1 Introduction / Executive Summary
Commercial, government, and non-profit organizations of all kinds increasingly find themselves under cyber-attacks these days. Ransomware, fraud, credential theft, PII theft, and intellectual property theft occur on a daily basis around the globe. IT teams mitigate the risks by employing and deploying a wide array of cybersecurity tools. Many components of security architectures are well-known: firewalls, VPNs, Endpoint Protection Detection & Response (EPDR), Security Incident and Event Management (SIEM), etc. In the last decade, security professionals have pivoted to address how to detect attacks and other malicious activities, rather than focusing solely on prevention. SIEM and IDS (Intrusion Detection Systems) were touted as solutions for detection, but they quickly maxed out their potential usefulness and have been forced to evolve. Endpoint Protection (EPP) has largely merged with Endpoint Detection and Response (EDR), which came to the fore as a means of discovering malicious behavior on desktops, laptops, and servers.
NDR solutions are designed to help security analysts discover evidence on the network and/or in the cloud of malicious activities that are in progress or have already occurred. NDR tools are effectively “Next-Gen IDS”. One of the big differences between NDR and old IDS tools is that NDR tools use multiple Machine Learning (ML) techniques to identify normal baselines and anomalous traffic, rather than static rules or IDS signatures. Given the volumes of network connection data that must be analyzed, using ML algorithms and models is a “must” rather than a “nice-to-have”. Historically, the major drawbacks to IDS were that it was labor intensive to operate, was of limited effectiveness, and could generate high numbers of false positives.
These security tools were created to discover and remediate certain types of attacks. Advanced Persistent Threats (APTs) are often perpetrated by actors from state intelligence agencies for the purpose of gathering intelligence on foreign companies and agencies, copying intellectual property, or sabotage. APT actors may also include well-funded but unscrupulous companies and hacktivist groups. Their goals often require long-terms presence on victims’ properties, hence the use of the term “persistent”. APT groups have historically been the most likely ones to use Zero-Day exploits (those which were previously unseen in the wild), that may give them the advantage of not being detected by EPDR agents. In the last couple of years, cybercriminal groups have begun to use APT strategies and tactics against their victims: gaining access to resources, siphoning out data, then detonating ransomware.
Enter NDR as an additional tool to discover hitherto unknown compromises. Since data exfiltration is usually an objective of attackers, even in contemporary ransomware cases executed by cybercriminal units, properly deployed NDR tools can be better suited at discovering lateral movement from the initial compromised device to other assets within the target organization, use of compromised privileged credentials, and data exfiltration attempts.
NDR tools are also deployed to provide visibility in OT/ICS/IIoT environments where it may not be possible to implement endpoint agent-based solutions. Enterprises often separate OT/ICS and IIoT devices onto their own networks for containment purposes. Such network segmentation is indeed useful, and the control points between these specialized networks and general-use and back-end networks are logical places to deploy NDR sensors.
NDR tools can also help discover and remediate more common types of attack such as unwanted bot activities, credential theft, and insider threats.
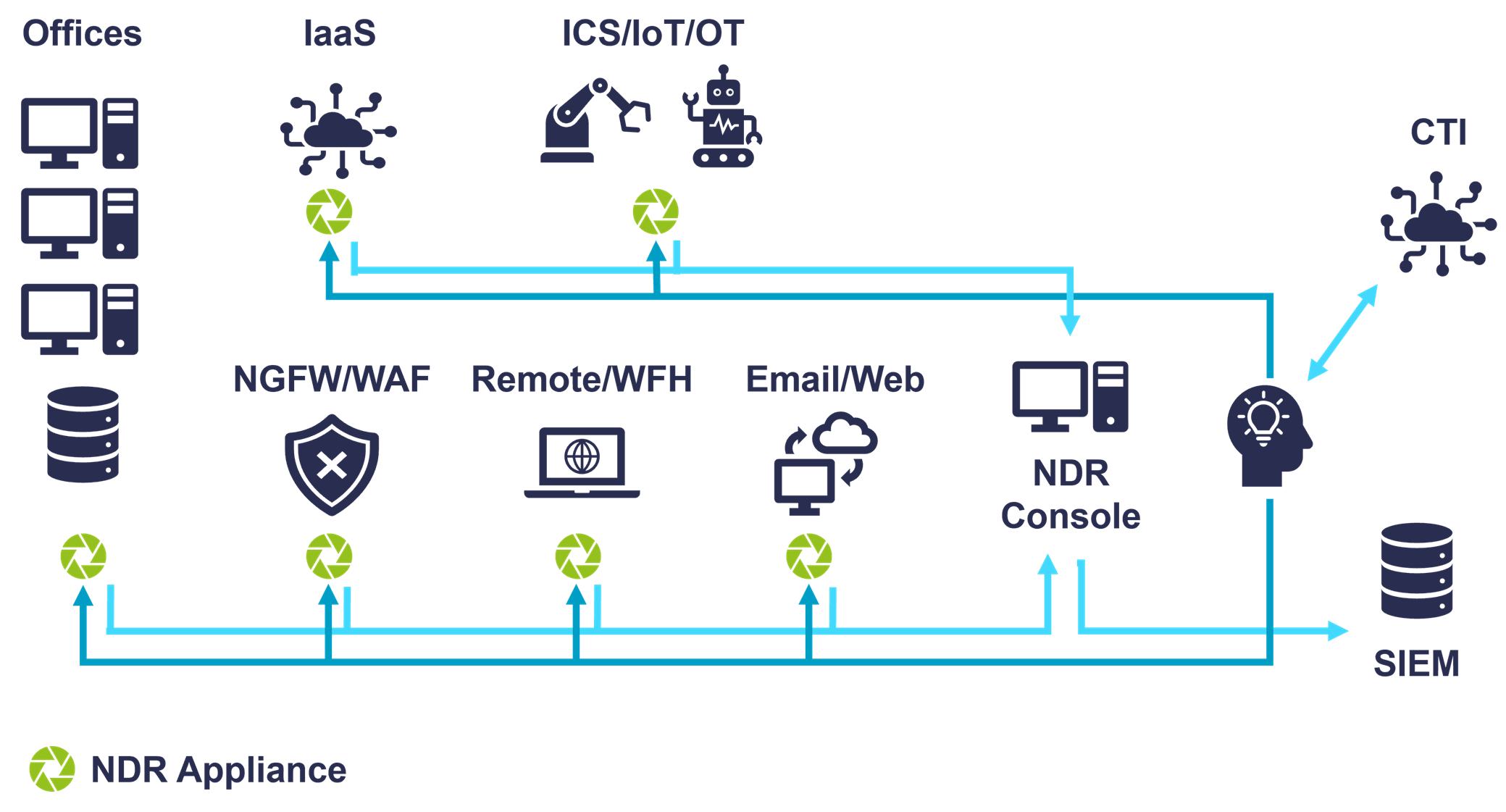
NDR solutions can log all activities from attached networks in a central secure location for both real-time and later forensic analysis. NDR solutions are usually implemented as a mix of appliances, virtual appliances, and IaaS VM images. Appliances and/or virtual appliances deployed on-premises must tap into physical networking gear at all relevant network control points: off switch and router span or tap ports, or off network packet brokers. For example, if your organization still has perimeters (and most do), NDR appliances need to be placed there. Vendors often talk about “north-south” (across perimeters) and “east-west” (lateral movement) deployment points. All directions need to be covered by NDR solutions for maximum coverage.
Alternatively, some NDR virtual appliances can be co-located with firewalls or other perimeter network devices. Other common places to deploy NDR sensors are between network segments, around IoT and/or OT and Industrial Control Systems (ICS) / SCADA networks, and around web-facing properties and Wi-Fi portals. With an irreversible Work-From-Home (WFH) trend in response to the global pandemic, NDRs should be deployed alongside VPNs. NDR VMs can be inserted into your IaaS and potentially PaaS infrastructure as well. Exactly how many appliances or virtual appliances your organization needs and where they should be placed depends on your architecture. Proper design of NDR deployments is necessary to monitor all traffic flows.
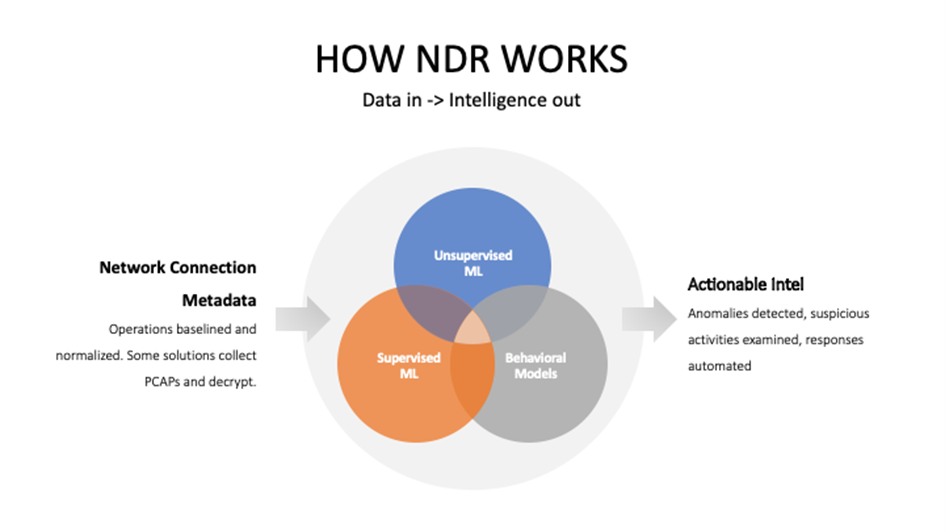
A key differentiator for NDR technology is the employment of multiple ML algorithms in the various analysis phases. At a high level, unsupervised ML finds outliers or anomalies in traffic patterns; while supervised ML models categorize possible threats among the outliers, classify malicious activities, domains, and other attributes. Supervised ML is more commonly used by vendors for Encrypted Traffic Analysis. Deep Learning (DL) algorithms and detection models utilize variations of neural networks and are the latest generation of AI/ML technology as applied to the cybersecurity space. Some NDR vendors use DL for Encrypted Traffic Analysis. The most effective solutions utilize several layers of ML-and DL-enhanced processing of all traffic at line speed. Vendor products in this segment typically advertise 10 – 200 Gbps throughput on network sensors, and 1 Gbps for IaaS traffic scanning.
In terms of responses, NDR solutions can provide dashboards/alerts/reports, display real-time visualizations, allow drilldowns into details, enrich discoveries with threat intelligence, correlate events and provide automated analysis, halt suspicious traffic, isolate nodes, and send event data to SIEMs, SOARs, and forensic/case management applications. In cases where vendor products operate in passive mode, they direct 3rd-party security tools via APIs to execute these responses.
NDR solutions are not usually easy to operate, and in some cases require a dedicated team of one or more analysts (depending on organization size) to make the best use of the capabilities. Knowing this, many vendors provide facilities within their solutions to automate aspects of analysis, including evidence collection, correlation, remediation suggestions, and root cause analysis (RCA). Many of the vendors in the NDR space offer managed services of different types to augment the products. Additionally, many MSSPs can manage an NDR deployment and handle the threat hunting and analysis tasks on behalf of their customers.
There are several good reasons to consider deploying NDR. The typical capabilities outlined above can be of service in discovering malicious activity that your other security tools may have missed.
Endpoint Protection Detection & Response (EPDR) agents are a must for every computing device that can run them. However, sometimes they may not catch every piece of malicious code. There are several reasons why NDR is a needed complement to EPDR and other security solutions:
- BYOD bypass: In permissive environments, some users may bring in infected devices and not know it because their machines do not have EPDR agents. Business partners and contractors may use their own devices, which may be beyond the control of the hosting organization.
- Ineffective EPP: Some EPP solutions are better at detecting and preventing malware than others. Also, EPP agents need to be updated; even those that use ML-driven heuristics and exploit prevention. If EPP solutions are weak or have outdated signatures or ML models, they are more likely to miss malware. Ultimately, it is not logically possible to design an anti-malware solution that can detect malicious code with 100% accuracy all the time.
- Non-traditional endpoints: Many IoT and IIoT devices can’t run EPDR. Operating systems may not support EPDR agents but are still susceptible to hacking. In other cases, IoT devices are simply not user configurable. Enterprises with large numbers of such devices tend to isolate them onto separate VLANs. These environments need security monitoring and detection capabilities that cannot be delivered by standard endpoint security solutions.
- Endpoint that cannot run agents: Some Linux and Windows computing devices have limited builds of operating systems to host specific applications and are not manageable by IT staff. For example, certain medical devices such as MRI machines can’t have 3rd-party security software added without invalidating warranties and support agreements. Other examples may include Industrial Control Systems (ICS) and SCADA networks. These environments are known to be targeted by particular kinds of malicious actors and given the highly critical nature of the work they do, must be monitored and protected. As in the IoT environments case, these environments need NDR solutions because other security technologies have no visibility here.
- Attack coverups: Advanced malware can erase application and operating system log entries and suppress security tool reporting. Unauthorized and unaudited use of compromised and privileged credentials may mask attacks. Signs of malicious activity may not make it to the SIEM from endpoints. Therefore, the only place where highly sophisticated attacks may be discovered may be at the network layer.
Organizations today increasingly use the cloud, and key resources may be located in IaaS or in SaaS. Thus, NDR solutions need visibility of cloud environments. Hybrid architectures are common, so many NDR customers need coverage for hybrid architectures.
Even though endpoint-based solutions may not have visibility of all malicious activities, malware communicates on networks: with command and control (C2) servers, to other assets in the environment (lateral movement), to participate in botnets for fraud or DDoS attacks, or to exfiltrate data. Therefore, NDR tools can discover malicious activities that endpoint solutions and SIEMs miss.
NDR solutions can be thought of another block in the foundation of security and monitoring architecture. Therefore, NDR sensors need to be strategically placed at optimum intersections within computing environments.
1.1 Highlights
The Top Ten findings in this Leadership Compass on Network Detection & Response solutions are:
- The NDR market continues to grow because customers do find value in modern ML-enhanced detection models over legacy IDS/IPS solutions.
- NDR and EPDR cover different kinds of environments, and both are needed in many kinds of organizations. Either type of solution alone may miss anomalies and thus signs of attacks.
- The future of NDR will be XDR, which is NDR + EPDR + User Behavioral Analysis (UBA) + Distributed Deception Platforms (DDP) + Cloud Workload Protection Platforms (CWPP). This market-wide union of product types is probably 3-5 years out, although some vendors have already begun to acquire and consolidate these products.
- Two major deployment paradigms exist in the NDR world: in-line sensors and passive sensors. In-line sensors offer direct response capabilities, while passive sensors rely on integrations. Both types of solutions continue to gain market share.
- Operational Technology Security and Industrial Controls Security are use cases that can be well-served by NDR. A majority of vendors in this report offer varying degrees of coverage for these environments.
- The Response part of NDR is becoming more widely utilized. Early adopters of NDR saw benefits from increased visibility and the ability to detect malicious activities, but many were not ready to allow automated responses. This may have been due to customers not fully trusting the solutions to take actions autonomously, such as shutting down connections and isolating hosts. Some may have felt like the risk of false positives negatively impacting productivity to have been too great. However, with the proliferation of ransomware, more NDR customers are opting to automatically mitigate damage.
- NDR as a managed service is rising. Some vendors offer managed detection and response services, and more MSSPs have NDR as part of their portfolio. NDR as part of an overall MDR (not just EDR) will be appealing to SMBs and some enterprises that need the functionality but do not have the expertise to deploy and maintain it.
- The product leaders in NDR are Arista Networks, Broadcom, Check Point, Cisco, ExtraHop, Fidelis Cybersecurity, Gurucul, NetWitness (RSA), and VMware.
- The innovation leaders in NDR are Arista Networks, Broadcom, Check Point, Cisco, ExtraHop, Fidelis Cybersecurity, Gurucul, and VMware.
- The market leaders in NDR are Arista Networks, Broadcom, Check Point, Cisco, ExtraHop, FireEye, NetWitness (RSA), and VMware.
















































