1 Introduction / Executive Summary
In recent years, several well-known software supply chain attacks have raised significant attention, such as the SolarWinds Supply Chain attack in late 2020 through a compromised SolarWinds' software development process which allowed malicious code to be injected into their Orion platform updates. Shortly after, in 2021, a Codecov Bash Uploader breach occurred when a popular code coverage tool script had been compromised, through which attackers gained unauthorized access to Codecov's infrastructure and modified the Bash Uploader script to collect sensitive environment variables and send them to an external server. This attack potentially exposed credentials and other sensitive data from organizations using Codecov. These and other software supply chain attacks led the U.S. government to issue an Executive Order on Improving the Nation's Cybersecurity by modernizing cybersecurity practices such as taking a zero-trust posture, improving its detection and response to cyber threats, and having the ability to investigate and recover from cyber-attacks. In one of the steps, the Executive Order calls out explicitly the documentation of a Software Bill of Materials (SBOM) for software products. An SBOM creates a machine-readable inventory of the components of a given software product. However, a Software Composition Analysis (SCA) is typically performed before generating an SBOM. An SCA analyzes the software components used in an application or system to identify and track their origins, licenses, and any known vulnerabilities or security issues. It gives insights into understanding the composition of the software and its dependencies. Once the SCA gathers the information about the software components, an SBOM can be generated.
Knowing what a software application or service is composed of is a good first step in ensuring software integrity, especially considering the increased use of third-party software within modern applications. When shifting left in a Software Development Life Cycle (SDLC), ensuring software source integrity should include a range of capabilities to provide the source code's security and authenticity are checked and reduce the risk of unauthorized modifications. This not only includes SCA and SBOM but also code monitoring, code tampering detection & prevention, identifying known Common Vulnerabilities and Exposures (CVEs), and embedded secrets such as passwords in the source code and other software artifacts, as some examples. As such, support for popular code source repositories integrations is also needed.
When testing the security of software applications, software Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) are commonly used but are not the only methods. SAST involves analyzing an application's source code, byte code, or binary code without executing it. It examines the code structure, logic, and patterns to identify potential security vulnerabilities, such as coding errors, insecure configurations, or unsafe coding practices. SAST allows for early detection of vulnerabilities during the development process, provides detailed vulnerability information, and can be integrated into the development environment, allowing developers to receive immediate feedback on security issues. Support for the programming and script languages used within the software should also be considered. DAST involves testing an application in a running state by interacting with its interfaces, such as web forms, APIs, or container services. By testing the application in its actual runtime environment, DAST can detect vulnerabilities dependent on specific runtime conditions, and provide a realistic assessment of an application's security posture.
Within the SDLC is a practice of software Continuous Integration/Continuous Delivery (CI/CD) that involves a set of tools to enable frequent and automated delivery of software changes to production environments. CI/CD pipeline security must also be considered in secure software development. CI/CD pipelines are subject to vulnerabilities that can enable cybercriminals to perform malicious code injection or data exfiltration during the software development lifecycle. These vulnerabilities can emerge from the insecure configuration of CI/CD tools and infrastructure, including code repositories, build servers, and artifact registries. In addition, as part of the CI/CD process, integrations with popular CI/CD tools for build automation, for example, should also be supported.
Overall, the security of the Software Supply Chain should be based on a set of prioritized risks. The ability to detect risks and vulnerabilities, prevent code tampering and leakage, ensure authentication and the principle of least privilege, identify anomalous and suspicious user activity, and governance of access and evaluation rules and APIs, as some examples, should be configurable through security policies.
In this Leadership Compass, the term “Software Supply Chain Security (SSCS)” refers to the ability to secure the software development lifecycle (SDLC) process throughout the development, testing, deployment, and maintenance phases – at every point along the way, including along the whole CI/CD pipeline. This also means having end-to-end visibility, at a granular level, at each phase of the software supply chain process.
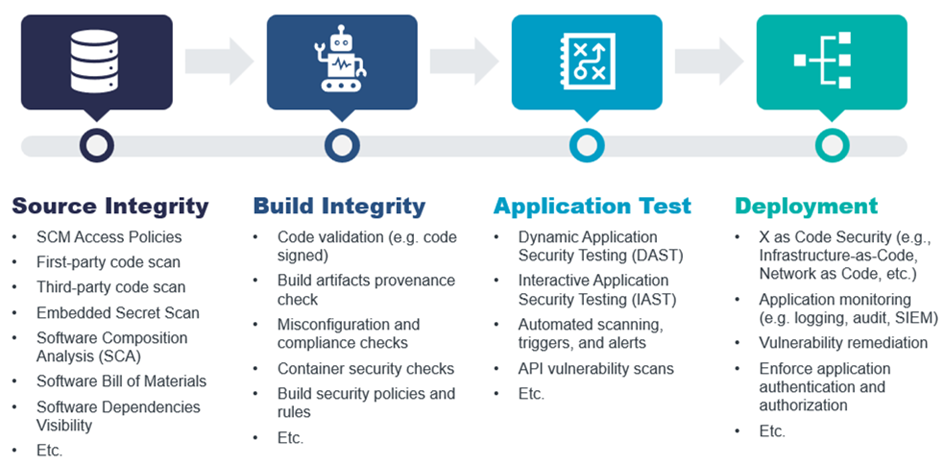
Figure 1: End-to-End Software Supply Chain Security
Highlights
- The SSCS market is still evolving to provide end-to-end SSCS capabilities.
- Solutions in today’s SSCS market tend to focus on certain portions of the software supply chain SDLC.
- Source code integrity capabilities are provided by the majority of vendors in this Leadership Compass
- Over half of the SSCS vendors provide good build integrity abilities
- Strong API or container security features are offered by half of the SSCS vendors evaluated
- Leaders in this Leadership Compass cover most of the end-to-end SSCS capabilities of the solutions evaluated
- It is expected that the SSCS market with continue to grow with solutions covering more of the entire SDLC security pipeline
- The Overall Leaders are (in alphabetical order) Aqua Security, Data Theorem, and Veracode
1.1 Market Segment
The SSCS market is still relatively new. Some products cover only point solutions along the Software Supply Chain, such as focusing on static source code analysis to discover code errors or vulnerability scans during the build and test cycles. In contrast, other products provide a more comprehensive range of capabilities to address most, if not all, of the complete end-to-end Software Supply Chain Security solution.
Integration options should include utilizing agents, APIs, SDKs, or CLIs to connect to a wide range of source management and CI/CD tools. Also, a good set of industry standards and technology protocols should also be supported. Because of the depth and breadth of the Software Supply Chain, workflows, automation, orchestration capabilities, and a level of intelligence through AI/ML or analytics should be available to minimize the complexity of the tasks involved.
SSCS solutions that cover the end-to-end SDLC pipeline are continuing to develop. However, KuppingerCole expects to see the SSCS market become more competitive and mature as the threats and attacks on the Software Supply Chain continue to grow.
1.2 Delivery Models
Delivery and deployment models should provide options for on-premises, cloud, or hybrid scenarios and provide options for containers, Kubernetes, or cloud-native environments. Managed service of the SCCS solution will also be considered. Ultimately, selecting a suitable SSCS solution delivery model will depend on the customer requirements and use cases.
1.3 Required Capabilities
This Leadership Compass analyzes the Software Supply Chain Security (SSCS) solutions ability to provide:
- Source code integrity
- Build integrity
- Vulnerability management of code, and other build and/or deployment artifacts
- Provide levels of intelligence, automation, and orchestration capabilities
- Allow for a wide range of source management and CI/CD tool integrations
- Offer visibility into the software supply chain under security control
- Support a range of industry compliance and technology standards
We expect solutions to cover several of these capabilities, at least at a good baseline level.
Inclusion Criteria
In this Leadership Compass, we are looking for comprehensive solutions that incorporate at some of the component building blocks needed to implement a full-featured Software Supply Chain Security (SSCS) which include:
- Support for several of the capabilities listed above
Exclusion Criteria
Vendors that only cover:
- Vendors without active deployments at customers (e.g., start-ups in stealth mode) will not be considered
However, there are no further exclusion criteria such as revenue or number of customers. We cover vendors from all regions, from start-ups to large companies.
Evaluation Criteria
Source Code Integrity:
- Code tampering detection and prevention (e.g., code signing)
- Software composition analysis (SCA)
- Static application security testing (SAST)
- Code monitoring, triggers, and alerts
- Finding embedded secrets in code and other artifacts
- Prevent code leakage
- Software Bill of Materials (SBOM)
- Identify proprietary code in public repositories
Build Integrity:
- Code validation before builds (e.g., check if code is signed)
- Build artifacts provenance check (e.g., source, dependencies, metadata, etc.)
- Misconfiguration and compliance checks
- Container security checks (e.g., docker image compliance, vulnerabilities)
- Security rules for confirming security build steps are executed
Vulnerability Management:
- Dynamic Application Security Testing (DAST)
- Interactive Application Security Testing (IAST)
- Automated scanning, triggers, and alerts
- API vulnerability scans
- Integration into software supply chain tools
- Ability to scan for vulnerability in a wide range of deployment environments
- Application misconfiguration scanning
- A level of intelligence (AI/ML, analytics) driven vulnerability detection
- Vulnerability remediation recommendations and guidance
- Workflows and orchestration for alerting, ticketing, remediation, etc.
Visibility and Reporting:
- Breadth of end-to-end visibility into aspects of software supply chain
- Visibility of software assets, SBOM, etc.
- Tracking of user activities and events
- Dashboard showing software supply chain statistics, trends, etc.
- Reports of SDLC metrics, compliance, auditing, vulnerability metrics, etc.
- Knowledge graph mapping of SSCS metadata and events
Other Security:
- Software supply chain policy rules and management
- Enforce authentication to supply chain tools (e.g., MFA, SSO)
- Authorization check to software supply chain tools
- API DevOps Lifecycle Management
- Integration with third-party IAM, SIEM, XDR, etc. solutions
- Support for industry compliance and technology protocol standards
Integrations with Software Supply Chain Tools:
- Source control management (e.g., git, GitHub, GitLab, TFS, etc.)
- Build automation tools (e.g., Puppet, Jenkins, Bamboo, etc.)
- CI/CD tools (e.g., CircleCI, Azure DevOps, GitHub Actions, etc.)
- ITSM solutions (e.g., ServiceNow, Zendesk, BMC Helix ITSM, etc.)
- Integrated development environment (IDE)
- ChatOps
Innovative Capabilities (Selection)
- X as Code Security (e.g., Infrastructure-as-Code, Network as Code, etc.) support
- Ability to identify proprietary code in public repositories
- Automatic vulnerability remediation
- Knowledge graph mapping of SSCS metadata and events
- Machine learning software supply chain auditing
- Software dependency graphs
- Secret scanning (e.g., finding passwords, keys, or tokens, etc. in code or other artifacts)
- API DevOps Lifecycle Management
- Container security checks
- ChatOps support
- Post deployment monitoring
The list of functionalities is not complete but intended to give an overview of our expectations regarding functionality in the Software Supply Chain Security market segment. Certain capabilities of high weightage will be rated higher than others.
Ultimately, selecting any SSCS solution on the market will depend on the organization’s particular requirements, which may depend on many other aspects, such as existing software management or other IT solutions currently being used today.
2 Leadership
Selecting a vendor of a product or service must not only be based on the information provided in a KuppingerCole Leadership Compass. The Leadership Compass provides a comparison based on standardized criteria and can help identify vendors that shall be further evaluated. However, a thorough selection includes a subsequent detailed analysis and a Proof of Concept of pilot phase, based on the specific criteria of the customer.
Based on our rating, we created the various Leadership ratings. The Overall Leadership rating provides a combined view of the ratings for
- Product Leadership
- Innovation Leadership
- Market Leadership
2.1 Overall Leadership
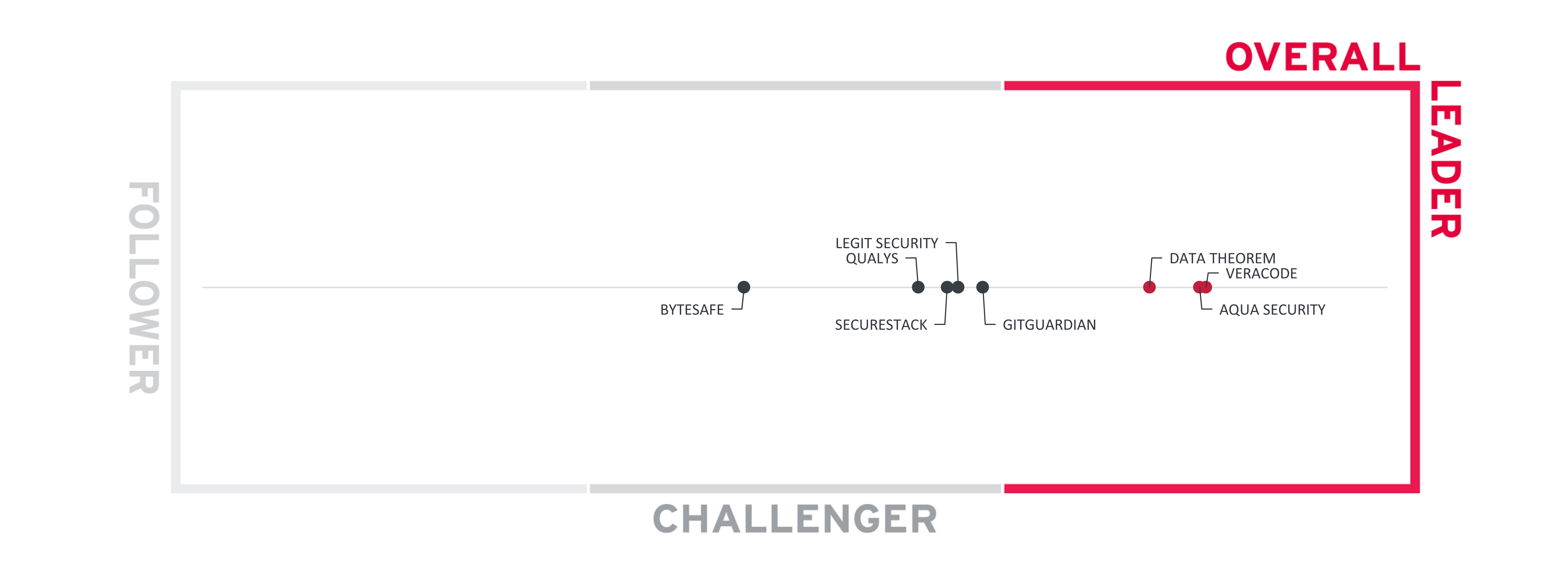
Figure 2: The Overall Leadership rating for the SSCS market segment
Overall Leaders are (in alphabetical order):
- Aqua Security
- Data Theorem
- Veracode
The Challengers in Overall Leadership are GitGuardian, Legit Security, SecureStack, Qualys, and Bytesafe.
2.2 Product Leadership
Product Leadership is the first specific category examined below. This view is mainly based on the analysis of service features and the overall capabilities of the various services.
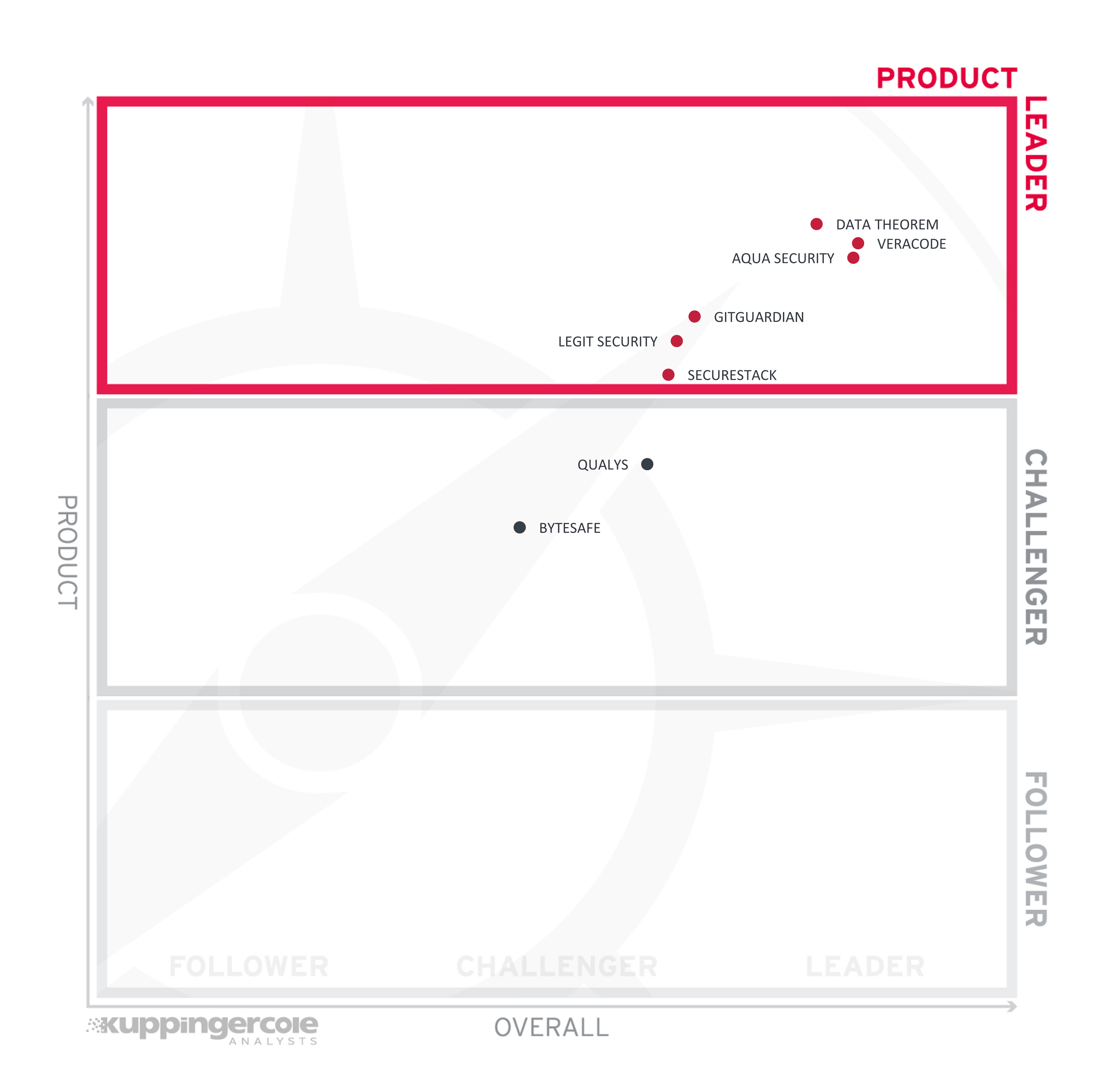
Figure 3: Product Leaders in the SSCS market segment
Product Leadership, or in this case Service Leadership, is where we examine the functional strength and completeness of services.
Product Leaders (in alphabetical order):
- Aqua Security
- Data Theorem
- GitGuardian
- Legit Security
- SecureStack
- Veracode
The Challengers in Product Leadership are Qualys and Bytesafe.
2.3 Innovation Leadership
Next, we examine innovation in the marketplace. Innovation is, from our perspective, a key capability in all IT market segments. Customers require innovation to meet evolving and even emerging business requirements. Innovation is not about delivering a constant flow of new releases. Rather, innovative companies take a customer-oriented upgrade approach, delivering customer-requested and other cutting-edge features, while maintaining compatibility with previous versions.
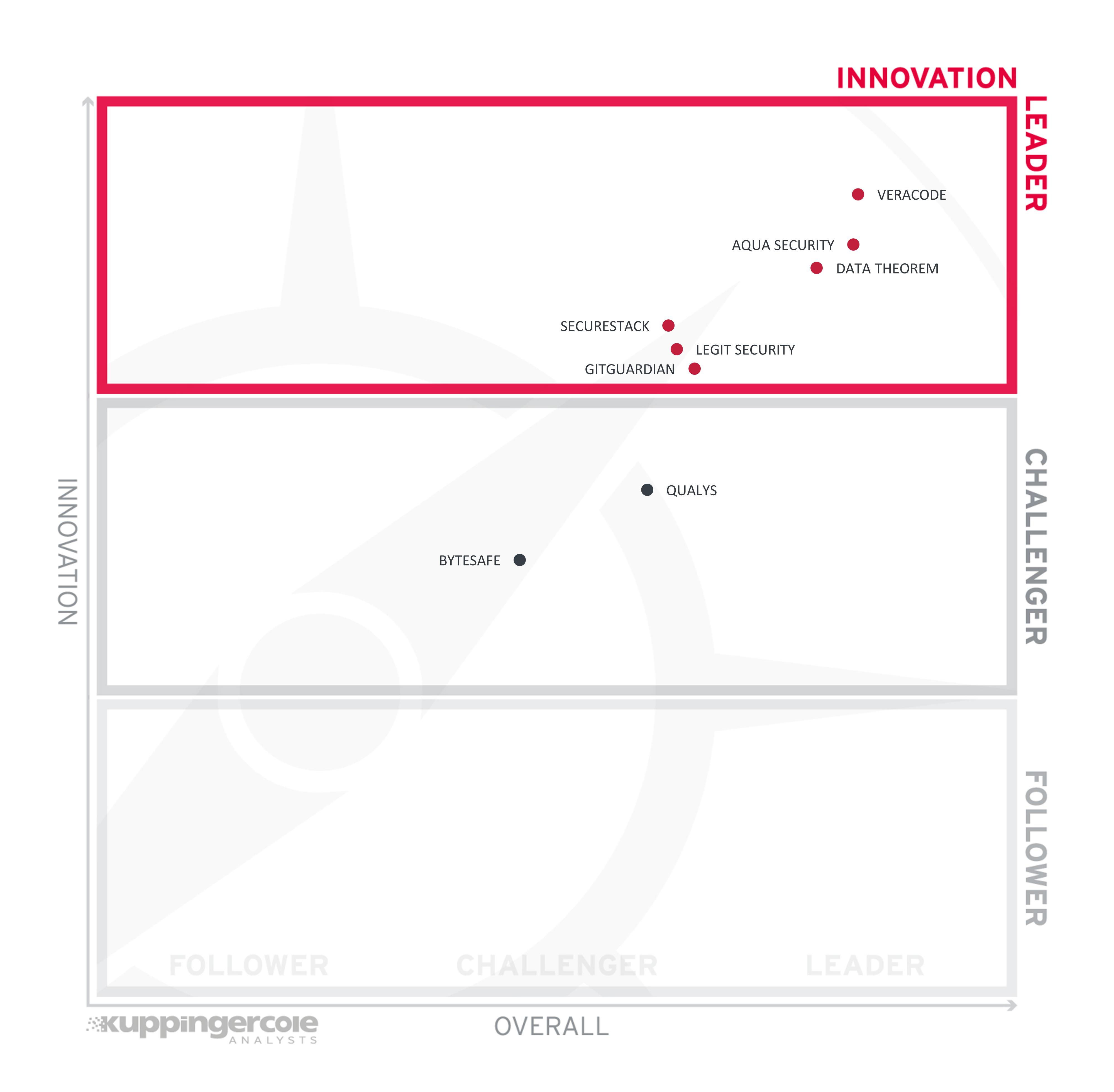
Figure 4: Innovation Leaders in the SSCS market segment
Innovation Leaders (in alphabetical order):
- Aqua Security
- Data Theorem
- GitGuardian
- Legit Security
- SecureStack
- Veracode
The Challengers in Innovation Leadership are Qualys and Bytesafe.
2.4 Market Leadership
Lastly, we analyze Market Leadership. This is an amalgamation of the number of customers, number of transactions evaluated, ratio between customers and managed identities/devices, the geographic distribution of customers, the size of deployments and services, the size and geographic distribution of the partner ecosystem, and financial health of the participating companies. Market Leadership, from our point of view, requires global reach.
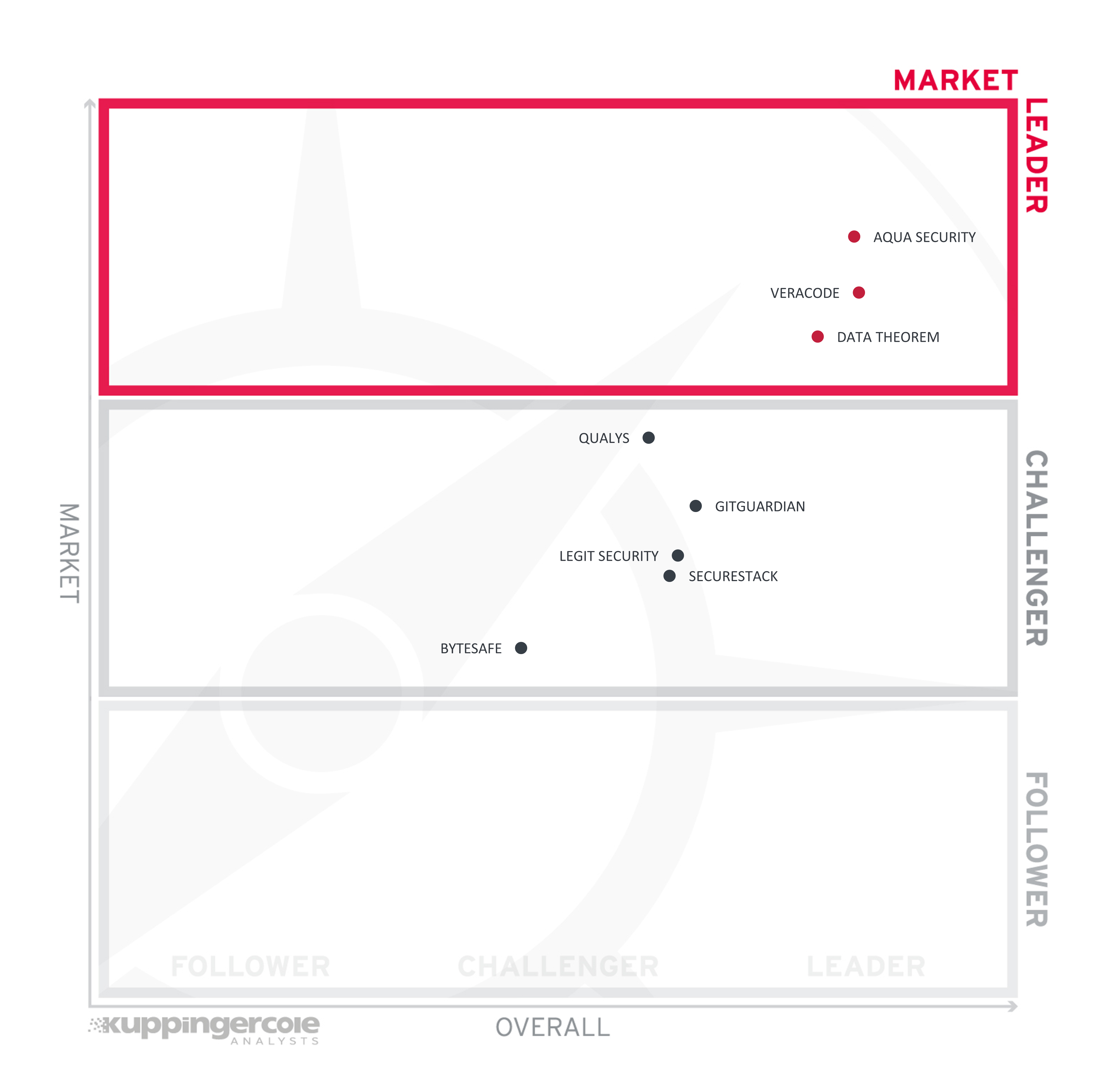
Figure 5: Market Leaders in the SSCS market segment
Market Leaders (in alphabetical order):
- Aqua Security
- Data Theorem
- Veracode
The Challengers in Market Leadership are Qualys, GitGuardian, Legit Security, SecureStack, and Bytesafe.
3 Correlated View
While the Leadership charts identify leading vendors in certain categories, many customers are looking not only for a product leader, but for a vendor that is delivering a solution that is both feature-rich and continuously improved, which would be indicated by a strong position in both the Product Leadership ranking and the Innovation Leadership ranking. Therefore, we provide the following analysis that correlates various Leadership categories and delivers an additional level of information and insight.
The first of these correlated views contrasts Product Leadership and Market Leadership.
3.1 The Market/Product Matrix
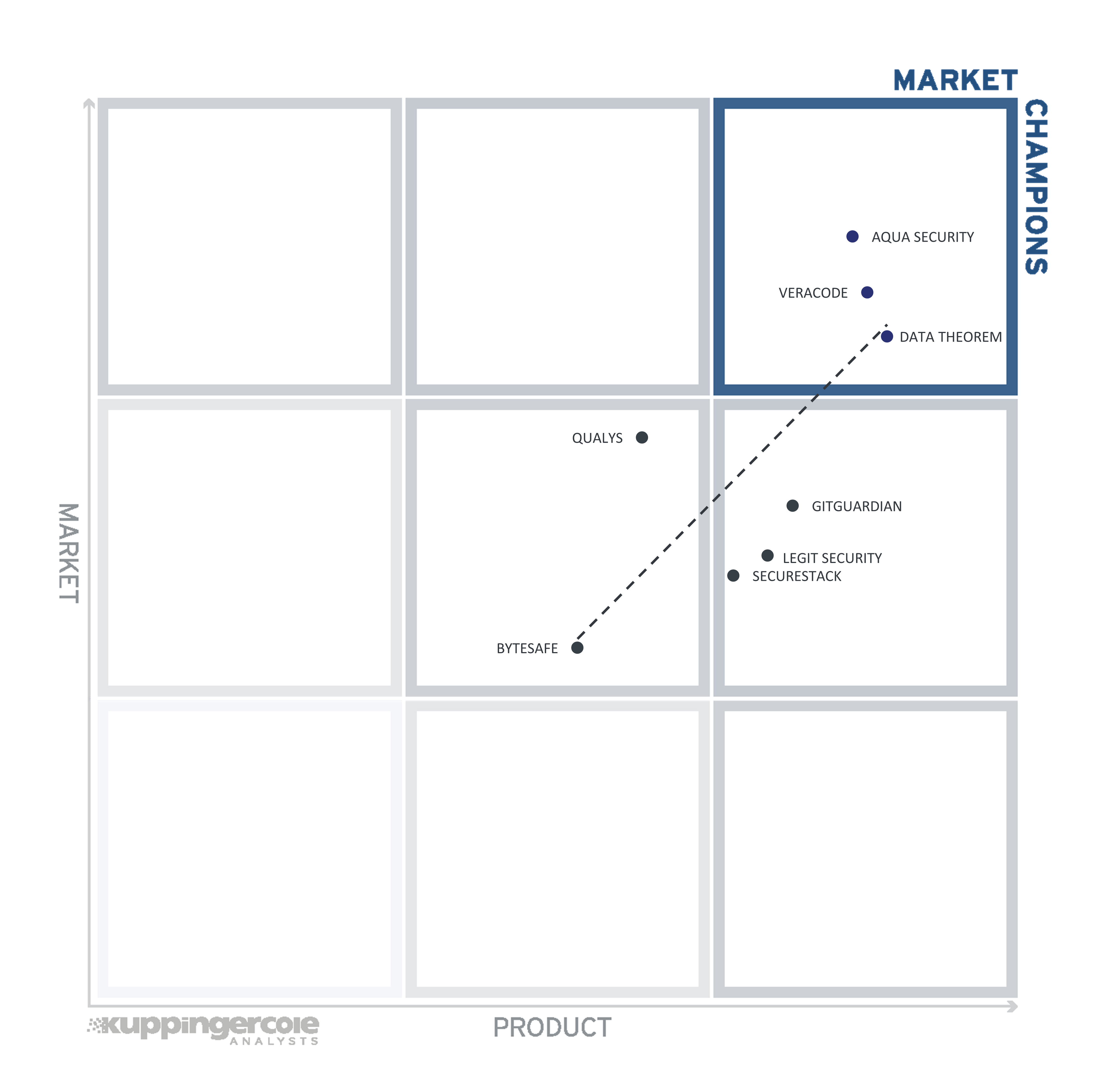
Figure 6: The Market/Product Matrix
Vendors below the line have a weaker market position than expected according to their product maturity. Vendors above the line are sort of “overperformers” when comparing Market Leadership and Product Leadership.
All the vendors below the line are underperforming in terms of market share. However, we believe that each has a chance for significant growth.
The Market Champions in Software Supply Chain Security are (in alphabetical order) Aqua Security, Data Theorem, and Veracode.
GitGuardian, Legit Security, and SecureStack are in the center right box, indicating that the strength of their solutions should garner them increasing market share in the years ahead.
Qualys and Bytesafe are found in the center of the chart, which demonstrates a correlation of service strength to market position.
3.2 The Product/Innovation Matrix
This view shows how Product Leadership and Innovation Leadership are correlated. It is not surprising that there is a pretty good correlation between the two views with a few exceptions. The distribution and correlation are tightly constrained to the line, with a significant number of established vendors plus some smaller vendors.
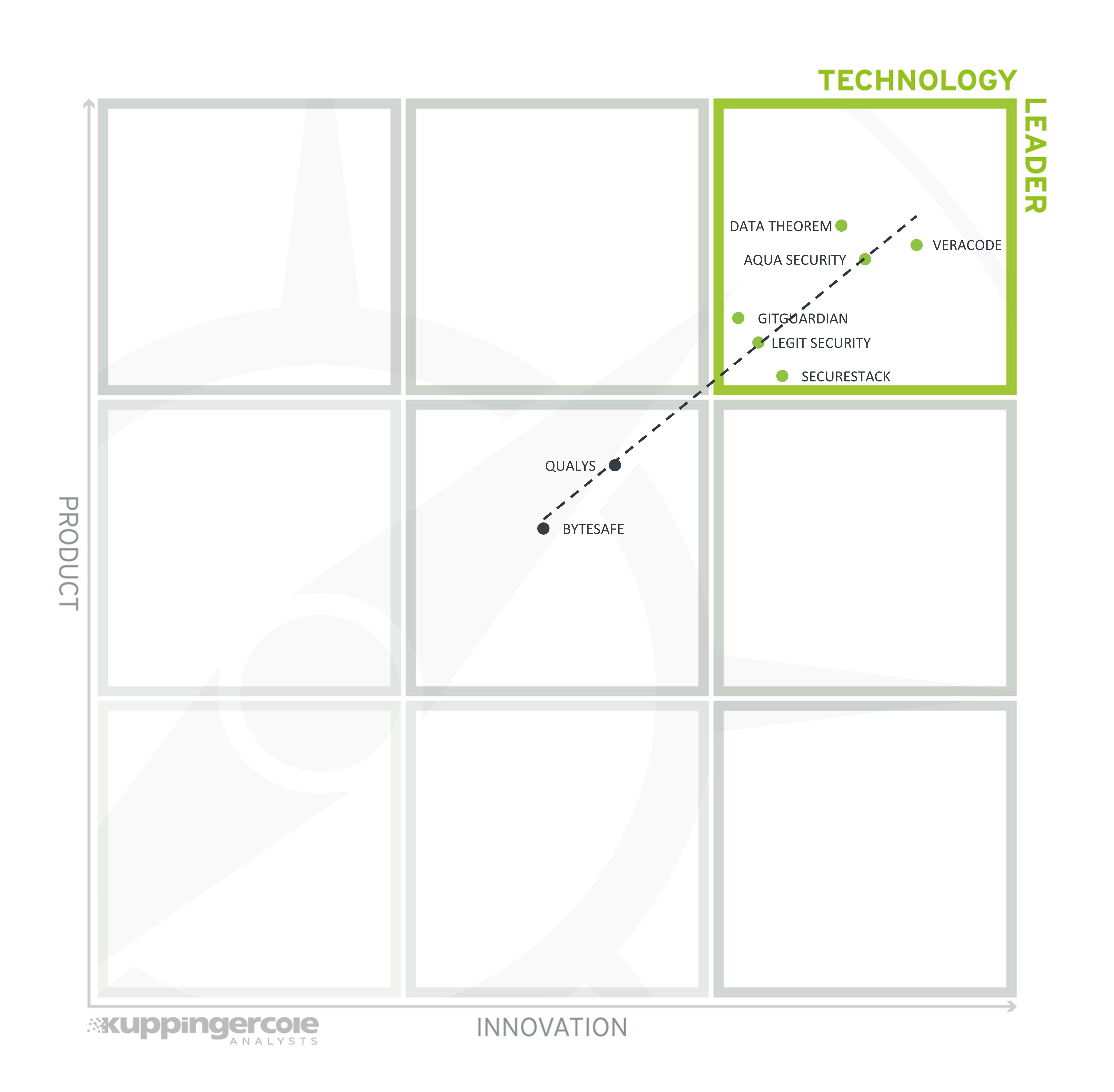
Figure 7: The Product/Innovation Matrix
Vendors below the line are more innovative, vendors above the line are, compared to the current Product Leadership positioning, less innovative.
The Technology Leaders in Software Supply Chain Security are (in alphabetical order) Aqua Security, Data Theorem, GitGuardian, Legit Security, SecureStack, and Veracode.
Qualys and Bytesafe are in the center of the chart. This shows a relationship between current product completeness and ability to incorporate innovation.
3.3 The Innovation/Market Matrix
The third matrix shows how Innovation Leadership and Market Leadership are related. Some vendors might perform well in the market without being Innovation Leaders. This might impose a risk for their future position in the market, depending on how they improve their Innovation Leadership position. On the other hand, vendors which are highly innovative have a good chance for improving their market position. However, there is always a possibility that they might also fail, especially in the case of smaller vendors.
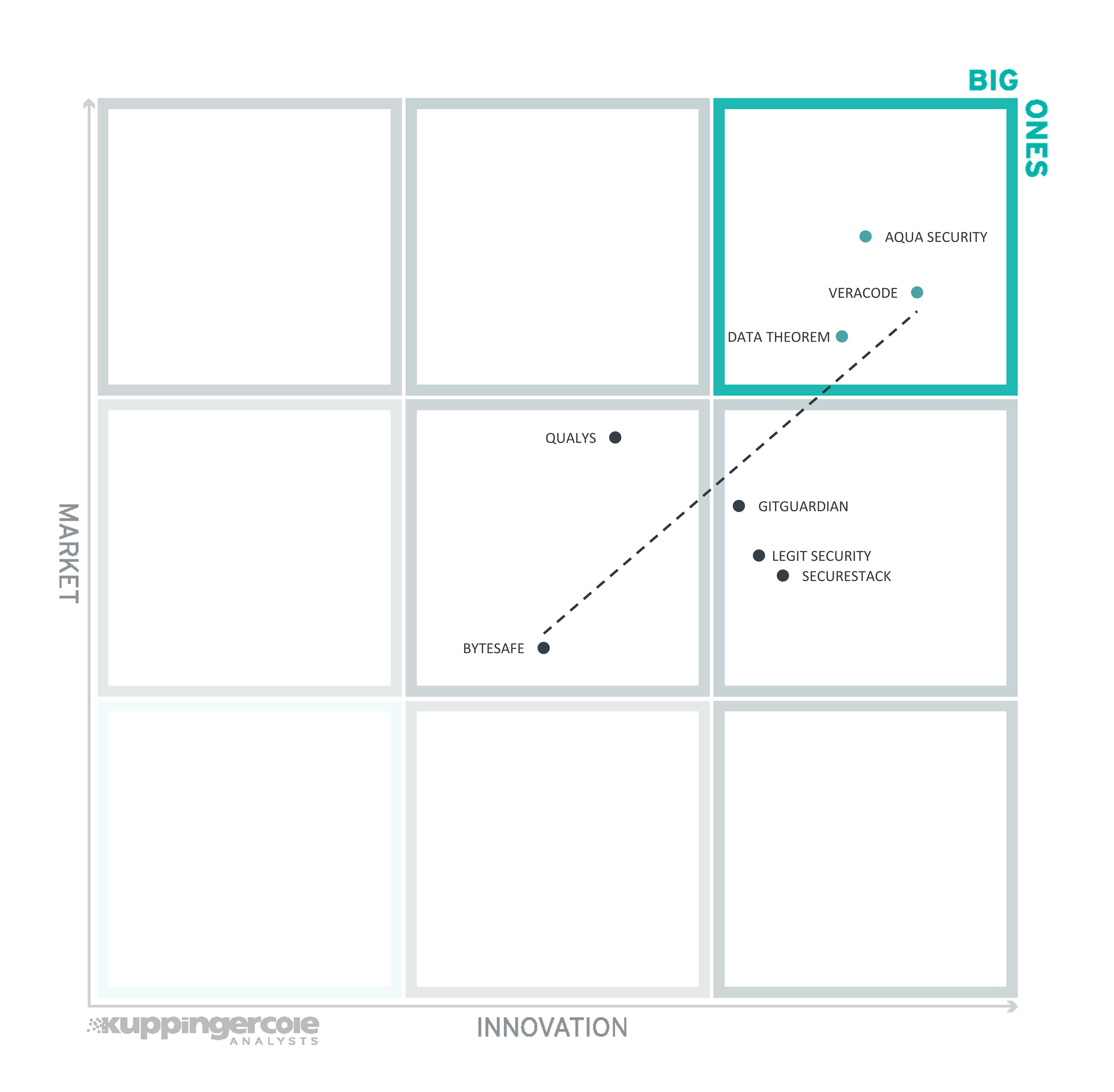
Figure 8: The Innovation/Market Matrix
Vendors above the line are performing well in the market as well as showing Innovation Leadership; while vendors below the line show an ability to innovate though having less market share, and thus the biggest potential for improving their market position.
The Big Ones in SSCS (in alphabetical order) Aqua Security, Data Theorem, and Veracode.
The center right box contains GitGuardian, Legit Security, and SecureStack. Each of these vendors has innovative SSCS solutions that have an excellent opportunity to capture additional customers.
Qualys and Bytesafe appear in the center square.
4 Products and Vendors at a Glance
This section provides an overview of the various products we have analyzed within this KuppingerCole Leadership Compass on Software Supply Chain Security (SSCS) solutions. Aside from the rating overview, we provide additional comparisons that put Product Leadership, Innovation Leadership, and Market Leadership in relation to each other. These allow identifying, for instance, highly innovative but specialized vendors or local players that provide strong product features but do not have a global presence and large customer base yet.
Based on our evaluation, a comparative overview of the ratings of all the products covered in this document is shown in Table 1. Since some vendors may have multiple products, these are listed according to the vendor’s name.
| Vendor | Security | Functionality | Deployment | Interoperability | Usability |
|---|---|---|---|---|---|
| AQUA SECURITY |  |
 |
 |
 |
 |
| BYTESAFE |  |
 |
 |
 |
 |
| DATA THEOREM |  |
 |
 |
 |
 |
| GITGUARDIAN |  |
 |
 |
 |
 |
| LEGIT SECURITY |  |
 |
 |
 |
 |
| QUALYS |  |
 |
 |
 |
 |
| SECURESTACK |  |
 |
 |
 |
 |
| VERACODE |  |
 |
 |
 |
 |
Table 1: Comparative overview of the ratings for the product capabilities
In addition, we provide in Table 2 an overview which also contains four additional ratings for the vendor, going beyond the product view provided in the previous section. While the rating for Financial Strength applies to the vendor, the other ratings apply to the product.
| Vendor | Innovativeness | Market Position | Financial Strength | Ecosystem |
|---|---|---|---|---|
| AQUA SECURITY |  |
 |
 |
 |
| BYTESAFE |  |
 |
 |
 |
| DATA THEOREM |  |
 |
 |
 |
| GITGUARDIAN |  |
 |
 |
 |
| LEGIT SECURITY |  |
 |
 |
 |
| QUALYS |  |
 |
 |
 |
| SECURESTACK |  |
 |
 |
 |
| VERACODE |  |
 |
 |
 |
Table 2: Comparative overview of the ratings for vendors
5 Product/Vendor evaluation
This section contains a quick rating for every product/service we’ve included in this KuppingerCole Leadership Compass document. For many of the products there are additional KuppingerCole Product Reports and Executive Views available, providing more detailed information.
5.1 Spider graphs
In addition to the ratings for our standard categories such as Product Leadership and Innovation Leadership, we add a spider chart for every vendor we rate, looking at specific capabilities for the market segment researched in the respective Leadership Compass. For the Leadership Compass Software Supply Chain Security (SSCS), we look at the following six categories:
- Source Integrity - Software source integrity includes a range of capabilities to ensure source code's security, and authenticity, and reduce the risk of unauthorized modifications. This includes Software Composition Analysis (SCA), Software Bill of Materials (SBOM), code monitoring, and tampering detection & prevention, as examples.
- Build Integrity - Software build integrity involves maintaining the integrity of build artifacts and ensuring the build process is secure, reliable, and trust that no unauthorized modification is allowed. Some capabilities include code validation before builds, build artifact provenance checks, misconfiguration, and compliance checks.
- Vulnerability Management – In the context of SSCS, vulnerability management refers to identifying, assessing, and mitigating security vulnerabilities within the software supply chain. This can include providing automated scanning, triggers, alerts, and capabilities such as vulnerability remediation recommendations and guidance, application misconfiguration scanning, and Dynamic Application Security Testing (DAST).
- API Security - This category looks at the solution's ability to mitigate the risks associated with APIs that are part of the software supply chain. Some example capabilities can perform API security scanning and detection of API vulnerabilities or simulate real API traffic for testing, check for OpenAPI definition compliance, detect OWASP API Security Top 10 Vulnerabilities, track API ownership, or provide dashboards that include risks and vulnerabilities metrics.
- Container Security - In the context of the SSCS, container security looks at the solution's ability to mitigate the risks associated with compromised or vulnerable containers that can introduce into the overall software ecosystem. This includes capabilities such as scanning and analyzing container images for known vulnerabilities and misconfigurations, ensuring secure practices are implemented during the image build process to help reduce security risks, container security testing, or adherence to container compliance.
- Intelligence & Automation - This category looks at the level and use of analytics and/or artificial intelligence to provide insight into different aspects of the SSCS domain as well as the ability to automate, assist or take action to remediate endpoint-related issues, as well as other capabilities.
- SSCS Visibility & Reporting - This category looks at the level and use of analytics and/or artificial intelligence to provide insight into different aspects of the SSCS domain, the ability to automate, assist or take action to remediate endpoint-related issues as well as other capabilities.
- CI/CD Tool Support - This refers to the ability to integrate and support Continuous Integration/Continuous Deployment (CI/CD) pipeline tools. Some examples include code source repositories, plugins or connectors to popular IDEs, container registries, issue-tracking systems, ITSM solutions, ChatOps, and tools that automate testing, builds, and orchestration.
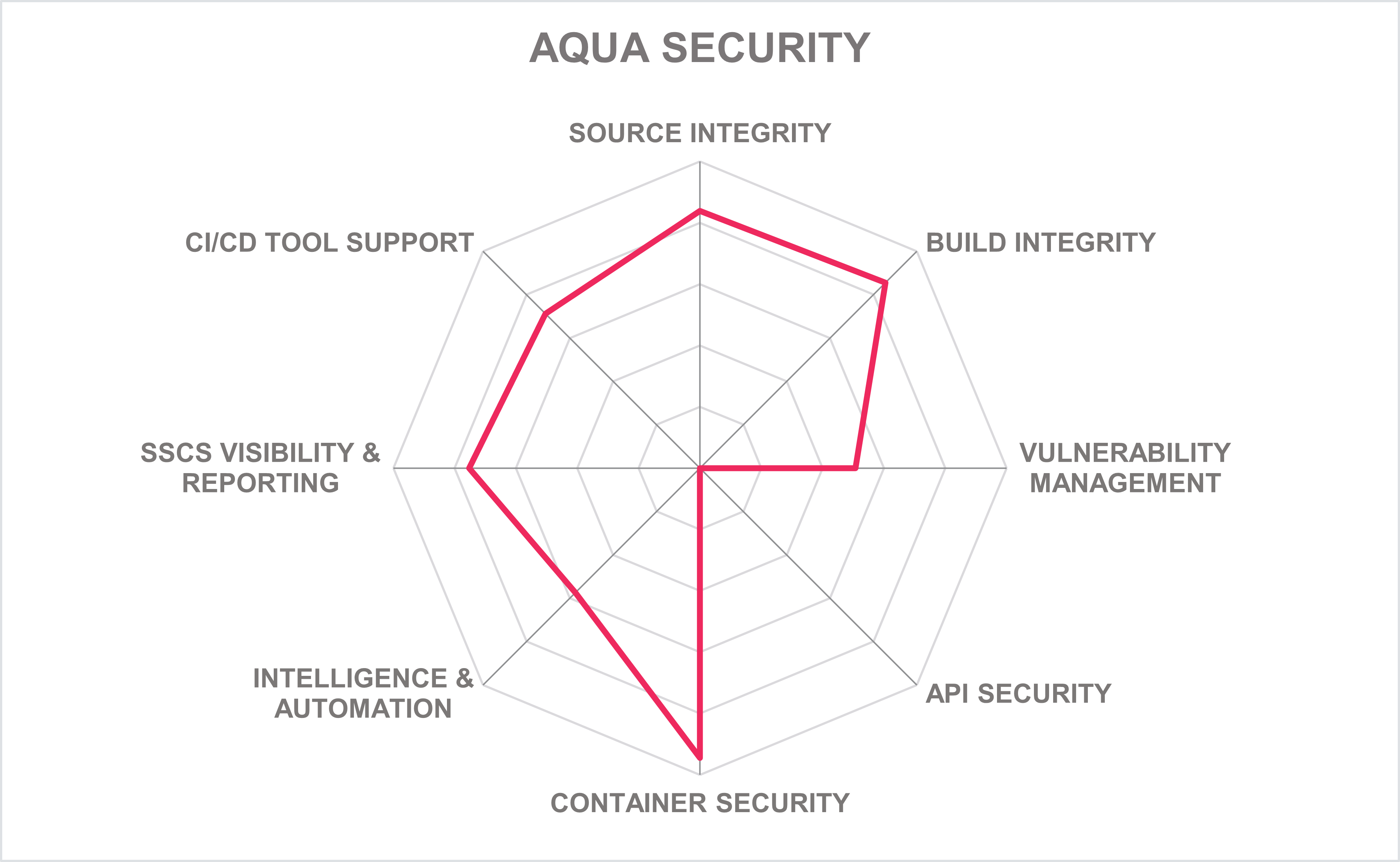
5.2 Aqua Security – Aqua SSCS
Aqua Security is a cloud-native security company with headquarters in Massachusetts, U.S., and Ramat Gan, Israel. Founded in 2015, it is one of the pioneers among dedicated cloud workload security solution providers. It also maintains a sizeable open-source ecosystem with projects like Trivy, a comprehensive security scanner. Aqua's SSCS (Software Supply Chain Security) is a module of the Aqua platform that is integrated with other parts of the platform, which can be licensed and bought separately.
Aqua Security platform provides a unified software supply chain security solution throughout the SDLC process. Aqua Security supports all major types of source code repositories. Its SCA tool can detect, report, and give remediation advice on a wide range of vulnerabilities and risks within source code packages, as well as provide open-source health markers such as maintainer data, package activity levels, and popularity. The solution also generates SBOMs in accordance with industry standards such as CycloneDX, SPDX, and NIST's SSDF. Its source code integrity scanning capabilities leverage analytics, as well as provide automation of the scanning and remediation capabilities within the development workflow. Code tampering detection and prevention capabilities are also given. Software builds integrity capabilities perform various checks that can ensure signed source code is used in the build process, detecting drifts in software artifacts configuration, and removing hard-coded secrets, for example.
The Aqua Security platform gives strong support to container security through its container image scans and its ability to provide dynamic threat analysis of images. It can scan containers running on VMs, and serverless containers such as Fargate and Azure Container Instances (ACI). Its dashboards include metrics on container-related risks, vulnerabilities, and misconfigurations. The solution can also integrate with a wide range of container registries and Kubernetes platforms. Missing are capabilities to scan, detect, and report on API vulnerabilities. However, good support is given to software supply chain visibility and reporting through its web-based administrative UI.
The Aqua Security platform is deployed primarily in cloud environments and can be delivered as SaaS, container, and to container-orchestration systems, supporting a wide range of container-based platforms. The service can be managed fully or partially by the customer on-premises or optionally fully managed by an Aqua Security partner. All of the solution's capabilities are accessible via APIs such as REST, JSON-RPC, Webhooks, LDAP, and AWS SQS. Although SDKs are not provided, all the solution's scanning capabilities are available via CLI. Good support is given to out-of-the-box integrations with CI/CD systems.
Aqua Security has a good market presence in the North American region, with growth in the EMEA and APAC regions with good customer growth with medium to enterprise organizations. Overall, Aqua Security provides a strong cloud-native platform with its SSCS module's source code and build integrity capabilities, with particular strength in container security features. Aqua Security should be on the shortlist for organizations considering deploying an SSCS solution.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 3: Aqua Security’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
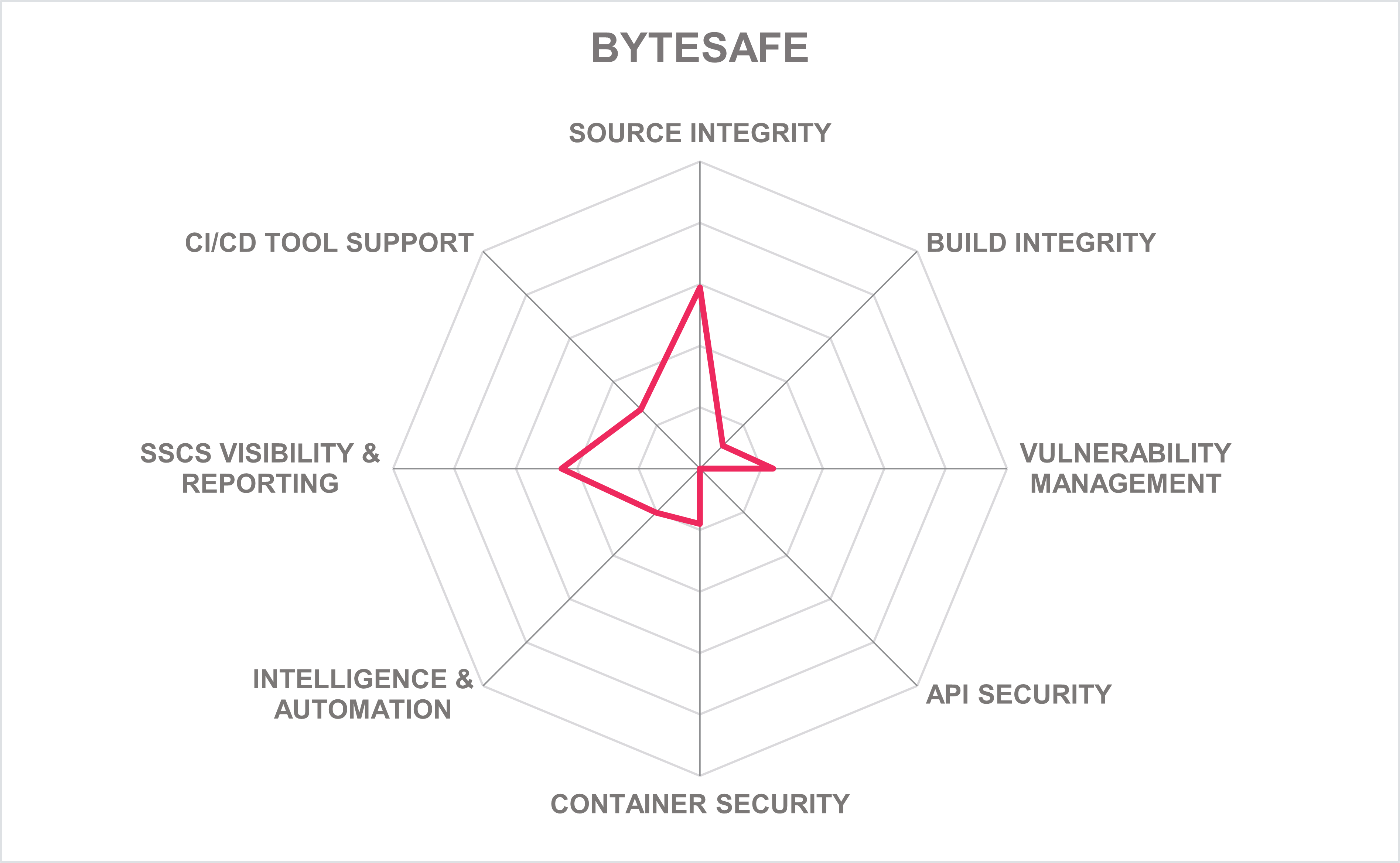
5.3 Bytesafe – Bytesafe
Bytesafe is based in Stockholm, Sweden. The Bytesafe platform provides four main capabilities. Bytesafe includes a Dependency Firewall that blocks open-source risk and dependency threats and a Package Management for source code package security. Its SBOM Observer provides Software Composition Analysis (SCA) for SBOM management that can identify open-source risk in applications and License Compliance that provides a license inventory and continuous compliance capabilities.
The Bytesafe platform focuses on protecting the SDLC from malignant and unintended exposure vulnerabilities and malware. The Bytesafe platform can connect to primarily Git-based code source code repositories, in which its Software Composition Analysis (SCA) can be used to analyze the repository to detect components, used dependencies, and open-source threats. Its SBOM generation covers a wide range of programming languages, and container/OSes. Build integrity security controls to build platforms are limited to blocking access to components with known vulnerabilities or non-compliant components with a customized policy. Bytesafe uses industry standards such as SPDX and CycloneDX in SBOM formats, SLSA framework to establish trust in package provenance, and the in-toto attestation framework.
The platform offers a range of popular CI/CD tool integrations out-of-the-box. Integration with the CI/CD tools are accomplished via APIs. The Bytesafe platform also provides a web-based administrative UI that gives a consolidated view of SCA and SBOM detail, source code vulnerabilities, and remediation information. The UI also includes an innovative graph-based dependency graph that can, for example, be used to show a given application with a policy violation (e.g., vulnerability in a software package), with the downstream apps or environments that use the vulnerable application, and the software team responsible for the application, in which that team would be notified. The solution provides dashboards and reports that include risks and vulnerabilities metrics regarding applications, and open-source artifacts, in addition to operations-related reports OOTB, such as security, SLA metrics, and software license compliance.
The Bytesafe platform can be deployed as SaaS on-premises or in the public cloud. Bytesafe can also be fully managed, with unlimited hosting of public and private packages and package registries, no bandwidth usage fees, updates of its vulnerability database, and product support. Most of the solution’s functionality is available via REST APIs, with some of its capabilities available via CLI. No SDK support is given, although software documentation is available online along with a Bytesafe Community Edition available on its Git repository.
With a customer base primarily focused in the EMEA region followed by a growing North American presence and serving SMBs to mid-market organizations, the Bytesafe platform provides capabilities towards the software integrity side of the software supply chain spectrum, which may be of interest to organizations needing that emphasis of SSCS capabilities.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 4: Bytesafe’s rating
| Strengths |
|
| Challenges |
|
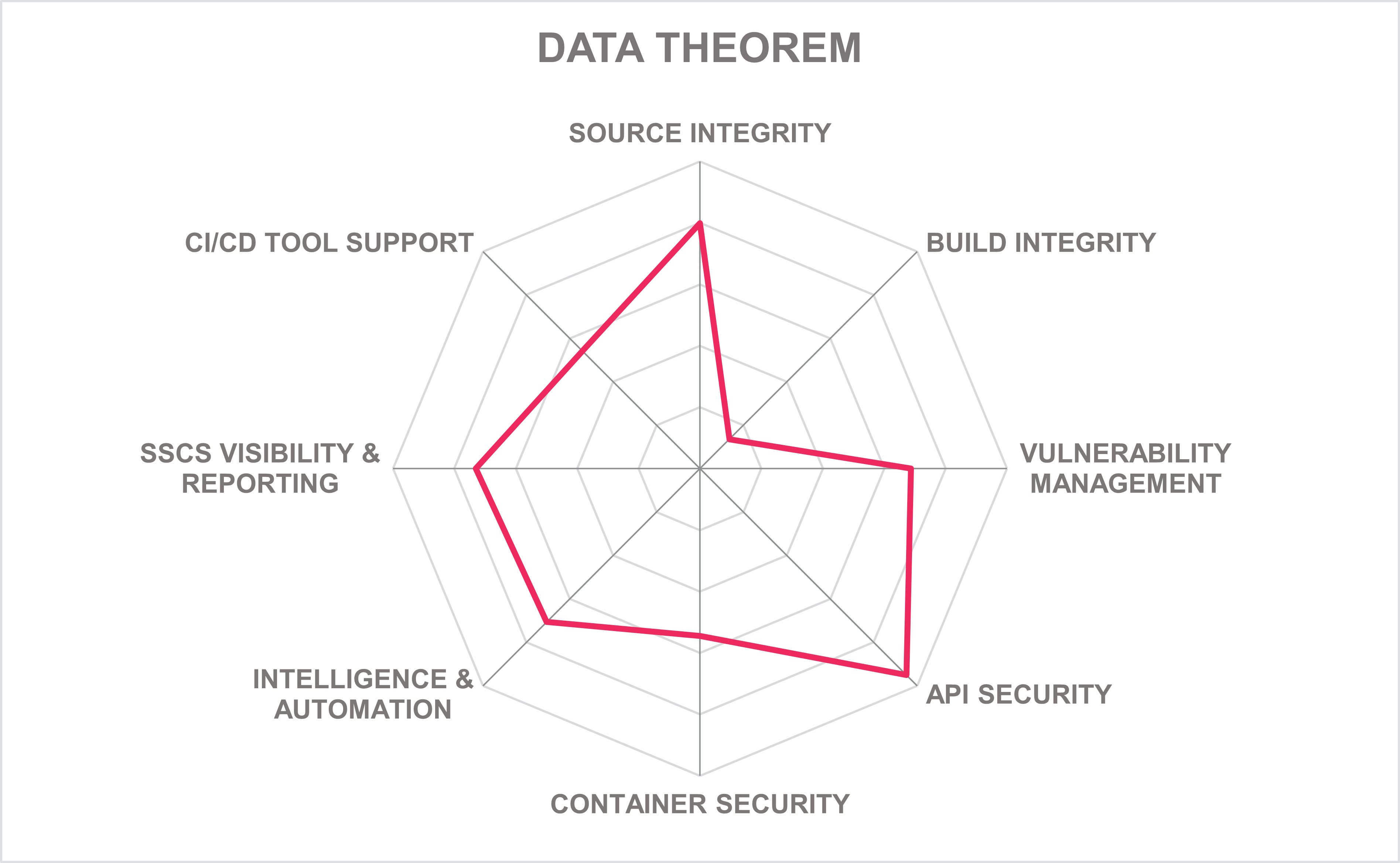
5.4 Data Theorem – Supply Chain Secure
Data Theorem is a privately owned company with offices in Palo Alto, CA, and Paris, France. Its Supply Chain Secure platform solution offers a stack analysis of applications that utilize the same underlying Analyzer Engine within a single product.
Data Theorem gives good support to source code integrity. Support is given for Azure DevOps, BitBucket, Git, Github, and GitLab code source repositories. Software Composition Analysis (SCA) is available, including black box SCA analysis of mobile app binaries, JS-based web apps, and SAST-based SCA. SBOM support includes SBOM ingestion, generation, validation, and trigger alerts on SBOM drift, with an ability to identify outdated and abandoned library features as well as support for CycloneDX and Software Package Data Exchange (SPDX) formats. The solution can also perform secret scanning, such as finding passwords, keys, or tokens in code artifacts. Missing is the ability to ensure build integrity. However, Data Theorem provides the ability to scan Terraform (IaC) code related to security issues. It can detect when hard-coded secrets are removed from pre-prod app binaries after a build but before deployment.
For SDLC vulnerability management, the solution supports a range of programming and script languages, such as Kotlin, Java, JavaScript, Objective C, Python, Swift, and TypeScript, using various static source code analysis techniques. The solution also provides plugins for popular IDEs, such as Android Studio, IntelliJ, pyCharm, Visual Studio, Visual Studio Code, and Xcode. The solution provides over 1,000 static rules within its source code SAST and mobile app binary SAST. Checks for IaC misconfigurations are available for AWS CloudFormation, Terraform, and Kubernetes. Dynamic Application Security Testing (DAST) is fully automated for APIs, mobile, web, and cloud applications. A wide range of CI/CD tool integrations are available OOTB, as well as popular container registries. The solution can scan and detect API vulnerabilities and then provide explanations of findings, including sample requests and responses, and recommendations and examples on how to remediate the issues.
The Supply Chain Secure solution can be delivered and deployed in a wide range of environments such as on-premises, cloud, or hybrid. The administrative portal UI is SaaS-based and is hosted in the public cloud. An optional container-based offering is available that can be deployed in a customer's cloud environments, as well as any environment that supports Docker, Red Hat, and Kubernetes container platforms. IaaS options included AWS, GCP, and Azure, and a fully or partially managed offering is also available. Almost all of the solution's functionality is accessible via REST APIs and Webhooks, although access via a CLI is unavailable. Support is given to SDKs covering a wide range of popular programming languages. Data Theorem has been independently certified to support compliance with ISO/IEC 15408 (Common Criteria) and ISO/IEC 27001.
Data Theorem has a strong presence in North America with footprints in both the EMEA and APAC regions. Data Theorem has good customer growth with medium to enterprise organizations. Its customers range from small to enterprise-level companies, emphasizing large organizations. Data Theorem also offers a strong partner ecosystem. Apart from providing stronger support for software build integrity, Data Theorem gives full spectrum SSCS support for the SDLC and should be on the shortlist for organizations evaluating an SSCS solution.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 5: Data Theorem’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
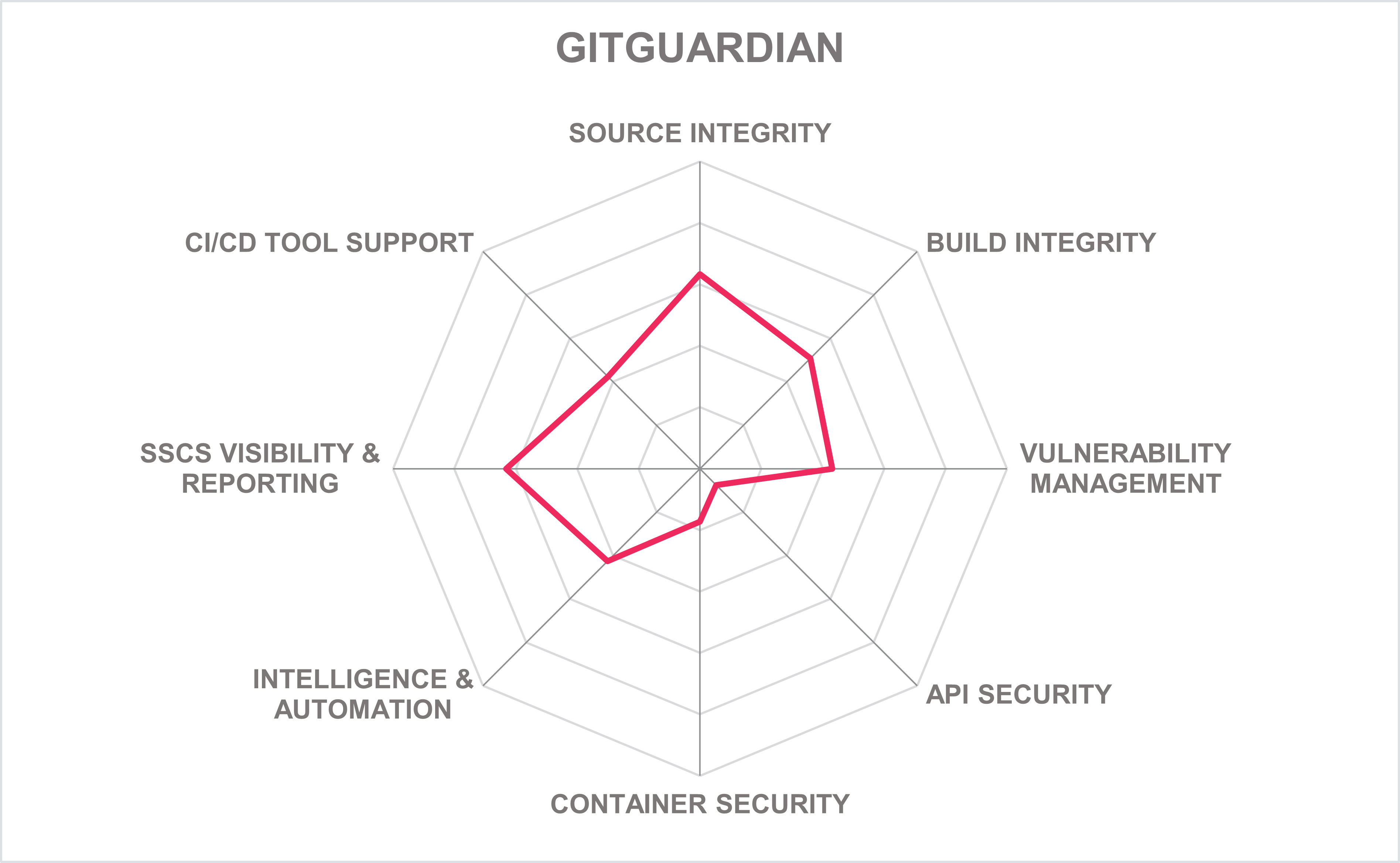
5.5 GitGuardian – GitGuardian Platform
GitGuardian is a private company founded in 2017 with offices in Paris, Ile-de-France, France, and Cambridge, MA, USA. Its GitGuardian Internal Monitoring solution is a single code security platform that allows organizations to detect and fix vulnerabilities in source code, containers, and infrastructure during the software development lifecycle. The platform includes Secrets Detection, Honeytokens, Infra as Code Security, and GitGuardian CLI capabilities.
Support for source code repositories includes Azure DevOps, BitBucket, Git, GitHub, and GitLab. An SCA tool is on the GitGuardian near-term roadmap. The solution's SBOM supports the CycloneDX and SPDX formats also on their near-term roadmap. The solution can perform secret scanning, such as finding passwords, API keys, database connection strings, private keys, and certificates, as well as detect leaked secrets and internal code that can be considered intellectual property on public GitHub with the GitGuardian Public Monitoring product. Its Honeytoken capability is an SDLC intrusion detection technology that also watermarks private code to detect code leakage when published publicly. For container security checks, the solution can scan for hardcoded secrets within Docker images. Build automation tool integrations support CircleCI, Travis CI, Jenkins, GitHub Actions, GitLab CI, and Azure DevOps. The solution does not provide plugins or connectors OOTB for popular IDEs. However, the GitGuardian CLI tool ggshield can be used in IDE integrated terminal console to view secrets or IaC scanning results directly in the IDE.
GitGuardian provides secrets detection for a wide range of programming and script languages. Infrastructure-as-Code (IaC) misconfigurations can also be scanned for AWS CloudFormation, Terraform, and YAML configuration files for Docker/Kubernetes. GitGuardian automates the remediation process, including validity and presence checks, severity assignments, and incident closing. It also integrates with ticketing and messaging systems like Jira, Splunk, PagerDuty, ServiceNow, and SumoLogic to support teams with their incident remediation workflows. Users of GitGuardian view scan details via its web UI, IDE terminal console, ChatOps tools such as Microsoft Teams, Slack, and Splunk On-Call, and CSV exports. Its web UI dashboards include risks and vulnerabilities metrics regarding applications, source code, IaC, and open-source artifacts.
GitGuardian is a SaaS platform hosted in the cloud but can also be deployed on-premises. GitGuardian uses Replicated to deliver its application to self-hosted environments with an option to install it in Embedded Kubernetes Clusters or Existing Kubernetes Clusters (using KOTS or Helm charts). The solution can also be delivered as a container that supports container-orchestration systems. Container orchestration system support is limited to Kubernetes. GitGuardian can also be installed as a plugin for GitHub through the GitHub Marketplace. Nearly all of the solution's core capabilities can be accessed via a REST API and Webhooks. GitGuardian provides a separate complementary CLI tool called ggshield that can scan for secrets and IaC security issues. The CLI application can detect 350+ types of secrets, as well as other potential security vulnerabilities or policy breaks affecting a codebase. ggshield is open-source and hosted on GitHub. An SDK is also available for the Python programming language.
GitGuardian customer base is primarily located in North America, with a growing presence in the EMEA, APAC, and Latin America that serves SMB to enterprise customers and a good global partner ecosystem. GitGuardian provides good core SSCS capabilities with several improvements on its near-term roadmap, making GitGuardian a consideration when evaluating SSCS solutions.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 6: GitGuardian’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
5.6 Legit Security – Legit Security Platform
Legit Security is headquartered in Palo Alto, California, USA. Its Legit Security Platform provides SBOM compliance, real-time SDLC auto-discovery & analysis, an application security control plane, and Code-To-Cloud traceability & security features.
For source integrity, Legit Security provides support for source code repositories, including Azure DevOps, BitBucket, Git, Github, and GitLab. Support is also given for the Gerrit code review tool. Its SCA tool can discover, detect, and report on source libraries, dependencies, vulnerabilities, licenses, and license conflicts, for example. The solution can also generate an SBOM in CycloneDX format, merge multiple sources of SBOMs, and translate between different SBOM formats. However, the ability to detect SBOM drift is on its roadmap. SBOM information can be extended to include context and provide links to the source repositories involved in building the source artifact. Legit Security automatically generates a real-time graphic model of the SDLC pipeline, infrastructure, security controls, and dependencies, as well as provides a graph database that can be queried against the SDLC model to search for threats, vulnerabilities, and other issues. Code tampering detection and prevention capabilities are given. The solution can also perform secret scanning, such as finding passwords, keys, or tokens in code artifacts, and in binaries, build logs, issues, documentation, and other development assets. Anomalous behavior within the SDLC systems can be detected and provide alerts.
For build integrity, the solution can perform various checks before a software build, such as ensuring that signed source code is used in the build process, detecting drifts in software artifacts configuration, and that hard-coded secrets have been removed. The solution can also perform container security checks for image compliance and vulnerabilities. An API vulnerability scanning capability is also available. Support for build automation tools includes CircleCi, Travis CI, Jenkins, Github Actions, GitLab CI, and Azure DevOps. Although the Legit Security platform provides SAST capabilities using semgrep. Legit Security supports scanning of Apex, C++, C#, Go, Kotlin, Java, JavaScript, PHP, Python, Ruby, Scala, Swift, and TypeScript programming and script languages. Also, checks for IaC misconfigurations can be scanned for the Ansible, AWS CloudFormation, and Azure Resource Manager platforms. OOTB plugins are available for Sublime Text and Visual Studio Code IDEs. Other IDEs are supported with Legit Security’s Command Line Interface offering for developer IDEs and endpoints.
The Legit Security solution is Kubernetes-based and can be deployed in all cloud environments; and can be delivered as a collection of Helm Charts or installed by Legit Security on a "bare metal" server. Docker containers are supported, which can be placed in front of the container-orchestration systems infrastructure. Legit can integrate in any on-premises environment whether it has a container platform or just a server. The solution is also offered as a fully managed service (SaaS) by the vendor and fully or partially managed on-premises. In the case of a hybrid deployment, a broker is deployed on-premises to provide a secure connection between the SaaS environment and the on-premises network. Nearly all of the solution's capabilities are accessible via a REST API, Webhooks, and GraphQL. Legit Security also gives CLI functionality for implementing security checks in the developer environment as well as for custom CI systems. However, SDKs are not available. Its product supports a number of compliance frameworks such as ISO 27001, SSDF, FedRAMP, SLSA, NIST SP 800-190 and SOC2.
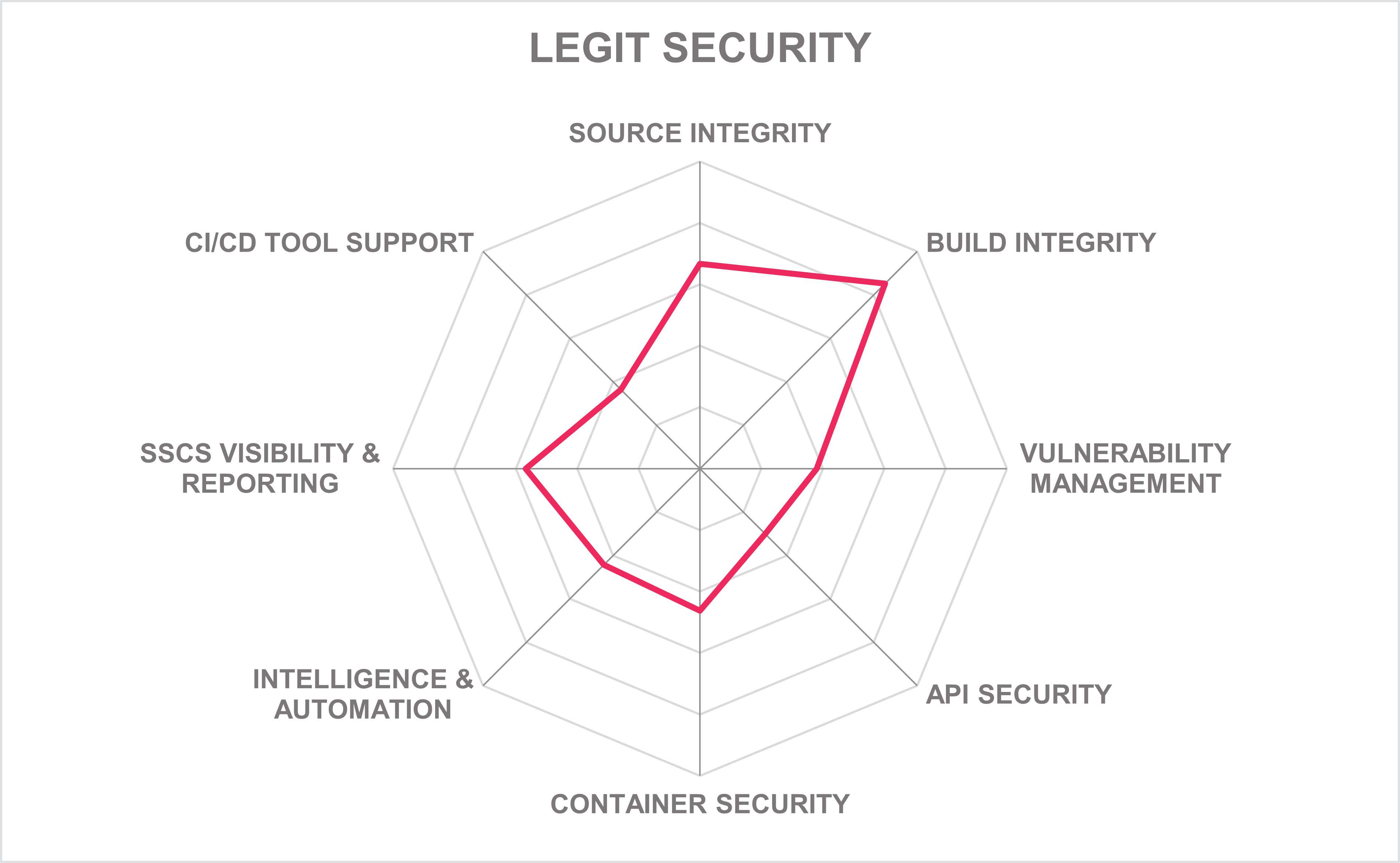
Legit Security was the youngest vendor evaluated in this Leadership Compass, being founded in 2020, although in that time it has grown an impressive list of Fortune 500 enterprise customers. Legit Security offers SSCS core capabilities to its customer base in North America and a growing presence in the EMEA and APAC regions for mid-market to enterprise organizations. In the short time the Legit Security platform has been in the SSCS market, it has provided a good partner ecosystem within North America, and KuppingerCole anticipates a stronger market presence and growth in capabilities in the future. Legit Security should be considered when evaluating SSCS solutions.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 7: Legit Security’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
5.7 Qualys – Qualys Suite
Qualys, Inc. is a cloud security and compliance solutions vendor founded in 1999 and headquartered in Foster City, California. It’s one of the veteran players in the vulnerability management market, the company was also the first to offer vulnerability detection using a SaaS model. In today's Software Supply Chain Security market, Qualys offers several solutions within their suite of products, including Qualys VMDR, Qualys Container Security, and Qualys WAS, focusing on application, container, and Infrastructure-as-Code (IaC) vulnerability testing.
Support for source integrity includes Software Composition Analysis (SCA) for containers and host security, which can discover, detect, and report software component vulnerabilities and their associated CVEs, as well as software libraries and their dependencies. Its SCA can make recommendations for the remediation of issues found during its scan. On its short-term roadmap is the solution's ability to perform security scans of container images for secrets. The solution's ability to generate a Software Bill of Materials (SBOM) is not given. For build integrity capabilities, Qualys Container Security can perform container security checks. Also, it can detect drifts in IaC software artifact configurations. Support for building automation tools is not provided.
Qualys WAS provides an industry-leading DAST tool that provides an automated vulnerability scanner. Also available are external cloud-based scanners and a virtual scanner appliance for deployment inside networks available with the Qualys VMDR. The Qualys WAS is capable of testing web applications, including single-page applications (SPA) and APIs used by mobile applications. WAS can test SOAP and REST API protocols, and the ability to detect OWASP API Security Top 10 Vulnerabilities is currently on the roadmap. For password-protected areas, WAS supports complex, form-based, and server authentication. The DAST tool allows CI/CD integrations to launch scans automatically as part of post-build actions. Alerts regarding threat, impact, and remediation information can be sent via email and APIs that monitor scan status and respond to events. Checks are available for container-related vulnerabilities such as Dockerfile commands, Kubernetes workloads, and CIS Docker and CIS K8s benchmarks. Overall, Qualys WAS can detect 750+ vulnerabilities out-of-the-box. The Qualys VMDR solution can provide vulnerability analytics.
The Qualys products can be deployed on-premises, in the cloud, and supports hybrid models. The solutions can be delivered as SaaS, containers, container-orchestration systems, software deployed to servers, as a plugin to an application, and as a managed service. Qualys supports Docker, Red Hat, Rancher Labs, Pivotal, SUSE, and Platform9 platforms when using the container-based delivery model. Delivery models are also supported for all major IaaS, such as AWS, GCP, and Azure when deploying to their Kubernetes services. Services can also be managed fully or partially by the vendor, partners, or the customer on or off premises. Access to the solution's functionality is available via SOAP and REST APIs. The Qualys CLI tool, QScanner, is on its short-term roadmap. However, SDKs are not available. Its products are independently certified to support compliance and standards such as the FIPS 197 Advance Encryption Standard, FIPS 140-2 - Cryptographic module standards, NIST 800-57 Key Management, PCI-DSS v 3.2, HIPAA/HITRUST, ISO/IEC 27001, and SOC 2 Type 2.
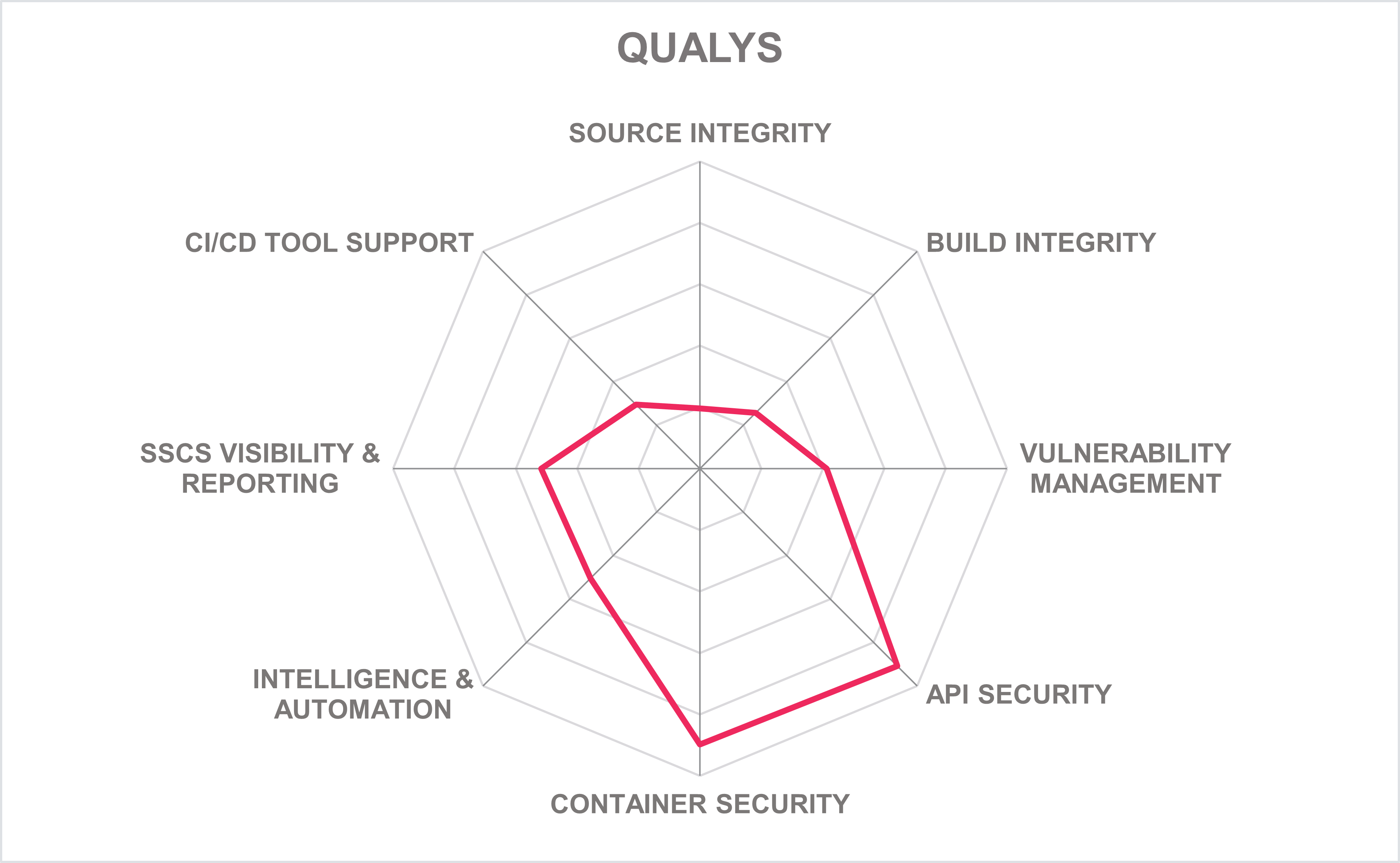
Qualys is a well-established company with customers primarily in North America, a presence in EMEA, and growth in the APAC region serving medium to enterprise organizations. Given Qualys’s strong focus on API and Container security within the SSCS SDLC process, it should interest organizations requiring those capabilities.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 8: Qualys’s rating
| Strengths |
|
| Challenges |
|
5.8 SecureStack – SecureStack DevSecOps Platform
Founded in 2018 and headquartered in Gold Coast, Queensland, Australia, SecureStack offers its SecureStack DevSecOps Platform that provides Source Code Integrity, Build Integrity, Application Vulnerability Testing, and Software Supply Chain Risk Visibility and Reporting capabilities.
In the area of source integrity, SecureStack supports a range of source code repositories such as Azure DevOps, BitBucket, Git, Gitea, Github, and GitLab. An SCA tool is provided that can discover, detect, and report on a wide range of software components and libraries, their locations and dependencies, and vulnerabilities, as well as license conflicts. The SCA tool can prioritize, and report issues found by severity and make recommendations for remediation of issues when discovered. The platform's SBOM capability is comprehensive and can collate the source code, cloud stack, and APIs a software application uses. The SBOM can also support the Common Package Enumeration (CPE), CycloneDX, and Package URLs (PURL) formats, merge multiple sources of SBOM documents, and detect and alert SBOM drift. The ability to detect and prevent code tampering is provided, as well as perform secret scanning that looks for finding passwords, keys, tokens, etc., in code or other artifacts.
For build integrity capabilities, SecureStack's platform can perform various checks before software builds, such as ensuring signed source code is used in the build process, detecting drifts in software artifacts configuration, and removing hard-coded secrets, as examples. Other build integrity features include detecting compromised build dependency, offering security controls for build platforms, providing security rules to confirm security build steps are executed, and sending alerts when build issues arise. The solution gives build automation support for a wide range of tools such as CircleCi, Travis CI, Jenkins, Github Actions, GitLab CI, Azure DevOps, AWS CodeBuild, CodeDeploy, Buddy Works, Build Kite, and Octopus Deploy.
SecureStack provides a DAST tool with an automated vulnerability scanner that can test web applications, single-page applications (SPA), mobile applications, and APIs. The DAST tool can detect 150+ vulnerabilities out-of-the-box. Its API security features include checks for OpenAPI definition compliance, detection of OWASP API Security Top 10 Vulnerabilities, and providing actionable information for API vulnerability remediation once found. SecureStack provides visibility of SSCS details through a web UI, ChatOps tools, and the CLI console. Details provided include results from SCA, SBOM, vulnerabilities, misconfigurations, cloud security posture management, and reported secrets & sensitive data. The SSCS solution also provides dashboards that include risks and vulnerabilities metrics.
The SecureStack DevSecOps Platform can be deployed on-premises, in the cloud, or as a hybrid model. Supported delivery models include SaaS, container-based, and software deployed to a server. A wide range of container-based platforms are supported for container delivery models, such as Docker, Red Hat, Rancher Labs, Pivotal, Mesosphere, SUSE, Platform9, and rkt (a.k.a Rocket). Delivery to the AWS IaaS platform is also supported. A managed service is offered as well. Less than half of the solution's capabilities are exposed via REST and GraphQL APIs, although almost all the functionalities can be accessed via CLI. However, SDKs are not available.
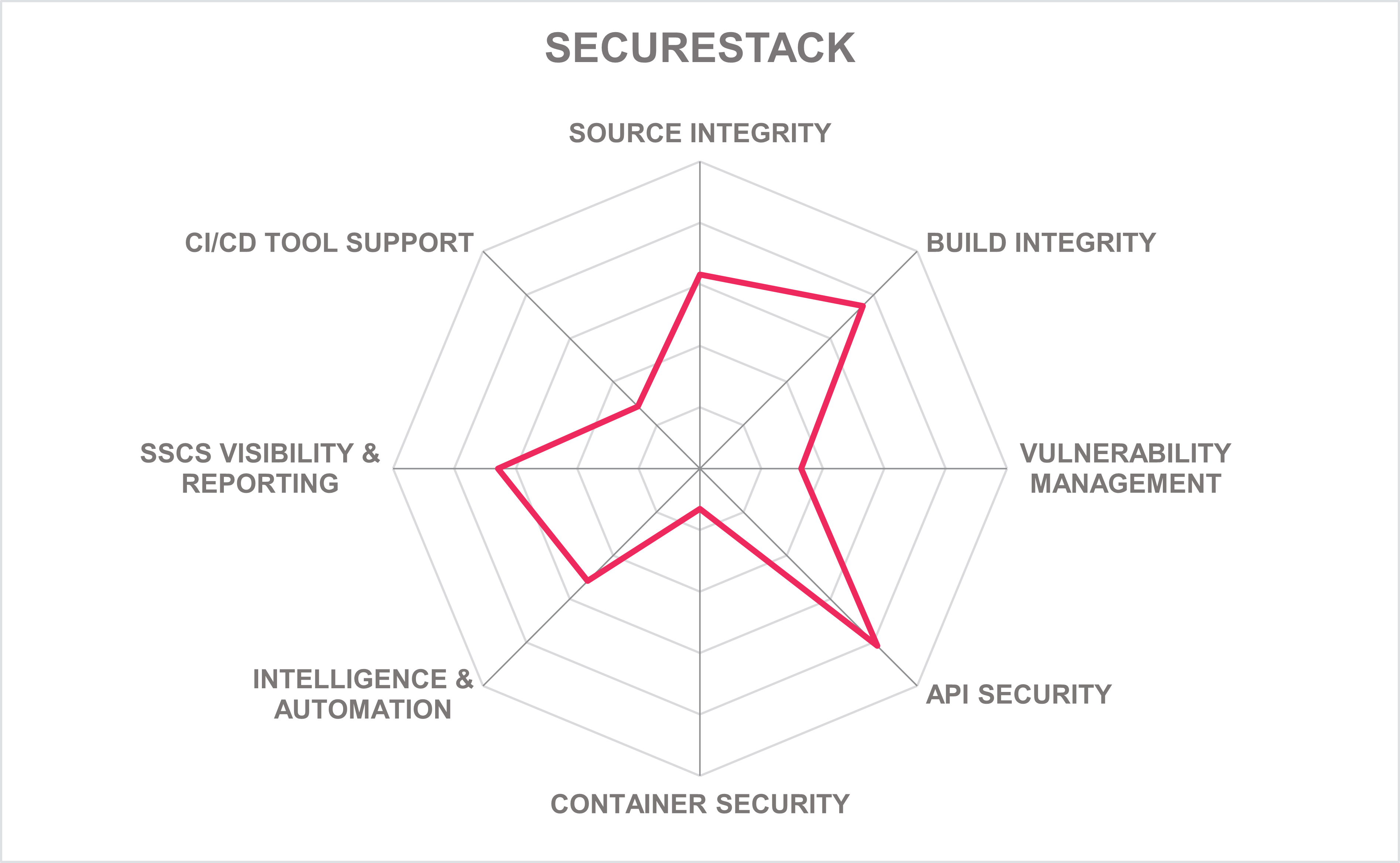
SecureStack customers are primarily in Australia and New Zealand, with growth in North America, which are SMB to mid-market organizations. SecureStack DevSecOps Platform offers good support in the areas of source and build integrity, as well as API security, and should be of interest to organizations in the APAC and North American regions.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 9: SecureStack’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
5.9 Veracode – The Veracode Continuous Software Security Platform
Since its founding in 2006, Veracode has been a longstanding vendor for providing tools in the Software Supply Chain Security (SSCS) market. It has also had a long history of acquisitions. Veracode was acquired by CA Technologies in 2017. In mid-2018, Broadcom acquired CA, but later that year, Thoma Bravo announced Veracode’s acquisition from Broadcom. In March of 2022, TA Associates became the latest company to acquire Veracode. Through these acquisitions, Veracode has continued building its capabilities in the SSCS market. The Veracode Continuous Software Security Platform is the latest iteration of its suite of products covering the areas of source code and builds integrity as well as application, container, and JavaScript vulnerability testing. Software Supply Chain risk visibility and reporting are also provided by the platform.
The Veracode Continuous Software Security Platform supports Azure DevOps, BitBucket, Github, and GitLab source code repositories. The Veracode SCA for third-party code scanning can detect and report on software libraries and software component vulnerabilities, dependencies, locations, and licenses and make recommendations for remediation if issues are found. Veracode’s SBOM can generate reports in multiple formats, which include Common Package Enumeration (CPE), CycloneDX, Package URLs (PURL), and Software Package Data Exchange (SPDX). Although the solution cannot merge multiple sources of SBOM documents, it can translate between SBOM formats. Code tampering detection and prevention are not provided; however, some capabilities can be achieved through integration with Venafi, which supports digitally signing build artifacts before uploading to build repositories or deployment. Build integrity features can ensure that signed source code is used in the build process, that hard-coded secrets have been removed, and perform container security checks. The Veracode Container Security can identify security issues in images, Docker files, and IaC code used to deploy container images.
The Veracode static analysis supports a wide range of programming and script languages and provides out-of-the-box plugins for popular IDEs, which include Eclipse, IntelliJ, Visual Studio, and Visual Studio Code. Its static analysis tests perform policy, sandbox, pipeline, and IDE scans and uses data flow and taint analysis as well as providing a control flow graph (CFG) technique. The solution can check for IaC misconfigurations for platforms like AWS CloudFormation, Azure Resource Manager, and Terraform. Support for OASIS Static Analysis Results Interchange Format (SARIF), Veracode has a GitHub action that initiates a Veracode Static Analysis Pipeline Scan and takes the Veracode pipeline scan JSON result file as an input and transforms it to a SARIF format. With the recent acquisition of Crashtest Security Suite, Veracode added a lightweight, developer-friendly dynamic tool to their existing platform’s DAST scanning capabilities. The solution also has the ability to automate vulnerability scans that can be scheduled or integrated into the CI/CD pipeline to trigger scans based on defined events. The Veracode DAST tool is capable of scanning microservices and APIs. DAST API scans focus on REST APIs and provide tests for valid Swagger 2.0 or OpenAPI 3 documentation.
Veracode is primarily a SaaS service hosted in the public cloud. IDE and CLI plugins and an agent are given as client-side scanning components on-premises. No managed service option is given, although Veracode provides manual pen testing to support AppSec programs. All of Veracode's Application Security Testing tools are available via REST and XML-RPC APIs. Access to most of Veracode scanning tools, such as its static analysis, SCA, and container security, are accessible via CLI. Veracode's SDKs provide access to the majority of the functionality and support the Java, .NET, and Python programming languages OOTB. The Veracode solution has been independently certified to support compliance and standards, such as SOC 2 Type 2, FedRAMP and StateRAMP.
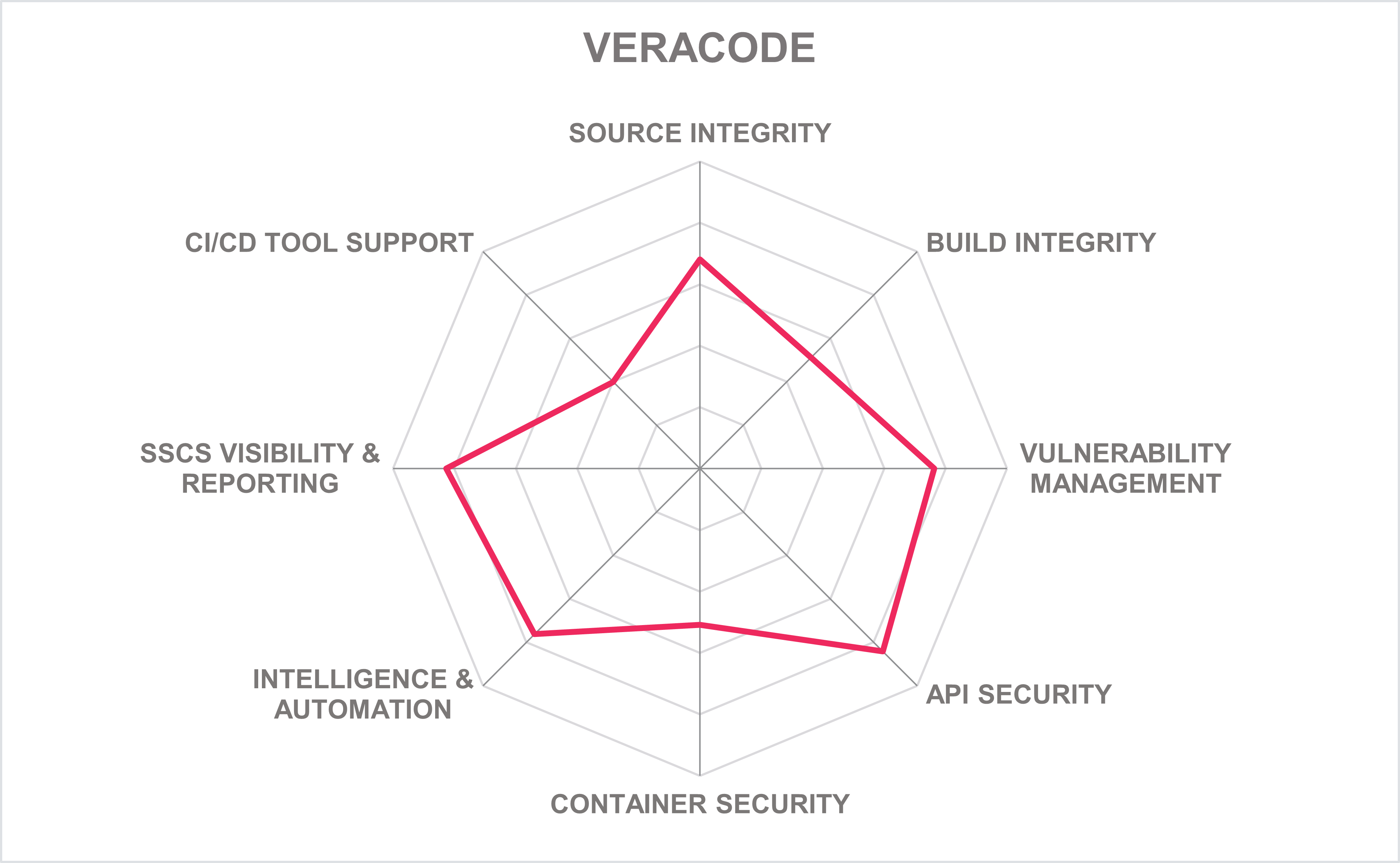
Veracode’s customer base comprises SMB to enterprise-level organizations located primarily in North America, with good growth in the EMEA, APAC, and Latin America. It also supports a good partner ecosystem commensurate to those customer regions. Veracode is a leader in all KuppingerCole Leadership Compass categories and provides depth in source, API security, and vulnerability detection SSCS capabilities while providing visibility of key SSCS indicators. Veracode should be considered when evaluating SSCS solutions.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
Table 10: Veracode’s rating
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
6 Vendors to Watch
Besides the vendors covered in detail in this document, we observe some other vendors in the market that readers should be aware of. These vendors do not fully fit the market definition but offer a significant contribution to the market space. This may be for their supportive capabilities to the solutions reviewed in this document, for their unique methods of addressing the challenges of this segment or maybe a fast-growing startup that may be a strong competitor in the future.
6.1 42Crunch
42Crunch is a privately held API security company headquartered in London, UK. Founded in 2016, the company focuses on proactive discovery and remediation in API contracts and runtime protection against API attacks. 42Crunch seeks to make API security a commodity by providing developer-focused tools, offering guidance and best practices, and supporting DevSecOps initiatives.
42Crunch offers two services that support software supply chain security. Its API Audit service acts as a linter that performs a static analysis of OpenAPI (Swagger) files, which then provides a report of identified issues by severity based on criteria such as security, data validation, schemas, and specification format as some examples. Its API Scan service can test the API's implementation to ensure OpenAPI contract conformance and detect vulnerabilities such as the OWASP API Security Top 10 Vulnerabilities. Both services offer plugins to developer IDEs and CI/CD Platforms.
Why worth watching: 42Crunch continues to build API tools to shift-left to support software supply chain security.
6.2 Anchore
Anchore, Inc. is a privately held company founded in 2016 and based in Santa Barbara, California, USA. The Anchore platform and its open-source tools seek to help developers and security teams provide secure cloud-native software by protecting the supply chain.
The Anchore Platform offers a range of software supply chain security capabilities that include SBOM (Software Bill of Materials), scanning for container vulnerabilities and registries, Kubernetes images, as well as scans for potential FedRAMP vulnerabilities. The platform integrates with CI/CD pipelines, container registries, and repositories, providing security checks and monitoring throughout the software supply chain.
Why worth watching: Anchore platform and open-source tools provide container-based and cloud-native software supply chain security.
6.3 Apiiro
Apiiro is a private company based in New York, New York, U.S.A. It provides a single application security platform that can provide application risk visibility, prioritization, and remediation by identifying, fixing, and preventing risks in applications and software supply chain pipelines, as well as integrating with application and cloud security tools. Some of the platform's capabilities include Application Security Posture Management, eXtended SBOM (XBOM), API Security Testing, Secrets Security, Open-Source Security using SCA, and Infrastructure as Code (IaC) Security.
Why worth watching: Apiiro provides some interesting features such as graph-based inventory, automated remediation, developer behavior analysis, and a risk graph.
6.4 ArmorCode
ArmorCode was founded in 2020 with headquarters in Palo Alto, California, U.S. It offers a single AppSecOps platform that provides security insight and collaboration between security and developer teams. The platform gives capabilities that include Application Security Posture Management, Unified Vulnerability Management, Application Security Orchestration and Correlation, and DevSecOps Automation.
ArmorCode AppSecOps platform integrates and correlates data from security, CI/CD, and cloud infrastructure tools, as well as ticketing and collaboration solutions in an organization's IT ecosystem. It provides dashboards of an application's security posture that includes vulnerability statistics and trends, SLA compliance, and IT ticket status over time, as some examples.
Why worth watching: ArmorCode provides capabilities that correlates security data and allows collaboration between DevOps and Security teams.
6.5 BluBracket
BluBracket provides a source code security solution that is capable of finding and fixing risks in software code. BluBracket was recently acquired by HashiCorp to expand its Secrets Management capabilities.
BluBracket Code Security Platform helps organizations identify and remediate code vulnerabilities, detect secrets such as API keys, access tokens, passwords, and sensitive data in code, and enforce secure coding practices through integrations with code repositories and developer and CI/CD tools. The platform provides security controls and insights into potential risks, including sensitive data exposure, hardcoded credentials, and other vulnerabilities.
Why worth watching: It will be interesting to see how the HashiCorp acquisition of BluBracket fits into its overall portfolio.
6.6 Bright Security
Bright Security is a private company founded in 2018 with offices in the USA, Israel, and Georgia. Bright Security offers a Dynamic Application Security Testing (DAST) platform for testing applications and API security.
The platform can test static web applications, including single-page apps (SPAs), APIs and microservices, and server-side mobile applications. Its API security can test common API protocols and formats such as REST, SOAP, and GraphQL APIs, as well as the ability to scan APIs via Postman Collections or Swagger. The platform integrates into the CI/CD pipeline to automatically test software builds, pull requests, or merges, to detect security issues. Supported CI/CD tools include GitHub Actions, CircleCI, Jenkins, Azure Pipelines, Travis CI, GitLab, TeamCity, and JFrog Pipelines.
Why worth watching: Bright Security provides automated testing of applications and APIs within the SDLC.
6.7 Check Point
Checkpoint, a global cybersecurity vendor, was founded 27 years ago in Israel. They now have dual HQs in Tel Aviv and Silicon Valley. Within its portfolio is a DevSecOps Solution to automate the SDLC. The solution offers code, container image, and IaC scanning. With all scans, Check Point’s CloudGuard solution will check for security vulnerabilities and non-compliance in the CI/CD pipeline policies. If security issues are found, remediation steps are provided, and the development pipeline is stopped before moving to production.
Why worth watching: Check Point CloudGuard provides a checkpoint before security issues are pushed to a cloud production environment.
6.8 ForAllSecure
Founded in 2012, ForAllSecure is a privately owned company based in Pittsburgh, Pennsylvania, U.S. Its solution, Mayhem, is a platform with a set of integrated products and provides a software security testing tool that can automate and enhance the process of finding vulnerabilities and weaknesses in software applications through advanced fuzzing techniques. It uses a patented form of symbolic execution that allows Mayhem to map out the possible execution paths of the running code and applies machine learning (ML) to the fuzzing process.
Why worth watching: ForAllSecure Mayhem provides an interesting approach to AppSec fuzz testing with additional capabilities to report vulnerabilities and provide remediation recommendations.
6.9 Lineaje
Lineaje is a privately held company based in Saratoga, California, U.S.A. that focuses on Software Supply Chain Security by offering its SBOM products. Its SBOM 360 product includes a CLI/SCA tool that can ingest SPDX, CycloneDX, SWID, as well as other formats. It's capable of decomposing software within source code repositories and binaries, and container images. This includes open-source packages and third-party and private source code. SBOM 360 can also detect dependency tampering. The Lineaje's Deep Learning Engine (LDLE) handles the decomposition of the source code, binaries, application packages, and packaged applications from the Cloud, On-Premises, and Contractor Premise locations by utilizing its API. As part of the LDLE processing, it can assign unique identities for components and build a deep transitive dependency graph of those components. The Lineaje's SBOM360 Hub allows for the publication of SBOMs in which the SBOMs can be uploaded in SPDX, and CycloneDX formats, then mapping a company's product SBOM to its product SKUs.
Why worth watching: Lineaje allows organizations to provide and publish SBOMs of the software it builds regardless of location.
6.10 OpenText
OpenText, founded in 1991, is a large public company headquartered in Waterloo, Canada. As part of the Micro Focus acquisition in early 2023, OpenText now offers the AppSec Fortify platform which provides SCA, SAST and DAST capabilities.
Fortify by OpenText SCA analyzes open-source and third-party software components used in applications, assesses their security risks, identifies vulnerabilities, manages their associated risks, and generates SBOMs. The Fortify SAST performs a static code analysis to identify security flaws and vulnerabilities in the source code of applications. It examines the codebase without executing the application and provides developers with detailed reports and recommendations for remediation. Fortify SAST supports 30+ languages and frameworks and can automate security within the CI/CD pipeline. The Fortify DAST capability enables organizations to assess the security of their applications in runtime by simulating real-world attacks. CyberRes Fortify scans the running application, identifies vulnerabilities, and provides actionable insights to enhance security. Fortify DAST can test API security and supports SOAP, REST, GraphQL, and gRPC protocols and formats.
Why worth watching: Fortify by OpenText provides a mature platform for the shift-left software supply chain security and is expected to continue to increase its capabilities with OpenText.
6.11 Snyk
Snyk is a private Boston U.S. company that offers software supply chain security products by identifying and addressing security vulnerabilities in open-source libraries and containers. Snyk Code provides SCA capabilities supported by security and application intelligence. Snyk Container gives container and Kubernetes security capabilities that helps find, prioritize, and fix vulnerabilities throughout the SDLC. In addition, Snyk IaC ensures secure deployment configuration and supports platforms such as Terraform, CloudFormation, ARM, Kubernetes, Docker, AWS, Azure, and Google Cloud.
Why worth watching: Synk provides software supply chain tools for modern applications through the SDLC.
6.12 Sysdig
Sysdig is a Kubernetes and cloud security vendor based in San Francisco, California. Founded in 2013 by the co-creator of the popular open-source project Wireshark, the company has deep roots within the OSS community and designs its products on an open-source security stack, including Prometheus, Falco, Sysdig Inspect, OPA, etc.
The company's flagship product is the Sysdig Platform, which combines container, Kubernetes, and cloud observability and security functions in a single universal foundation that turns cloud posture management, vulnerability management, and container visibility into actionable insights for DevOps and security teams. Sysdig Monitor and Sysdig Secure can be licensed separately or together.Why worth watching: The platform is built upon popular OSS tools that can be deployed independently, while the enterprise SaaS offering offers additional capabilities.
7 Related Research
Executive View: Veracode Application Security Platform - 79060
Leadership Compass: API Management and Security - 80477
Leadership Compass: Container Security - 80207
Leadership Compass: Network Detection & Response (NDR) - 80489
Leadership Compass: Secrets Management - 80769
Leadership Compass: Security Orchestration, Automation and Response (SOAR) - 80016
Market Compass: Cybersecurity for Industrial Control Systems - 80913
Market Compass: IT-GRC Tools - 71165
Market Compass: Policy Based Access Management - 81101
8 Methodology
8.1 About KuppingerCole's Leadership Compass
KuppingerCole Leadership Compass is a tool which provides an overview of a particular IT market segment and identifies the leaders within that market segment. It is the compass which assists you in identifying the vendors and products/services in that market which you should consider for product decisions. It should be noted that it is inadequate to pick vendors based only on the information provided within this report.
Customers must always define their specific requirements and analyze in greater detail what they need. This report doesn’t provide any recommendations for picking a vendor for a specific customer scenario. This can be done only based on a more thorough and comprehensive analysis of customer requirements and a more detailed mapping of these requirements to product features, i.e. a complete assessment.
8.2 Types of Leadership
We look at four types of leaders:
- Product Leaders: Product Leaders identify the leading-edge products in the particular market. These products deliver most of the capabilities we expect from products in that market segment. They are mature.
- Market Leaders: Market Leaders are vendors which have a large, global customer base and a strong partner network to support their customers. A lack in global presence or breadth of partners can prevent a vendor from becoming a Market Leader.
- Innovation Leaders: Innovation Leaders are those vendors which are driving innovation in the market segment. They provide several of the most innovative and upcoming features we hope to see in the market segment.
- Overall Leaders: Overall Leaders are identified based on a combined rating, looking at the strength of products, the market presence, and the innovation of vendors. Overall Leaders might have slight weaknesses in some areas, but they become Overall Leaders by being above average in all areas.
For every area, we distinguish between three levels of products:
- Leaders: This identifies the Leaders as defined above. Leaders are products which are exceptionally strong in certain areas.
- Challengers: This level identifies products which are not yet Leaders but have specific strengths which might make them Leaders. Typically, these products are also mature and might be leading-edge when looking at specific use cases and customer requirements.
- Followers: This group contains vendors whose products lag in some areas, such as having a limited feature set or only a regional presence. The best of these products might have specific strengths, making them a good or even best choice for specific use cases and customer requirements but are of limited value in other situations.
Our rating is based on a broad range of input and long experience in that market segment. Input consists of experience from KuppingerCole advisory projects, feedback from customers using the products, product documentation, and a questionnaire sent out before creating the KuppingerCole Leadership Compass, and other sources.
8.3 Product Rating
KuppingerCole Analysts AG as an analyst company regularly evaluates products/services and vendors. The results are, among other types of publications and services, published in the KuppingerCole Leadership Compass Reports, KuppingerCole Executive Views, KuppingerCole Product Reports, and KuppingerCole Vendor Reports. KuppingerCole uses a standardized rating to provide a quick overview on our perception of the products or vendors. Providing a quick overview of the KuppingerCole rating of products requires an approach combining clarity, accuracy, and completeness of information at a glance.
KuppingerCole uses the following categories to rate products:
- Security
- Functionality
- Deployment
- Interoperability
- Usability
Security is primarily a measure of the degree of security within the product/service. This is a key requirement. We look for evidence of a well-defined approach to internal security as well as capabilities to enable its secure use by the customer, including authentication measures, access controls, and use of encryption. The rating includes our assessment of security vulnerabilities, the way the vendor deals with them, and some selected security features of the product/service.
Functionality is a measure of three factors: what the vendor promises to deliver, the state of the art and what KuppingerCole expects vendors to deliver to meet customer requirements. To score well there must be evidence that the product / service delivers on all of these.
Deployment is measured by how easy or difficult it is to deploy and operate the product or service. This considers the degree in which the vendor has integrated the relevant individual technologies or products. It also looks at what is needed to deploy, operate, manage, and discontinue the product / service.
Interoperability refers to the ability of the product / service to work with other vendors’ products, standards, or technologies. It considers the extent to which the product / service supports industry standards as well as widely deployed technologies. We also expect the product to support programmatic access through a well-documented and secure set of APIs.
Usability is a measure of how easy the product / service is to use and to administer. We look for user interfaces that are logically and intuitive as well as a high degree of consistency across user interfaces across the different products / services from the vendor.
We focus on security, functionality, ease of delivery, interoperability, and usability for the following key reasons:
- Increased People Participation: Human participation in systems at any level is the highest area of cost and the highest potential for failure of IT projects.
- Lack of excellence in Security, Functionality, Ease of Delivery, Interoperability, and Usability results in the need for increased human participation in the deployment and maintenance of IT services.
- Increased need for manual intervention and lack of Security, Functionality, Ease of Delivery, Interoperability, and Usability not only significantly increase costs, but inevitably lead to mistakes that can create opportunities for attack to succeed and services to fail.
KuppingerCole’s evaluation of products / services from a given vendor considers the degree of product Security, Functionality, Ease of Delivery, Interoperability, and Usability which to be of the highest importance. This is because lack of excellence in any of these areas can result in weak, costly and ineffective IT infrastructure.
8.4 Vendor Rating
We also rate vendors on the following characteristics
- Innovativeness
- Market position
- Financial strength
- Ecosystem
Innovativeness is measured as the capability to add technical capabilities in a direction which aligns with the KuppingerCole understanding of the market segment(s). Innovation has no value by itself but needs to provide clear benefits to the customer. However, being innovative is an important factor for trust in vendors, because innovative vendors are more likely to remain leading-edge. Vendors must support technical standardization initiatives. Driving innovation without standardization frequently leads to lock-in scenarios. Thus, active participation in standardization initiatives adds to the positive rating of innovativeness.
Market position measures the position the vendor has in the market or the relevant market segments. This is an average rating over all markets in which a vendor is active. Therefore, being weak in one segment doesn’t lead to a very low overall rating. This factor considers the vendor’s presence in major markets.
Financial strength even while KuppingerCole doesn’t consider size to be a value by itself, financial strength is an important factor for customers when making decisions. In general, publicly available financial information is an important factor therein. Companies which are venture-financed are in general more likely to either fold or become an acquisition target, which present risks to customers considering implementing their products.
Ecosystem is a measure of the support network vendors have in terms of resellers, system integrators, and knowledgeable consultants. It focuses mainly on the partner base of a vendor and the approach the vendor takes to act as a “good citizen” in heterogeneous IT environments.
Again, please note that in KuppingerCole Leadership Compass documents, most of these ratings apply to the specific product and market segment covered in the analysis, not to the overall rating of the vendor.
8.5 Rating Scale for Products and Vendors
For vendors and product feature areas, we use a separate rating with five different levels, beyond the Leadership rating in the various categories. These levels are
- Strong positive: Outstanding support for the subject area, e.g. product functionality, or outstanding position of the company for financial stability.
- Positive: Strong support for a feature area or strong position of the company, but with some minor gaps or shortcomings. Using Security as an example, this can indicate some gaps in fine-grained access controls of administrative entitlements. For market reach, it can indicate the global reach of a partner network, but a rather small number of partners.
- Neutral: Acceptable support for feature areas or acceptable position of the company, but with several requirements we set for these areas not being met. Using functionality as an example, this can indicate that some of the major feature areas we are looking for aren’t met, while others are well served. For Market Position, it could indicate a regional-only presence.
- Weak: Below-average capabilities in the product ratings or significant challenges in the company ratings, such as very small partner ecosystem.
- Critical: Major weaknesses in various areas. This rating most commonly applies to company ratings for market position or financial strength, indicating that vendors are very small and have a very low number of customers.
8.6 Inclusion and Exclusion of Vendors
KuppingerCole tries to include all vendors within a specific market segment in their Leadership Compass documents. The scope of the document is global coverage, including vendors which are only active in regional markets such as Germany, Russia, or the US.
However, there might be vendors which don’t appear in a Leadership Compass document due to various reasons:
- Limited market visibility: There might be vendors and products which are not on our radar yet, despite our continuous market research and work with advisory customers. This usually is a clear indicator of a lack in Market Leadership.
- Declined to participate: Vendors might decide to not participate in our evaluation and refuse to become part of the Leadership Compass document. KuppingerCole tends to include their products anyway if sufficient information for evaluation is available, thus providing a comprehensive overview of leaders in the market segment.
- Lack of information supply: Products of vendors which don’t provide the information we have requested for the Leadership Compass document will not appear in the document unless we have access to sufficient information from other sources.
- Borderline classification: Some products might have only small overlap with the market segment we are analyzing. In these cases, we might decide not to include the product in that KuppingerCole Leadership Compass.
The target is providing a comprehensive view of the products in a market segment. KuppingerCole will provide regular updates on their Leadership Compass documents.
We provide a quick overview about vendors not covered and their offerings in chapter Vendors and Market Segments to watch. In that chapter, we also look at some other interesting offerings around the market and in related market segments.
9 Copyright
© 2024 KuppingerCole Analysts AG all rights reserved. Reproduction and distribution of this publication in any form is forbidden unless prior written permission. All conclusions, recommendations and predictions in this document represent KuppingerCole's initial view. Through gathering more information and performing deep analysis, positions presented in this document will be subject to refinements or even major changes. KuppingerCole disclaims all warranties as to the completeness, accuracy and/or adequacy of this information. Even if KuppingerCole research documents may discuss legal issues related to information security and technology, KuppingerCole does not provide any legal services or advice and its publications shall not be used as such. KuppingerCole shall have no liability for errors or inadequacies in the information contained in this document. Any opinion expressed may be subject to change without notice. All product and company names are trademarks ™ or registered trademarks ® of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
KuppingerCole Analysts support IT professionals with outstanding expertise in defining IT strategies and in relevant decision-making processes. As a leading analyst company, KuppingerCole provides first-hand vendor-neutral information. Our services allow you to feel comfortable and secure in taking decisions essential to your business.
KuppingerCole Analysts AG, founded in 2004, is a global, independent analyst organization headquartered in Europe. We specialize in providing vendor-neutral advice, expertise, thought leadership, and practical relevance in Cybersecurity, Digital Identity & IAM (Identity and Access Management), Cloud Risk and Security, and Artificial Intelligence, as well as for all technologies fostering Digital Transformation. We support companies, corporate users, integrators and software manufacturers in meeting both tactical and strategic challenges and making better decisions for the success of their business. Maintaining a balance between immediate implementation and long-term viability is at the heart of our philosophy.
For further information, please contact clients@kuppingercole.com.
















































