar Recording
Dell Identity Manager 7.0: Why Things Have Changed
Jan 13, 2016
IAM (Identity & Access Management) is a central discipline of Information Security. But it rarely starts on a green field – commonly there are already some IAM components in place such as directories, Single Sign-On etc. There might also be e. g. IT service management tools in the company. Thus, IAM must integrate well into the existing landscape. Depending on their current infrastructure and requirements, organizations therefore might want to start at different points with IAM. Successful implementations demand a holistic, unified view.
Webinar Recording
Protecting the Keys to Your Kingdom Against Cyber-Attacks and Insider Threats
Dec 15, 2015
Do you really know who and how many employees in your company use a privileged account? Are these accounts properly managed and secured? Answering just one of these questions with "no" or "don't know" puts the most valuable data assets of your enterprise at risk.
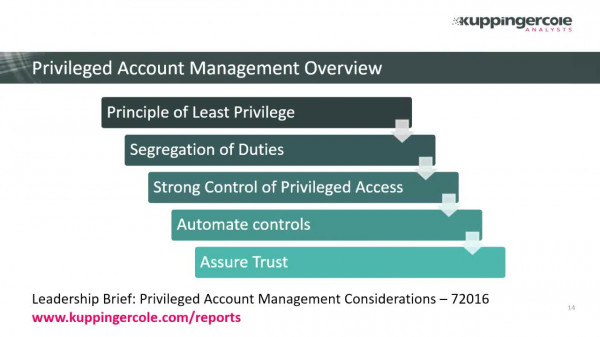
Webinar Recording
The Seven Keys to a Successful Privileged Account Management Strategy
Nov 18, 2015
How can IT professionals successfully walk the thin line between protecting their organization's critical data and at the same time enable users and administrators to work productively? First of all, it is absolutely important to control, monitor, and audit privileged access in order to mitigate the risks posed by insider threats, prevent data breaches, and meet compliance requirements.
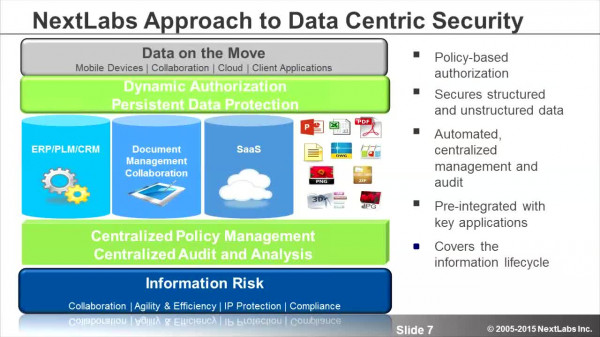
Webinar Recording
Controlling Access through Centralized Authorization
Nov 13, 2015
Access to applications have been managed effectively for the most part, through authentication and identity management. This has driven the combination of ease of use and security behind explosive growth of consumer and enterprise applications. However, with the proliferation of connected devices and smart phones brings a new set of challenges beyond these traditional controls requiring the use of authorization as a fundamental component for a complete access and security strategy.
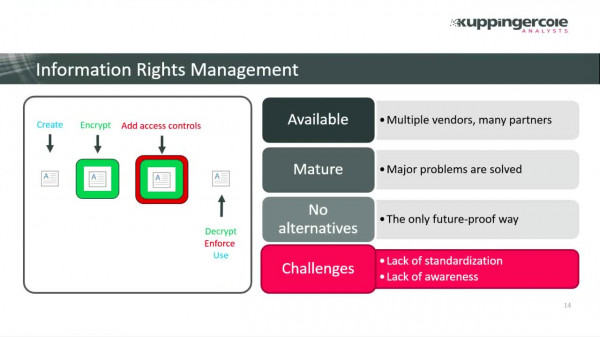
Webinar Recording
Forget Firewalls - Enterprise Data is your New Perimeter
Oct 30, 2015
One of the biggest challenges modern enterprises are facing is the evolution toward connected businesses. To survive in this fiercely competitive environment, businesses strive to be as agile as possible, to continuously adopt new business models and to open up new communication channels with their partners and customers. Thanks to rapidly growing adoption of cloud and mobile computing, enterprises are becoming more and more interconnected, and the notion of a security perimeter has almost ceased to exist.

Webinar Recording
Intelligente Protokollierung von Aktivitäten
Oct 28, 2015
Einen Einblick in die Administration von kritischen Systemen zu haben ist notwendig, um die Einhaltung von Vorschriften kontrollieren und den Schutz des Systems, als Kernstück des Unternehmens, sicherstellen zu können. Durch die Protokollierung und Analyse der Aktivitäten von privilegierten Nutzern und Administratoren können Fehlverhalten und daraus resultierende Gefahren schneller erkannt und weitere negative Auswirkungen für Systeme, Anwendungen und Daten verhindert werden.
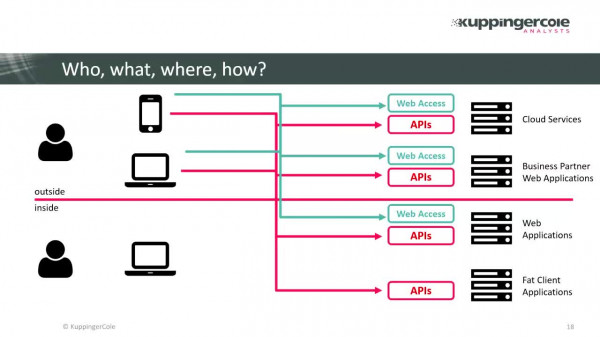
Webinar Recording
One IT, One Identity: Mastering the Security Challenge in the Age of Digital Transformation
Oct 23, 2015
A few years ago, KuppingerCole's Analysts came up with the term "identity explosion", meaning the exponential growth of identities organizations have to deal with caused by Cloud Computing, Mobile Computing, Social Computing, Big Data, the Internet of Things and more. The digital transformation of business is now raising the impact of this explosion - which means that we have to transform our understanding of identities and access.
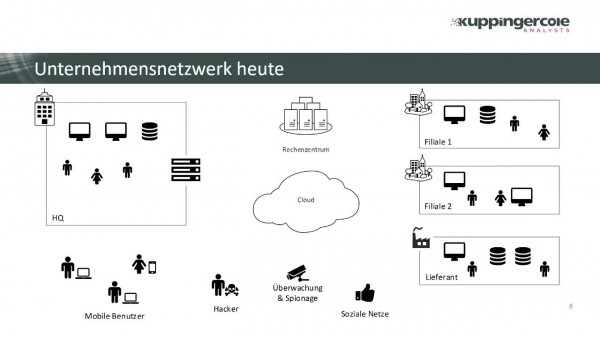
Webinar Recording
Internet Security as a Service
Oct 22, 2015
Das Internet hat ganze Industriezweige und Geschäftsmodelle revolutioniert und darüber hinaus unsere Arbeitsweise grundlegend verändert. Über Jahrzehnte gewachsene Arbeitsabläufe und Geschäftstätigkeiten wurden innerhalb kürzester Zeit ausgehebelt. Unternehmen öffnen sich zunehmend den Vorteilen von Cloud-Anwendungen, wie Office 365, Salesforce, etc. Allerdings stellen sie oftmals fest, dass zuerst die WAN-Infrastruktur aktualisiert werden müssen.
Webinar Recording
Universal SSO: Strategies & Standards for Single Sign-On Across Web and Native Applications
Oct 16, 2015
Many organizations have had some form of Web Access Management solution deployed for years. Whether this is pure-play Web Access Management, providing Web Single Sign-On capabilities and coarse-grain Access Management, or more advanced technology including Web Application Firewall functionality, one target is to manage access of employees and business partners to these applications.

Webinar Recording
7 Common Symptoms of IAM & IAG Diseases
Oct 09, 2015
Complaining users, missed targets in connecting systems and reduced manual work - these are only three of common symptoms of IAM & IAG diseases. To heal these diseases a company must start with the right measures such as introducing consistent role management and multi-level recertification, integrating an IT Service Management/Ticketing System, etc. Get more knowledge about roles, recertification and processes for a working IAM & IAG strategy.
Webinar Recording
The CISO Imperative: Taking Control of SAP Cyber Attacks
Sep 30, 2015
It is impossible to overestimate the importance of SAP system security for modern enterprises. SAP solutions are widely used in all industries to store sensitive information and run critical business processes: from Enterprise Resource Planning and Human Resources systems to Business Intelligence to Customer Relationship and Supply Chain Management. Constant availability and protection of SAP systems is critical for over 250,000 enterprises around the world, as is their continued visibility and auditability to ensure compliance.
Webinar Recording
Access Governance in a Cloudy Environment
Sep 22, 2015
Organizations are increasingly using the new technologies of smart devices, cloud computing and social media to connect with their customers, improve service and reduce costs. To successfully exploit these new technologies organizations need to understand and manage the risks that these bring.
Webinar Recording
Effiziente Administration von Benutzerberechtigungen - Wenn Rollenvergaben alleine nicht ausreichen
Sep 17, 2015
Die Einhaltung und Umsetzung komplexer Regularien stellt viele Organisationen vor große Herausforderungen. Das Berechtigungsmanagement muss mit Blick auf die Vielzahl möglicher Berechtigungen beherrschbar bleiben. Eine rein rollenbasierende Berechtigung ist aber mit Blick auf die notwendig werdende Anzahl statischer Rollen oft nicht angemessen. Die regelbasierte Vergabe von Berechtigungen kann hier eine wichtige IT-Governance-Komponente darstellen.
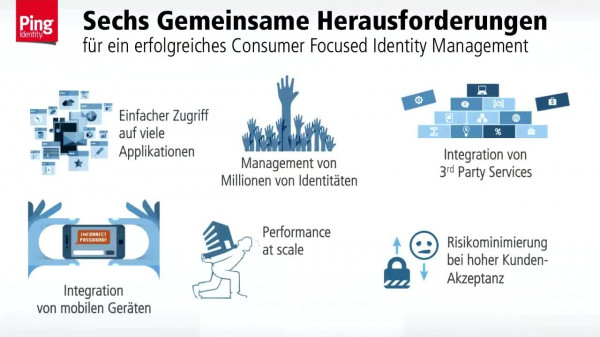
Webinar Recording
Im Mittelpunkt steht das Kundenerlebnis: Consumer Focused Identity Management
Sep 15, 2015
In den letzten fünf Jahren haben sich die Bedürfnisse von Unternehmen, was den Zugriff auf kritische Anwendungen oder die Sicherheit von Kundenidentitäten betrifft, deutlich geändert. Zunehmend vernetzte Kunden, die auf neue Art und Weise über verschiedene Kanäle aktiv werden, lassen die Grenzen der Kundeninteraktion verschwimmen. Das neue Kundenverhalten zwingt Marketingabteilungen und Geschäftsbereiche nun dazu, eng mit den IAM-Verantwortlichen zusammenarbeiten: Sie müssen gemeinsam eine passende Lösung finden, die das Unternehmen bei der Schaffung, Pflege und Optimierung von...
Webinar Recording
From Static Roles to Dynamic Attribute-Based Authorisation
Sep 09, 2015
Traditional identity & access management (IAM) relies on the modeling of roles and permissions for the administration of rights. However, the digital transformation of business models and the demand for more flexibility and increased speed of implementation is turning out to be more than what a pure role model could provide. IAM is now much more essential to operations than was the case a few years ago, and therefore requires more agility. Dynamic authorisation provides this and is the core of the new IAM framework.
Webinar Recording
Vulnerability Assessment 2.0: Improving Accuracy and Reducing Costs with Behavior Analysis
Sep 02, 2015
Vulnerability scanners and management tools have been an important part of every information security specialist’s arsenal for decades. Nowadays, with the continued erosion of corporate perimeters and overwhelming increase in advanced targeted attacks exploiting known and unknown vulnerabilities, they are more important than ever before. Learn more about the emerging new generation of vulnerability assessment tools, which focus on clear and concise actionable reports instead of raw detection logs, providing considerable time and cost savings for your security team.

Webinar Recording
Controlling and Monitoring Administrative Access to Enterprise IT
Jun 29, 2015
Managing and monitoring privileged access to Enterprise Systems has turned out to be one of the most important aspects of IT security for almost any type of organization.
Webinar Recording
Beyond Database Security: Adaptive, Policy-Based Access Control for Dynamic Data Filtering and Data Masking
Jun 24, 2015
Controlling access to databases can be anything between complex, performance-breaking and not fine-grained enough. In this webinar we will explore new approaches to this challenge and how they tackle frequent performance and security issues.
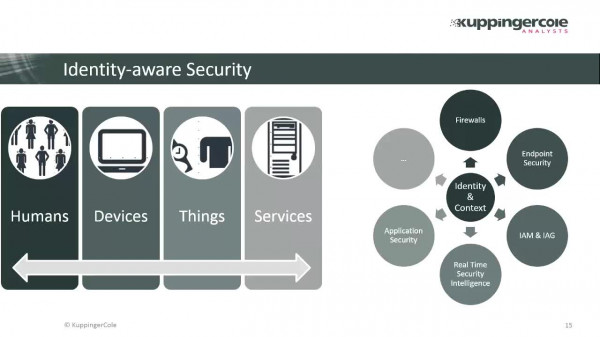
Webinar Recording
How to Cope with Challenging Identities in a Converged World
Jun 18, 2015
Over the past years the term of the Identity Explosion, depicting the exponential growth of identities organizations have to deal with, raised. We introduced the need for a new ABC: Agile Business, Connected. While agility is a key business requirement, connected organizations are a consequence of both the digital transformation of business and of mobility and IoT. This rapid evolution in consequence means that we also have to transform our understanding of identities and access.
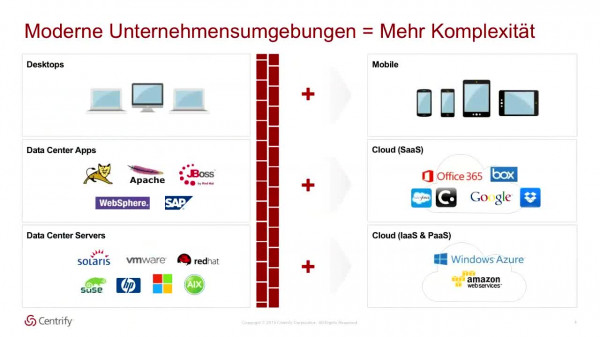
Webinar Recording
Mit Active Directory zu sicherer Zugriffskontrolle für das Digitale Business
Jun 16, 2015
„Identität ist der neue Perimeter“ und „Identity und Access Management/Governance sind das Fundament für die Sicherheit des digitalen Unternehmens“ – so könnte man die Trends der kürzlich in München zu Ende gegangenen European Identity & Cloud Conference 2015 (EIC) zusammenfassen.

Webinar Recording
Ground Control to Major CRO: Is Identity Governance a Risky Experience?
Jun 03, 2015
In today’s fast changing world the digitalization of businesses is essential to keep pace. The new ABC – Agile Businesses Connected – is the new paradigm organizations must follow. They must connect to their customers, partners and associates. They must become agile to respond to the changing needs of the market. They must understand, manage, and mitigate the risks in this connected world. One important aspect of this is the governance of the ever-increasing number of identities – customers, things, together with their access.
Webinar Recording
Bedrohungen für privilegierte Zugänge erkennen und abwenden
May 19, 2015
Mit den jüngsten Sicherheitsvorfällen rücken Systemadministratoren und privilegierte Zugangsdaten weiter in das Zentrum des Interesses. Die nicht abreißenden Schlagzeilen über Fälle von Datendiebstahl bei Unternehmen und Behörden zeigen, dass es sich nicht um Einzelfälle handelt, sondern um ein Problem, dem sich alle Unternehmen stellen müssen.
Webinar Recording
The Future of Federation
May 19, 2015
Federated authentication is the bedrock of secure Cloud access control. It enables organisations to extend their business operations beyond their network boundaries and join identity repositories from multiple sources and access multiple service providers using the same authentication environment.

Webinar Recording
Borderless Identity: Managing Identity in a Complex World
Apr 30, 2015
Security and the Internet of Everything and Everyone from Industrial Control Systems, through wearable tech, to “smart” devices for home, office and car there is an explosion of “things” being added to the network. But not just things. Our corporate nets are adding partners and their employees, contractors, vendors, clients, customers, potential customers and more. 25 years ago we were amazed by the million object directory - today we could conceivably add that many objects in a month.

Webinar Recording
Information Security at Work: Automating End-User Password Reset for Better Efficiency and fewer Headaches
Apr 29, 2015
In this webinar, KuppingerCole Senior Analyst Amar Singh and Thycotic CEO Jonathan Cogley will talk about essentials for the digital transformation of your enterprise: Managing your end user identities and offering end users self-service password reset abilities to increase help desk efficiency without compromising security.
Webinar Recording
Lean, Intelligent IAM Processes for the ABC - Agile, Business, Connected
Apr 24, 2015
The constantly accelerating pace of change in today's businesses and their requirements influence all types of organizations, their business and operational processes and the underlying IT. Keeping up to speed with agile, innovative businesses and their requirements increases the demand for intelligent IAM processes.
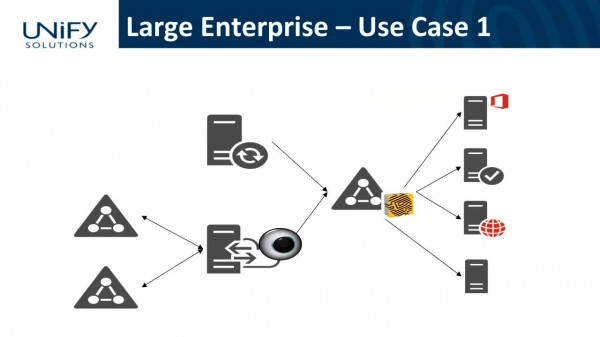
Webinar Recording
Enabling Cloud Governance
Apr 22, 2015
While many organisations have good governance over their on-premise identity and access management environment with authentication monitoring and attestation reporting this too often gets relegated to the “too-hard” basket when it comes time to migrating the Cloud services.

Webinar Recording
External IAM & Your CRM - A Winning Combination
Apr 22, 2015
Identity and Access Management (IAM) projects have the notorious reputation of being complex, time-consuming and expensive. Fresh thinking and new approaches are now changing how IAM solutions are being deployed so that you can enable revenue generating services faster than ever. One of these advances is the ability to integrate your IAM solution with your CRM – leveraging your customer and partner data as a powerful component of your IAM strategy. To learn more about the technology and the business benefits, we invite you to join our upcoming webinar.
Webinar Recording
Make your Enterprise Applications Ready for Customers and Mobile Users
Apr 17, 2015
Rapidly growing demand for exposing and consuming APIs, which enables organizations to create new business models and connect with partners and customers, has tipped the industry towards adopting lightweight RESTful APIs to expose their existing enterprise services and corporate data to external consumers. Unfortunately, many organizations tend to underestimate potential security challenges of opening up their APIs without a proper security strategy and infrastructure in place.
Webinar Recording
Monitor Your Cloud Administrators and Managed Service Operators – Avoid Privilege Abuse and Fraud
Apr 15, 2015
Both the use of cloud services and outsourcing services to MSPs (Managed Service Providers) are on the rise. Managing cloud services or opening on-premise, hybrid, and external services for management by external operators requires the ability for controlling access, particularly privileged operator and administrator access, to these services. Who can manage your cloud services, particularly the ones that offer just one shared administrative account? And who controls the access of external operators to your services?
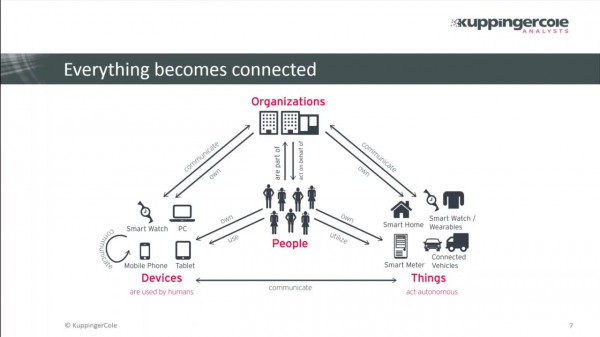
Webinar Recording
Access Management and Federation for the Agile, Connected Enterprise
Mar 11, 2015
Two things are for sure in IT today: The cloud is here to stay. And on-premise IT at least in medium-sized and large organizations will not disappear quickly. IT environments are increasingly becoming hybrid. This requires well thought-out solutions for connecting the on-premise and the Cloud environments. Furthermore, allowing access of mobile users, supporting cloud-based directories for consumers and business partners, or integrating with apps and things imposes new challenges.
Webinar Recording
Industrial Control System Security: Getting a Grip on OT Cyber Security
Mar 06, 2015
Are your operational technology (OT) networks hosting Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) systems, well secured? For many organizations, the answer is still “no”. Information security generally focuses on Information Technology (IT) networks and systems, not on the OT systems used in manufacturing, utilities and critical industrial infrastructures.
Webinar Recording
Managing the Password Chaos
Feb 13, 2015
More than 10 years ago, Bill Gates predicted the death of the password. A decade later, reality shows that passwords are still the most common authentication method. Security and costs of passwords are critical factors for enterprises and organizations.

Webinar Recording
Mastering the Digitalization of Business: Digital Identities and the Cloud
Jan 20, 2015
How to make use of cloud services and digital identities of employees, partners, customer and things to leverage your business to the next level
It is the combination of identity services, mobility support, and cloud services that allows organizations not only digitalizing their business, but keeping it secure anyway. It is about enabling business agility while not ending up with unprecedented risks. Combining business innovation with IT innovation, particularly around identities and the cloud, is the foundation for successfully mastering the digital revolution.
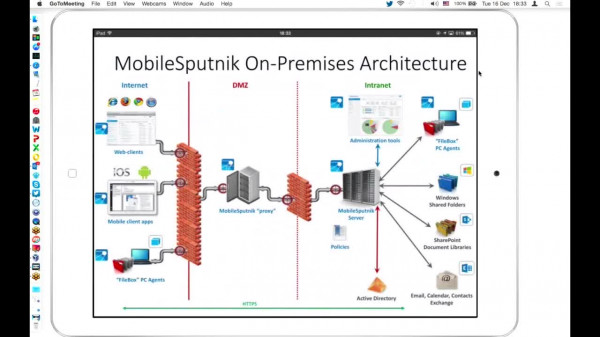
Webinar Recording
Secure Mobile Information Sharing: Adressing Enterprise Mobility Challenges in an Open, Connected Business
Dec 17, 2014
Fuelled by the exponentially growing number of mobile devices, as well as by increasing adoption of cloud services, demand for various technologies that enable sharing information securely within organizations, as well as across their boundaries, has significantly surged. This demand is no longer driven by IT; on the contrary, organizations are actively looking for solutions for their business needs.
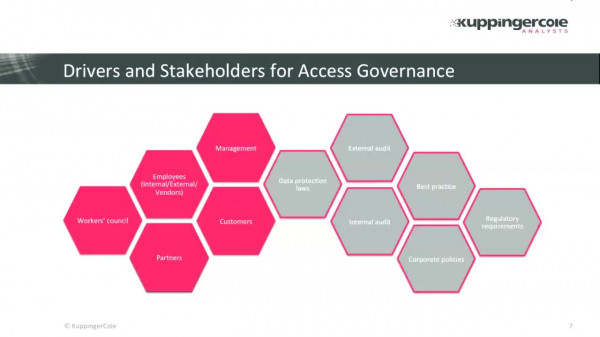
Webinar Recording
Understand Your Access Risks - Gain Insight Now
Dec 12, 2014
Access Intelligence: Enabling insight at any time – not one year after, when recertifying again
Imagine you have less work and better risk mitigation in your Access Governance program. What sounds hard to achieve can become reality, by complementing traditional approaches of Access Governance with Access Intelligence: Analytics that support identifying the biggest risks, simple, quick, at any time. Knowing the risks helps in mitigating these, by running ad hoc recertification only for these risks or even triggering automated changes. Instead of recertifying everything regularly, Access...
Webinar Recording
Access Governance for Today's Agile, Connected Businesses
Dec 10, 2014
In today’s fast changing world the digitalization of businesses is essential to keep pace. The new ABC – Agile Businesses Connected – is the new paradigm organizations must follow. They must connect to their customers, partners and associates. They must become agile to respond to the changing needs of the market. They must understand, manage, and mitigate the risks in this connected world. One important aspect of this is the governance of the ever-increasing number of identities – customers, things, together with their access.
Webinar Recording
Identity & Access Management als Fundament für das Digitale Business
Dec 05, 2014
Das Digitalzeitalter, die Verschmelzung der digitalen mit der „wirklichen“, der analogen Welt, verändert unser Geschäft grundlegend und irreversibel. Bestehende Geschäftsmodelle an die neuen Anforderungen anzupassen und neue Chancen wirksam und effizient zu nutzen, ist die große Herausforderung dieser Transformation und unserer Zeit. Plötzlich ist die IT überall und Bestandteil aller Ebenen der Wertschöpfung. Alle Beziehungen eines Unternehmens, insbesondere aber die zu Kunden und Geschäftspartnern, müssen neu gedacht werden. So auch die Informationssicherheit.

Webinar Recording
SAP Security Made Easy. How to Keep Your SAP Systems Secure
Nov 21, 2014
Security in SAP environments is a key requirement of SAP customers. SAP systems are business critical. They must run reliably, they must remain secure – despite a growing number of attacks. There are various levels of security to enforce in SAP environments. It is not only about user management, access controls, or code security. It is about integrated approaches.

Webinar Recording
Database Security On and Off the Cloud
Nov 19, 2014
Continued proliferation of cloud technologies offering on-demand scalability, flexibility and substantial cost savings means that more and more organizations are considering moving their applications and databases to IaaS or PaaS environments. However, migrating sensitive corporate data to a 3rd party infrastructure brings with it a number of new security and compliance challenges that enterprise IT has to address. Developing a comprehensive security strategy and avoiding point solutions for database protection is now more important than ever.
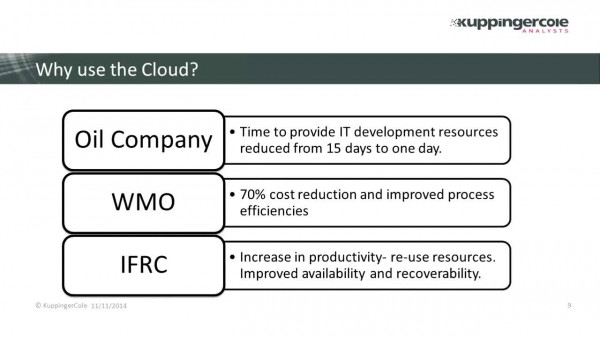
Webinar Recording
How to Protect Your Data in the Cloud
Nov 11, 2014
More and more organizations and individuals are using the Cloud and, as a consequence, the information security challenges are growing. Information sprawl and the lack of knowledge about where data is stored are in stark contrast to the internal and external requirements for its protection. To meet these requirements it is necessary to protect data not only but especially in the Cloud. With employees using services such as iCloud or Dropbox, the risk of information being out of control and leaking is growing. Incidents such as the iCloud leakage of photos are just the tip of the iceberg.

Webinar Recording
One Identity for All: Successfully Converging Digital and Physical Access
Nov 05, 2014
Imagine you could use just one card to access your company building and to authenticate to your computer. Imagine you had only one process for all access, instead of having to queue at the gate waiting for new cards to be issued and having to call the helpdesk because the system access you requested still isn’t granted. A system that integrates digital and physical access can make your authentication stronger and provide you with new options, by reusing the same card for all access infrastructures. Convergence saves money by reusing technologies. Convergence makes processes faster by...

Webinar Recording
IAM for the User: Achieving Quick-wins in IAM Projects
Oct 16, 2014
Many IAM projects struggle or even fail because demonstrating their benefit takes too long. Quick-wins that are visible to the end users are a key success factor for any IAM program. However, just showing quick-wins is not sufficient, unless there is a stable foundation for IAM delivered as result of the IAM project. Thus, building on an integrated suite that enables quick-wins through its features is a good approach for IAM projects.
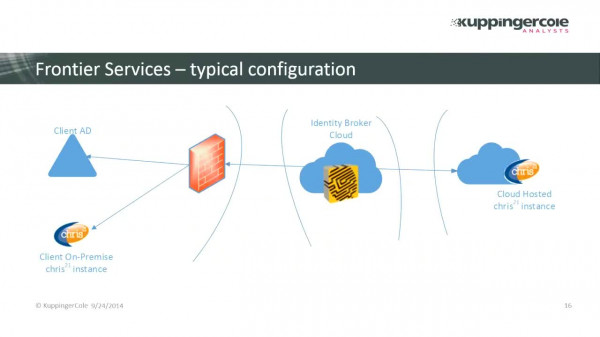
Webinar Recording
Intelligent Identity Management in the Cloud - A Use Case
Sep 24, 2014
Most organisations fail to plan identity management in the Cloud. They adopt a variety of software-as-a-service solutions each requiring its own identity repository with a periodic synchronisation that fails to provide sufficient governance over de-provisioned accounts. This webinar looks at the issues with managing identities in the Cloud and one potential solution.
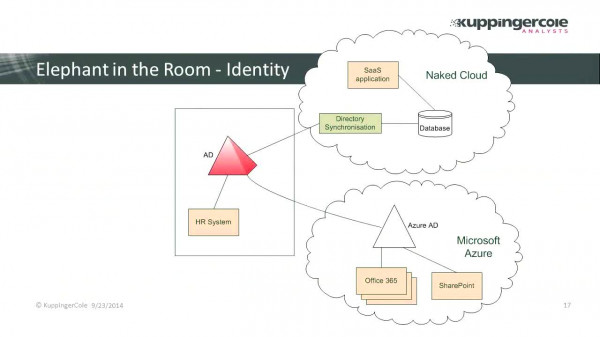
Webinar Recording
So Your Business is Moving to the Cloud - Will it be Azure or Naked Cloud?
Sep 23, 2014
Most companies do not plan their migration to the cloud. They suddenly find that there are multiple users of cloud services in their organisation, each of which was a good idea at the time but now form a disparate approach to cloud services with no strategic vision, a significant training impost and little governance over their cloud-based applications and infrastructure.
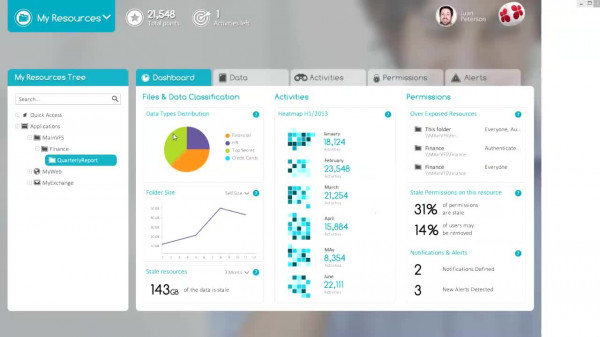
Webinar Recording
5 Steps to Protect Your Data from Internal & External Threats
Sep 11, 2014
Most organizations have already been hacked or been victims of data theft (internal or external), whether they know it or not – or know it and haven’t been willing to acknowledge it. Many are operating in specific regulatory environments, but aren’t in full compliance, leaving them vulnerable to lawsuits or even criminal prosecution.
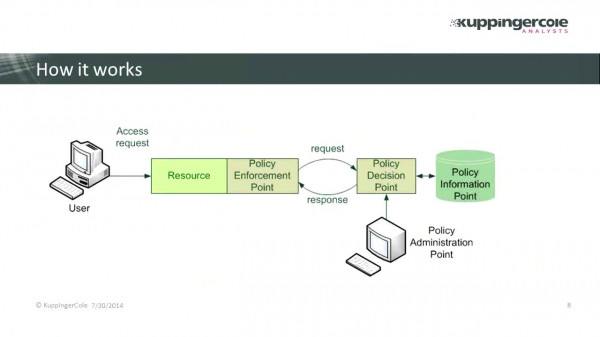
Webinar Recording
Identity Managed Data Loss Prevention - sleep well at night
Jul 30, 2014
It’s never been easier to control who has access to what, who authorised it, who’s access hasn’t been removed and to generate reports on it all. We’ll look at the direction of technological and standards development and discuss the ramifications – what do you have to do to exploit the potential?

Webinar Recording
How to share your Corporate Information with whomever you want - securely?
Jul 04, 2014
Organizations are facing a dilemma today. On one hand, they need to collaborate far more flexible than ever before. Employees want to use the Cloud and are mobile. Collaboration with business partners is ever-tightening. Employees already are sharing files with customers using Cloud services such as Dropbox, Skydrive, etc. On the other hand, information security concerns are growing and pressure from regulations is ever-increasing.
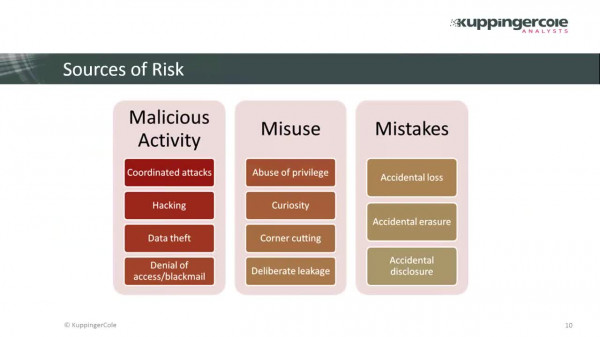
Webinar Recording
Can't see the wood from the trees?
Jun 25, 2014
The challenges you face are not getting any easier. You need to provision user access efficiently and effectively and maintain regulatory compliance while simultaneously protecting company assets by identifying and eliminating risk. It’s a daunting task. How can you quickly and easily assess access risk so you can prioritize the areas in your enterprise that require attention?
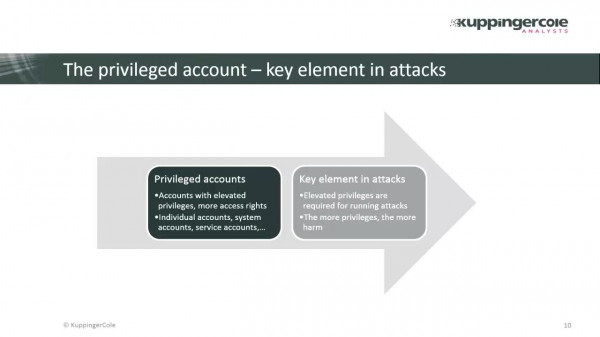
Webinar Recording
How to Stop the Insider Threat: Protect Yourself from Privileged Users
May 06, 2014
The attack landscape is changing. Targeted, advanced and persistent external attacks are increasing. However, despite all discussions about external threats, one thing is clear: The biggest threat is internal, and comes from your own users. Whether these are malicious or just human errors, the risk for your sensitive information is immense.

Webinar Recording
Extend your existing Active Directory to the Cloud
Apr 30, 2014
Most organizations use Microsoft Active Directory as a strategic element of their on-premise network infrastructure. However, handling external users such as customers and partners is not easy. This new ABC – the Agile Business: Connected – is the challenge.
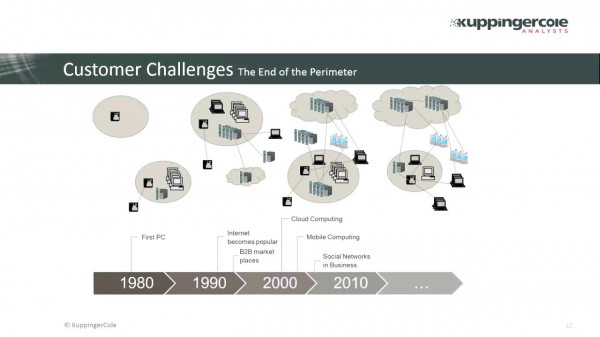
Webinar Recording
Identity and Access Management: Where to Start?
Apr 29, 2014
Many organizations – of all sizes – still have no or only a rudimentary IAM in place. When looking at IAM, it quickly turns out that this is about more than a single technology.
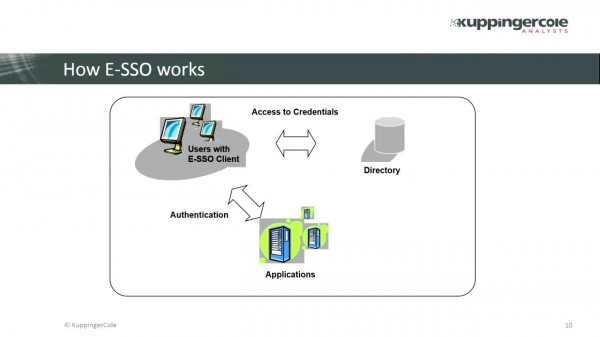
Webinar Recording
Enterprise Single Sign-On - is there still a need for?
Apr 10, 2014
In this KuppingerCole Webinar, we will look at Enterprise Single Sign-On (E-SSO) and the alternatives. Starting with the use cases for single sign-on and related scenarios, we will analyze the technical alternatives. We look at various aspects such as the time for implementation, the reach regarding applications to sign-on, users, and devices and compare the alternatives.
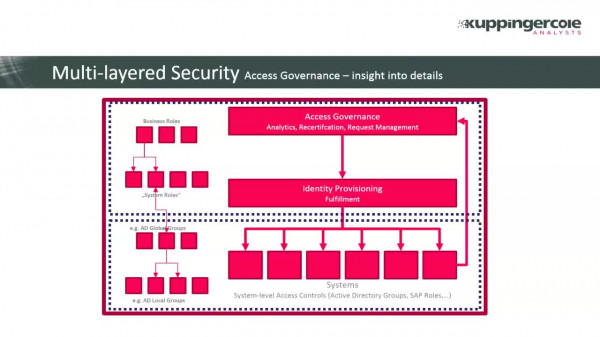
Webinar Recording
Migrating away from your current Identity Provisioning solution
Apr 09, 2014
Many organizations currently consider migrating away from their current Identity Provisioning solution. There are many reasons to do so: vendors became acquired and the roadmap changed; the requirements have changed and the current solution does not appear being a perfect fit anymore; a lot of money has been spent for little value; the solution does not suit the new requirements of managing external users and access to Cloud services...
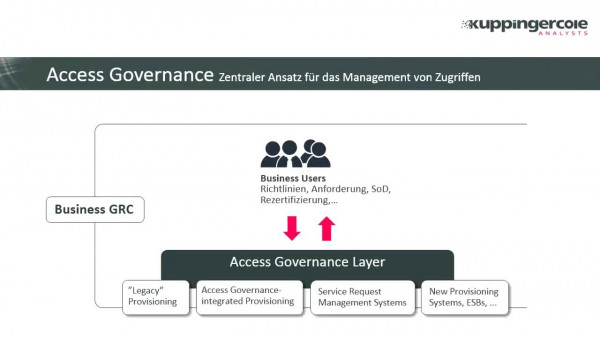
Webinar Recording
Die wahren Zugriffsrisiken kennen und verringern - real-time statt nur einmal jährlich
Apr 03, 2014
Access Governance ist inzwischen eine etablierte Disziplin innerhalb der Governance- und Informationssicherheitsorganisation von Unternehmen. Mit Access Intelligence-Funktionen werden vermehrt zusätzliche Analysedienste bereitgestellt, mit deren Hilfe man besondere Risiken beispielsweise durch eine ungewöhnliche Anhäufung von Zugriffsberechtigungen bei bestimmten Benutzern identifizieren kann.
Webinar Recording
One Identity for All - Efficient and Cost-effective Identity Management in the Cloud and for the Cloud
Mar 25, 2014
"To cloud or not to cloud?" - this is no longer the question. It is rather to what extent and depth enterprises leverage cloud computing. With identity and access management (IAM) solutions for their internal IT systems, enterprises have achieved a high level of security, transparency and compliance. They do not want to go back to the old days of erratic and insecure identity management when they have to deal with multiple cloud providers and their proprietary user management interfaces.
Webinar Recording
Mitigate Targeted Attacks with Privileged Account Analytics
Mar 25, 2014
Targeted attacks continue to hit the headlines as the pinnacle of cyber-attacks faced by businesses. Once the perimeter defenses fail to defend against targeted attacks, the mitigation focus has shifted to inside the network. Security analytics focused on privileged account activity can increase detection rates, cost less and be easier to operate. Learn how advanced and insider attacks maneuver throughout your organization, and where and how to intercept them with targeted privileged account analytics.
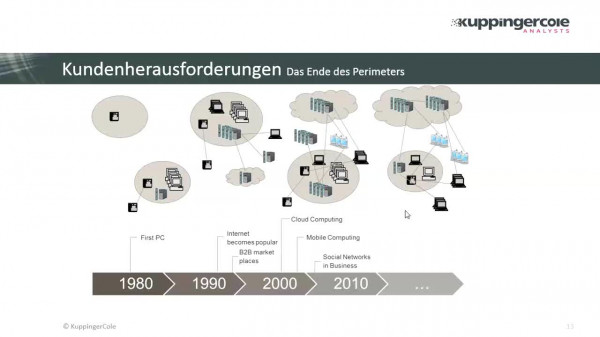
Webinar Recording
Das neue ABC: Agile Business, Connected
Mar 20, 2014
Die “Identity Explosion” stellt Unternehmen vor neue Herausforderungen. Statt sich beim IAM (Identity und Access Management) primär um die Mitarbeiter zu kümmern, muss man im „Extended Enterprise“ auch Geschäftspartner und oftmals Millionen von Kunden verwalten und ihnen kontrollierten Zugriff auf interne Systeme ebenso wie Cloud-Lösungen geben.
Webinar Recording
Secure Information Sharing: Microsoft Azure RMS Enabling your Organisation to Securely Share Any Document with Anyone
Mar 12, 2014
The challenge of all organizations in these days of connected businesses and their need for agility in changing markets – the new ABC: Agile Business, Connected – is creating new challenges for IT. One of these challenges is securely sharing information.

Webinar Recording
Marketing will das Facebook-Login. Und was ist mit der Informationssicherheit?
Feb 18, 2014
Unternehmen verändern sich schneller denn je. Die Zusammenarbeit mit Kunden und Geschäftspartnern in neuen Geschäftsmodellen führt zu immer neuen Anforderungen an die IT. Diese muss reagieren und die Business-Innovationen unterstützen, statt sie zu behindern. BYOI (Bring Your Own Identity) und Social Logins sind sichtbarer Ausdruck dieser Innovationen und deshalb von hohem Gewicht.

Webinar Recording
Informationen schützen, Risiken reduzieren: Privilegierte Zugriffe kontrollieren
Jan 28, 2014
Geschäftliche Informationen machen einen wesentlichen Teil des Unternehmenswertes aus. Diese Informationen sind aber gefährdeter als jemals zuvor. Diese Gefahr entsteht aber keineswegs nur durch externe Angriffe, sondern in hohem Maße immer noch durch interne Anwender mit umfassenden Berechtigungen.

Webinar Recording
Zugriffsrechtsmanagement - Risiken erfolgreich minimieren
Jan 16, 2014
Aussagen von Auditoren zu Risiken durch privilegierte Nutzer sind nicht wirklich nötig, um ein besonderes Augenmerk auf privilegierte Zugriffe zu werfen.

Webinar Recording
Big Data - The Holy Grail for Information Security?
Dec 19, 2013
With an increasing number of fraud incidents, customer data losses and other breaches on one side, and the disappearance of the classical perimeter because of the need to finally extend the enterprise to partners and customers on the other side, introducing Big Data for Security Analytics seems to be the logical next level for your information security strategy. In this webinar, KuppingerCole´s Principal Analyst Martin Kuppinger will talk about the benefits and challenges using Big Data for security analytics, and he will draw your attention to the additional risk that may come along with...

Webinar Recording
Business Ready IAM with Sony Computer Entertainment and Simeio Solutions
Dec 10, 2013
In the age of BYOD, mobile, connected & extended enterprise, securing the perimeter isn´t enough anymore to keep the bad guys out. Organizations are leveraging the power of Identity and Access Governance to enable business, for both the enterprise and with their customers. It is important to have a sound foundation that aligns with your business strategy, while keeping pace with market trends and customer needs.
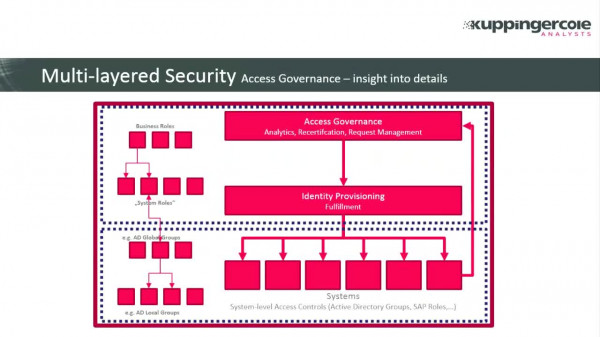
Webinar Recording
Time to Review and Rethink: Does Your Current IAM Still Suit Your Needs?
Dec 04, 2013
Many organizations have started their journey into the world of IAM several years ago.

Webinar Recording
Moving Access Governance to the Next Level: Beyond Check-box Compliance
Nov 19, 2013
Identity Access Governance and Intelligence (IAG/IAI) is one of the key disciplines of today’s Information Security. While many organizations still are in the deployment phase and focus on fulfilment of regulatory compliance in some selected systems, the challenges already have changed. It is not sufficient to govern access in SAP environments or some few other IT systems to really tackle all of today’s Information Security challenges. The threat landscape is changing and attacker tactics have fundamentally changed, resulting in adversaries that are more formidable than ever before, and who...

Webinar Recording
Negotiating the Cloud Standards and Advice Jungle
Nov 05, 2013
The cloud is a hot topic and most SDOs (Standards Defining Organizations) have at least one initiative in this area. This plethora of initiatives has confronted the users of cloud services as well as CSPs (Cloud Service Providers) with a jungle of frameworks, standards, advice and certifications. In this webinar, KuppingerCole´s Senior Analyst Mike Small will provide a summary of these and some practical advice on their relevance and usability.
Webinar Recording
Identity Information Quality
Oct 23, 2013
Identity Information Quality has been a challenge since the early days of IAM, and it remains top of the list in many projects. Good quality of identity information is the foundation of any information security initiative. In this webinar, we will discuss strategies and solutions to improve identity data quality.
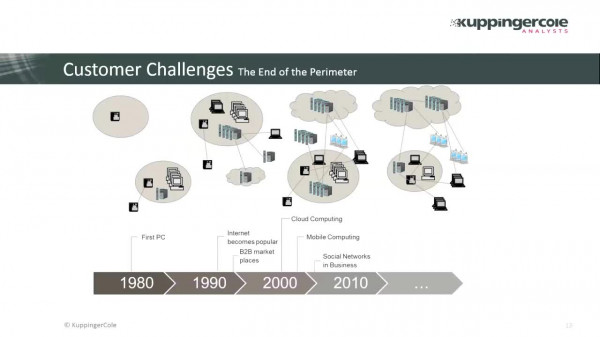
Webinar Recording
Extended Enterprise - The New Scope of Information Security
Oct 18, 2013
Managing access to information and services deployed anwhere for employees, partners and customers in any context on any type of device owned by any party involved - there couldn´t be a much more challenging task. In this webinar, KuppingerCole´s Principal Analyst Martin Kuppinger will introduce you into the new concept of managing the "explosion" of identities and devices.

Webinar Recording
Strategic Information Security Investment Planning - The Legal Perspective
Oct 16, 2013
The ever increasing challenge of meeting regulatory compliance is putting more and more pressure on your information security budget? Then it may be time to include some legal arguments to convince your management that you need to spend more on information security. In this webinar, KuppingerCole´s Fellow Analyst, Lawyer and Data Protection expert will help you finding these arguments.
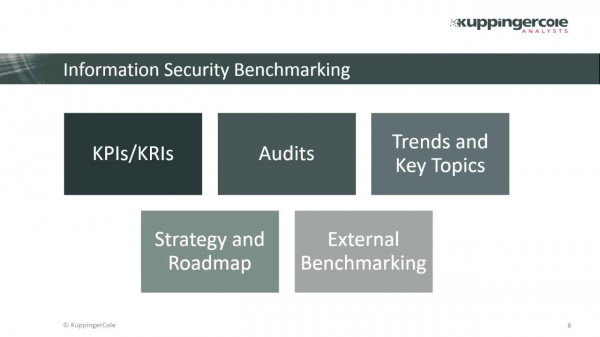
Webinar Recording
Approaches and Elements of Maturity Benchmarking in Information Security
Oct 09, 2013
Information Security is hard to measure. If your security strategy fits well into your organization´s needs, then the risks are low and there is hardly anything happening that you could measure. Or, the other way round - the more you can measure, the more your job is at risk. True? Join us in this webinar to find out.

Webinar Recording
Wie Sie Ihre Daten unausspionierbar transportieren und speichern
Oct 09, 2013
Die neuesten Enthüllungen über die Angriffe westlicher Geheimdienste, allen voran der NSA, auf kryptografische Implementierungen sorgen verbreitet für Unsicherheit darüber, wie man sich mit welchen heute verfügbaren Werkzeugen noch wirksam vor dem Ausspionieren schützen kann. In diesem Webinar sprechen KuppingerCole Senior Analyst Prof. Dr. Sachar Paulus und Lutz Emrich vom SIZ über die Auswahl und den Einsatz solcher Werkzeuge. Dieses Webinar baut auf unser einführendes Webinar mit dem Titel "Verschlüsselung richtig einsetzen" auf.
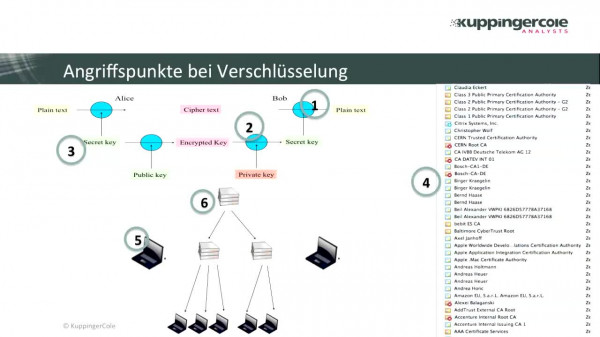
Webinar Recording
Verschlüsselung richtig einsetzen
Oct 09, 2013
Die NSA und ihre Helfer in Europa und Deutschland haben gewaltige Möglichkeiten, sich in Ihr berufliches und privates digitales Leben unbemerkt einzuschleichen. Die jüngsten Enthüllungen zur Entschlüsselungspraxis der NSA und den Zugriff auf Smartphones steigern einerseits die Beunruhigung. Andererseits aber liefern sie genügend Details über die Praxis staatlichen Hackertums, um eine Verteidigungslinie definieren zu können. Prof. Dr. Sachar Paulus, Krypto-Experte und KuppingerCole Senior Analyst, gibt Ihnen 5 Tipps, wie Sie einen wesentlichen Teil staatlich organisierter Angriffe auf Ihre...
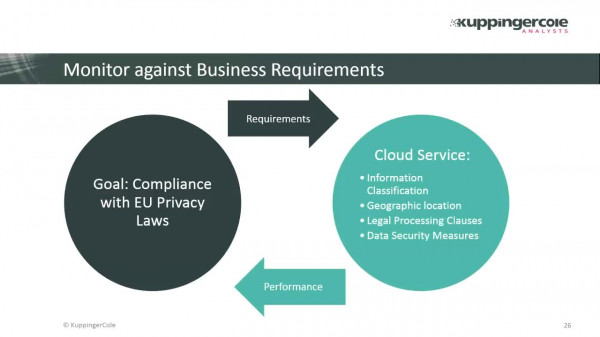
Webinar Recording
How Mature is Your Cloud?
Oct 04, 2013
Cloud services are outside the direct control of the customer organization and their use places control of the IT service and infrastructure in the hands of the CSP (Cloud Service Provider). A structured approach is essential to ensure organizational readiness for the cloud, to select the right service to meet business needs and other non-functional requirements like security and compliance and to enable that service to be assured. This webinar gives an introduction into cloud maturity assesment basics and is a great preparation for the KuppingerCole Information Risk & Security Summit...

Webinar Recording
Authorization as a Calculated Risk
Sep 26, 2013
Access to corporate information often is based on binary, either/or propositions, without the context of an access request being taken into account. The level of assurance that the requesting person is who she claims to be is not determined, missing the opportunity of establishing a metric for the level of security of the connection. In the first part of this webinar, KuppingerCole Senior Analyst Dave Kearns, along with guests from Nok-Nok Labs and Certivox, will show you how going beyond passwords to a risk- and context-based authentication and authorization would help you to reach the...

Webinar Recording
The Business Side of the API Economy: Enabling the Agile, Connected Enterprise
Sep 24, 2013
Today’s businesses have to be far more agile than ever before. Competing on global scale, economic turmoil, rapid innovation and other factors put pressure on organizations. One of the results is that businesses have to be better connected with other businesses and customers than ever before. They have to be faster in their own business processes and the processes that connect them with others. They have to make more out of information, by combining information from various sources, including openly available data. Smart information that is based on combining information from various...

Webinar Recording
The Future of Authentication and Authorization
Jul 23, 2013
Clearly, there is a trend towards approaches for strong, simple, and flexible authentication, beyond passwords. However, just talking about multi-factor authentication and password vaults is not sufficient. What organizations should evaluate are versatile authentication and, as the next and logical step, context- and risk-based authentication and authorization. That is the real trend. In this webinar, KuppingerCole Senior Analyst Dave Kearns will talk about the bigger picture on the future of authentication and authorization.
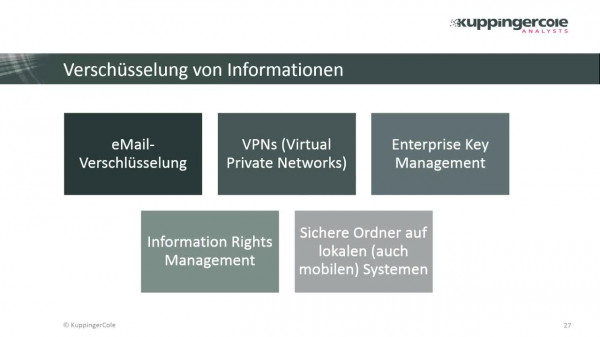
Webinar Recording
PRISM: Wie schütze ich mein Unternehmen wirksam vor Wirtschaftsspionage?
Jul 10, 2013
Das organisierte und systematische Ausspionieren von Privatpersonen und Unternehmen durch staatliche Einrichtungen ist zwar nicht neu und keineswegs auf US-Einrichtungen beschränkt. Aber es ist durch die jüngsten Enthüllungen in Zusammenhang mit dem PRISM Projekt der US-Sicherheitsbehörde NSA einmal mehr in unser Bewußtsein gerückt, dass wir durch solche Übergriffe verwundbarer geworden sind und der anrichtbare Schaden nicht selten existenzbedrohliche Ausmaße annimmt. In diesem Webinar gibt Ihnen KuppingerCole Gründer Martin Kuppinger Empfehlungen, wie Sie Ihre wirklichen Gefahren erkennen...

Webinar Recording
Cloud Assurance & Cloud Risk Awareness in the Light of PRISM
Jul 05, 2013
With the recent unveiling of systematic and large scale espionage activities conducted by US government agencies, the level of trust into cloud services run and controlled by 3rd parties has reached a new low. Google, Facebook, Skype, Apple, Verizon and many other service providers did open their databases to NSA and enabled them to search your mails and documents for information considered as valuable in whatever context. In this webinar, KuppingerCole´s Senior Analyst Mike Small will give you an introduction on how to identify the key assurance challenges of the different kinds of Cloud...
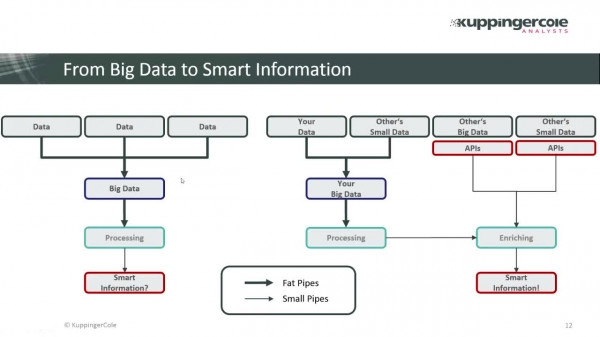
Webinar Recording
Quo Vadis SAP?
Jun 06, 2013
Martin Kuppinger and Craig Burton will discuss about how the "Computing Troika" Cloud, Mobile and Social Computing will necessarily influence SAP´s products and Services strategies.

Webinar Recording
The Common Credentials Dilemma - How to Get a Grip on Password Sprawl for Privileged Accounts
May 10, 2013
A lot of organizations still have not mitigated one of the most severe IT security risks: Password sprawl for privileged accounts. Privileged accounts are accounts that have elevated privileges. They can be both personal, such as business users with high-level privileges, and shared, such as administrator, dba, or root – not to speak of all the admin accounts of network equipment etc. Unfortunately, a large portion of accounts with highly elevated privileges is shared. To manage these accounts, to avoid password sprawl, and to in consequence mitigate risks, both guidelines and technologies...
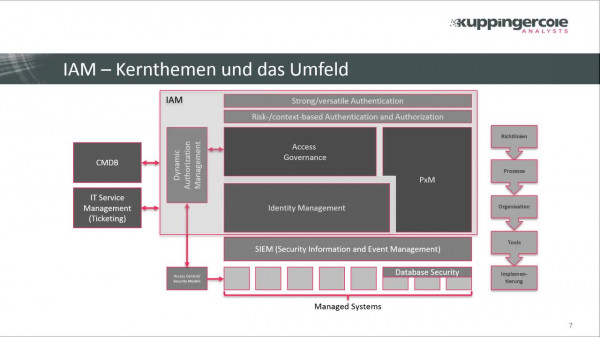
Webinar Recording
Benutzer- und Berechtigungsmanagement für den Mittelstand leicht gemacht
Apr 30, 2013
Das Benutzer- und Berechtigungsmanagement ist ein Thema für Unternehmen jeder Größenordnung. Während große Unternehmen meist schon seit längerer Zeit den Schritt hin zu einer zentralen Infrastruktur für IAM (Identity and Access Management) gemacht haben, ist die Situation im Mittelstand häufig noch durch das Fehlen einer Gesamtlösung geprägt. Systeme wie das Active Directory, SAP, Produktionssysteme und andere wichtige Business-Systeme werden unabhängig voneinander verwaltet. Das Risiko für die Informationen ist entsprechend hoch – gerade auch für das geistige Eigentum, das Firmenwissen,...
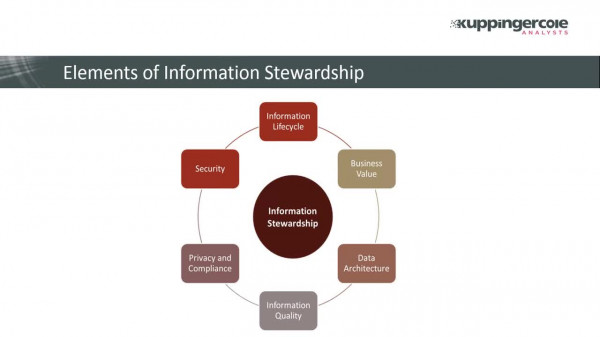
Webinar Recording
Bridging (the gap between) Access Governance and Privileged User Management… and they lived happily ever after!
Apr 25, 2013
Access Governance (modeling a desired state, then detecting and remediating risks deriving from any deviation from such a model) and Privileged User Management (controlling the activity of the SysAdmins, operating at the system level) have been historically taught as a single mantra within Identity Management lectures, but ultimately treated as different technologies and implementation projects.
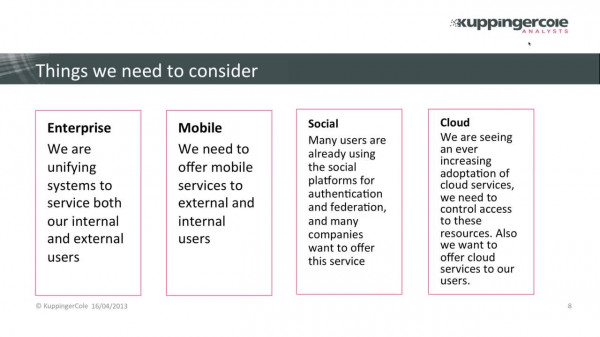
Webinar Recording
Rapidly Evolving Identity & Access Management to Meet Today´s B2C & Cloud Challenges
Apr 17, 2013
The world of Identity and Access Management is growing in scope, and must change and adapt faster than ever before. CIOs are under pressure to shift from employee-centric IAM to consumer-facing IAM that drives top-line revenue. As a result, they are quickly learning that legacy enterprise IAM solutions are not designed to solve today´s web challenges (enterprise, cloud, social, mobile).
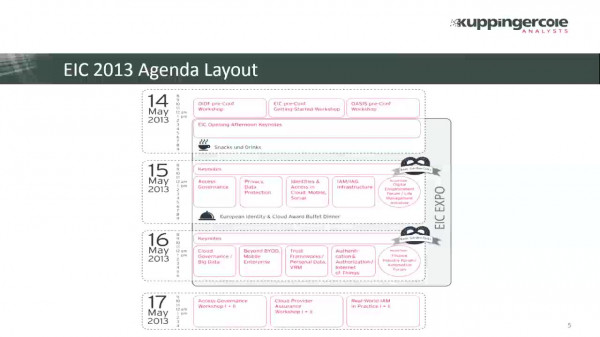
Webinar Recording
European Identity & Cloud Conference 2013 Preview
Apr 10, 2013
The European Identity & Cloud Conference (EIC) 2013 once again will be Europe´s most important event exploring the future of information technology. Join us in this webinar for a compehensive preview on this year´s key topics and speakers.
Webinar Recording
Extending Data Governance Beyond the Database
Mar 22, 2013
Traditionally, enterprise data governance started within your database management system by establishing the appropriate access control and auditing policies to prevent unauthorized access and demonstrate those controls. Now a new generation of database security solutions allow organizations to extend database security policies beyond the database management system and across the enterprise.

Webinar Recording
Protecting Information in an Unstructured World
Mar 20, 2013
Join KuppingerCole Senior Analyst Mike Small and TITUS CTO Steph Charbonneau in this Webinar to learn the Major causes of information loss and leakage and how to avoid them by bringing structure to Information through Information Stewardship.
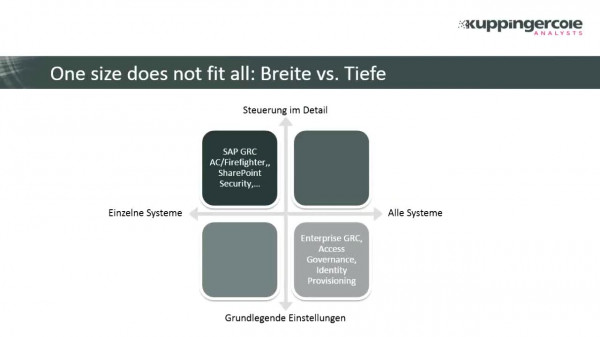
Webinar Recording
SAP Identity Management und GRC: Miteinander statt nebeneinander!
Mar 15, 2013
In diesem Webinar beschreibt KuppingerCole Principal Analyst Martin Kuppinger unterschiedliche Architekturkonzepte, verfügbare Produkte und deren mögliche Rolle in IAM / GRC-Gesamtlösungen im SAP-Umfeld. Richtig gemacht, können Unternehmen durch einen integrativen Ansatz für IAM und GRC ihre Audit-Anforderungen besser erfüllen, schlankere Prozesse realisieren, die Arbeitslast für Fachbereiche reduzieren und eine schlankere und damit günstigere IT-Infrastruktur für IAM und GRC umsetzen.

Webinar Recording
European Identity & Cloud Conference 2013 - Agenda Preview
Mar 12, 2013
The European Identity & Cloud Conference (EIC) 2013 once again will be Europe´s most important event exploring the future of information technology. Join us in this webinar for a compehensive preview on this year´s Agenda and speakers.

Webinar Recording
BYOD, Social Networking, Cloud - sicher und kalkulierbar
Mar 11, 2013
Die Einbindung mobiler Endgeräte, seien Sie im Eigentum des Mitarbeiters oder des Unternehmens, die Nutzung von Social Media im Unternehmen und der vielfältige Einsatz von Cloud-Anwendungen - all dies ist Alltag geworden und stellt IT-Professionals in den Unternehmen jeden Tag vor neue Herausforderungen.

Webinar Recording
Rethinking Identity and Access Governance in a World of Change and Complexity
Feb 01, 2013
The convergence of Cloud, Mobile and Social Computing create strong new opportunities and change the way we use Information Technology, shifting the control into the hands of the users. Governing identity and access in such a complex environment is key to success. Join us in this webinar to discuss these challenges.

Webinar Recording
European Identity & Cloud Conference 2013 Preview
Jan 22, 2013
The European Identity & Cloud Conference (EIC) 2013 once again will be Europe´s most important event exploring the future of information technology. Join us in this webinar for a compehensive preview on this year´s key topics and speakers.
Webinar Recording
Expand your GRC Controls to Cover all Systems - How to Make SAP GRC Work in a Heterogeneous World
Dec 13, 2012
SAP GRC, especially with the new release, is a key component in the GRC (Governance, Risk Management, Compliance) strategies and implementations of many organizations. It provides a broad functionality, but it is mainly targeted at SAP environments. Even while SAP in many organizations is the core business environment, auditors have started looking at other environments as well – for example the Microsoft Windows and SharePoint infrastructure which holds most of the unstructured data. In addition, there are several industries and many organizations which have a series of other core business...
Webinar Recording
Using IAM Technology to Protect Information, to Defend the Brand & Increase Business Productivity
Dec 05, 2012
Identity & Access Management first and foremost is a business dimension and should be process-oriented and results-driven. In this webinar you will learn how to enable business owners to decide and be accountable of wo gets access to what.
Webinar Recording
Access Governance und dynamische Zugriffsteuerung kombiniert: So machen Sie ihre IT-Sicherheit fit für die Zukunft
Dec 03, 2012
Herkömmliche Konzepte für die Informationssicherheit, bei denen Zugriffsberechtigungen basierend auf vergleichsweise starren Gruppen oder Rollen in Form von statischen Konstrukten reichen heute nicht mehr aus, um den aus den großen Trends Cloud Computing, Mobile Computing und Social Computing wirksam begegnen zu können. In diesem Webinar lernen Sie, wie sich Access Governance weiterentwickeln muss und welche Rolle die dynamische Zugriffssteuerung in Zukunft spielen wird.
Webinar Recording
Reach the Next Maturity Level in your IAM Deployment - Beyond Classical Provisioning
Nov 30, 2012
Cloud, Mobile, Social Computing - IAM requirements are rapidly changing and need to go beyond classical provisioning. In this webinar, KuppingerCole´s Principal Analyst Martin Kuppinger will guide you through these new challenges and talk about maturity levels of IAM deployments. Quest Software (now part of Dell) Principal Solutions Architect Paul Walker will contribute a number of best practice examples and talk about his experience from migrating existing provisioning environments to up-to-date flexible and future-proof solutions.
Webinar Recording
The Strategic Approach to Cloud Computing. From Tactics and Chaos to Efficiency
Nov 08, 2012
Selecting your Cloud Service Provider right and making sure that he steadily delivers on his promise - this needs processes in place at your organization enabling a structured way of selecting an appropriate cloud service from a myriade of offerings availabe in the market, and laying the foundations for effective and efficient cloud audits. Join this webinar to learn how to create such processes and reduce risks of high migration efforts, unnecessary costs or even unavailability of critical services.
Webinar Recording
Best Practices for Business-Driven Identity & Access Management
Nov 07, 2012
Social Computing, Mobile Computing and the Cloud are challenging your enterprise´s security strategy and create the need for a new look at IAM. In this webinar, Martin Kuppinger (KuppingerCole) and Deepak Taneja (Aveksa) will talk about the changing requirements for Identity and Access Management in global organizations.
Webinar Recording
Identity Management as a Service (IdMaaS) - the Dope or are we Duped?
Oct 31, 2012
Big players like salesforce.com entering the market: Will this redefine the way we do IAM and solve our challenges in the days of Cloud Computing, Mobile Computing, and Social Computing?

Webinar Recording
Identity in an API Economy
Oct 17, 2012
In an API Economy, everyone and everything has an API. That means 26 billion APIs by the year 2015. What is your organization doing to prepare for this fundamental shift in IT infrastructure? Join KuppingerCole´s Distinguished Analyst Craig Burton and Layer 7 Technologies CTO Scott Morrison in this webinar to understand more about the API Economy and the role of Identity for your organization.
Webinar Recording
Risiken erkennen und wirksam vermeiden: Integrierte Ansätze und Lösungen für IT GRC
Oct 10, 2012
Als böten traditionelle Infrastrukturen mit ihren Schwachstellen und Angriffspunkten nicht bereits genügend Risiken, machen IT-Konsumerisierung, Social Media im Unternehmen und alle damit verbundenen Veränderungen die Ungewissheit zum Standard. Traditionelles Risk Management stößt hier an seine Grenzen. In diesem Webinar gibt Ihnen KuppingerCole Senior Analyst Prof. Dr. Sachar Paulus einen Überblick über die aktuellen Trends, Ansätze und Lösungen im Bereich IT-GRC. Danach spricht Mark Fischer von ITConcepts über seine Praxiserfahrungen bei der Einfürhung von IT-GRC-Lösungen.

Webinar Recording
Risiken vermeiden beim Management privilegierter Identitäten
Sep 28, 2012
Komplexe Organisationsstrukturen, Legionen unterschiedlicher Zielplattformen und -Systeme, kombiniert mit einer großen Zahl schlecht dokumentierter Legacy-Systeme - das Management privilegierter Benutzerkonten und die von solchen Konten ausgehenden hohen Risiken für die Informationssicherheit erfordert viel Aufmerksamkeit, ein tiefes Verständnis für die Compliance-Anforderungen, die an Ihr Unternehmen gestellt werden, und vor allem flexible Lösungen. In diesem Webinar erhalten Sie einen Überblick über die unterschiedlichen Lösungsansätze des Privileged Identity Management und deren...
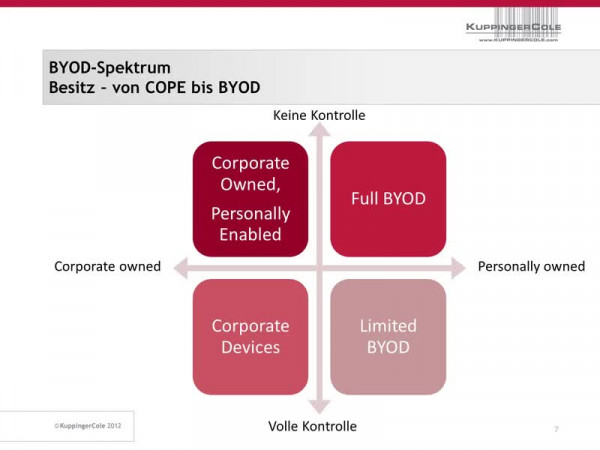
Webinar Recording
BYOD, Social Networking, Cloud - sicher und kalkulierbar
Sep 20, 2012
Die Einbindung mobiler Endgeräte, seien Sie im Eigentum des Mitarbeiters oder des Unternehmens, die Nutzung von Social Media im Unternehmen und der vielfältige Einsatz von Cloud-Anwendungen - all dies ist Alltag geworden und stellt IT-Professionals in den Unternehmen jeden Tag vor neue Herausforderungen. In diesem Webinar wird Martin Kuppinger, Principal Analyst bei KuppingerCole, darüber sprechen, wie die Unternehmens-IT die Erschließung des Nutzens dieser Trends ermöglicht, ohne die damit verbundenen Risiken für Ihre Informationssicherheit zu erhöhen.
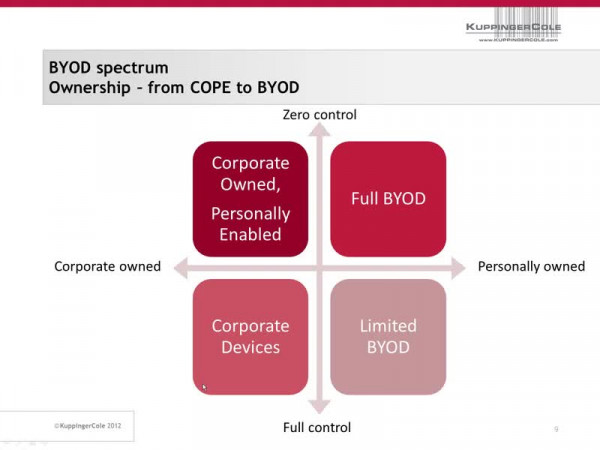
Webinar Recording
Preparing Your Enterprise for the Generation Y: BYOD & Mobile Device Management
Sep 19, 2012
A plethora of mobile devices are invading the enterprise at incredible speed, raising issues in areas like access control, policy enforcement, security of confidential data on users’ devices, and many others. Practices of “bring your own device,” (BYOD) and “company owned, personally enabled,” (COPE) are trying to describe methods of mitigating the risks involved. In this training, KuppingerCole Principal Analyst Martin Kuppinger will help IT professionals to find their best way through the myriad of recommendations and solutions related to this issue, and implement the right corporate...
Webinar Recording
SAML is Dead. Long Live SAML!
Sep 17, 2012
Is SAML a dead protocol or just a walking Zombie ready to consume all enterprise brains? Or is it yet alive and well both in legacy and the future? Attend this webinar to join the discussion KuppingerCole´s Distinguished Analyst Craig Burton about health and well being of the Federated sign-on protocol of choice -- SAML.
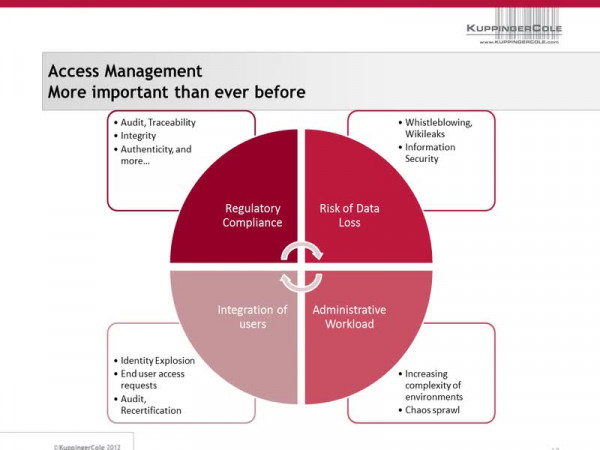
Webinar Recording
XACML and the Externalization of Authorization: How to do it Right
Aug 15, 2012
This training will give an overview about XACML and the concepts behind, from the way policies are expressed to the different components like PEPs, PDPs, or PAPs. It also will look at the shortcomings XACML currently has and how to best deal with them. It will look at different approaches in which XACML currently is used, showing the breadth and potential limitations of XACML. And it will discuss where to better not use XACML itself but to “translate” things.
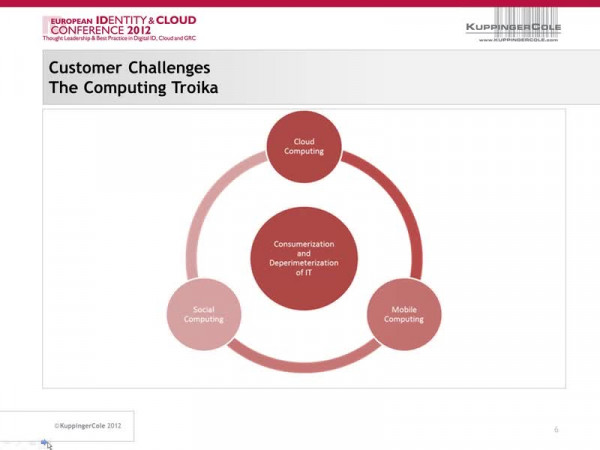
Webinar Recording
Preparing Your Enterprise for the Generation Y: BYOD & Mobile Device Management
Aug 08, 2012
A phletora of mobile devices are invading the enterprise at incredible speed, raising issues in areas like access control, policy enforcement, security of confidential data on users’ devices, and many others. Practices of “bring your own device,” (BYOD) and “company owned, personally enabled,” (COPE) are trying to describe methods of mitigating the risks involved. In this training, KuppingerCole Principal Analyst Martin Kuppinger will help IT professionals to find their best way through the myriad of recommendations and solutions related to this issue, and implement the right corporate...
Webinar Recording
Enterprise Role Management Done Right: Building the Bridge Between Business and IT
Jul 23, 2012
Enterprise Role Management still is a key topic when it comes to efficiently manage large groups of users. The art of clearly defining projects for role discovery and implementation, architecture model development and lifecycle maintenance with regards to scope and resources is your most important takeaway from this training.

Webinar Recording
Life Management Plattformen & die Zukunft des Social Networking
Jul 18, 2012
Social Networking steckt noch in den Kinderschuhen, der eher suboptimal sich entwickelnde Kurs der Facebook-Aktie mag ein Indiz dafür sein. Social Networking wie wir es heute kennen, basiert in der überwiegenden Zahl der Geschäftsmodelle darauf, dass die Nutzer weitgehend auf Privatspäre und Kontrolle über ihre persönlichen Daten verzichten. Durch die sich häufenden Fälle von Datenmissbrauch und Identitätsdiebstahl wirkt dieser Verzicht mit jedem Tag unangebrachter. Life Management Plattformen bringen Social Networking und Privatsphäre zusammen und schaffen die Basis für neue...
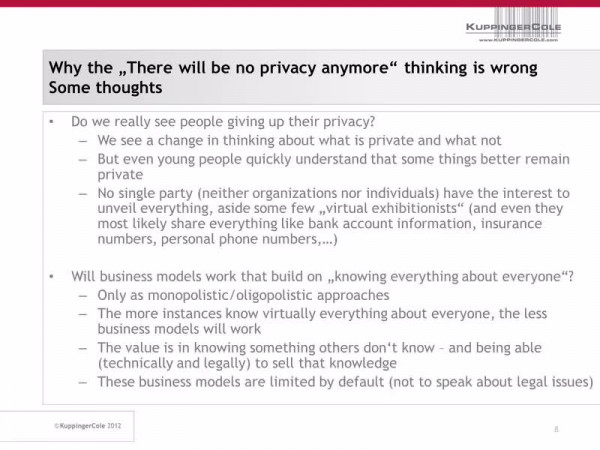
Webinar Recording
How to Unleash the Power of Life Management Platforms
Jul 18, 2012
Life Management Platforms will change the way individuals deal with sensitive information like their health data, insurance data, and many other types of information – information that today frequently is paper-based or, when it comes to personal opinions, only in the mind of the individuals. In this webinar, KuppingerCole Founder and Principal Analyst Martin Kuppinger will describe, why Life Management will be a key trend and how it will influence your enterprise.
Webinar Recording
Intelligent Access Management - Vorsprung vor dem Auditor
Jul 04, 2012
Nie war es wichtiger als heute, genau darüber Bescheid zu wissen, wer wozu berechtigt ist und wer was getan hat. In diesem Webinar geht es um das intelligente Management von Zugriffsrechten. Um Risiken zu reduzieren, Compliance sicherzustellen und um den Anwendern selbst die Möglichkeit zu geben, ihre Zugriffsrechte zu organisieren.
Webinar Recording
Choosing the Right Cloud
Jun 28, 2012
The rise of cloud computing has changed the rules for optimising your IT strategy. However within cloud computing there are many choices. Making the right choices can save time and money making the wrong choices can increase risks. This training will look at how to choose the right cloud for your business need.
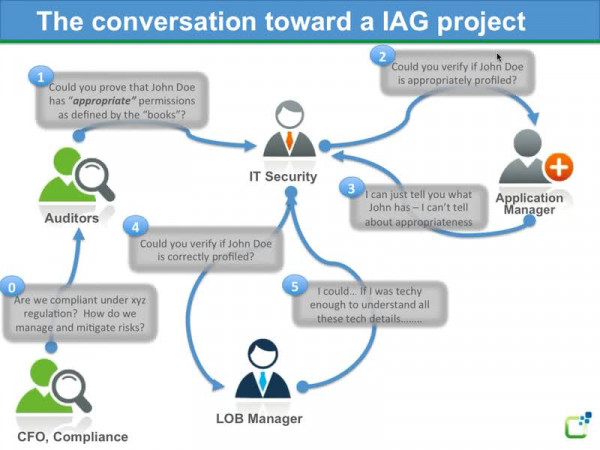
Webinar Recording
Quantifying Access Risk: How to Sell the Access Governance Project to your CFO
Apr 26, 2012
How can Access Risk be measured and made visual? How can it be used to prioritize processes such as Access Certification or Role Modeling? This webinar aims to explain new methodologies for Access Risk scoring to prioritize corrective actions and justify to your CFO why investment done on Identity & Access Governance project is good value for money.

Webinar Recording
Identity & Access Management in the Cloud: Real or a Mirage?
Mar 30, 2012
Traditional IAM solutions have not kept pace with cloud innovation. Therefore, new approaches to identity and access management are gaining ground. Should you move your IAM infrastructure to the cloud? What is the role of related standards? These and more questions will be addressed in this webinar.

Webinar Recording
Conducting an Orchestra - The New Role of IAM
Mar 23, 2012
With the loss of control over many resources through current trends like BYOD (bring your own devices) and usage of cloud services, enterprise IT is going through a radical change. In this webinar, you will learn about the new role of Identity & Access Management as an information security cornerstone.

Webinar Recording
Returning (or finally bringing?) Identity and Access Management (IAM) to the User
Mar 22, 2012
IAM needs the involvement from the end users and their business line managers, because it is there where access related risks can be handled best. Join us in this webinar to discuss, how you can leverage acceptance of your IAM solution.
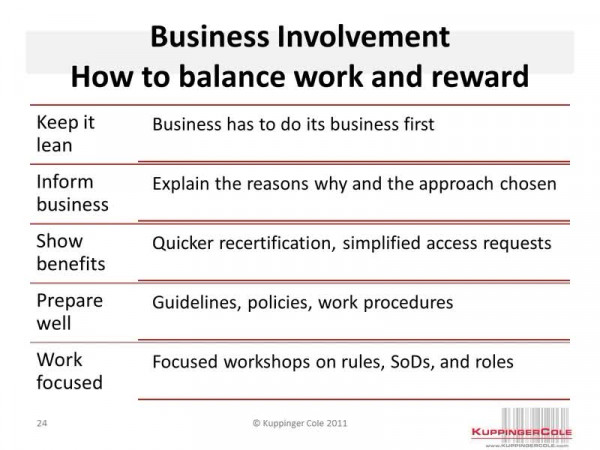
Webinar Recording
Access Risks - from SAP to the Outer Space: an Identity & Access Governance Journey
Mar 14, 2012
Access Governance applies across the entire application landscape, but has the largest impact on SAP where key business processes are managed. As SAP pose unique Access Security needs, it tends to be left in isolation. This webinar will explain how to address SAP specific needs without losing the benefits of an Enterprise wide Identity & Access Governance implementation.

Webinar Recording
Access Governance richtig gemacht: Investitionsschutz und zielgerichtete Weiterentwicklung
Feb 29, 2012
Access Governance – dieser Begriff steht für Lösungen, mit denen sich Zugriffsrechte besser steuern und kontrollieren lassen. Die regelmäßige Re-Zertifizierung und damit Überprüfung von Zugriffsberechtigungen gehört ebenso dazu wie analytische Funktionen für den Status von Zugriffsberechtigungen und Rollenmanagement-Funktionen. Die Lösungen müssen aber auch das Management von Zugriffsberechtigungen mit einfachen Bestellfunktionen für Berechtigungen durch Endanwender und damit auch eine gute Integration mit bestehenden Provisioning-Systemen unterstützen. Nur mit einem vollständigen Kreislauf...

Webinar Recording
Best Practice Driven Identity & Access Management
Feb 21, 2012
Mobile devices and apps, cloud based services, social networks, personal life management platforms - or, in short terms, let your customer in. Managing identities behind these trends creates the need for a new look at IAM. In this webinar, Dave Kearns will discuss with industry experts on the most important qualities a new generation of effective IAM solutions has to provide.
Webinar Recording
Sicherheitsanalysen und Sicherheitsmanagement - schnell, automatisiert, intelligent
Feb 16, 2012
Auch wenn häufig viel zu leichtfertig der Begriff "Cyberwar" verwendet wird (denn Tote gibt es nur im wirklichen Krieg) - die Bedrohungslage durch Online-Kriminalität ist immens geworden. Security Information and Event Management (SIEM) stellt Ihnen wirksame Mittel dagegen zur Verfügung und hilft Ihnen dabei nicht mehr nur rein reaktiv tätig werden zu können. In diesem Webinar sprechen wir mit Ihnen über neue Herangehensweisen in diesem Bereich.
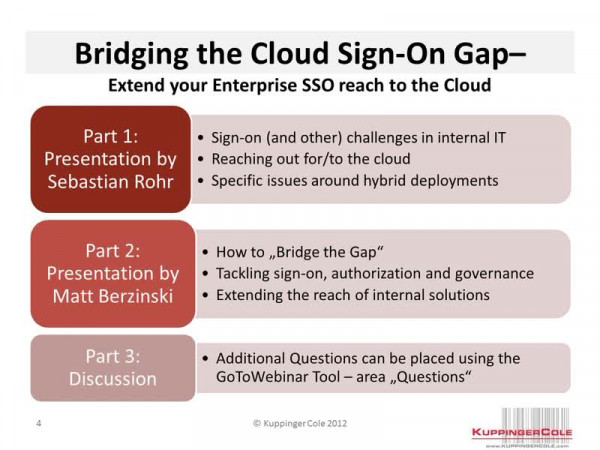
Webinar Recording
Bridging the Cloud Sign-on Gap
Feb 09, 2012
With a plethora of user names and passwords to remember, end users are already frustrated. Adding multiple cloud applications makes it more difficult for end users and increases help desk call volume. Single-Sign on can bridge the gap between the enterprise and the cloud while reducing user frustration. In this webcast KuppingerCole and Oracle will discuss how organizations can benefit from a cloud sign-on strategy. In addition, you will learn how single sign-on can jump start your cloud access management strategy and improve security.

Webinar Recording
Back to the ROOTs
Feb 02, 2012
In diesem Webinar erläutert zunächst Martin Kuppinger die aktuellen Trends im Markt für PxM (Privileged Access, Account, Identity, User Management) und die Frage, wo und wie man PxM-Lösungen mit seiner übrigen Identity und Access Management-Infrastruktur verbinden sollte. Daran anschliessend stellt Jochen Koehler von Cyber-Ark praktische Ansätze zur Verwaltung von privilegierten Identitäten vor.
Webinar Recording
Privacy by Design
Jan 27, 2012
2011 was, once again, a bad year for privacy as data breaches releasing usernames, passwords, credit card details and even medical records continued to make news right through the end of the year. Time has proven that no amount of imposed regulation can protect privacy in the face of a determined hacker. What’s needed is what’s called Privacy by Design. Join us in this webinar, where Senior Analyst Dave Kearns will discuss with Ontario´s Information and Privacy Commissioner Dr. Ann Cavoukian, who originally developed the privacy by design concept, and with McAfee Chief Frivacy Officer...
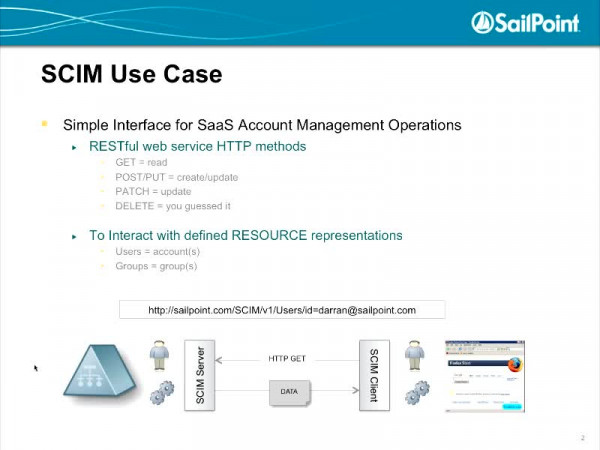
Webinar Recording
Clearing up a Cloudy Standard: Simple Cloud Identity Management
Dec 15, 2011
"Simple Cloud Identity Management (SCIM) appears to be our best chance for any sort of public provisioning standard, something we desperately need and have needed for years", says Dave Kearns. Join him, Ping Identity CTO Patrick Harding and SailPoint CTO Darran Rolls for this webinar on the newest provisioning specification which both Harding and Rolls have been involved with from the beginning.
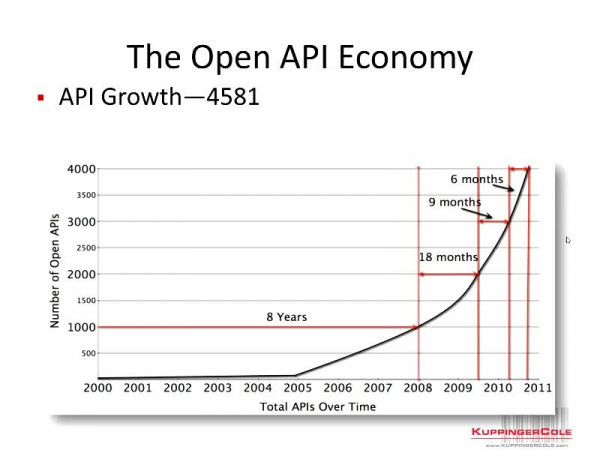
Webinar Recording
The Open API Economy - Opportunities and Risks
Dec 13, 2011
Three main (business) trends are driving technology in all areas: Social Computing, Mobile Computing and Cloud Computing. Looking behind the curtain, we see that these three trends with strong impact on everything around us are based on yet another trend, which is enabling companies to build their business models on top of services and features available through Open APIs (standardised application programming interfaces through which applications can connect to other applications). The impact of Open APIs on the way we do business is growing so fast, that we have to label it not just as a...
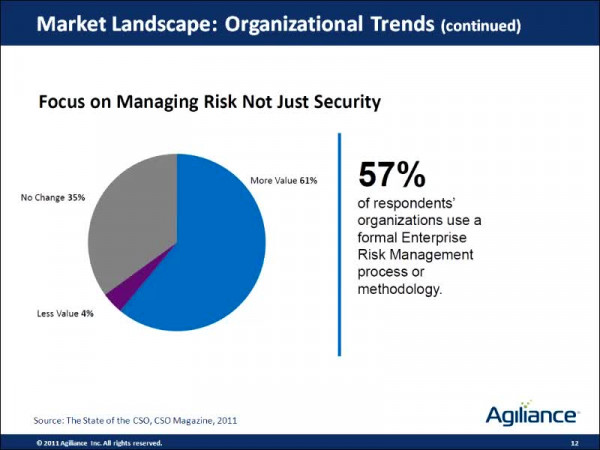
Webinar Recording
Risk. The New Compliance
Dec 01, 2011
For many years complying with government standards and industry regulations has been seen as a check box in the lengthy list of IT security tasks.
However, most recent changes in the ecosystem (e.g., increased cyber security threats) have led to a rethinking of this approach. More and more organizations realize that instead of looking at Governance, Risk, and Compliance from a centralized perspective, it is more efficient to let business operations drive these efforts as that's where the organization's risk knowledge resides. Join this webcast where we reveal how to tackle risk and its...
Webinar Recording
Access Governance: Identity Management aus dem Business für das Business
Nov 22, 2011
Verantwortung kann nicht delegiert werden. Es sind die Mitarbeiter der Fachabteilungen, die gegenüber Aufsichtsorganen, Prüfern und Justiz in der Verantwortung stehen und letztlich auch in die Haftung genommen werden. Alleine schon deshalb (aber natürlich auch, weil sie näher am Prozess sind und es deshalb besser können) muß ein modernes Identity Management fachabteilungstauglich sein. Identity & Access Governance. In diesem Webinar beschreibt zunächst Martin Kuppinger, worauf es ankommt, wenn man seine Identity Infrastruktur den Fachabteilungen als Service zur Verfügung stellt. Danach...

Webinar Recording
Why Access Governance Moves the Risk and Reward Balance in your Favour
Nov 15, 2011
In this webinar, KuppingerCole´s Principal Analyst Martin Kuppinger will describe, how to reduce business risks through transferring responsibility for defining, maintaining and auditing information security policies and access rules from IT to those business divisions which actually need these policies to do their job. Following to Martin´s presentation, Quest Software´s Phil Allen will show practical approaches and best practices implementing such an Access Governance program.

Webinar Recording
Solving the Million Record Challenge with XACML
Nov 11, 2011
This webinar with Martin Kuppinger and Gerry Gebel is part of our XACML how-to series and will highlight, how you can implement XACML policies in "big data" scenarios.

Webinar Recording
The Clock is Ticking: Rethink PCI 2.0 Compliance
Nov 03, 2011
The time when you will ultimatively have to demonstrate PCI DSS 2.0 compliance is getting closer now. We therefore would like to invite you to join us in this webinar to have a look at how you can certify fast and at reasonable cost. Don´t miss this webinar and its great speaker lineup: KuppingerCole´s Senior Analyst Dave Kearns, Tom Arnold from Payment Software Company, who is one of the leading Qualified Security Assessors in the world, and Dr. Torsten George from Agiliance.
Webinar Recording
IdM in der Praxis: Urlaubs- und Krankheitsvertretungen einfach und sicher gemacht
Oct 25, 2011
Sie sind hoffentlich gut erholt und wohl behalten zurück aus Ihrem Urlaub? Dann wünschen wir Ihnen, dass Ihre Vertretung gute Arbeit geleistet hat und Ihr Erholungseffekt nicht alsbald durch liegen gebliebene Arbeit aufgezehrt wird. Gute Arbeit kann eine Vertretung allerdings nur dann wirklich leisten, wenn sie dieselben Zugriffsrechte und Systemberechtigungen hat wie Sie. Wie man dies auf einfache und nachvollziehbare Art und Weise erreichen kann, ohne dass Sie Ihre Passworte weitergeben müssen, das erfahren Sie in diesem Webinar.

Webinar Recording
Surviving the Cyber Security Attack Wave
Oct 14, 2011
In this webinar, KuppingerCole's co-founder and Principle Analyst Martin Kuppinger will talk about the key elements of a pro-active security risk management strategy. Then, Dr. Torsten George from Security and Operational Risk Management pioneer Agiliance will describe the elements of a properly planned and implemented security risk management program that enables organizations to reduce risk by making threats and vulnerabilities visible and actionable, enabling them to prioritize and address high risk security exposures before breaches occur.

Webinar Recording
XACML Made Easy: Modeling High Level Policies in XACML
Oct 07, 2011
In this webinar, Principal Analyst Martin Kuppinger will give an overview on how the XACML standard can be used to achieve a top-down approach to governance. Following Martin's presentation, Axiomatics' Director of Technology Partnerships and former Kuppinger Cole Analyst Felix Gaehtgens will show examples that show how easy it actually is to translate high-level access control requirements from written English into XACML policies that implement tight control. Felix will then describe how to model XACML policies to integrate risk-awareness in access controls.
Webinar Recording
Thriving in Change - Using Federation and the Cloud to Minimize IT Costs
Sep 29, 2011
Overcoming the inherent security and identity management challenges is key to a successful move into the cloud. In this webinar, KuppingerCole's Senior Analyst, Sebastian Rohr, will give suggestions for successful adoption of cloud computing that overcome the inherent security and identity management challenges. Sebastian will be joined by Travis Spencer, a Sr. Technical Architect in Ping Identity’s CTO office, who will elaborate on these options, drawing on the lessons learned from the hundreds of Ping Identity customers that have overcome these difficulties.
Webinar Recording
Why Managing Privileged Users Benefits your Business
Sep 28, 2011
In this webinar, KuppingerCole's co-founder and principal analyst Martin Kuppinger will give you an overview on the dos and don'ts of privileged user management, with a special emphasis on hybrid cloud environment. Followed by Martin, Phil Allen, Quest Software's Director Identity Management EMEA, will talk about Quest Software's solution focus within the privileged user management sphere, which recently received a strong boost through the acquisition of e-DMZ Security.
Webinar Recording
Integrating Access Governance and Entitlement Management
Sep 22, 2011
Under the impact of the worldwide financial services crisis and the resulting recession in major Western markets have put pressure on governments to introduce new legislation to alleviate the danger of a reoccurrence. However, new oversight regulations always tend to add complexity. For example, the new US Dodd-Frank Act is 6 times the size of its predecessor, the 2002 Sarbanes Oxley Act. Responding to these new set of laws forces enterprises and organizations to improve the transparency and flexibility of their access governance procedures. In this webinar, we will explore the diverse...

Webinar Recording
Game On: Managing Multi-Regulatory Compliance
Sep 17, 2011
In this webinar, KuppingerCole's co-founder and Principle Analyst Martin Kuppinger will give you an overview on how to stay compliant in a multi-regulatory environment. Followed by Martin, Cognosec CEO Oliver Eckel will reveal best practices of managing compliance in today's multi-regulatory world.

Webinar Recording
How to Prepare for BYOD (Bring Your Own Device)
Jul 01, 2011
In a recent blog entry , KuppingerCole´s principal analyst Martin Kuppinger wrote, that the acronym BYOD stands for IT departments accepting that they’ve lost against their users. Now we have to see, how we can make the best out of it and minimize the risks involved with private mobile devices logging into corporate networks. In this webinar, Tim Cole will moderate a discussion between Craig Burton and Martin Kuppinger on how to prepare your enterprise for BYOD by providing a risk-based selection of secure paths to access corporate information and to protect that information.
Webinar Recording
Database Firewall - Build the First Line of Protection
May 03, 2011
Database Security is one of the key elements within any IT security strategy, given that several of the most severe incidents in IT are related to attacks against databases and that most of the critical and sensitive information in organizations is stored in databases. Database firewalls implement a first line of defense, blocking in real time any suspicious data manipulation without forcing production environment redesign. Thus, companies should consider the value that these tools can add to their security strategy.
Webinar Recording
Identity Management - in the Cloud and for the Cloud
Apr 21, 2011
How to best deploy Identity and Access Management today? There is an increasing number of opportunities, including hosted and cloud-based options. And there is an increasing number of services in the cloud which have to become integrated into the IAM ecosystem. Thus the question is: How to best deploy IAM to serve all requirements?

Webinar Recording
Business-Centric, Cloud-Aware Identity and Access Management
Apr 15, 2011
In this webinar, KuppingerCole´s Principal Analyst Martin Kuppinger will introduce you into the key elements of a future-proof and cloud-ready Identity and Access Management strategy and how to deal with hybrid cloud environments. Following Martin, Ralf Knöringer and Rudolf Wildgruber from Siemens IT Solutions and Services will present case studies and product features of Siemens DirX Identity and DirX Audit and show how to realize an Identity Governance solution that creates business value.
Webinar Recording
Reliable Protection for Information in Databases
Apr 13, 2011
How to best protect data? This is about processes, this is about technology. Whilst Database Governance focuses on the big picture, technology enables the required controls. Amongst them, encryption is a key technology – supporting critical controls to prevent by-passing the access controls mechanisms within databases and in the surrounding system environment. In this webinar, Martin Kuppinger will outline how Database Security solutions fit into the approach of Database Governance, which role encryption technologies play therein, and what it needs for a holistic approach on Database...

Webinar Recording
Access Management: Simplify Access to Web- and Cloud-based Applications without Compromising Security
Apr 01, 2011
The role of web access management has changed and nowadays serves as a central layer of protection for many different services, enabling federations and allowing versatility for users. Join us in this webinar to learn, how to transform your traditional web access management into such a central multi-purpose layer.
Webinar Recording
Overcoming Enterprise Entitlement Barriers by Externalizing Authorization
Mar 30, 2011
Entitlement Management is about keeping control of authorizations within applications by externalizing the policy management and the authorization decisions. However, a strategic approach on to Entitlement Management requires strategic offerings, supporting standards and built to scale. In this Webinar, Martin Kuppinger will talk about the status and evolution of the market for Entitlement Management, the role XACML plays, real-world architectural consideration and approaches. Followed by Martin, Subbu Devulapalli from Oracle will talk about solutions and real-world use cases.

Webinar Recording
Identity Management, Access Governance und Datenschutz: Sind Sie auf der sicheren Seite?
Mar 24, 2011
Datenschutz - ein notwendiges Übel? In zahlreichen Unternehmen ist dieses Thema auch heute in der Tat noch eine Randerscheinung, obwohl mit der gesteigerten öffentlichen Wahrnehmung und damit einher gehenden Sensibilisierung jeder bekannt werdende Verstoß zu einer fundamentalen Schädigung der Substanz Ihres Unternehmens führen kann. Dieses Webinar hilft Ihnen dabei, den Datenschutz wirksam und effizient in Ihrem Unternehmen zu verankern.
Webinar Recording
Database Governance - How to Put the Right Controls in Place to Protect Your Data
Mar 16, 2011
In this webinar, Martin Kuppinger will, for the first time ever, introduce the concept of Database Governance, the reasons why you should do that and the connection to Governance initiatives as well as Database Security technologies. He will as well talk about the areas where new conceptual and technical approaches will be required.
Roxana Bradescu of Oracle then will talk about practical approaches to make Database Governance work today – to enhance your level of protection of the valuable information assets.

Webinar Recording
Recent Trends and Best Practices in Internal Audit Management for Better Business Performance
Mar 11, 2011
Internal Audit (IA), traditionally a vehicle preserving assets and ensuring compliance, has been expanding it´s scope into a means for business process improvement and operational excellence, while at the same time it has to cope with an increasing number of high-impact risks. The challenge is, to shift course from IA´s asset preserving role to a new, value creation focused role. In this webinar, Martin Kuppinger will talk about this paradigm shift in IA, how it can be aligned more closely to your company´s strategies, and how an up-to-date Enterprise GRC strategy will help you to create...
Webinar Recording
Externalize Authorization - XACML and Beyond
Mar 04, 2011
Externalizing and centralizing authorization from applications has recently gained momentum, as related standards like XACML have matured and experiences shared by early adopters have been positive. Obviously, potential benefits from a standardized method for authorization are tremendous. KuppingerCole Research therefore has defined a clear focus in the area of centralized authorization, monitoring the market and analyzing best practices. In this webinar, Martin Kuppinger will give an update on his recent findings and he will discuss with Doron Grinstein, CEO at authorization and XACML...
Webinar Recording
Sicherheit in der Cloud: Die 5 wichtigsten Regeln für eine funktionierende Sicherheitsstrategie
Feb 23, 2011
Cloud Computing findet jenseits der traditionellen physischen Grenzen, dem sogenannten Perimeter" statt, der den Mittelpunkt traditioneller Sicherheitsansätze bildete. In dem Maße, in dem sensitive Unternehmensdaten und Anwendungen zunehmend in die Cloud abwandern, steigt die Unsicherheit darüber, wie denn Informationssicherheit in der Cloud überhaupt gewährleistet werden kann. In diesem Webinar beschreibt Martin Kuppinger die 5 wichtigsten Regeln für eine funktionierende Cloud-Sicherheitsstrategie. Klaus Hild, Senior Technology Specialist Identity and Security bei Novell, wird...

Webinar Recording
Mehr Informationssicherheit durch effizientes Berechtigungsmanagement
Feb 19, 2011
Es gibt eine ganze Reihe von Gründen, warum das Thema Berechtigungsmanagement aktuell in der Unternehmenspraxis eine große Rolle spielt. Einerseits, weil es die Basis bildet für den Umgang mit Informationsrisiken (Stichwort Wikileaks), andererseits aber natürlich auch, weil es bei vielen Unternehmen Nachholbedarf gibt, um einen besseren Überblick über Berechtigungen zu bekommen und aus einem bisher eher mühseligen Geschäft mit Hilfe zeitgemäßer Werkzeuge Einsparpotenziale zu erschließen. Mit diesem Webinar bieten wir Ihnen die Möglichkeit, sich zu aktuellen Trends und Entwicklungen im...

Webinar Recording
The Business Value of Log Management Best Practices
Jan 26, 2011
Although log management recently has been gaining more attention as a key element of any information security strategy, many even large organizations have not yet developed and implemented log management best practices. In this webinar, Kuppinger Cole´s Pricipal Analyst Martin Kuppinger will discuss with you the business value of best practices for log management. Followed by Martin, Pascal Oetiker from Novell will describe his view on how to develop and implement log management best practices.








































































































































































































































































































































































































































































































































































































