1 Introduction / Executive Summary
In less than a decade, containers have undergone an impressive evolution: from a lightweight virtualization technology to the de-facto standard for software distribution to a powerful underlying platform for complex and distributed applications. For many organizations, container orchestration platforms like Kubernetes serve as a universal foundation for deployment, scaling, and management of applications that works consistently across on-premises and multi-cloud environments.
The growing demand for new software architectures has given rise to microservices that allow businesses to develop and deploy their applications in a much more flexible, scalable, and convenient way - across multiple programming languages, frameworks, and platforms. Microservices, containers, and Kubernetes have quickly become synonymous with modern DevOps methodologies, continuous delivery, and deployment automation and are generally praised as a breakthrough in developing and managing cloud-native applications and services.
Unfortunately, this massive change in infrastructure and a major increase in overall complexity (although much of it is hidden from developers thanks to multiple layers of abstraction and convenient tools) has introduced numerous new risks and security challenges as well as new skills needed to mitigate them efficiently.
Initial attempts to repurpose existing security tools for protecting containerized and microservice-based applications have quickly proven to be inadequate due to their inability to adapt to the scale and ephemeral nature of containers. Static security products that focus on identifying vulnerabilities and malware in container images, while serving a useful purpose, do not address the full range of potential risks.
The need to secure containerized applications at every layer of the underlying infrastructure (from bare-metal hardware to the network to the control plane of the orchestration platform itself) and at every stage of the development lifecycle (from coding and testing to deployment and operations) essentially means that container security has to cover the whole spectrum of cybersecurity and then some.
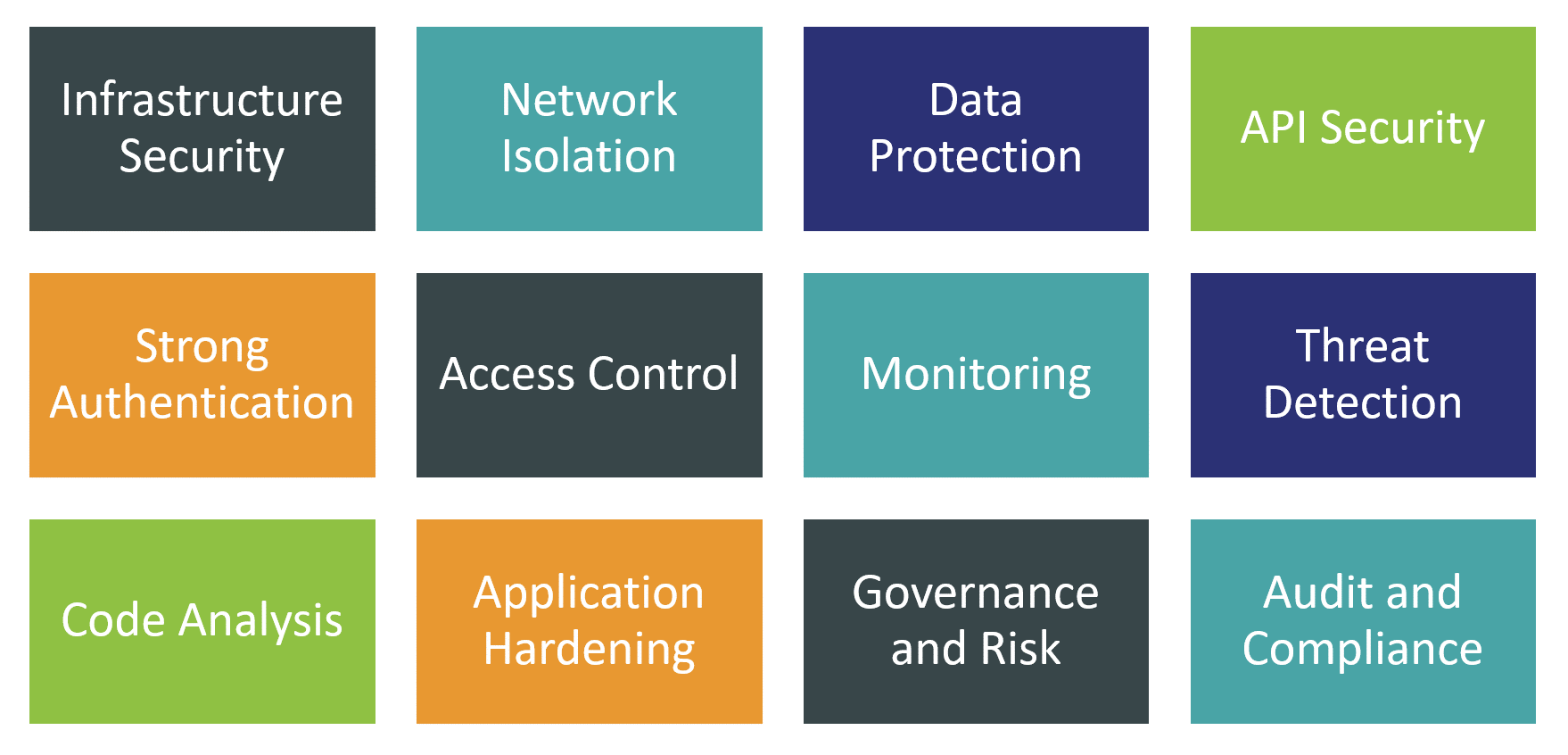
This is why for this Leadership Compass, we have decided to focus primarily on the universal container and Kubernetes security platforms, which aim to analyze, monitor, assess, and mitigate risks along the full lifecycle of application containers - starting with developing, testing, and hardening container images to runtime monitoring and threat detection to responding to identified security incidents. At the same time, we expect container security solutions to expand their coverage to multiple layers of infrastructure including hardware, host OS, virtualization, and networking layers.
1.1 Highlights
- In less than a decade, containers have quickly evolved from a simple idea of packaging software for distribution into a universal platform for automating application deployment, scaling, and management.
- Docker containers and Kubernetes orchestration platform have emerged as the most popular standard for developing, packaging, and running modern cloud-native, loosely coupled, highly scalable application architectures across multi-cloud and hybrid environments.
- Universal adoption of containerized architectures has fundamentally changed the ways of collaboration between developers, operations, and security teams, enabling new cloud-native and hybrid DevOps use cases, but bringing new risks and threat vectors as well.
- Repurposing existing cybersecurity tools for the sheer scale and ephemeral nature of modern container platforms is a challenging task for vendors, and these tools are not suited to address the container-specific risks such as securing Kubernetes clusters and registries.
- At various stages of the container lifecycle, different stakeholders are responsible for securing specific parts of container infrastructures, thus creating the potential for additional friction and miscommunication between teams. Removing this friction is one of the primary goals of modern container security solutions.
- The market for specialized container security solutions is growing rapidly with large public cloud providers, large veteran security vendors, and innovative startups offering competing solutions targeted towards customers of different sizes and from various industries. As with many other cybersecurity markets, this segment is undergoing active consolidation, with large vendors acquiring specialized solution providers and integrating their tech into full-range security platforms.
- Both small and fully cloud-native software development teams and large organizations with massive on-prem or hybrid infrastructures can find the solutions most appropriate for their needs: from fully managed natively integrated security controls in container orchestration services to universal, flexible, and open enterprise-grade platforms.
- The overall leaders in the Container Security market are (in alphabetical order): Aqua Security, Lacework, Palo Alto Networks, Red Hat, SUSE NeuVector, Sysdig, and VMware.
















































