1 Management Summary
Much has changed since the last market compass on Dynamic Access Management. Technology is galloping ahead at dizzying rates that many organizations find difficult to assimilate. This is unfortunate because if they can't stay abreast of advances in technology, when new competitors come on the scene, agile and lean competitors without the baggage of more mature enterprises, there is a danger that established companies will find their market-share diminishing. But it does not have to be this way. With a pivot to a unified-services approach, underpinned by consistent policy, mature enterprises can compete with start-ups, leveraging their experience to remain competitive. A unified-services approach is one in which the services a user can access do not vary depending upon the technology on which they are deployed; accessing services will be consistent regardless of whether the applications are on-premises, delivered via cloud infrastructure or via cloud -native deployments.
To achieve this, organizations need to make a strategic decision to unify IT development and operations (DevOps). There must be a shift from a siloed environment to a holistic, integrated approach. Silo's may be functional i.e., staff from the marketing department do not talk to anyone in the production department; or infrastructure siloes may exist i.e., data center operators do not interact with cloud service providers and have nothing to do with SaaS (Software as a Service) applications on public cloud infrastructure. But such practices are detrimental, it must be remembered that all diverse deployments start as a tactical response to a business need. Migration to an 'integrated services' approach, driven by a common strategy is now required.
This strategy should be focused on managing complexity. Over the past few years, organizations have gone from managing their own data centers, to accepting services deployed on vendor-managed clouds, to deploying apps on VMs on public clouds, to allowing business units to engage with SaaS app vendors or cloud platform suppliers, to deploying containerized software, to developing cloud native solutions. Each step along this journey has decreased oversight across the IT environment and increased cybersecurity threats. Access control management of administrative accounts on cloud infrastructure is often inadequate. Nightly transfers of personal identity data to multiple SaaS providers across the internet are not uncommon. APIs in containerized cloud native deployments across disparate cloud environments occur in the absence of mandated management and security settings. The adoption of cloud platforms often abrogates the CIO from the responsibility for administration and governance services. The IT environment has become too broad for many CIOs to effectively manage and too complex to fully understand.
But complexity can be reduced by mandating a service-based approach, rather than a product approach, and by moving to automated, policy-based management across runtime environments. A service-based approach means applications are loosely coupled with the user interface provided to the client, the user no longer needs access to the infrastructure on which the application is running, they only need to access the exposed services. Policy-based access control assists in this decoupling; it allows organizations to enforce consistent entitlements across multiple applications for multiple business units. 'Where an app is running' becomes less important than the 'availability of the service' that it is providing. The focus is now on the response, resilience and redundancy of an organization's business services.
A four-step process is recommended for the design and deployment of a PBAM environment:
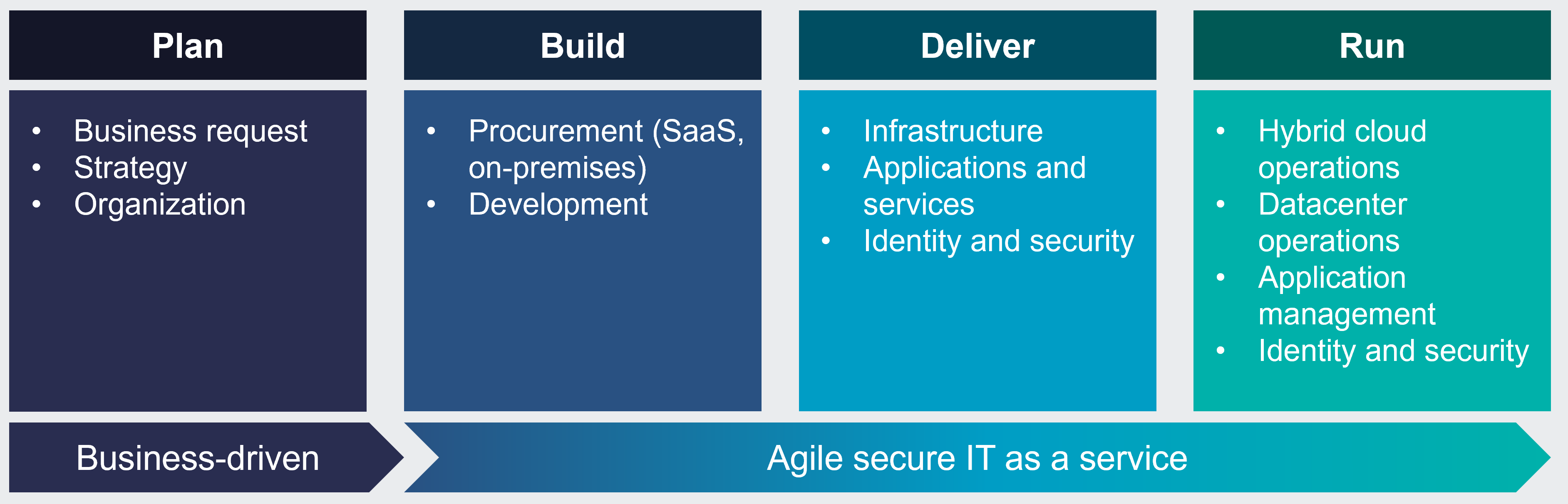
| Plan | A cross-functional team should be engaged for the project planning to ensure all potential stakeholders have input into the access control strategy for the organization. |
| Build | A design that satisfies the outcomes of the planning stage is required. A decision on the most appropriate deployment is required, and the most appropriate development environment must be selected. Component and system testing will complete the build stage. |
| Deliver | Stakeholders should be involved in the acceptance testing as the solution is promoted to production. Most development environments employ Continuous Integration/Continuous Delivery (CI/CD) toolsets that automate much of the deployment activity and keep diverse deployments current. |
| Run | Operational personnel require tools that provide visibility across hybrid and multi-cloud deployments and a management interface with dashboard features to allow continuous monitoring of the PBAM environment. Connection to the enterprise SOC/SIEM tools is highly advisable. |
A dynamic access management environment will reduce complexity by employing a consistent policy across the IT environment, from the on-premises services (legacy line-of-business applications), the IaaS (Infrastructure as a Service) cloud-based apps, and increasingly multi cloud deployments. A consistent set of policies across the entire environment is increasingly important for organizations that are adopting cloud native service deployments where it is no longer a monolithic VM being deployed but containerized services. Such an approach not only leverages benefits of the cloud, such as scaling, but also supports a more agile development environment, an important capability that will reduce 'time to value' and heighten competitiveness.
Cloud-native deployments, which expose services via containers or micro-services, require a new approach for access control. Legacy dynamic access management environments are not able to service multiple APIs in an efficient and agile manner, and typically do not support Cloud Native Computing Foundation (CNCF) protocols. But over the past two years vendors have developed tools to address this market. Cloud-native deployments leverage Open Policy Agent (OPA) protocols and adhere to the CNCF framework.
This Market Compass seeks to cater for both ends of the access control market from traditional PBAC environments, consisting of policy decision points servicing multiple enforcement points, usually adhering to the XACML framework on one end, to cloud-native environments servicing cloud container approaches and microservices platforms, typically adopting the OPA protocol, at the other end.
Key Findings:
- Rapid advances in technology development pose a threat to existing organizations that are typically less agile than their start-up competitors. PBAM solutions can assist by 'building-in' agility with common policies across multiple environments.
- Organizations must seek solutions that reduce complexity and encourage collaboration across the enterprise, a unified approach to providing services that transcend business units can encourage collaboration.
- Access control is increasingly recognized as being essential to cybersecurity, with account take overs responsible for most unauthorized intrusions, PBAM solutions provide access control consistency, reducing vulnerability.
- To fully leverage the benefits of cloud-deployed solutions a cloud-native approach to leverage the scaling capabilities of the cloud and increase agility is required.
- Robust governance strategy requires consistent access control policy across corporate resources. This requires:
- Centralized policy management
- Real-time policy decisions
- Policy lifecycle management and analytics
- To satisfy corporate governance requirements integration between the authorization engine and corporate SOC/SIEM tools is required.
















































