Commissioned by Ping Identity
1 Introduction
APIs are fascinating. No, really! And one does not have to be a developer or an IT expert to appreciate the impressive transformation they have gone through within the last decade or so.
From what used to be a purely technical concept created to make developers’ lives easier, Application Programming Interfaces (APIs) have evolved into one of the foundations of modern digital business. Today, APIs can be found everywhere – at homes and in mobile devices, in corporate networks and in the cloud, even in industrial environments, to say nothing about the Internet of Things.
APIs allow developers to create applications faster by enabling support for modern architectures like microservices. They ensure that applications from different vendors can exchange data seamlessly, orchestrate massive cloud infrastructures and global networks of smart devices. They enable business communications with suppliers, service providers, and customers. APIs can also unlock numerous new business models for companies to offer their core services in innovative ways, to reach new customer bases or to streamline sales and services across multiple channels.
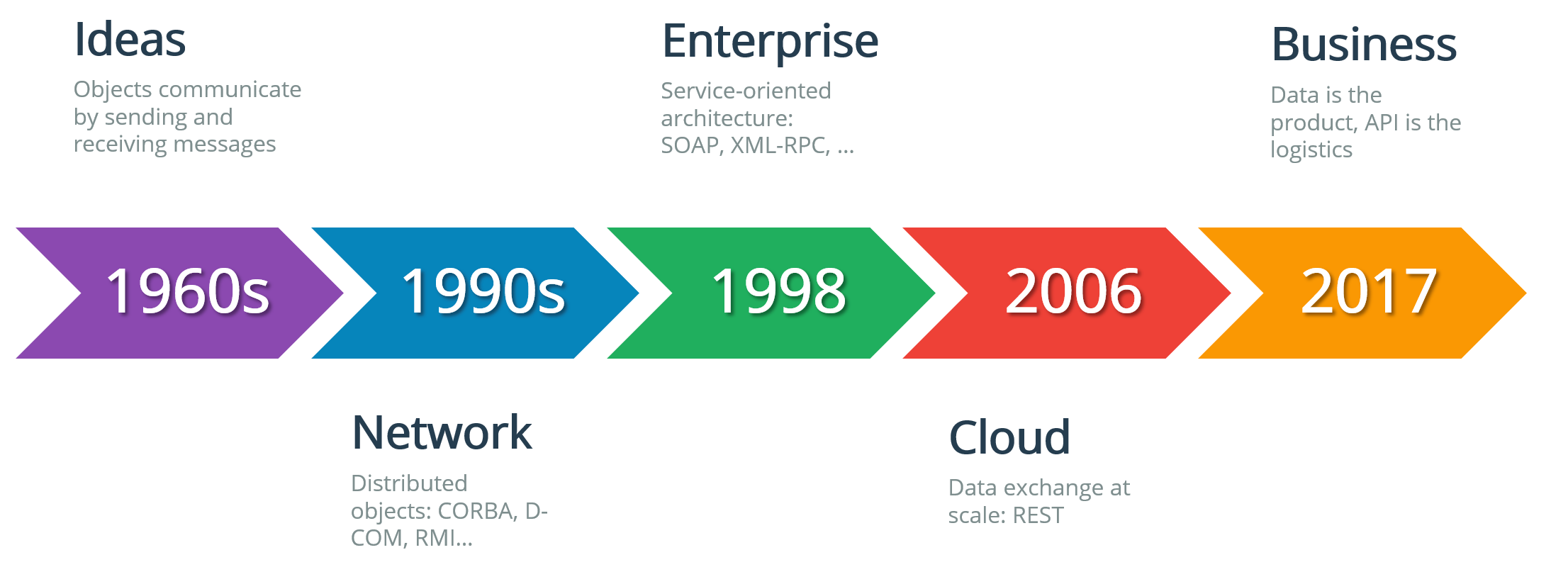
The term itself, as well as the general concept of designing applications as loosely coupled building blocks that communicate over abstract interfaces appeared first in the 1960s. The concept was driven by the growing complexity of software and the resulting need to hide that complexity from developers, allowing them to focus on business logic of their applications and reuse existing code for handling less important things.
The next stage of the API evolution came in the 1990s when the concept has been expanded to support remote API calls over network protocols. This allowed developers to provide or consume application functions across heterogeneous platforms, allowing even greater flexibility in designing complex software using different frameworks and technologies. On an even larger, internet-wide scale, this has led to the emergence of Web Services, object-oriented interfaces for exchanging data over the standard HTTP protocol – in a sense, the World Wide Web of machine-to-machine communications.
The breakthrough came in the early 2000s when the Representational State Transfer (REST) has emerged as an innovative architectural style for developing web services. This approach was an extremely fast, scalable and lean alternative to earlier enterprise standards like SOAP. Now, everyone could create and publish their APIs very quickly, using only existing standard protocols and formats (like HTTP, XML, and JSON) and existing tools.
In a world where digital information is one of the “crown jewels” of many modern businesses (and even the primary source of revenue for some), APIs are now powering the logistics of delivering digital products to partners and customers. Almost every software product or cloud service now comes with a set of APIs for management, integration, monitoring or a multitude of other purposes.
The rapid adoption of REST APIs also coincided with the exponential growth of cloud computing and mobile device proliferation, where they were the perfect medium to enable integrations between these heterogeneous systems and facilitate data exchange on a massive scale.
Modern graphical user interfaces and websites are becoming increasingly reliant on APIs as well, to ensure that user experience remains consistent across any device or client application. In fact, every action performed by a website visitor, mobile app user or even by a smart device involves at least one API call to a remote backend system. In short, APIs are everywhere!
This massive and ever-increasing growth clearly indicates that APIs are no longer just “an IT thing” – they have a very tangible impact on nearly every business’s operational efficiency, scalability, and agility and in the end, directly influence its profitability.
It is no surprise then that back in 2017, Forbes has declared it “the Year of API Economy”[^1], recognizing the value of APIs for creating new business models and generating new revenue flows across almost every industry around the world. Following the same logic, however, 2019 should be considered the Year of API Security, as the world is finally coming to the realization that the explosive growth of the API economy has ushered in a whole range of new security implications…










































