1 Introduction
Endpoint Privilege Management (EPM) platforms manage threats associated with privileged access rights originating on laptops, tablets, smartphones, or other endpoints. EPM tools offer controlled and monitored escalation of user privileges on endpoints and often include capabilities such as application white and blacklisting for endpoint protection. Some form of user behaviour analytics tool is also commonly included.
Traditionally, privileged access was primarily given to a small set of administrators who needed to perform maintenance and upgrade tasks, mostly on-premises LANs or endpoint machines. In some cases, senior employees may have had elevated access rights for specific tasks. Privileged management use cases now extend across entire organizations, with users requiring task-based and workflow access to data, services, and applications held on legacy systems and multi-cloud-based infrastructures. And increasingly admins, users, and specialists such as DevOps will seek access from an endpoint device, which may not be issued by the organization itself.
This change explains why PAM software, in general, has developed in the last few years. Both new and traditional vendors have responded well to demands for more advanced PAM capabilities suitable for the modern computing era. And this development has extended to the previously static area of Endpoint Privilege Management which, now very much part of the multi-cloud, hybrid IT architectures currently proliferating.
Interest in Least Privilege and Zero Trust based architecture and policies has also grown as organizations look to secure the cloud as well as on premises. Buyers are increasingly aware that a well-configured, modern PAM platform can be an integral part of such architecture and that the traditional capabilities of PAM must extend to supporting cloud environments and SaaS applications and services.
The future of business operations will revolve around a new paradigm of a highly dynamic IT architecture that melds multiple cloud platforms with legacy networks on premises, partner networks, and even, in some cases, mainframe installations. This is what KuppingerCole has christened the Dynamic Resource Entitlement and Access Management (DREAM) paradigm and is what the next iteration of modern PAM platforms (and other identity and data governance tools) should support; to deliver secure access entitlements and greater business value across a new generation of cloud resources and operations.
Moreover, the outbreak of the pandemic and subsequent alteration in the work culture has meant that workforces are accessing applications remotely on all sorts of devices. These new, ultra-hybrid networks will push existing identity and security frameworks to their limit and call for solutions that provide controlled, rapid access to dynamic, often ephemeral resources, wherever they exist. Managing dynamic privileged access from endpoints must be secure and friction free if it is to succeed in delivering value to the organization and convenience to users.
2 Product Description
Founded in London in2006, ARCON has established itself as one of the leaders in Privileged Access Management (PAM) software, with a growing customer base. ARCON has a local presence in UK, USA, EMEA, APAC and ANZ with its Operations and R&D center in Mumbai, India.
Designed to enforce a Just-in-Time (JIT) privileged access principle following the principles of Zero Trust and Least Privilege, ARCON Endpoint Privilege Management is presented as a centralized component to ensure a rule and role-based access to business-critical applications. The centralized component of ARCON EPM can be implemented on cloud or on premises and end users connect from an endpoint via an authorized browser.
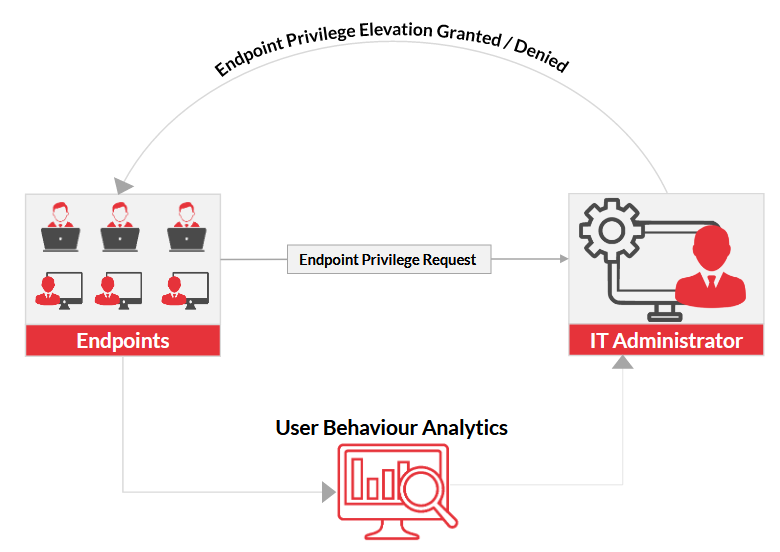
ARCON Endpoint Privilege Management is based on a simple concept; an end user requests privileged access to install an application, run an application in elevated mode, or change the configuration of the system or other potentially risk activity. Such request must be approved by an administrator before it can happen.
Increasingly such requests will be dealt with on a Just in Time (JIT) basis in line with Zero Trust and Least Privilege principles, rather than set up as a standing privilege account - and ARCON's platform supports this out of the box.
The access platform is attached to a User Behaviour Analytics Engine (UBA) which compiles and filters user activity data at endpoints to help reduce bad actor activity and employee error (sometimes referred to as insider threat). Administrators and managers can use this data to improve endpoint security and protect systems from unauthorized access in the future.
ARCON EPM wisely focuses on policy management to assist in managing privileged access. It creates policies for end users by automatically profiling the user's roles and responsibilities to assist in provisioning a policy-based access management system for the organization
The package is set up for an increasingly common scenario in business identity management, i.e., nontraditional privileged users seeking on the fly access to resources for a particular task or project. If the identity has already onboarded to the platform, an admin can quickly decide whether to allow access on a JIT basis -or whether to reject it. If that user has not been already profiled, this task can be automated as before. It's simple and effective.
Malware and ransomware, the scourge of business today, often hitch a ride into corporate systems by fooling end users to open what looks like a benign application or email. If a user attempts to execute an application already on the application backlist this operation will be automatically blocked. Access to non-authorized web browsers can also be blocked on a similar basis. The safe use of web browsers is often overlooked but remains a potent threat surface as attackers seek to exploit vulnerabilities in browsers, and even those features designed to help users such as password managers. With ARCON EPM, admins can restrict users to authorized browser, and possibly disable features within the browsers.
Extrusion or copying of files via an endpoint or USB should be controlled as part of any Endpoint Management program and the ARCON platform can automatically block file copy via USB to a third-party device - and can spot uploads from USB devices also. Useful and important. Few PAM platforms today are shipped without some form of analytics and ARCON offer a good option here with its expertise gained in wider PAM for behaviour analytics, and specifically geared to the needs of remote access management. ARCON has engineered Machine Learning and AI to assist in detecting patterns of misuse and or suspicious behaviour.
Critical alerts displayed during monitoring of endpoint privileges have categories as per the extent of seriousness and risk to the wider organization. The patterns of anomalies and the importance of accessed resources decide if the alerts are low, medium, and high.
ARCON goes a bit further with its analysis engine, however. It brings with it a level of data governance not often seen in other EPM products. The analysis provides insight into specific data classification, whether critical data resides on the endpoint and level of exposure.
Every day enterprises generate hundreds of gigabytes more business data. ARCON Data Intellect builds a ring-fence around data and builds a contextual security layer around the data. ARCON Data Intellect enables the classification of data, itemization of the exposed data, categorization of the critical data, and understanding of the 'where' and 'what' of data. With this, it provides actionable insights on data that is useful for forensic analysis and overall information security.
In addition, the File Integrity Monitoring (FIM) capability can track unauthorized file changes on user device in real time and processes, track unauthorized changes and keep a track of file history, and roll back if needed. This level of data governance and lifecycle management is unusual in a EPM product and is very welcome, especially in the environment where remote and home working, and subsequent new data flows, is prevalent.
For those looking for a wider PAM solution, ARCON also offers software which is fully compatible with the ARCON EPM platform. These opens more advanced PAM features to the customer including DevOps environment support which controls access to embedded secrets and scripts in DevOps pipelines. There is support SSH keys (in addition to vaulted passwords) which provides an encrypted and stronger set of credentials to protect access to privileged accounts as there is always a danger that passwords can be exposed by brute force techniques. Privileged access management must also include controlling machine identities in modern multi-cloud and hybrid computing environments. ARCON PAM supports Application to Application Password Management (AAPM) through an automated process where password changes are managed by giving the required details of the servers, the IP addresses, and the new passwords for the authentication process.
Finally, there is the option to integrate ARCON Guard. This is a SSH server-based utility for command restriction and elevation. It restricts and elevates all the commands when the server is accessed through third-party applications. The file monitoring feature detects when and who made the modifications to critical system configuration files on the server
All of this ensures that while ARCON Endpoint Privilege Management is a relatively simple application, it does provide a pathway into integrating ARCON's well-rounded set of PAM applications and tools as access management needs of the organization expand.
3 Strengths and Challenges
ARCON has fashioned a practical and effective Endpoint Privilege Management platform that is simple to deploy and to use. It's good enough stand on its own for organizations that are seeking to manage increased privileged activity, even if they already have a PAM solution installed for more traditional PAM applications. Even better, ARCON EPM can be deployed as a first PAM platform and added to by ARCON's other PAM products to create a more comprehensive suite - or even left as a stand-alone platform for organizations that have increased risk at the endpoint.
As well as the JIT capability of managing privilege access and the good level of analytics offered in its UBA engine, ARCON has also seen the importance of data governance and lifecycle management as more data and files are transferred from enterprise architectures to endpoints. It's the wisdom of including these that sets the platform apart from many others in the sector. Against this is perhaps an interface that looks a little dated and ARCON's need to market the platform more effectively, but overall, this is a well-engineered and scalable platform that will fulfill the needs of many organizations seeking better control of privileged data flows across endpoints.
| Strengths |
|
| Challenges |
|
4 Related Research
Blog: PAM Can Reduce Risk of Compliance Failure but is Part of a Bigger Picture
Blog: Privileged Access Management Can Take on AI-Powered Malware to Protect
Blog: Taking One Step Back: The Road to Real IDaaS and What IAM is Really About
Market Compass: Data Governance Platforms -71137
Leadership Brief: Privileged Account Management Considerations - 72016
Leadership Compass: Identity Provisioning - 70949
Leadership Compass: Identity Governance & Administration - 71135
Leadership Compass: Privileged Access Management - 80636
5 Copyright
© 2024 KuppingerCole Analysts AG all rights reserved. Reproduction and distribution of this publication in any form is forbidden unless prior written permission. All conclusions, recommendations and predictions in this document represent KuppingerCole's initial view. Through gathering more information and performing deep analysis, positions presented in this document will be subject to refinements or even major changes. KuppingerCole disclaims all warranties as to the completeness, accuracy and/or adequacy of this information. Even if KuppingerCole research documents may discuss legal issues related to information security and technology, KuppingerCole does not provide any legal services or advice and its publications shall not be used as such. KuppingerCole shall have no liability for errors or inadequacies in the information contained in this document. Any opinion expressed may be subject to change without notice. All product and company names are trademarks ™ or registered trademarks ® of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
KuppingerCole Analysts support IT professionals with outstanding expertise in defining IT strategies and in relevant decision-making processes. As a leading analyst company, KuppingerCole provides first-hand vendor-neutral information. Our services allow you to feel comfortable and secure in taking decisions essential to your business.
KuppingerCole Analysts AG, founded in 2004, is a global, independent analyst organization headquartered in Europe. We specialize in providing vendor-neutral advice, expertise, thought leadership, and practical relevance in Cybersecurity, Digital Identity & IAM (Identity and Access Management), Cloud Risk and Security, and Artificial Intelligence, as well as for all technologies fostering Digital Transformation. We support companies, corporate users, integrators and software manufacturers in meeting both tactical and strategic challenges and making better decisions for the success of their business. Maintaining a balance between immediate implementation and long-term viability is at the heart of our philosophy.
For further information, please contact clients@kuppingercole.com.










































