Ensuring the availability of processes and services in the event of an incident or a cyber attack is a fundamental part of a company’s cybersecurity approach. Commonly used phrases when it comes to such cybersecurity strategies, are Incident Response Management (IRM) and Business Continuity Management (BCM). Both should be part of a company's cybersecurity strategy, but what is the difference, how are they connected, and at what point in time do they start?
Identification and prevention are fundamental
Every organization is under attack, and there is the risk of being hit by a major attack at any time. Therefore, it is important to have the necessary plans and strategies in place. And to to that, you first need to know where your most critical risks are. Figure 1 shows what this process usually looks like, and that IRM and BCM should start in the “Respond & Recover” phase.
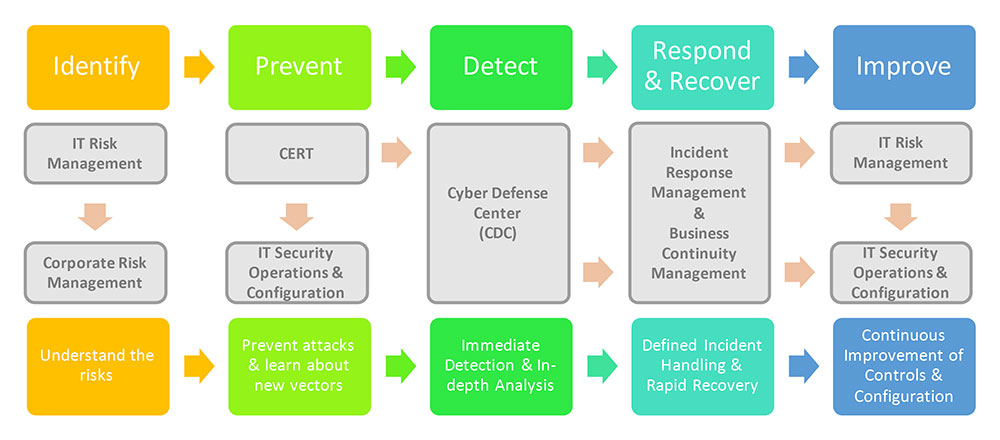
Figure 1: The integrated process for a company's cybersecurity approach
There are processes that are unique to the “Prevent” phase. A company’s IT Risk Management team should identify and rate risks in a global approach as part of the Corporate Risk Management process in order to understand the risks. Prevention mechanisms should be implemented by the IT Security Operations & Configuration team for the highly rated risks. Current threats that are shared by vendors or have been identified in actual breaches are typically fixed by the Computer Emergency Response Team (CERT), for instance, through the installation of patches or hotfixes. The goal in the prevention phase is to prevent attacks and continually learn about new vectors.
Detection could be made months after the attack
In the “Detection” phase, Cyber Defense Center (CDC) actively tracks current and older log files and orchestrates Information to detect potential attacks or data breaches that may have been missed by the mechanisms used by the CERT and IT Security Operations team. If the CDC detects an anomaly, they start an in-depth analysis. If an incident is verified, they hand it over to Incident Response Management and Business Continuity Management teams, where the “Respond & Recover” phase begins.
It is essential for a company to Respond & Recover after an attack
Incident Response Management’s first step is to rate the criticality of an incident and collect more details of the attack to inform further action. At this point in time two parallel streams jump into action: The Incident Response Management (IRM) and the Business Continuity Management (BCM) streams.
IRM is responsible for mitigating the effects of the attack. After the evaluation, a team of experts is usually formed to collect and evaluate further forensic details. Any affected systems are isolated, and in the event of data loss, these are evaluated, and recovery measures are initiated to return to normal operations. An important part of IRM is also internal and external communication. Especially in the case of a data breach, information must be forwarded to the relevant data protection supervisory authority, depending on the country.
Business Continuity Management, in turn, takes care of the continued availability of business functions in the event of a system failure or loss of data. In the case of a data breach, for example, this can be the provision of backups, which means the creation of regular backups as part of the BCM strategy is required. In case of a ransomware attack, alternative systems or devices can be provided or, in the worst case, business operations can even be switched to manual analog processes. BCM is always only a temporary measure for emergencies.
Use the knowledge after an attack to improve your security
To ensure that a company improves its security in the long term and that incidents with the same cause cannot recur, regular review and improvement after an incident is necessary.
What can a company do to sustainably improve security?
Clearly, a company must invest in a process for Incident Response Management and be prepared for an attack. If an incident occurs, it is too late to deal with “who is responsible for what” and “who needs to be informed”. The same applies to Business Continuity Management: once data is lost or no longer accessible, it is too late to worry about data backups or a plan B.
A good point to start could be KuppingerCole’s Master Class about Incident Response Management, which also covers some topics of Business Continuity Management. Meeting, networking, and discussing topics like BCM with peers will be possible at EIC 2020, May 12th to 15th, in Munich.
KuppingerCole is specialized in offering advisory services for cybersecurity, artificial intelligence, and identity and access management. If your company needs assistance finding the right toolset, architecture or what to focus on, KuppingerCole Analysts is happy to support you.
Related Research:

















































