1 Empfehlungen
SAP-Sicherheit geht weit über die klassische Access Governance hinaus, die Anwender, ihre Zugangsrechte und Rollen, geplante Rezertifizierungen und die Identi-fikation von Verstößen anhand von Regeln der Funk-tionstrennung (Segregation of Duties, SoD) betrachtet. Obgleich diese Aspekte extrem wichtig bleiben, da sie typischerweise im Blickpunkt von Auditoren und Auf-sichtsbehörden stehen, erfordert SAP-Sicherheit heute einen 360-Grad-Ansatz:
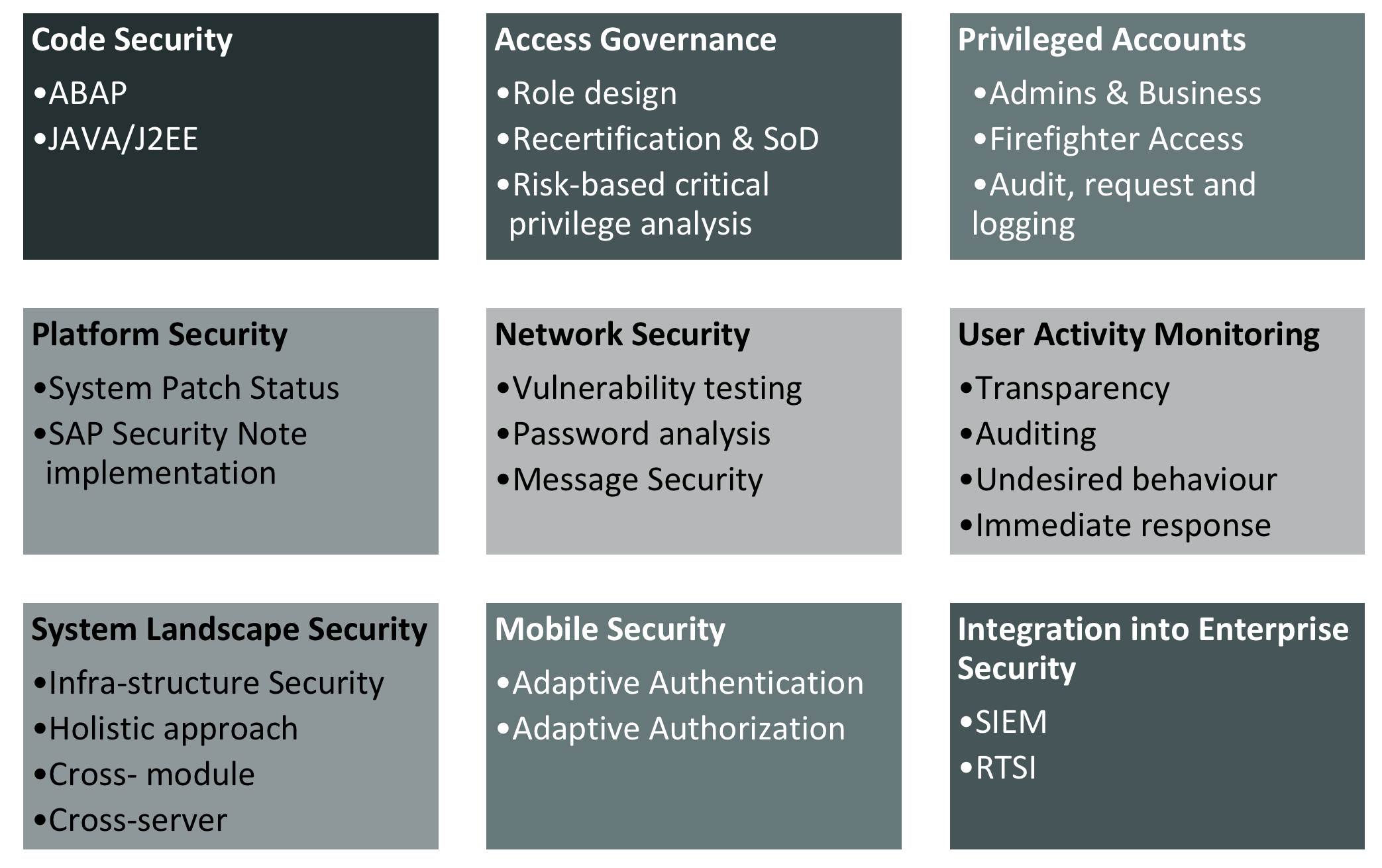
- Definiere und implementiere Sicherheitsprozesse mit allen relevanten Interessengruppen (IT-Betrieb, Technologie-Experten, IT-Sicherheit, Ge-schäftsbereiche, interne Auditoren), integriert in eine übergreifende GRC-Richtlinie (Governance, Risk Management, Compliance).
- Wähle einen Risiko-basierten Ansatz durch Identi-fikation und Bewertung aller relevanten Werte und definiere geeignete Maßnahmen zur Mitiga-tion.
- Definiere und implementiere eine starke System-sicherheit(Betriebssystem, Software auf dem ak-tuellen Patch-Stand) für alle Systeme, inkl. SAP.
- Teste die Sicherheitskonfiguration auf allen Ebe-nen durch regelmäßige Audits oder Penetrations-tests.
- Abonniere verfügbare Sicherheitsinformations-dienste mit aktuellen Daten, inkl. neuester Infor-mationen über Schwachstellen und Abwehrmög-lichkeiten.
- Ziele auf einen hohen Automatisierungsgrad ab, um die Effizienz zu erhöhen und manuelle Eingrif-fe (und damit die Wahrscheinlichkeit menschli-chen Versagens) zu reduzieren.
- Nutze Zugriffs- und Sicherheitsanalysen, um bei Bedarf unerlaubte Zugriffe und Aktivitäten sofort zu erkennen und zu verhindern.
- Biete gezielten Einblick in den aktuellen Status durch auf Interessensgruppen zugeschnittene Be-richte, Management-Cockpits (Übersichtsseiten) und Administrationsschnittstellen.










































