1 Introduction / Executive Summary
As businesses embrace Digital Transformation and become increasingly cloud-native, mobile, and interconnected, the corporate network perimeter is gradually disappearing, exposing users to malware, ransomware, and other cyber threats. Traditional perimeter security tools no longer provide adequate protection from these threats. But even more so, traditional remote access solutions like virtual private networks (VPN) can no longer ensure the scalability and performance needed for the increasingly mobile and remote workforce, especially during pandemic times.
VPN is a typical example of a technology that was never designed for the purposes it is used nowadays. Besides creating potential bottlenecks by forcing companies to backhaul remote users’ traffic to a central location and thus negatively affecting performance and productivity, VPN appliances grant those users full, uncontrolled access to entire LANs. This dramatically expands the attack surface of corporate networks, provides easy lateral movement for potential attackers, and enables uncontrolled access to internal resources with implicit trust.
Unsurprisingly, Zero Trust is rapidly gaining popularity as a modern alternative to traditional perimeter-based security. An infrastructure designed around this model treats every user, application, or data source as untrusted and enforces strict security, access control, and comprehensive auditing to ensure visibility and accountability of all user activities.
Back in 2009, John Kindervag, then with the analyst firm Forrester, came up with the idea that networks should be designed without implicit trust, enforcing strict identity verification and least-privilege access policies for every user, device, or application, regardless of whether they are located in the former local area network or somewhere on the Internet. His ideas on eliminating the very concept of “trusted systems” from corporate networks helped popularize the catchy term “Zero Trust”, which had been first introduced over 15 years before.
In the same year, Google introduced BeyondCorp, a security framework created as a result of a sophisticated cyberattack on their internal infrastructure and aimed at preventing similar breaches in the future. BeyondCorp shifted access controls from the perimeter to individual devices and users, thus dramatically reducing the potential attack surface for future hackers and making it much more difficult for them to perform lateral movements, compromising one system after another.
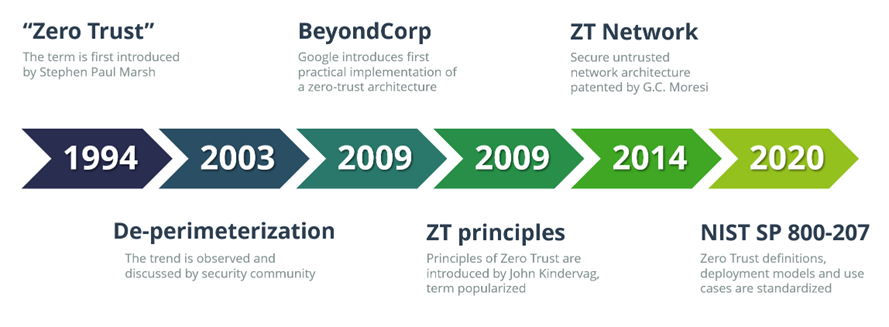
This has essentially started the Zero Trust “gold rush”, with numerous organizations eagerly looking for a possibility to buy into the new trend and with quite a few vendors quickly repackaging their existing products with new “Now with Zero Trust” labels.
One of the fundamental misconceptions the industry experts are still struggling to explain to the public is that Zero Trust is not an off-the-shelf product, but a journey that begins with a long-term business strategy and focuses on a step-by-step implementation, using existing or readily available tools and technologies, while maintaining the continuity of business processes and avoiding adding even more complexity to the existing architecture
However, even if the concept itself turned out to be quite difficult to get hold of, it has created entirely new markets for innovative security, compliance, and identity solutions. Without Zero Trust, we would not have cloud access security brokers (CASB), no Secure Access Service Edge (SASE) platforms, and, of course, no software-defined networking and micro-segmentation technologies that provide the backbone for the whole Zero Trust Network Access market.
As a concept, Zero Trust Network Access is based on the assumption that any network is always hostile, and thus, any IT system, application, or user is constantly exposed to potential external and internal threats. There is no place for a “trusted network” in a Zero Trust architecture, which is radically different from the traditional approach based on the notion of a security perimeter that separates a trusted local network from the rest of the world outside.
In various incarnations, ZTNA has existed for years, and for many early adopters of Zero Trust tenets, it has become the first building block in their long-term ZT strategies. However, the notorious COVID-19 pandemic, which forced the majority of the corporate workforce around the globe to work from home for two years, has provided a huge boost to the worldwide adoption of these solutions as a modern, more flexible and scalable alternative to aging VPN infrastructures.
In this Leadership Compass, we provide an overview of the existing solutions implementing this approach. They might be based on different underlying technologies and focus on different aspects of the Zero Trust methodology, but fundamentally, all of them solve the same problem: enabling secure yet convenient access to business applications and other resources for users regardless of their location, whether in an office, at home or anywhere else.
1.1 Highlights
- In recent years, Zero Trust architectures have gained enormous popularity as a more secure, yet flexible and future-proof alternative to traditional perimeter-based security. By eliminating the very notion of a trusted system, ZT architectures enforce strict identity verification and least-privilege access policies for every user, device, or application, regardless of where they are located.
- Zero Trust Network Access solutions apply this concept to network-based access to existing applications and other systems. By creating a logical identity- and context-based overlay over existing (and presumed hostile) networks and preventing discovery and access of applications for unauthorized users, ZTNA solutions enforce strict, fine-grained policies, thus eliminating the possibility of implicit trust and unchecked access to sensitive resources.
- ZTNA is the key technology that enables modern Zero Trust architectures, together with comprehensive identity management, strong multi-factor authentication, and real-time behavior analytics. Besides dramatically reducing the attack surface and preventing lateral movement for hackers (and thus significantly improving security posture), it has the potential to greatly simplify both the users’ and administrators’ experiences.
- The market for ZTNA solutions is currently experiencing explosive growth. Both large established vendors and small but innovative startups are offering a multitude of solutions that promise to address various usage scenarios: simplified cloud migration, seamless hybrid and multi-cloud architectures, or a modern replacement for VPN.
- The concept of Secure Access Service Edge (SASE) converges network and security solutions into a unified and tightly integrated platform that is entirely delivered from the cloud, dramatically reducing the complexity of corporate network infrastructures, and offering consistent productivity and protection at a global scale.
- The Overall Leaders in Zero Trust Network Access are (in alphabetical order): Absolute Software, Broadcom, Cato Networks, Cisco, Cloudflare, Google, Jamf, Lookout, NetFoundry, Palo Alto Networks, and Perimeter 81.
















































