1 Highlights
Unmanaged non-human identities number in the millions and present a serious risk to IT security
The number of cyber-attacks involving non-human attacks is increasing
Workload identities, a type of non-human identities (or identities for apps and services), are of particular interest to attackers as they can offer a short cut to network penetration
Multi-cloud access and agile working environments such as DevOps have increased the usage of non-human identities
Organizations need to reevaluate legacy IAM strategies designed for non-human Identities
Workload identities should not be set and forget but continually assessed and managed by software tools and policies
Microsoft is launching a new generation of identity and cloud management tools including Microsoft Entra Workload Identities and Permissions Management
2 Introduction
Attacks on organizations that involve non-human identities are proliferating. We are seeing the growth of ransomware attacks that use non-human identities to hijack systems and exfiltrate data. Cyber attackers can use stolen or leaked credentials to conduct credential stuffing attacks on non-human identities, such as bots or applications. One of the most high-profile attacks involving non-human identities was SolarWinds in 2020, where malicious code was placed into applications used for automatic software updates and this spread out to customers. More recently in December 2022, hackers gained access to high level LastPass developer accounts and stole source code that had been left unprotected. The hackers targeted the home PC of a senior developer, inserted a keylogger to steal the primary password and used this to get a foothold into cloud resources. They then stole non-human identity passwords used for automated services residing in a LastPass AWS account.
Unlike human identity access management, non-human identity credentials are often of the “set and forget” type because the workload attached is expected to perform the same routine over and over. Non-human identities are often not so well covered by traditional Privileged Access Management (PAM) software designed to manage the quirks of human identities first and foremost.
Non-human identities assigned to software (see Figure 1) are used to authenticate and authorize access to cloud resources such as databases, storage, and other services. In the Microsoft Azure and Microsoft Entra ecosystems, these are called workload identities and can also be targeted through misconfigurations, such as weak credentials or incorrect permissions. Workload identities may have a human administrator assigned to them but it can be hard to keep track of all workload identifies assigned to services, scripts, containers etc. Adversaries have used workload identities to establish persistence in cloud environments after gaining initial access through a compromised administrator.
Concurrently, multi-cloud IT architectures have become essential to organizations seeking the speed and dynamism to run applications and tools needed for fast changing markets and operating conditions. DevOps and other agile teams within organizations have come to rely on dynamic clouds to complete workloads, in response to demands from their internal customers.
These networks are much more open to employees, third party users, suppliers, and customers; what was once considered “privileged” is becoming the norm as collaboration and data sharing become ubiquitous between applications. The emergence of non-human identities gaining access to cloud-based resources is an important part of this environment.
This new architecture incorporates multiple instances of cloud services including Infrastructure as a Service (IaaS), Platform as a Service (PaaS) and Software as a Service (SaaS), hybrid combinations of cloud and on-premises installations.
The speed at which these environments operate has put severe pressure on the capabilities of traditional access management platforms such as Identity Governance Administration (IGA), Identity Access Management (IAM) and Privileged Access Management (PAM). Hence the need for newer Cloud Infrastructure Entitlement Management (CIEM) platforms and easier to use management tools for non-human identities attached to workloads operating across the cloud.
3 Types of Non-human Identities
Non-human identities are proliferating and acquiring new significance for identity and security managers in modern computing environments.
One of the significant changes that have been taking place is the rapid growth in the volume and different types of non-human identities. Failure to ensure comprehensive identity management capabilities for these identities as well as human identities is likely to expose organizations to business, security, and compliance risks.
It is therefore important for organizations to recognize where and how non-human identities are used in their IT environments and to ensure they have the necessary systems and processes in place to manage them properly. They should also ensure they are controlled with the required visibility, security, traceability, authentication, and authorization processes. Non-human identities are emerging in four main areas: Device, IT Admin, Software, and Automation (see Figure 1 below).

Figure 1: Different classes of non-human identities and the things assigned to them. (Source: KuppingerCole).
Device
A group of non-human identities interacting with enterprise IT resources that range from the personal to the industrial and other internet connected devices collectively known as the Internet of Things (IoT).
IT Admin
Within IT Admin, service accounts and shared accounts are increasingly used by non-human identities to perform repetitive admin and maintenance functions.
Workloads
These are applications, scripts or code, services and containers that perform automated tasks and often linked to DevOps and Automated Admin functions (see above) but not exclusively. The emergence of Infrastructure as Code (IaC) has accelerated the growth in software identities. In this domain, non-human identities often interact with other non-human identities and applications.
Automation
Machine Learning technologies in analytics and behavior analysis have introduced a whole new set of resources to the enterprise IT environment with identities that also need to be managed.
The number of non-human identities will continue to multiply and will interact with each other more often, and across more domains. The sheer number of non-human identities and the labyrinthine environments in which they operate is the key challenge to management. But it is not the only challenge. The spread of cloud and digital infrastructures has in many cases not been regulated or planned by management - so called decentralized purchasing. Often it is the result of semi- organic growth with departments defining and sourcing components on an autonomous basis. This includes the adoption of IoT, automation tools and code development, and such autonomy in cloud and software procurement is likely to be permanent. This has also increased the number of non-human identities significantly.
Vendors and buyers of IAM tools are realizing that the existence of standing privileges for human identities is a risk and capabilities have been developed to strip human identities of such access (known as Least Privilege). However, it is likely that many millions of forgotten or unknown non-human identities, especially software identities, continue to have unmonitored standing access to critical parts of the enterprise as default. There is a growing realization among all enterprise stakeholders that this is untenable.
4 How to Manage and Secure Non-human Identities
Non-human identities, including workload identities, have a role in modern IT infrastructures to ensure the smooth running of key departments and the creation of new applications and infrastructure. How can CISOs and IT leaders start to control their usage and protect the wider organization?
Before any software or technology platform can be deployed, IT leaders must consider the type of capabilities, policies and functions needed to bring non-human identities under control. They should also consider some administrative and operational changes to assist in managing non-human identities. In print these steps seem logical but, will require hard work, time and input from multiple departments including IT security, DevOps, HR, Identity Management leaders and other parties. Some processes can be implemented with existing software (like PAM for example) and others by improving business policies. Others will require new software designed to manage cloud activity and also software to control all types of non-human identities.
Some basic points to consider:
- Consider non-human identities as more risky than human identities
- Remove embedded passwords from code repositories, applications, containers etc.
- Implement a policy of least privilege access for all identities not just human
- Remove or modify workload identities with long credential expiration times
- Remove all unnecessary permissions assigned to workloads
- Remove all unnecessary permissions for admins or end users that manage non-human identities attached to workload identities
- Implement lifecycle management for permissions, workloads, and identities
- Ensure there is a process or software tool to constantly check and monitor access and entitlement permissions across the IT estate
Some more granular points to consider:
- Identify which existing technologies (e.g., PAM) can be used and whether/when these may need to be modified/improved/replaced
- Understand the types of human and non-human identities needed for ongoing digital transformation
- Define central policies across tools to enable consistent Identity Access Governance for all recognized identities
For most businesses these steps will mean making changes to their IT architecture to become more agile and flexible. It may involve the purchase of extra tools such as software platfroms dediacted to managing workload and other non-human identities in the cloud partculalry, but also on-premises.
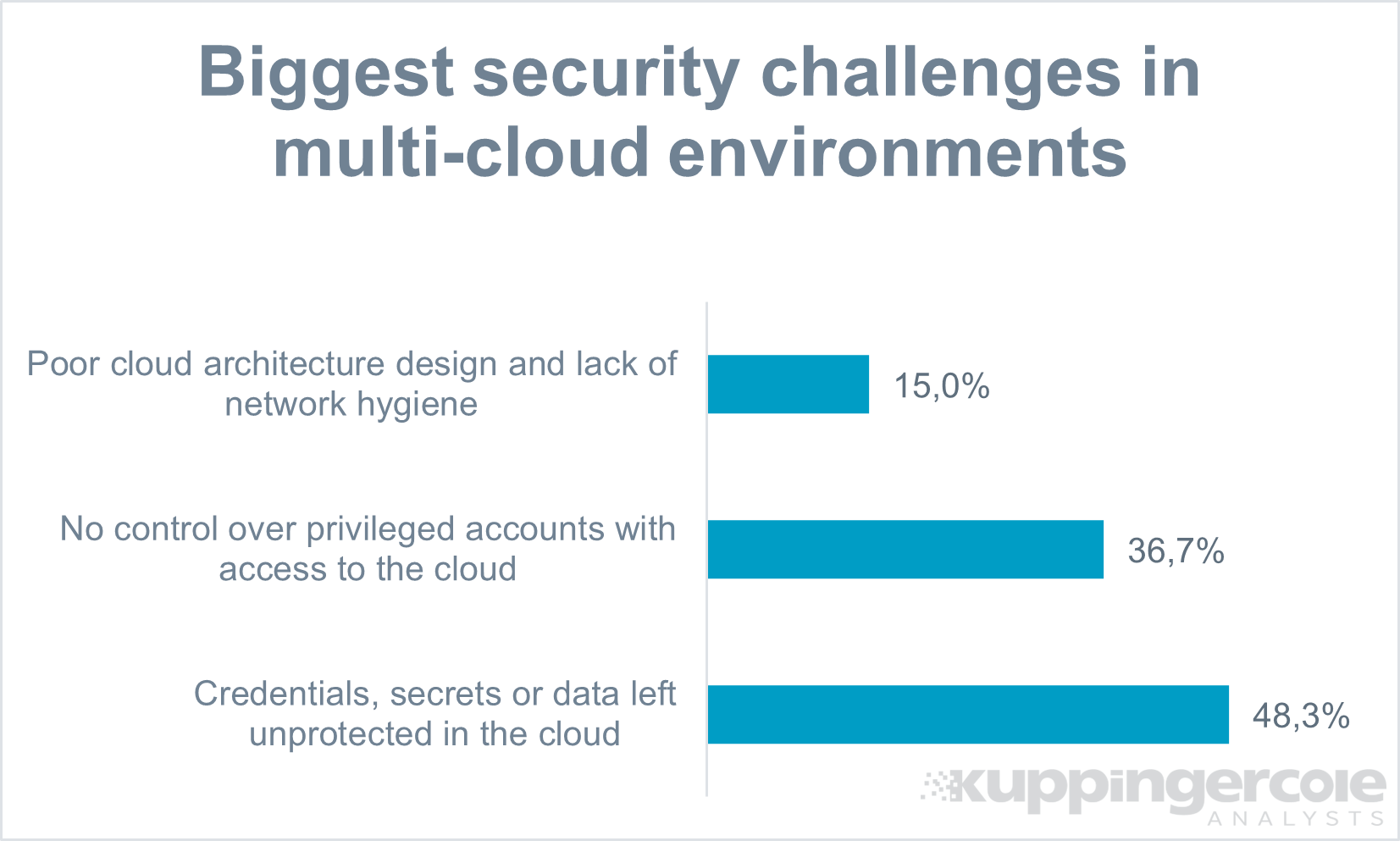
Figure 2: Polling demonstrates the concern buyers have about the risks in multi-cloud deployments. (Source: KuppingerCole)
Cloud Identity and Entitlement Management software helps govern cloud entities by offering visibility into unnecessary permissions, detecting potential threats, and enforcing consistent access regulations across all cloud platforms.
Going forward, organizations should plan to support all kinds of identities and ensure they have the tools to understand the level of risk in each identity type so they can make informed decisions on how those identities can be used for specific transactions or interactions. This may involve risk-based scoring through Identity Governnace platforms and also adaptive authentication and authorization techniques via Identity Providers.
5 Microsoft Entra Workload Identities and Permissions Management
Microsoft Entra is intended to make identity management more dynamic and compatible with multi-cloud environments.
Microsoft Entra is growing its portfolio of identity and access management products. In this section we look at two: Microsoft Entra Workload Identities and Microsoft Entra Permissions Management. The two are compatible and can be made to work together through the Microsoft Entra Admin Center, but also available to procure as separate products.
5.1 Microsoft Entra Workload Identities
Microsoft Entra Workload Identities is an IAM solution specifically focused on managing workload identities as defined earlier in the text. It contains tools to secure access, detect risk and manage the lifecycle of workload identities assigned to applications and services in Azure.
Key to the software usability is its deployment of conditional access policies to control access of workload identities. Admins can add new access management policies then assign these to workload identities,
Admins can control policies by scripting the policy parameters under which a workload identity may access a resource – this includes approved location, or a specific risk setting decided by the admin. Creating and setting policies is accomplished through the Microsoft Entra Admin Centre. All changes and settings are easily configured via drop down menus and click boxes.
Risky workload identity activity can be discovered in the Microsoft Entra Admin Centre by clicking on “Risky Workload Identities” and then allowing the tool to identify those tracked as risky by for example, unusual sign in behaviour or other anomalous behaviour displayed by the Microsoft Entra Workload Identity. Full details of the identity’s history are made available to the administrators
More granular information on workload identities can also be found and the Entra Admin Center will come up with a list of recommended actions at any one time. These include renewing expiring workload credentials and removing unused or inactive applications registered in Azure AD. Microsoft Entra Workload Identities allows admins to view new and unused workload identities and review whether they still need access to certain resources.
Microsoft Entra Workload Identities uses cloud-based AI to scan for workloads identities that have been compromised and block their access by setting conditional access policies, and help implement Zero Trust principles into workload identity management.
5.2 Microsoft Entra Permissions Management
Microsoft Entra Permissions Management is a Cloud Infrastructure Entitlement Management (CIEM) platform that complements the activity of Microsoft Entra Workload Identities. It generates on-demand access to high-risk permissions and provide always on monitoring to right size identity permissions and prevent excess standing privileges for identities.
The product offers visibility and control over permissions for any identity and any resource within Microsoft Azure, Amazon Web Services (AWS) and Google Cloud Platform (GCP). The number of IaaS platforms supported is highly likely to be expanded as Microsoft develops the platform. It uses a modern dashboard interface to provide admins or IT managers with an easy-to-understand window into the activity of all identities, both human and workloads, across multicloud infrastructures.
A primary capability of an effective CIEM platform is full discovery and visibility into identities and their permissions across multi-cloud. This informs a key part of the platform; the Permissions Creep Index, a qualitative measure of risk by comparing an identities’ permissions granted vs. permissions used and their access to high-risk resources.
To deploy Microsoft Entra Permissions Management, customers are required to have an Azure Active Directory (Azure AD) account to sign in to. Once established, customers with a Global Admin role can execute Permissions Management on their Azure AD tenant, and then onboard AWS, GCP or Azure cloud accounts as needed.
Once discovery has been completed Permissions Management can automatically delete permissions that have been unused for more than 90 days, granting additional permissions on-demand for just-in-time access for cloud resources. All such actions can be triggered by a request for access from an identity, and all activities are recorded for analytics purposes. The user experience is the same for any identity type, identity source and cloud. A human identity can also request access on behalf of a workload identity which is a neat and forward-thinking capability.
Permissions Management offers out-of-the-box forensic reports which are also fully customizable to meet the needs of the reporting channels. Reports can be scheduled or produced on-demand in response to an incident or investigation and distributed by email. Future development will include refinement of the UX and dashboard to mirror that of other Microsoft platforms. More importantly, Microsoft says it will support more IaaS services across the board in the future.
6 Recommendations
Identity and Access Management has never been more important, but it has also never been more challenging as the IT world becomes increasingly services-oriented, mobile, and cloud-based. These changes include the proliferation of non-human identities, which is something no organization can afford to overlook as they gear up their IAM capabilities for the short, medium, and long term. It is essential that all organizations:
- Identify where and how non-human entities interact with their IT systems
- Ensure that all these entities have unique identities that can be managed through an identity management system
- Identify all non-human identities with privileged access
- Monitor audit and sign-in logs for anomalies, and archive logs in case of an incident
In the medium to long term, organizations need to adapt to a new way of doing business in an increasingly digital and services-based world. KuppingerCole Analysts believe that IAM must therefore evolve to become a service akin to an Identity utility that is easy to consume and flexible in supporting emerging business requirements across heterogenous and increasingly hybrid modern enterprise IT environments.
These steps will enable the organization to start building digital services based on a future-proof platforms to provide a centralized set of services to enable a consistent approach to access management, identity governance and administration (IGA), consent and privacy.
7 Related Research
https://www.kuppingercole.com/research/lc80355/privileged-access-management-for-devops
https://www.kuppingercole.com/research/an71125/integrating-security-into-an-agile-devops-paradigm
https://www.kuppingercole.com/research/lc80474/zero-trust-network-access
https://www.kuppingercole.com/research/lc80767/ciem-dynamic-resource-entitlement-access-management-dream-platforms
https://www.kuppingercole.com/research/lc80757/access-management-2022
https://www.kuppingercole.com/research/lc80207/container-security
Privileged Access Management 2023 | KuppingerCole
8 Copyright
© 2024 KuppingerCole Analysts AG all rights reserved. Reproduction and distribution of this publication in any form is forbidden unless prior written permission. All conclusions, recommendations and predictions in this document represent KuppingerCole's initial view. Through gathering more information and performing deep analysis, positions presented in this document will be subject to refinements or even major changes. KuppingerCole disclaims all warranties as to the completeness, accuracy and/or adequacy of this information. Even if KuppingerCole research documents may discuss legal issues related to information security and technology, KuppingerCole does not provide any legal services or advice and its publications shall not be used as such. KuppingerCole shall have no liability for errors or inadequacies in the information contained in this document. Any opinion expressed may be subject to change without notice. All product and company names are trademarks ™ or registered trademarks ® of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
KuppingerCole Analysts support IT professionals with outstanding expertise in defining IT strategies and in relevant decision-making processes. As a leading analyst company, KuppingerCole provides first-hand vendor-neutral information. Our services allow you to feel comfortable and secure in taking decisions essential to your business.
KuppingerCole Analysts AG, founded in 2004, is a global, independent analyst organization headquartered in Europe. We specialize in providing vendor-neutral advice, expertise, thought leadership, and practical relevance in Cybersecurity, Digital Identity & IAM (Identity and Access Management), Cloud Risk and Security, and Artificial Intelligence, as well as for all technologies fostering Digital Transformation. We support companies, corporate users, integrators and software manufacturers in meeting both tactical and strategic challenges and making better decisions for the success of their business. Maintaining a balance between immediate implementation and long-term viability is at the heart of our philosophy.
For further information, please contact clients@kuppingercole.com.