1 Introduction
Digital technologies have transformed customer habits. With the increasing adoption of digital services and platforms, millions of people share their sensitive data with other organizations and entities. In many regions of the world, data regulation laws obligate organizations to provide secure user access to the customer data that is spread across different applications and directories. Access control is a key component of cybersecurity processes that enables organizations to manage who is authorized to access which data and resources. Organizations that fail to control user access can end up suffering from cyberattacks and/or violate regulatory compliance regulations. In order to mitigate risks and prevent cyberattacks, organizations must consider the right authorization concept that brings flexibility, adaptability, and observability to their business and IT environment.
Today, many organizations still use traditional Role-Based Access Control (RBAC) to grant access to applications and data based on a user's roles. However, IAM (Identity and Access Management) teams are required to manually change the access rights (via roles) in case of a job change, or if an employee leaves the company. In case of organizational changes, role models frequently require major updates, causing massive workloads. Furthermore, customer data use cases don’t tend to fit cleanly into roles; instead, access to customer data is managed by consents, entitlements and relationships which force organizations to look for access control solutions that extend beyond RBAC.
These traditional approaches for user access management are cumbersome to implement and inefficient, especially for large organizations working with dynamic organizations, a lot of change in human resources, plus the external entities to manage. Unlike roles, policies are easier to define, and they all have the same structure: Subject, Action, Resource, Context.
Addressing many pain points that organizations experience, PBAC (Policy-Based Access Control) enables administrators to have a greater control over access rights and edit permissions to a large number of users at once, coming into effect immediately and avoiding the lengthy and error-prone provisioning processes that are part of PBAC. Policies can be based on contextual controls and attributes, such as job title, file type, time of day, access location, and risk score. PBAC empowers IAM teams with flexibility to add fine-grained access control to resources and data based on policies.
PBAC allows organizations to enforce consistent entitlements across their IT environment from legacy applications and systems to IaaS (Infrastructure as a Service), cloud-based platforms, and multi-cloud deployments. An entitlement or authorization decision is provided to a Policy Enforcement Point (PEP), which can be the authentication system, API gateways, the applications themselves if they support such concepts, or integrated directly into company-owned and developed digital services. Modern applications are built on APIs, which provide a perfect hook to extend access control with PBAC capabilities without changing the application. Furthermore, organizations with legacy on-premise applications can, to a certain extent, adopt a policy-based approach to their access management systems.
A strong access management system is essential for embracing a Zero-Trust approach. PBAC contributes to this security paradigm by managing users’ access to systems and applications using predefined policies and contextual controls that are dynamically evaluated during the authentication or authorization. This aligns with one of the core principles of Zero-Trust, “Don’t trust. Verify!”.
This report looks at Ping Identity’s PingOne Authorize, which is one of the PBAC solutions in the market. Delivering capabilities like dynamic, policy-based authorization and API access management, PingOne Authorize allows organizations to centrally manage authorization, based on easy-to-create, fine-grained policies that are enforced at runtime.
2 Product Description
Founded in 2002, Ping Identity is an IAM company, headquartered in Denver, US with global presence and customer base. Ping Identity has offices in Denver, Austin, Boston, Vancouver, London, Edinburgh, Paris, Bangalore, Israel, and Melbourne. Having around 1400 employees, Ping Identity entered into a definitive agreement to be acquired by Thoma Bravo, a private equity firm, for approximately $2.8 billion in August 2022.
Offering capabilities like orchestration, fraud detection, risk management, directory, identity verification, personal identity, authentication, SSO (Single Sign-On), MFA (Multi-Factor Authentication), web/API access, dynamic authorization, and API intelligence, the PingOne Cloud Platform is a multi-tenant IDaaS (Identity as a Service) platform, designed to serve different use cases. Organizations can choose the right set of capabilities they need among PingOne for customers, PingOne for workforce, PingOne for government, and PingOne for individuals. Delivering a comprehensive set of cloud identity and access management services, the PingOne Cloud Platform helps organizations manage their identity challenges by allowing them to choose any PingOne services they need without interdependency or vendor lock-in.
Ping Identity provides integrations with over 1800 applications, services, and APIs, such as AWS IAM Identity Center, Google IdP Adapter, Salesforce, and Slack. The PingOne application portal is where users can single sign-on into the integrated applications using a central, unified interface.
PingOne offers a wide variety of IAM services such as PingOne API Intelligence, PingOne Authorize, PingOne Credentials, PingOne Fraud, PingOne MFA, PingOne Risk, PingOne SSO, PingOne Verify, and PingID. Users can view and monitor activities pertaining to the services they possess as well as add new services to their PingOne environment in the dashboards provided by PingOne. The dashboards can be customized to different viewing options for configured services, auditing, alerts, and environment properties. While the authentication and the authorize sections are the main dashboards, and separated from each other, users can access MFA, Risk, Fraud, and API Intelligence sub-dashboards under the authorize dashboard. MFA is required to access PingOne dashboards.
Based on the acquisition of Symphonic Software’s technology for policy-driven authorization in late 2020, Ping Identity is converging two software-based solutions, PingAccess and PingAuthorize, under a new native SaaS product, PingOne Authorize, which launched in late 2021. By controlling what end users can see and do inside of applications and APIs, PingOne Authorize delivers a fine-grained, cloud-based dynamic authorization that provides centralized visibility and management of access and authorization policies, and administration for applications, APIs, and data.
PingOne Authorize is a SaaS (Software as a Service) solution that ships with a business-friendly UI (User Interface). It remains available on-premises as PingAuthorize. Both deployment models support staging lifecycles: development, testing, and production. Ping Identity plans to offer PingOne Authorize as a managed service for hybrid deployment options in the future. For as-a-service deployments, PingOne Authorize can be easily added to organizations’ PingOne environment via the admin console. It can also integrate with other PingOne services, such as PingOne Fraud and PingOne Risk.
The Trust Framework is where an organization-wide view of data and service ecosystem is found. Here, technical teams retrieve definitions for digital assets, services, and users across the domains of their organization. This framework allows organizations to define entities that are used to build policies. The policies are typically defined by IAM or business teams who understand application requirements and regulatory compliance. The policies also define who has access to which resources and data.
PingOne Authorize delivers policy-based control of UX (User Experience), and fine-grained Attribute-Based Access Controls (ABAC) to manage data and application functionality based on attributes including user location, time of access, group membership, transaction value, devices, user preferences and behaviors, financial data, and risk scores. It enables adaptive authorization using external fraud and risk signals. Going beyond OAuth (Open Authorization) capabilities and recognizing the growing importance of APIs, PingOne Authorize aims to increase the flexibility and agility of API access management controls. Key capabilities include:
Dynamic Authorization: Dynamic authorization delivers fine-grained and context-aware authorization based on policies. It builds on centralized rules and policies to control who can access which data and take which actions in SaaS, mobile, web, and enterprise applications. Assembling contextual attributes like preferences, devices, risk scores, history, behaviors, transactions, and financial data, dynamic authorization offers real-time access request evaluation. To facilitate policy deployment and update, dynamic authorization extends roles with centrally managed policies. Externalizing authorization eliminates the need for code modifications and application downtime when stakeholders and developers make changes to policies. By providing insight into user behavior and activities with central monitoring and tracking capabilities, dynamic authorization aims to protect sensitive data and alleviate customers’ data privacy concerns. It centralizes data access governance control and protects data accessed through data stores and APIs. Dynamic authorization, by delegating administration, enables business users to implement their own policy administration.
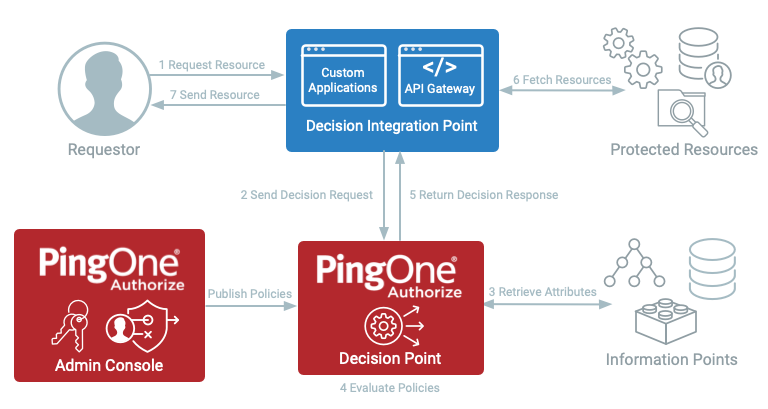
Figure 1: PingOne Authorize Dynamic Authorization Request Flow
- The admin console, also known as Policy Administration Point (PAP), centralizes authorization and manages policies.
- Custom applications or an API Gateway act as a decision integration point, also known as Policy Enforcement Point (PEP). Here, resource requests are received and sent to the decision point. The decision integration point can allow or block a user’s access or require further user action before proceeding (e.g. step up with MFA).
- The decision point receives the decision request and evaluates it with the retrieved attributes from information points. It is also known as a Policy Decision Point (PDP).
- The information point provides additional information to the decision point. Information points, such as data APIs, need to be defined as attributes and services in the Trust Framework. Retrieved information may be specific to the user (e.g. user profile attributes), the accessed resource, or the user’s environment (e.g. device risk). It is also known as a Policy Information Point (PIP).
API Access Management: Supporting custom and fine-grained policies, API Access Management enables IAM teams to centrally manage common access control use cases by extending the authorization capabilities of the API gateway. It is designed to centralize visibility of API activity and runtime auditing of authorization events, simplify API access use cases, and eliminate OAuth and OpenID Connect (OIDC) guesswork. It also helps IAM teams focus on authorization and access control rather than core API features. By providing centralized configuration, API Access Management reduces the complexities of working with OAuth across multiple systems. Coarse-grained access control capability ensures that only the right users and clients access API services. Ping Identity integration kits distribute enforcement to API gateways including Apigee, Kong, and Mulesoft.
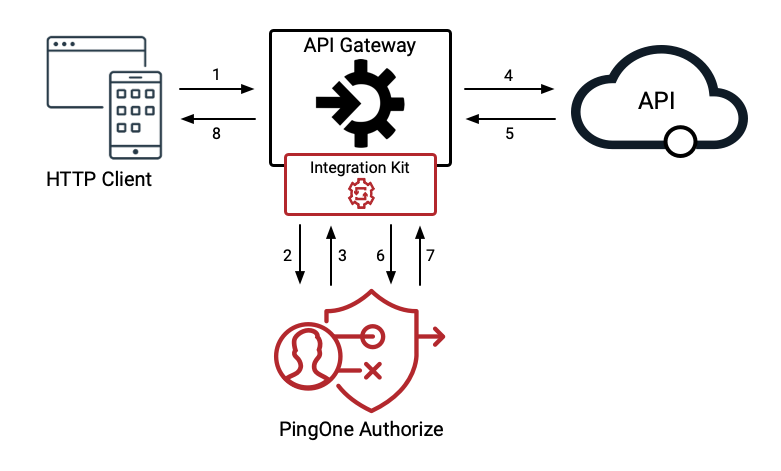
Figure 2: Traffic flowing through an API gateway, PingOne Authorize, and a protected API.
- An organization’s API Gateway manages the full lifecycle of APIs through design, development, test, deployment, versioning, security, and analytics. A PingOne Integration Kit installed on an API gateway connects APIs to the PingOne HTTP Access Policy service.
- API Services are the microservices and serverless functions developed by organizations, representing the actions and operations that users can interact with (e.g. read account, view resource). API Services may refer to target APIs, upstream APIs, or backend APIs.
- Authorization decisions for a given API Service are externalized to PingOne Authorize. Policy decisions are determined after the access control rules are evaluated. The policy decision can allow or block a user’s access, modify the API request, or filter and redact parts of the API response based on a user’s permissions.
3 Strengths and Challenges
PingOne Authorize offers a solution for fine-grained, policy-based authorization that allows organizations across industries to quickly react to changing business and regulatory requirements. PingOne Authorize supports orchestration with other IAM solutions and offers a wide variety of integration options to other applications such as business applications, APIs, and services. The Trust Framework utilizes organizational data on which the business-driven policies are defined.
Although Ping Identity delivers a comprehensive set of authorization services, some capabilities of PingOne Authorization, such as API access management and delegated administration support, are not included in certain solution packages. Supporting on-premises and cloud platforms, PingOne Authorize is not yet available for Hybrid platforms.
| Strengths |
|
| Challenges |
|
4 Related Research
Leadership Compass - Access Management 2022
Leadership Compass - Enterprise Authentication Solutions
Leadership Compass – Providers of Verified Identity 2022
Market Compass - Policy Based Access Management
Advisory Note - 2022 IAM Reference Architecture
Executive View – Ping Identity’s PingFederate
5 Copyright
© 2024 KuppingerCole Analysts AG all rights reserved. Reproduction and distribution of this publication in any form is forbidden unless prior written permission. All conclusions, recommendations and predictions in this document represent KuppingerCole's initial view. Through gathering more information and performing deep analysis, positions presented in this document will be subject to refinements or even major changes. KuppingerCole disclaims all warranties as to the completeness, accuracy and/or adequacy of this information. Even if KuppingerCole research documents may discuss legal issues related to information security and technology, KuppingerCole does not provide any legal services or advice and its publications shall not be used as such. KuppingerCole shall have no liability for errors or inadequacies in the information contained in this document. Any opinion expressed may be subject to change without notice. All product and company names are trademarks ™ or registered trademarks ® of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
KuppingerCole Analysts support IT professionals with outstanding expertise in defining IT strategies and in relevant decision-making processes. As a leading analyst company, KuppingerCole provides first-hand vendor-neutral information. Our services allow you to feel comfortable and secure in taking decisions essential to your business.
KuppingerCole Analysts AG, founded in 2004, is a global, independent analyst organization headquartered in Europe. We specialize in providing vendor-neutral advice, expertise, thought leadership, and practical relevance in Cybersecurity, Digital Identity & IAM (Identity and Access Management), Cloud Risk and Security, and Artificial Intelligence, as well as for all technologies fostering Digital Transformation. We support companies, corporate users, integrators and software manufacturers in meeting both tactical and strategic challenges and making better decisions for the success of their business. Maintaining a balance between immediate implementation and long-term viability is at the heart of our philosophy.
For further information, please contact clients@kuppingercole.com.










































