1 Introduction
SAP is the leading vendor of Line of Business (LoB) applications. Their applications covering Enterprise Resource Planning (ERP) and many other use cases form the backbone of business operations in many organizations, ranging from medium-sized business to the world’s largest organizations. Aside from SAP, there are many other vendors. In addition, the SAP portfolio is becoming more diverse regarding architectures, implementation, and deployment models.
Taking such a central role in organizations, SAP systems of different types and other LoB systems operated in different deployment models, need special care from security teams that understand the specifics of these environments, and are equipped with specialized tools. SAP/LoB Security Solutions are essential for improving the security posture in the business application environments and mitigating risks to these core LoB applications.
There are various challenges organizations are facing for improving the security posture of their SAP and LoB application environments:
- System hardening: System hardening in SAP/LoB landscapes requires specialized solutions covering all elements of complex environments, from operating systems and databases to the business applications.
- Patch deployment: Deliver patches and hotfixes in a controlled, efficient manner without disrupting operations.
- Code vulnerability analysis: The specific programming languages used such as ABAP (Advanced Business Application Programming) require specialized tools for enforcing code security.
- Log analysis & threat detection: Complex, large-volume log information needs to be understood for extracting information about concrete threats.
- Heterogeneous environment support: The LoB landscape is becoming increasingly diverse, requiring solutions that support a range of different types of applications and deployment models.
- Siloed organizations: Many of these applications are still managed by dedicated teams residing in a distinct organizational unit. Integration with the broader cybersecurity and system administration teams is essential.
- Data Security: Dynamically masking and restricting access to sensitive production data based on user attributes and other customizable policies. Additionally, scrambling data to ensure security of replicated test data in non-production environments, when data is in transit, or when direct access to the database is possible. Dynamic data security controls are essential to ensure comprehensive protection of production and non-production data, as well as enforcing data loss prevention (DLP) mechanisms.
- Dynamic Access Control: Expanding access controls beyond a traditional, inflexible role-based access control (RBAC) security model with dynamic policies and attribute-based access controls (ABAC). A policy-based approach is important for managing access securely and effectively across an infinitely growing number of users and applications as organizations scale and migrate to S/4HANA.
Holistic SAP/LoB Security solutions support customer organizations in mitigating cybersecurity risks to their business application environments, both with specialized capabilities and in integration to other security systems such as centrally deployed and managed SIEM solutions. Traditionally, such solutions only cover specific capabilities that help in better protecting one security aspect such as code security. Modern cybersecurity best practices require a holistic and integrated security platform approach to improve the overall security of these environments. The various solutions on the market differ in both breadth and depth of capabilities as well as in their ability for supporting the wide range of existing SAP and other LoB applications, services, and environments.
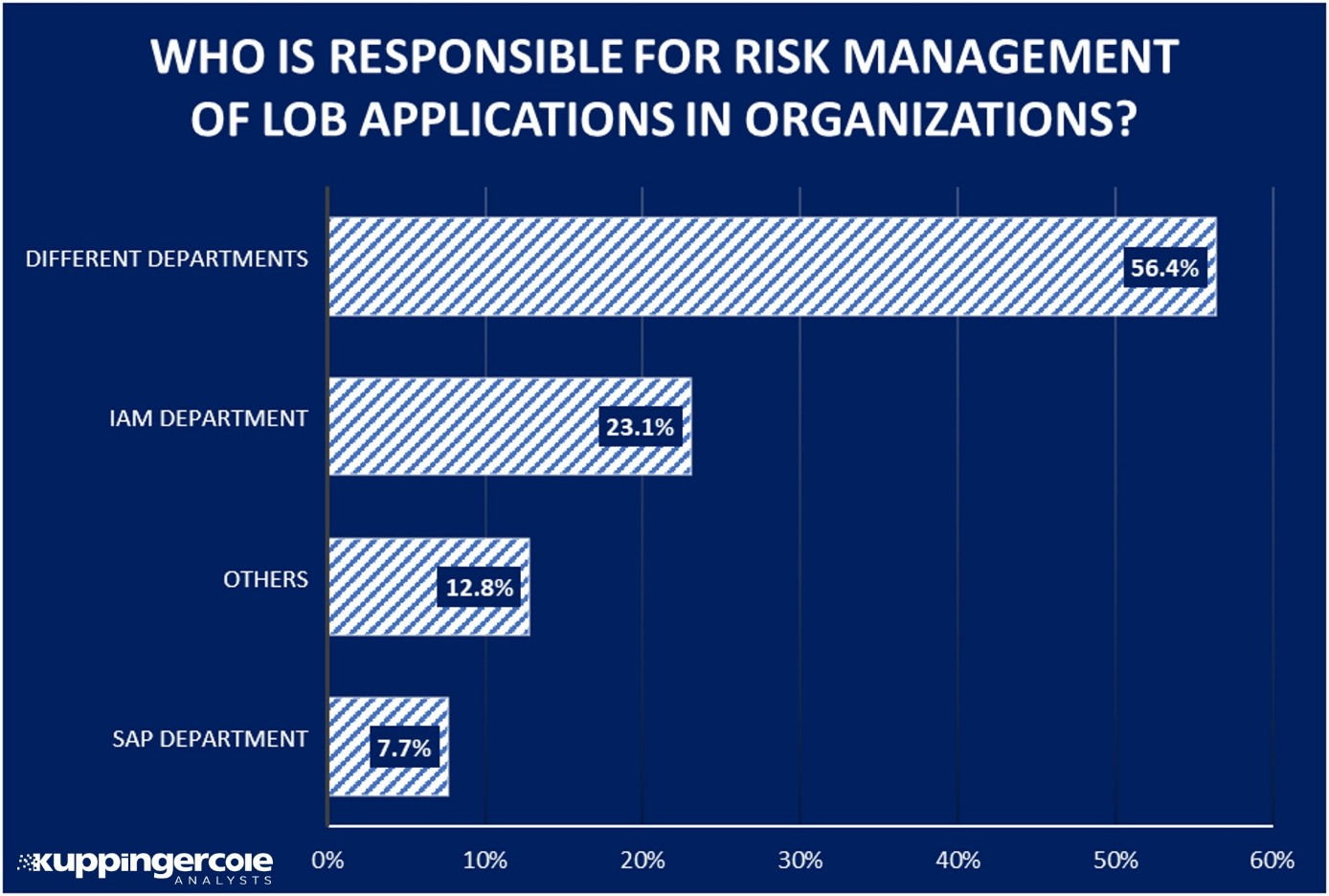
Figure 1: Risk Management and Security are still not handled consistently in organizations.
Pathlock is one of the vendors in this market, delivering a range of capabilities with their Cybersecurity Applications Controls offering.
















































