Playlist
European Identity & Cloud Conference 2012
Keynotes and selected sessions from the European Identity & Cloud Conference 2012.
Please note that most of these videos are only available for the conference participants or users having a KuppingerCole Research subscription.
Show more
43 videos in this playlist
Event Recording
EIC 2012 Session: Database Firewalls - Advancing Security for Enterprise Data
May 16, 2012
Martin Kuppinger, KuppingerCole Dr. Steve Moyle, Oracle Sebastian Rohr, KuppingerCole April 19, 2012 16:30

Event Recording
EIC 2012 Session: Exchanging Metadata through Different Federations on a Global Scale
May 15, 2012
Nicole Harris, Head of Identity Management, JISC Advance April 19, 2012 15:40
Event Recording
EIC 2012 Session: Federation or Synchronization – the Future of the Cloud
May 15, 2012
Andrew Nash, Google Darran Rolls, SailPoint Travis Spencer, Ping Identity April 19, 2012 15:20

Event Recording
EIC 2012 Session: What Federation is About – in Theory and in Practice
May 15, 2012
Dave Kearns, KuppingerCole April 19, 2012 15:00

Event Recording
EIC 2012 Session: Security for Virtualized Environments, Privileged Users and PCI Compliance
May 15, 2012
Guy Balzam, CA Technologies Stephan Bohnengel, VMware Giovanni Ciminari, Telecom Italia April 19, 2012 14:30

Event Recording
EIC 2012 Session: From Virtualization to the Cloud and Beyond
May 15, 2012
Craig Burton, KuppingerCole Martin Kuppinger, KuppingerCole April 19, 2012 14:00
Event Recording
EIC 2012 Session: The Kuppingercole IT Model and the API Economy
May 14, 2012
Craig Burton, KuppingerCole Kim Cameron, Microsoft Martin Kuppinger, KuppingerCole Fulup Ar Foll, KuppingerCole Dr. Steven Willmott, 3Scale April 19, 2012 11:30

Event Recording
EIC 2012 Session: VRM and the Intention Economy - Now What?
May 14, 2012
Craig Burton, KuppingerCole Scott David, K&L Gates LLP Marcel van Galen, Qiy Drummond Reed, Connect.Me Doc Searls, Berkman Center for Internet and Society Phil Windley, Kynetx April 19, 2012 10:30
Event Recording
EIC 2012 Session: IT Strategies and Information Security in Banks - The Regulator´s View
May 11, 2012
Dr. Markus Held, Bundesanstalt für Finanzdienstleistungsaufsicht (BaFin) April 18, 2012 11:30

Event Recording
EIC 2012 Session: Access Governance Case Study - Friends Life Realizes Quick Time To Value
May 10, 2012
Julia Bernal, Group Business Security & Data Protection Manager, Friends Life April 18, 2012 17:30

Event Recording
EIC 2012 Session: Identity & Access Management as a Key Element for a Value focused Security Strategy
May 10, 2012
Ralf Knöringer, Atos IT Solutions and Services GmbH Hassan Maad, Evidian Shirief Nosseir, CA Technologies Christian Patrascu, Oracle Peter Weierich, iC Consult GmbH April 18, 2012 17:00
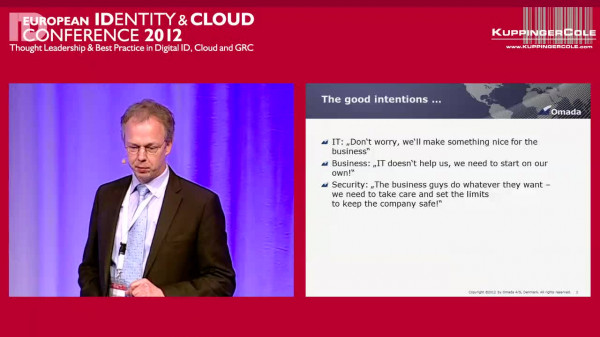
Event Recording
EIC 2012 Session: How to successfully get business to participate in IAM and Access Governance
May 10, 2012
Dr. Martin Kuhlmann, Omada Edwin van der Wal, Everett April 18, 2012 15:30
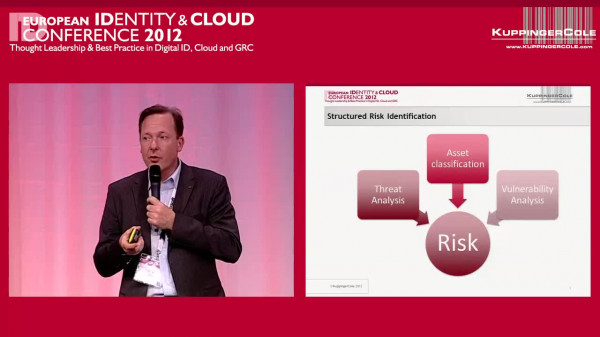
Event Recording
EIC 2012 Session: Delivering Actionable Recommendations to Senior Management based on a Structured Risk Identification and Evaluation Process
May 10, 2012
Dr. Waldemar Grudzien, Association of German Banks Berthold Kerl, Deutsche Bank AG Prof. Dr. Sachar Paulus, KuppingerCole April 18, 2012 15:00
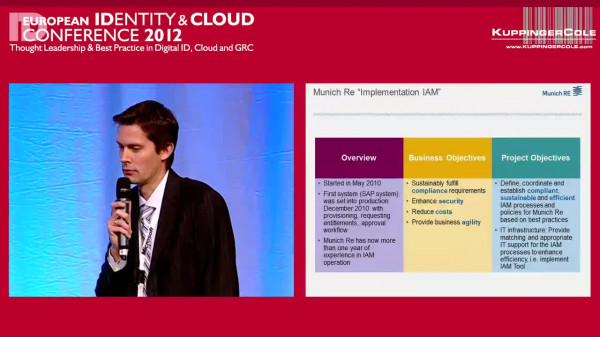
Event Recording
EIC 2012 Session: Munich Re’s Identity & Access Management - Experience Report and Best Practices
May 10, 2012
Wolfgang Zwerch, MunichRe April 18, 2012 14:30

Event Recording
EIC 2012 Session: IAM Governance in the New Commerzbank
May 10, 2012
Dirk Venzke, Director, Commerzbank AG April 18, 2012 14:00

Event Recording
EIC 2012 Session: How to Address Regulatory Needs Fast and Lean
May 10, 2012
Dr. Waldemar Grudzien, Association of German Banks Dirk Venzke, Commerzbank AG Dr. Horst Walther, Kuppinger Cole Wolfgang Zwerch, MunichRe April 18, 2012 12:00
Event Recording
EIC 2012 Session: Facing the Online Threats against Retail and Banking Customers - What are the Future Perspectives?
May 10, 2012
Prof. Dr. Sachar Paulus, Senior Analyst, KuppingerCole April 18, 2012 11:00
Event Recording
EIC 2012 Session: Cyber Crime, Cloud, Social Media... - IS Threats for Banks are Constantly Increasing. What Should We Be Doing?
May 10, 2012
Berthold Kerl, Deutsche Bank AG April 18, 2012 10:30
Event Recording
EIC 2012 Keynote: Interview - What are the Privacy and Information Security Challenges 2012 and Beyond?
May 05, 2012
Roy Adar, Vice President of Product Management, Cyber-Ark Dr. Nigel Cameron, CEO, Center for Policy on Emerging Technologies Martin Kuppinger, KuppingerCole Shirief Nosseir, Marketing Manager, CA Technologies Jim Taylor, VP Identity and Security Management, NetIQ April 17, 2012 15:40

Event Recording
EIC 2012 Keynote: Conflicting Visions of Cloud Identity
May 05, 2012
Kim Cameron, Creator of the Laws of Identity and Microsoft Identity Architect, Microsoft April 17, 2012 15:20

Event Recording
EIC 2012 Keynote: eID new challenges with Digital Agenda and Cloud Computing
May 05, 2012
Prof. Dr. Reinhard Posch, CIO for the Austrian Federal Government, Republic of Austria April 17, 2012 15:00

Event Recording
EIC 2012 Keynote: "Che cosa sono le nuvole?” (What are the clouds?)
May 05, 2012
Dr. Emilio Mordini, CEO, Centre for Science, Society and Citizenship CSSC April 17, 2012 14:40
Event Recording
EIC 2012 Opening Keynote
May 05, 2012
Dr. Nigel Cameron, CEO, Center for Policy on Emerging Technologies Martin Kuppinger, KuppingerCole April 17, 14:00
Event Recording
EIC 2012 Closing Keynote
May 03, 2012
Dave Kearns, Senior Analyst, KuppingerCole Prof. Dr. Sachar Paulus, Senior Analyst, KuppingerCole April 19, 2012 17:30
Event Recording
EIC 2012 Keynote: Trust and Complexity in Digital Space
May 03, 2012
Dr. Jacques Bus, Secretary General, Digital Enlightenment Forum April 19, 2012 9:30
Event Recording
EIC 2012 Keynote: The Future of Attribute-based Credentials and Partial Identities for a more Privacy Friendly Internet
May 03, 2012
Prof. Dr. Kai Rannenberg, T-Mobile Chair of Mobile Business & Multilateral Security, Goethe University in Frankfurt April 19, 2012 9:00

Event Recording
EIC 2012 Keynote: How Identity Management and Access Governance as a Service make your Cloud Work and your Business more Agile
May 03, 2012
Ralf Knöringer, Manager Business Unit IAM, Atos IT Solutions and Services GmbH April 19, 2012 8:30

Event Recording
EIC 2012 Keynote: How to build a Secure and Open Cloud
May 02, 2012
Stephan Bohnengel, Sr. Specialist Systems Engineer Security, VMware April 18, 2012 18:40
Event Recording
EIC 2012 Keynote: Top Challenges and Threats Security Managers Should Watch Out For
May 02, 2012
Prof. Dr. Eberhard von Faber, Security Strategy and Executive Consulting, T-Systems April 18, 2012 18:20

Event Recording
EIC 2012 Keynote: How Mobility Clouds the Future and SOA / Web 2.0 gives way to the Cloud API
May 02, 2012
André Durand, Founder & CEO, Ping Identity April 18, 2012 18:00
Event Recording
EIC 2012 Keynote: Information Security Governance in Banks: Delivering Actionable Recommendation to Management
May 02, 2012
Berthold Kerl, Managing Director, Head of Information & Technology Risk Governance, Deutsche Bank AG April 18, 2012 9:30
Event Recording
EIC 2012 Keynote: Securing Critical Banking Infrastructures in the Age of Cyber Warfare
May 02, 2012
Dr. Waldemar Grudzien, Director, Department Retail Banking and Banking Technology, Association of German Banks April 18, 2012 9:00
Event Recording
EIC 2012 Keynote: Leveraging Identity to Manage Enterprise Change and Complexity
May 02, 2012
Jim Taylor, VP Identity and Security Management, NetIQ April 18, 2012 8:30

Event Recording
EIC 2012 Keynote: Identity Management & Cloud Security - There’s a Workflow for That
May 01, 2012
Patrick Parker, Founder and CEO, The Dot Net Factory April 17, 2012 19:10

Event Recording
EIC 2012 Keynote: Scaling Identity, Access, and Audit Controls to Internet Proportions
May 01, 2012
Mike Neuenschwander, Sr. Director, Oracle April 17, 2012 18:50

Event Recording
EIC 2012 Keynote: Free Customers: The New Platform
May 01, 2012
Doc Searls, Berkman Fellow, Berkman Center for Internet and Society at Harvard University April 17, 2012 18:30

Event Recording
EIC 2012 Keynote: What About Bring your own Device?
May 01, 2012
Dr. Barbara Mandl, Senior Manager, Daimler AG April 17, 2012 18:10

Event Recording
EIC 2012 Keynote: How do Today’s Technology Challenges make Real IAM Possible?
May 01, 2012
Jonathan Sander, Director of IAM Business Development, Quest Software April 17, 2012 17:50
Event Recording
EIC 2012 Keynote: What Standards Have Done and Will Do for Cloud Identity
May 01, 2012
Dr. Laurent Liscia, Executive Director, OASIS April 17, 2012 17:30

Event Recording
EIC 2012 Keynote: Externalized Authorization - What is it Good for?
May 01, 2012
Peter Weierich, Senior Strategy Consultant, iC Consult GmbH April 17, 2012 17:10
Event Recording
EIC 2012 Keynote: Cloud, Consumerization & Identity: Time to Transform the Security Model
May 01, 2012
Shirief Nosseir, Marketing Manager, CA Technologies April 17, 2012 16:50

Event Recording
EIC 2012 Keynote: Ripped from the Headlines – The ‘Privileged’ Connection – Solved!
May 01, 2012
Roy Adar, Vice President of Product Management, Cyber-Ark April 17, 2012 16:30

Event Recording
European Identity Award 2012 Ceremony
Apr 26, 2012
The European Identity Awards 2012 honoring outstanding projects and initiatives in Identity Management, GRC (Governance, Risk Management and Compliance) and Cloud Security were presented yesterday by the analyst group KuppingerCole at their annual event, the European Identity Conference 2012 in Munich. Winners were chosen from a shortlist of exemplary projects and initiatives compiled by the analysts at KuppingerCole, end-user companies and vendors during the last 12 months.













































