Insights
Research
Advisory
Events
Videos
KC Open Select
Company
KuppingerCole's Advisory stands out due to our regular communication with vendors and key clients, providing us with in-depth insight into the issues and knowledge required to address real-world challenges.

Compare solution offerings and follow predefined best practices or adapt them to the individual requirements of your company.

Meet our team of analysts and advisors who are highly skilled and experienced professionals dedicated to helping you make informed decisions and achieve your goals.

Meet our business team committed to helping you achieve success. We understand that running a business can be challenging, but with the right team in your corner, anything is possible.
|
Delinea is a leading provider of privileged access management (PAM) solutions that make security seamless for the modern, hybrid enterprise. Our solutions empower organizations to secure critical data, devices, code, and cloud infrastructure to help reduce risk, ensure compliance, and simplify security. Delinea removes complexity and defines the boundaries of access for thousands of customers worldwide, including over half of the Fortune 100. Our solutions put privileged access at the center of cybersecurity by defining the boundaries of access. Our customers range from small businesses to the world's largest financial institutions, intelligence agencies, and critical infrastructure companies. |

Ransomware Attacks have become the biggest single cyber risk for enterprises of any size and industry. Research indicates a steep rise not only in the number of attacks, but as well in the average damage per incident. It is therefore essential that organizations are prepared for these attacks.

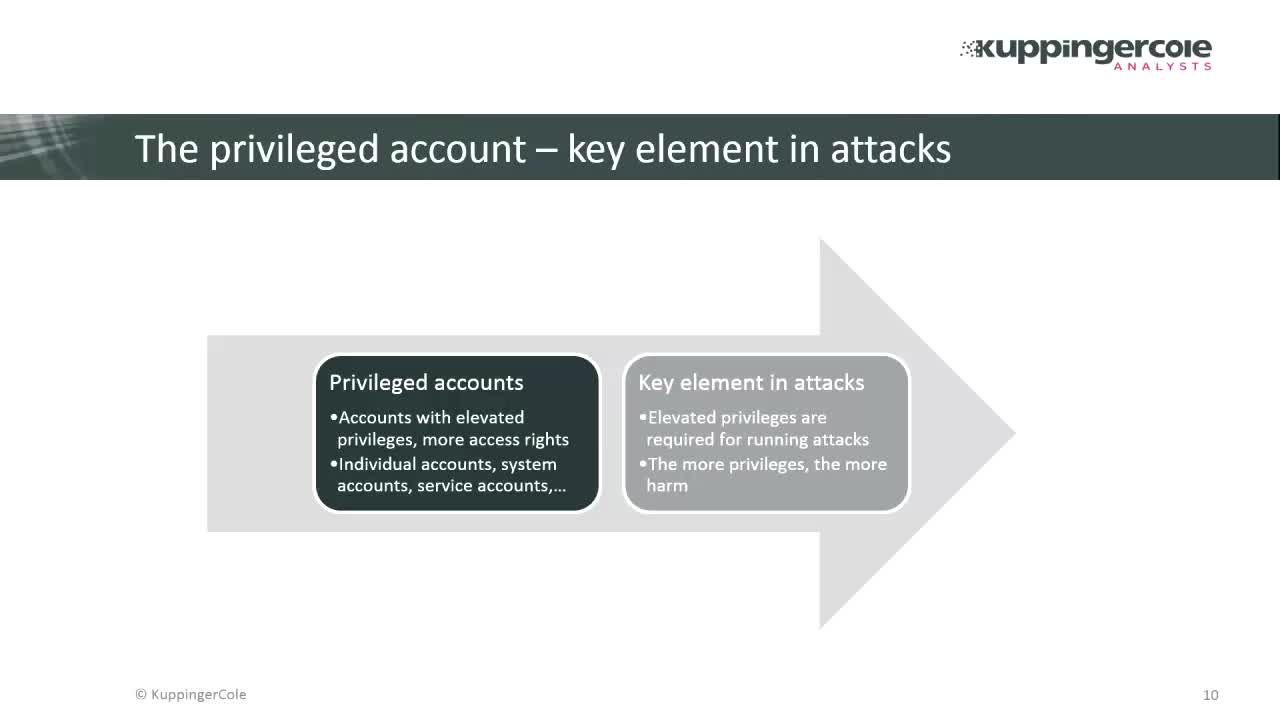
Privileged Access Management (PAM) continues to be a top priority for many organisations throughout the world. It is one of the most important solutions to help organisations reduce the risk from cyberattacks that target their privileged accounts and help move passwords into the background reducing cyber fatigue. A compromised privileged account enables an attacker to move around the network undetected, download malicious payloads, stage compromised servers and cause significant financial losses to their victims.
Almost all users are now privileged users. With 80% of breaches involving the compromise of IT and business user credentials you must create a plan to reduce the risks posed by “overprivileged access” users, applications, and services. When users are over-privileged it only takes attackers a few easy steps to become a full domain administrator. We must make it more difficult that force attackers to take more risks increasing the chance of detecting them early before serious damage is done.
One question for all organizations is how to get started. Where is the best place to begin for managing and protecting privileged access? It’s vital that you have have a solid strategy. Whether you’re starting a new PAM project or strengthening an existing Privileged Access Solution, Joseph Carson, Thycotic’s Chief Security Scientist and Advisory CISO will guide you step-by-step through planning your journey to privileged access security and introduce you to the PAM checklist that will help guide you to both maturity and success.

What makes a PAM strategy different from enterprise password management or Identity Access Management? What are the first actions you should take to protect your privileged accounts in the shortest amount of time? And, how has the definition of “PAM Basics” changed as the industry and cyber risks have evolved? This webinar is a must for teams launching PAM initiatives to ensure they start on the right foot. As you progress on your PAM journey, there’s always something new to learn. If you’ve already begun your PAM rollout, this event is a great chance to confirm you’re setting the appropriate milestones and see how others demonstrate success.

As the adoption of cloud applications and services accelerates, organizations across the globe must understand and manage the challenges posed by privileged access from remote employees, third parties, and contractors. With 77% of cloud breaches due to compromised credentials, making sure your users get easy and secure access to the cloud should be a top priority.
Join Thycotic chief security scientist and author Joseph Carson as he explains a practical approach to help you define and implement privileged access cloud security best practices. He will also share how Thycotic’s new Access Control solutions can safeguard cloud access by both IT and business users.

KuppingerCole Webinar recording