1 Introduction / Executive Summary
Operational Technology (OT) encompasses the hardware and software systems that control, automate, and monitor equipment and physical processes in industrial settings such as manufacturing, warehouse and logistics management, power generation and distribution, transportation, and healthcare. These systems include Supervisory Control And Data Acquisition (SCADA) systems, Programmable Logic Controllers (PLCs), Human-to-Machine Interfaces (HMIs) and other devices and software that are designed to monitor and control the operation of machines, processes, and other specialized equipment in real-time. Operational Technology (OT) includes Industrial Controls Systems (ICS), Critical Infrastructure Systems (CIS), and Industrial Internet of Things (IIoT).
Critical Infrastructure Systems include energy, communications, defense industrial base, critical manufacturing, food and agriculture, government, healthcare, and transportation sectors. Some organizations in CIS are public utilities. Organizations that use Industrial Controls Systems (ICS) are generally considered to be a superset of the sectors in CIS, many of which operate as private enterprises. Industrial IoT (IIoT) refers to commoditized, IP communications-enabled devices (often sensors) which are increasingly used within ICS and CIS.
OT environments can have very high availability and security requirements, which, in many cases, necessitate the deployment of specially designed cybersecurity and identity management solutions.
The need to secure OT has increased in prominence for multiple reasons. Regulation to protect the public is being legislated by governments in many jurisdictions worldwide. Governments have intervened in cases of compromise of OT infrastructure, particularly where CIS has been involved. Companies and utilities are investing in IIoT technology to take advantage of expanding functionality and are decreasing costs to improve efficiency. Lastly, some high-profile attacks on ICS and CIS have brought awareness of cybersecurity risks to both the general public and to the boardroom.
Successful cyber-attacks against ICS infrastructure can cause significant downtime, lost productivity, reputation damage, and even threaten for-profit companies’ viability. Successful cyber-attacks against CIS can cause power outages, failures of public utilities, and even jeopardize lives. Organizations that operate OT environments must invest to avoid the downtime and damage that results from cyber-attacks
Companies and utilities that have OT systems typically have extreme uptime requirements and very short and infrequent system maintenance windows. This can exacerbate the problems of upgrading security products and even keeping critical systems up-to-date with security patches.
Securing access to OT assets is a paramount concern. Some attacks against ICS and CIS operators have used improperly secured Virtual Private Networks (VPNs) and other remote access tools as vectors. The Zero Trust Network Access (ZTNA) model is a leading cybersecurity paradigm that is founded upon the principle of least privilege. ZTNA can help reduce the risk of unauthorized access to OT environments.
Organizations that have OT should regularly review their security architectures and make investments to close cybersecurity gaps where discovered.
This whitepaper will review the cybersecurity threat landscape for OT, describe the high-level security architecture and some of the tool types needed for OT, consider some of the key requirements of the German KRITIS regulation, and provide an overview of the Cyolo Zero Trust Access solution.
2 Highlights
-
Operational Technology, including Industrial Control Systems, Industrial IoT, and Critical Infrastructure, face many of the same threats as Enterprise IT but also threats that are specific to the OT world.
-
Governments have enacted regulations mandating cybersecurity for Critical Infrastructure including companies involved in high-priority manufacturing
-
Multiple complementary cybersecurity frameworks and standards exist to aid in designing OT security architecture
-
Cybersecurity architectures for OT must address asset discovery, access control, IT security tool integration, detection and response capabilities, and OT protocol level threats
-
Zero Trust Network Access is an excellent approach for enabling secure access control for OT environments
3 The OT Threat Landscape
OT and ICS have become increasingly vulnerable to cyber-attacks in recent years. Attackers are more frequently targeting OT and ICs due to geopolitics. These risks pose significant consequences, ranging from disruption of operations and denial of service to financial losses and even potential harm to human safety.
Industrial control systems comprise the technologies and processes responsible for managing and controlling essential operational functions, such as manufacturing processes, power generation and distribution, water treatment, and traffic and transportation systems. These systems rely on interconnected devices, sensors, and software to automate and monitor critical processes. However, this interconnectivity in itself exposes OT and ICS to an array of security risks and threats.
Consider the Colonial Pipeline incident of May 2021. Their enterprise IT assets were hit by a ransomware attack. Due to concerns that the ransomware would spill over into their pipeline controls systems, they shut down operations for six days during the investigation and remediation.
Ransomware is a top concern for OT/ICS security and for good reason. Ransomware attacks on industrial organizations doubled in 2022, mostly targeting manufacturing organizations. Ransomware attacks are very expensive, with the recent case of Dole stating that the February 2023 attack cost the company $10.5M and affected half of the company’s servers and one-quarter of their endpoints.
Dragos, an industrial cybersecurity specialist company, monitors threat actors that reconnoiter and attack OT systems. Dragos reported on the Chernovite group’s PIPEDREAM, which is a toolkit that can create and deliver malware that can compromise ICS. It has been used against the mining, renewable energy, food and beverage, pharmaceutical, chemical, water and wastewater industries. Attackers go after companies that can pay the ransoms and cannot afford the downtime.
Cybercriminal gangs and other threat actor groups have also started using Advanced Persistent Threat (APT) tactics, whereby they compromise endpoints and servers on victim networks and exfiltrate data (without encrypting it). The adversaries then threaten to publish it if a ransom is not paid. The numbers of both reported ransomware and data extortion cases are rising again in 2023.
Organizations that have OT face the same kinds of threats as enterprise IT including ransomware, account takeovers, APTs, and Supply Chains as vectors, as well as OT-specific threats.
Other cyber-attacks have been more direct. In February 2021, an attacker gained control of an HMI at the Oldsmar, Florida water treatment plant and briefly increased the amount of sodium hydroxide injected into the water supply. The attacker used a shared password for the TeamViewer remote access application. Plant operators reversed the malefactor’s actions within 3-5 minutes.
Some attacks have come through common software programs and network management solutions. The attackers in both the Kaseya and Solarwinds incidents used compromised server and software as vectors to infect and further compromise many organizations. Software Supply Chain vulnerability is seen as an escalating risk for both IT and OT estates.
4 Security Architecture for OT, CIS, and ICS to Aid in Regulatory Compliance
Designing and implementing security architectures for OT environments is more complicated than for IT environments. Though many traditional IT security tool types may work in OT, the specialized equipment, software, and communications protocols used in the OT world vary widely and often require dedicated OT security solutions.
For enterprise IT security, solutions such as Identity and Access Management (IAM), Endpoint Protection Detection & Response (EPDR), Network Detection & Response (NDR), Security Information and Event Management (SIEM), Secure Web Gateways (SWG), email security, Data Leakage Prevention (DLP), and Next Gen Firewalls (NGFW) are always recommended. In many cases, these tools are essential for areas with OT as well. However, there are many OT environments, particularly those in CIS and ICS, where agent-based security products cannot run because the devices that operate in those areas cannot accept software agents. Typically this is because there may be operating system incompatibilities, installing unapproved software may be prohibited by the device manufacturers, or the devices themselves may be supported by manufacturer or an authorized third party.
OT security architectures need to address eight major areas of functionality.
Asset Discovery and Management – One cannot protect assets if one doesn’t know they exist. Asset discovery is foundational for security. There are two major methods for performing asset discovery: active and passive. Active asset discovery entails setting up nodes or appliances that have access to all OT network segments and allowing them to regularly query devices and interpret their responses. Passive asset discovery requires nodes or appliances on OT network segments that can listen and understand the network communications between OT components, such as HMIs, PLCs, and sensors. Both approaches use the discovered information for building a central database. Asset management involves tracking hardware, firmware, operating system, and OT applications.
SIEM and SOC Integrations – OT networks often have a wide array of computing devices, sometimes including standard IT servers, applications, and endpoints. Security teams need a centralized repository of security information. Traditional IT security services such as SIEM (Security Information and Event Management), which are designed to collect and parse logs and output security intelligence, are also useful and necessary in OT environments. The primary design consideration is whether to combine OT signals into the general enterprise IT SIEM and security infrastructure. Some industries are regulated such that logical and physical separation are required. However, others may find value in consolidating IT and OT into a single SIEM. SIEMs are one key piece of the overall security toolset used in SOCs (Security Operations Centers). Depending on the size, complexity, and regulatory landscape, some ICS and CIS operators may choose to dedicate SOC(s) to their OT infrastructure.
Management Interface - Security solutions for OT must provide an interface that shows environment details, displays real-time events, and provides management capabilities. The user interface should be highly functional and intuitive. The management interface should make it easy to rotate passwords and possibly defer password management to an IAM and Privileged Access Management (PAM) solution, particularly for service and device accounts.
Protocol Support – ICS and CIS applications and devices often use different communications protocols than are typically found on IT networks. HMIs, PLCs, and sensors use protocols such as BACnet, CANbus, CIP, DNP3, IEC 61850, IEEE 11073, LonTalk, ModBus, MQTT, OPC, S7, XMPP, and others. As examples, DNP3 is used for SCADA communications in public utilities; ModBus is widely used in manufacturing for PLC and SCADA communications; S7 is used by operators of Siemens equipment; and MQTT and XMPP are lightweight messaging protocols used by IoT and IIoT devices. Most enterprise IT security tools do not understand these protocols sufficiently to be able to detect and respond to threats on OT networks; thus, specially designed OT security solutions are needed.
Threat Detection – OT networks and the devices that operate within them face many of the same threats that can be found in IT plus additional types of threats specific to the type of environment. Threats include ransomware and DoS as well as malicious firmware, rogue insiders, and supply chain attacks. OT environment security challenges can be compounded by insufficient network segmentation, weak or hard-coded passwords, and lack of interoperability with standard IAM solutions. Access to OT specific threat intelligence is required. Security solutions in this space ideally should employ Artificial Intelligence / Machine Learning (AI/ML) based detection models to develop baseline profiles of normal activities, detect anomalous behavior, and classify potential malicious activities for investigation.
Event Response – Once security events are detected, they must be dealt with promptly. OT security tools need capabilities to take actions such as collecting forensic information, terminating processes on affected nodes, suspending user accounts, requiring additional (stronger) authentication or authorization, terminating networks connections, isolating nodes or networks, etc. Solutions should allow for pre-defined and customizable playbooks to direct responses, in some cases automatically.
Deception Tools – Given the criticality of OT systems, luring would-be attackers away from production assets and/or having the ability to learn about their Tactics, Techniques, and Procedures (TTPs) has become a requirement. OT security solutions may include deception features that enable emulation of certain ICS and CIS device types, communications, and credentials (including service account types).
Access Control – The Zero Trust Network Access paradigm and principle of least privilege applies to all OT environments: every access attempt to any OT resources must be properly authenticated and authorized. Identity and Access Management (IAM) solutions must be in place to create and manage users, groups, entitlements, and affected logical resources. Strong Multi-Factor Authentication (MFA) should be used for both local and remote access. Fine-grained authorization should govern the types of actions authenticated users can take. Accounts must be managed according to lifecycles. Devices and applications that require elevated privileges must be carefully secured and not over-provisioned. Integration with enterprise IAM solutions can make managing logical access in OT much easier. OT settings usually include multiple physical locations, and access control to facilities must be in place. Wherever possible, Physical Access Control Systems (PACS) should be integrated with OT IAM systems (and enterprise IT) systems.
Zero Trust Network Access assumes that every network is always hostile, and thus, any IT or OT system, application, or user is constantly exposed to potential external and internal threats.
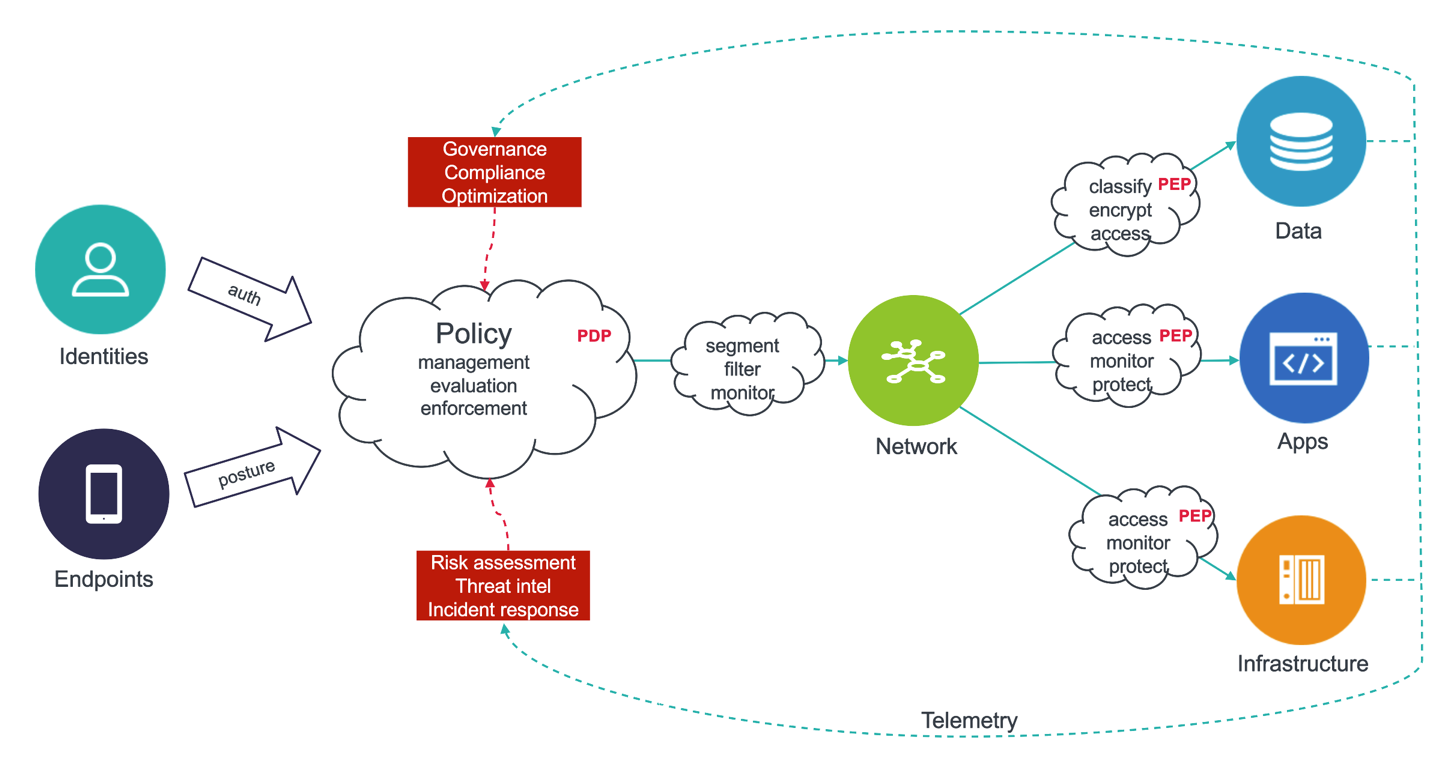
Figure 1: The Main Components of Zero Trust Architecture
Zero Trust Network Access solutions for OT must address the following requirements:
- Application-level, not only network-level segmentation
- Separation of control and data planes
- Support for common OT applications and devices
- Scalable, decentralized architecture to reduce latency
- Centralized, unified deployment and policy management
- Device posture validation as a prerequisite for access
- Multi-factor authentication, single sign-on support, granular authorization per session
- Continuous session monitoring, anomaly detection
- Additional threat protection capabilities
- Built-in reporting and compliance audit functions
For more information on Zero Trust Architectures, see NIST SP 800-207.
5 The KRITIS and BSI IT Security Act 2.0 Cybersecurity Regulations
The risks and consequences of cyber-attacks against critical infrastructure have driven adoption of regulations in various locations around the world mandating secure architectures and technical controls. KRITIS and the follow-on IT Security Act 2.0 are related examples of such regulations.
The term KRITIS (KRITische InfraStrukturen, or critical infrastructure) is a comprehensive cybersecurity framework that is promulgated at protecting critical infrastructures from cyber threats. The German government enacted KRITIS regulations that set forth requirements for organizations both public and private that are operating in the defined sectors. KRITIS mandates measures for ensuring the security, availability, and integrity of critical infrastructure systems, applications, and data. The German Federal Office for Information Security (BSI) is responsible for designating critical infrastructure sectors based on the provisions outlined in the Act on the Federal Office for Information Security (BSIG).
Critical infrastructure (KRITIS v1) is defined as facilities, equipment, or parts thereof which
-
are part of the sectors energy, information technology and telecommunications, transportation and traffic, health, water, nutrition, and the finance and insurance industries and
-
are of high importance to the functioning of the community since their failure or impairment would result in material shortages of supply or dangers to public safety.
In 2021, Germany passed the IT Security Act 2.0, which expands the types of affected organizations to include waste management, arms manufacturers, defense contractors, chemical manufacturers, IT security product and service vendors, and all other large German companies. Nearly 1,800 organizations are covered by IT Security Act 2.0. The scope also now includes software and IT services as well as facilities. After being notified by the BSI that an organization is subject to these regulations, critical infrastructure must register and document pertinent systems, and points of contact within each organization must be named.
According to section 8a (1) BSIG, appropriate cybersecurity controls must be in place to avoid disruptions in KRITIS systems. Specific measures are not called out, but rather, other cybersecurity standards are referenced, including ISO 27001, and the NIST Cybersecurity Framework (CSF). Other standards for specific industries are referenced, such as ISO 27017/27018 for cloud, ISO 27019 and CIP for energy utilities, and CLC/TS 50701 for railways. Detected attacks or service interruptions must be reported immediately, the message format is clearly defined.
KRITIS operators are obligated to conduct regular risk analyses to discover and evaluate potential threats, vulnerabilities, and risks to their systems. This includes assessing the threats, potential impact of disruptions, and implementing appropriate risk management measures.
KRITIS requires bi-annual audits and/or certifications from identified organizations. The BSI may, at its discretion, also require that its agents have access to critical infrastructure operators’ facilities and systems.
KRITIS operators should cooperate with the BSI and other relevant authorities, as well as share threat and risk information to enhance the collective security and resilience of all critical infrastructure.
Governments regulate and mandate strict cybersecurity for critical infrastructure because of its importance in the maintenance of societies.
Taking the NIST CSF as a guide for security architecture, there are five major functions and multiple categories of tools and tasks per function that should be deployed:
Identify: Asset Management, Business Environment, Governance, Risk Assessment, Risk Management Strategy, and Supply Chain Risk Management
Protect: Identity Management and Access Control, Awareness and Training, Data Security, Information Protection Processes & Procedures, Maintenance, Protective Technology
Detect: Anomalies and Events, Security Continuous Monitoring, Detection Processes
Respond: Response Planning, Communications, Analysis, Mitigation, Improvements
Recover: Recovery Planning, Improvements, Communications.
The functions and categories from NIST CSF align with the tool types recommended in the section on Security Architecture for OT, CIS, and ICS to Aid in Regulatory Compliance.
Non-compliance with KRITIS can be costly, with fines ranging from unavailability of the named contact up to €100,000, failure to report disruption at €500,000, and failure to comply with BSI orders to rectify security deficiencies at €20,000,000.
6 Cyolo Industrial Secure Remote Access
Cyolo’s Zero Trust Access solution is designed for ICS and CIS environments and provides Zero Trust Network Access for customers’ existing infrastructure, legacy applications, and even air-gapped hardware.
Cyolo, founded in 2020 in Tel Aviv, is a well-funded cybersecurity startup focused on securing access to OT resources. Cyolo solves some common security challenges, including Industrial Secure Remote Access, Third Party Secure Access, and Mass Onboarding Secure Access. All are designed to meet the particular access control requirements of OT environments such as in manufacturing, energy generation and distribution, and oil and gas, as well as IT environments for insurance, finance and banking, life sciences, and pharmaceutical industries.
For Industrial Secure Remote Access, there are two major components: the Identity Access Control (IDAC), which is the central engine, and the Edge, which is the gateway that funnels user connections to the IDAC for authentication and authorization. The IDAC can serve as an Identity Provider (IdP), which allows Cyolo solutions to work in completely air-gapped environments. Cyolo’s IDAC can also work as a Relying Party to Microsoft Active Directory (AD), Azure AD, or any LDAP compliant directory. The IDAC can also leverage RADIUS, OpenID, and SAML. Cyolo supports SCIM for bulk import and provisioning of users from these directory types. The IDAC uses a Reverse Proxy (RP) architecture to protect OT and enforce access control policies.
Acting as an IdP, Cyolo offers TOTP, SMS, and QR code authentication. Via the federation methods listed above, Cyolo can accept CAC/PIV cards, Smartcards, and Yubikeys for strong, hardware-based authentication. Customer administrators can leverage Microsoft AD and Azure AD groups to build policies or create groups within the IDAC which can be composed of members from any directory. The IDAC also serves as Privileged Access Manager (PAM), managing PKI keys in a vault and recording session level activities. Supervisory approval for sessions and the recording of sessions is particularly useful for preventing unwanted firmware changes and having a user-level accountability for critical actions.
With regard to the Purdue Model, the IDAC is generally installed in Level 2 (controls systems such as HMIs and SCADA) or Level 3 (operations systems such as batch management, data historians, and middleware). Edge components perform Server Name Indicator (SNI) routing. Edge components are most often installed at perimeters between Purdue Levels 3 and 4. Enterprises may deploy multiple Edges for internal IT staff, IT staff operating remotely, equipment manufacturers, and contractors. Both the IDAC and Edge run on Ubuntu.
The IDAC controls access to the networks that contain the ICS and CIS devices from networks above the Purdue Levels 2 and 3. IDACs do not segment or block access from within those ICS and CIS networks.
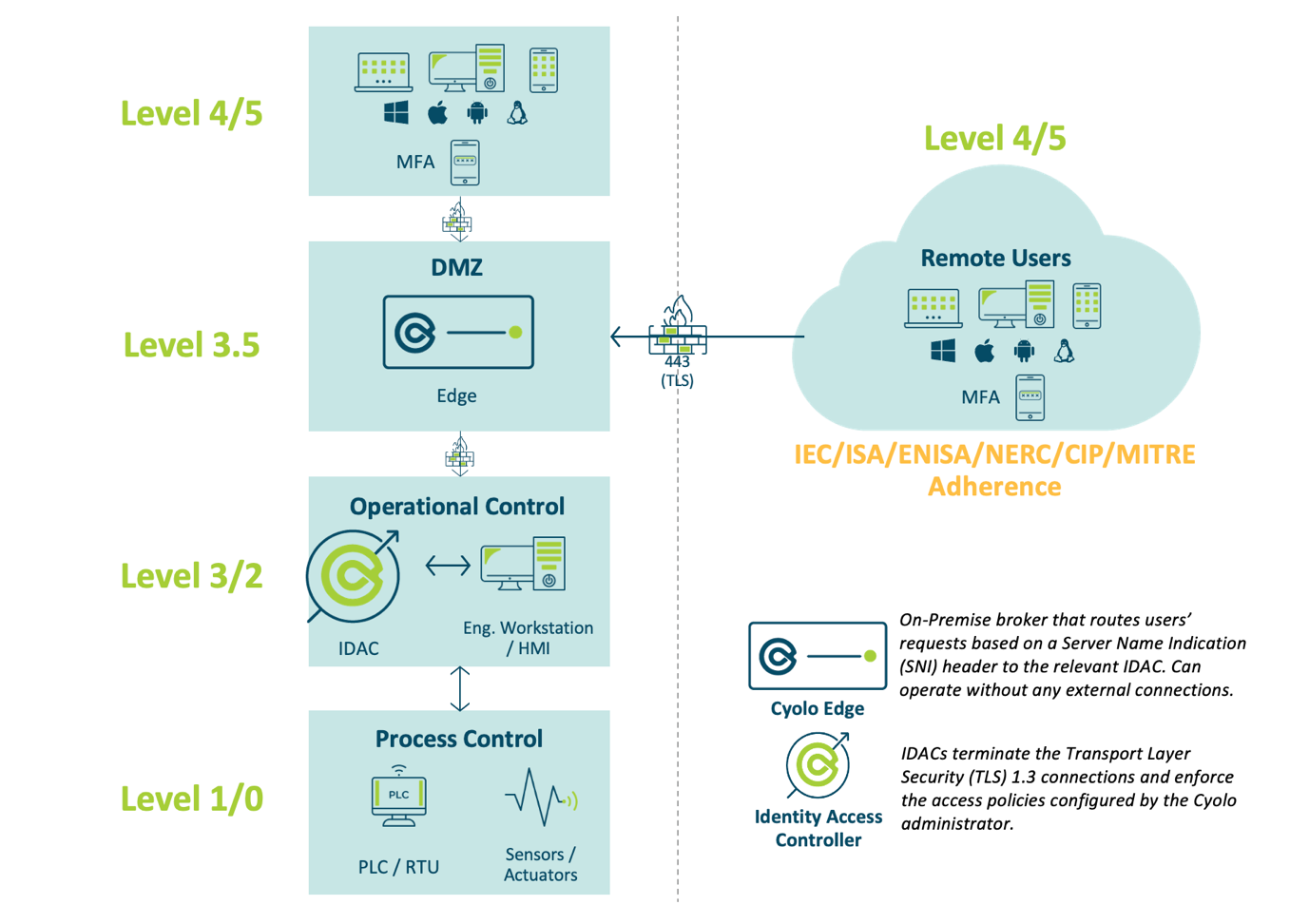
Figure 2: Cyolo Industrial Secure Remote Access Product Architecture (used with permission)
Customer administrators configure access by groups to applications. Applications supported include RDP, SSH, telnet, and VNC. Cyolo can broker both web or native application access (whereby authentication codes and CLI strings are delivered via the browser for the user to paste into thick client apps such as PuTTY). Credentials are not shared between the originating endpoint and protected system in both native and web access methods. Cyolo offers a thin connector client for legacy applications that require specific TCP/IP ports. All communication between the IDAC and users is over HTTPS (port 443), while the IDAC handles port mapping for those legacy apps for users. Separate SSH jump boxes are not needed.
Historically, many organizations have used shared or group accounts for access to OT resources. Shared accounts lack individual accountability for administrative actions, which may not be compliant with some regulations and decrease security posture. Cyolo’s solution enables organizations to force individual users to authenticate (and optionally be authorized on a per-session basis by supervisors), thereby gaining the identity granularity needed for operating in high security environments.
Policies can lock down access to specific IPs, IP ranges, or URLs within the OT networks. Many additional attributes can be evaluated within policies, including device posture checks, device certificates, geo-location, supervisor approval, and date/time. The IDAC can apply very granular controls to request actions, such as file upload/downloading, using the clipboard, redirecting drives, using or redirecting printers, using multiple monitors, recording session, supervisory interacting with sessions, allowing camera recording, allowing audio input,
The IDAC can enforce Device Posture Checks (DPCs) on hosts that have Cyolo agents installed. DPC policy elements can include limiting access to certain operating system levels, requiring endpoints to be joined to the domain, drives to be encrypted, and requiring certain files to be present (which can be extended to include requiring anti-malware).
From a user perspective, all their provisioned and authorized applications appear in their portal after successful authentication. Users can customize the portal appearance to make it more efficient for how they work. Mobile device agents are available, and users can now access their portals from Android & iOS devices.

Figure 3: Cyolo Application Portal (used with permission)
The IDAC log files show event ID, date/time, IDAC name, site, user, authority, accessed application, status, and IP address. The IDAC sends event telemetry to SIEMs via syslog or to AWS S3 buckets. All IDAC functions are exposed via Swagger documented APIs. Product roadmap items include API-level integration with other IAM consoles and interoperability with additional security tools such as SOAR systems.
Cyolo Industrial Secure Remote Access provides a feature-rich access control solution for OT, ICS, and CIS.
Cyolo Industrial Secure Remote Access combines Zero Trust Network Access and Privileged Access Management capabilities for Operational Technology Environments.
7 Recommendations
Organizations that operate OT face significant challenges in security. In many cases, these organizations have the same security risks as enterprise IT plus special risks from threats that target the specialized equipment used in manufacturing, transportation, power generation and distribution, agriculture, etc. Therefore, these organizations must develop and maintain a security architecture that adequately protects both types of environments.
As governments have recognized the importance of both CIS and high-priority ICS, many have enacted regulations that require organizations operating in these spaces to augment their security. In the US, the National Institute for Standards and Technology has a number of Special Publications that can aid in designing more secure OT architectures, including NIST SP 800-53 Security and Privacy Controls for Information Systems and Organizations, NIST SP 800-82 Guide to Operational Technology (OT) Security, NIST SP 800-161 Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations, and NIST SP 800-207 Zero Trust Architecture. The NIST Cybersecurity Framework is referenced by many other organizations and governments for design principles.
The North American Energy Reliability Corporation (NERC) has guidelines for power generation and distribution organizations: CIP.
CIS organizations operating in the EU need to comply with the European Program for Critical Infrastructure Protection Revision of Directive 2008/114/EC and the European Union Agency for Cybersecurity (ENISA) Network and Information Systems Revised Directive (common called NIS 2). In Germany, the aforementioned and referenced KRITIS and IT Security Acts apply.
In order to create a resilient cybersecurity architecture for OT, we recommend considering the tools that address the full set of functions described in section one, including asset discovery and management, SIEM and enterprise SOC integration, unified management interfaces, OT protocol support, OT threat detection and response, deception tools, and access controls.
Access Controls for OT are of the utmost importance. Proper authentication and authorization in line with Zero Trust principles can reduce the risk of compromise, ransomware, upstream supply chain attacks, and disruption of services. To design and deploy Zero Trust Network Access for OT, we recommend surveying your existing OT infrastructure and associated access controls. Identify all users, groups, and repositories, keeping in mind that many users from outside your organization may have accounts or various entitlements. Discover all the assets in the lower Purdue levels (under and sometimes including level three) and the protocols and applications used to communicate with them. Look for ZTNA solutions that support strong authentication, MFA, federation, and granular authorization for all users, regardless from which domains they originate. ZTNA solutions for OT should also allow managing elevated privileges, supervisory approvals, and detailed auditing.
Zero Trust is a journey. Given the size and complexity of many organizations that run Operational Technology, it will likely take some time to roll out ZTNA solutions that cover the full enterprise. Periodically assess your progress and be prepared to upgrade solutions as new ZTNA capabilities become available. Keeping components up-to-date with firmware and patches is also an essential activity to protect ZTNA solutions and the systems which they protect secure.
8 Related Research
NIS2 Directive - Who, What, and How
Leadership Brief: EU NIS2 Directive
Leadership Brief: Business Continuity in the Age of Cyber Attacks
Leadership Brief: A Methodology for Architecting a Secure Future
Advisory Note: Maturity Level Matrix for Cybersecurity
Advisory Note: Cyber Risk – Choosing the Right Framework
Market Compass: Cybersecurity for Industrial Control Systems
Leadership Compass: Security Orchestration Automation & Response
Leadership Compass: Zero Trust Network Access
9 Copyright
© 2024 KuppingerCole Analysts AG all rights reserved. Reproduction and distribution of this publication in any form is forbidden unless prior written permission. All conclusions, recommendations and predictions in this document represent KuppingerCole's initial view. Through gathering more information and performing deep analysis, positions presented in this document will be subject to refinements or even major changes. KuppingerCole disclaims all warranties as to the completeness, accuracy and/or adequacy of this information. Even if KuppingerCole research documents may discuss legal issues related to information security and technology, KuppingerCole does not provide any legal services or advice and its publications shall not be used as such. KuppingerCole shall have no liability for errors or inadequacies in the information contained in this document. Any opinion expressed may be subject to change without notice. All product and company names are trademarks ™ or registered trademarks ® of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
KuppingerCole Analysts support IT professionals with outstanding expertise in defining IT strategies and in relevant decision-making processes. As a leading analyst company, KuppingerCole provides first-hand vendor-neutral information. Our services allow you to feel comfortable and secure in taking decisions essential to your business.
KuppingerCole Analysts AG, founded in 2004, is a global, independent analyst organization headquartered in Europe. We specialize in providing vendor-neutral advice, expertise, thought leadership, and practical relevance in Cybersecurity, Digital Identity & IAM (Identity and Access Management), Cloud Risk and Security, and Artificial Intelligence, as well as for all technologies fostering Digital Transformation. We support companies, corporate users, integrators and software manufacturers in meeting both tactical and strategic challenges and making better decisions for the success of their business. Maintaining a balance between immediate implementation and long-term viability is at the heart of our philosophy.
For further information, please contact clients@kuppingercole.com.