1 Introduction
The KuppingerCole Leadership Compass provides an overview of vendors and their product or service offerings in a certain market segment. This Leadership compass focuses on the market segment of access governance, including specific capabilities for access intelligence. While most vendors offer either identity provisioning or access governance focused products, many others offer combined or separate products for both identity provisioning and access governance integrated into what is today frequently called IGA (Identity Governance and Administration).
From our interaction with organizations of varied IAM maturity across industry verticals, we note that while some are still looking for an identity provisioning solution with limited or no access governance capabilities, many others have emerging requirements for a promising and stand-alone access governance solution. As security leaders consider access governance to be an important part of their overall IAM strategy to build a robust identity analytics platform, we see a considerable shift in the product roadmap of IAM vendors to support access governance features and build better access intelligence capabilities. There’s an increased demand for access governance ‘only’ products in the market, especially from organizations that already have an identity provisioning tool in place or whose entry point for IAM is access governance. One of the more common adoption patterns we have observed in the market is where fulfillment through identity provisioning is achieved via a managed service, and access governance is run by and within the organization itself to retain an absolute control over governance functions. Several other adoption patterns for access governance products are witnessed in the industry, including where an organization’s primary requirement is better access governance for enhanced auditability and role governance.
Based on the adoption trends, changing customer priorities and deployment patterns, we decided to create three distinct Leadership Compass documents to help security leaders identify relevant IAM market segment and subsequently shortlist most appropriate technology vendors based on their immediate IAM priorities:
- LC Identity Provisioning: This Leadership Compass focuses on solutions with strong support for identity provisioning. While we expect some baseline access governance capabilities, they are not a necessary evaluation criterion. However, we also look at complete IGA offerings if they have strong identity provisioning support.
- LC Access Governance: This Leadership Compass focuses primarily on access governance and Intelligence capabilities, with required integrations into own or third-party entitlements and/or account repositories. We look at complete IGA offerings here too if they have strong access governance & Intelligence capabilities.
- LC Identity Governance and Administration: In this Leadership Compass, the primary focus is on the vendors that offer both identity provisioning and access governance capabilities, either as a common product or separate but integrable product components to deliver capabilities across the IGA spectrum.
These three LCs are complemented by two other Leadership Compass documents – LC IGA for SMBs (small and midsize businesses) that identifies and focuses on functional and operational IGA requirements of SMBs that are different in both objective and magnitude than large organizations. The other Leadership Compass is LC IAM Suites that focuses on comprehensive IAM suites and evaluates vendors for their completeness and functional depth of IAM portfolios to include core and even adjacent IAM capabilities such as Privilege Management, Enterprise SSO, Identity Federation, Web Access Management, API Gateways, Fraud Detection and Prevention etc. in addition to IGA as an integrated offering.
With these various LCs, we aim to provide CISOs and security leaders responsible for IAM the most practical and relevant information that they need to evaluate technology vendors based on the specific use-case requirements, whether these are IGA-driven, provisioning focused, governance focused, focused on comprehensive IAM suites or a combination of these.
1.1 Market Segment
Access Governance & Intelligence is an IAM focused risk management discipline that facilitates involvement of business in the overall management of access rights across an organization’s IT environment. Access governance provides necessary (mostly self-service) tools for business to manage workflows and access entitlements, run reports, access certification campaigns and SOD checks. Access intelligence refers to the layer above access governance that offers business-related insights to support effective decision making and potentially enhance access governance. Data analytics and machine learning techniques enable pattern recognition to deliver valuable intelligence for process optimization, role design, automated reviews and anomaly detection.
Access governance concerns the access mechanisms and their relationships across IT systems, and thus is instrumental in monitoring and mitigating access-related risks. These risks most commonly include information theft and identity fraud through unauthorized changes and/ or subversion of IT systems to facilitate illegal actions. Many prominent security incidents during the last few years originated from poorly managed identities and prove the need to address these issues across all industry verticals. Data thefts, loss of PII (Personal Identifiable Information), breach of customer’s privacy and industrial espionage are becoming common security risks in virtually every industry today.
Access Governance, an IAM focused risk management discipline, focuses on providing answers to three key questions:
- Who has access to what?
- Who has accessed what and why?
- Who has granted that access?
That is done via a set of functionalities, which include the following features:
- Access Warehouses: Collecting current and previous access information from different systems. The collection can be done via direct or extensible connectors using established standards such as HTTP or webservices. Provisioning connectors or flat file imports are commonly used for the purpose.
- Access Certification: Requiring the responsible persons (such as resource owners or application managers) to do scheduled or ad-hoc reviews of the current status of access controls and request changes if required.
- Access Analytics and Intelligence: Analytical capabilities to facilitate business-friendly understanding of the current status of access controls, sometimes complemented by adding real-time monitoring information about access to IT assets.
- Access Risk Management: Using a risk-based approach to evaluate and assign risk score for access requests and invoking relevant access workflows and notifications based on configured policies.
- Access Request Management: Providing interfaces to request access to specific information or systems including workflow policy configurations to define and manage request flows.
- SoD controls and enforcement: Definition and enforcement of business rules to identify and prevent Segregation of Duty risks.
- Enterprise Role Management: A complementary technology given that roles are the typical method used to manage access. Thus, Enterprise Role Management, including the capability of analyzing and defining roles, is mandatory.
Access governance is one of the key IAM technology for any organization due to the massive impact of potential security risks arising from lack of proper access governance controls. Access risks can have severe operational impact and can be derived from organizational-wide security risks – the Barings Bank incident and the Société Générale scandal being prominent examples of such risks that could have been prevented with appropriate access governance in place. There are several other access-related security risks in today’s organizations that have a direct impact on business, including but not limited to, intellectual property theft, occupational fraud in ERP systems including SOD conflicts and other policy violations, reputational damage due to the loss of customer information and privacy-related data, and many more. An adequate access governance framework is thus essential for the organizations dealing with constantly changing paradigm of security and risk management.
Access governance products focus on implementing and governing the controls for access management. This includes controls for attestation and recertification processes as well as auditing, reporting and monitoring capabilities which, in turn, invoke active management of preventive controls to identify and mitigate the access risks. Additional aspects are data analytics for pattern recognition to drive process automation, effective role management, anomaly detection and access simulation as part of access intelligence capabilities.
From KuppingerCole’s perspective, a complete access governance approach must go beyond the governance of “standard users” to include privileged users as well. Most access certification reviews today are conducted at application level. It is becoming increasingly important for organizations to have a consolidated view of a user’s access entitlements including access to privileged accounts. Conducting separate access certification campaigns for standard and privileged access can be complex and time consuming. While privileged users are pretty much the same as “standard” users from an access governance perspective, Privilege Management tools add features such as restricting elevation of rights at run-time and managing shared account passwords. Complete solutions would require tight integration between both groups of capabilities, to not only identify the risk in access governance but mitigate it by using specific Privilege Management capabilities. Some privilege management vendors are beginning to offer access governance features of their own, while most others offer integration with access governance tools to deliver a common access governance platform for standard and privileged users.
We also see the need for looking at advanced, integrated capabilities of managing access controls within the target systems such as SAP environments or Microsoft Windows File Server/Active Directory environments. Some vendors are moving in the direction of Entitlements and access governance (EAG)[^1] or Data access governance.
From a KuppingerCole view there is a need for specific tools to provide in-depth governance and management functionality under the integrated layer of CCM (Continuous Controls Monitoring) or IT GRC. While there is some functional overlap, we don’t expect the available GRC tools to deliver even basic capabilities to meet the access governance requirements of organizations. An integration with GRC tools, however, is a recommended approach for several reasons including gaining better visibility in the state of access-related compliance and feeding any regulatory changes into the access governance framework.
To summarize, we consider the following features as core elements of an access governance solution:
- Role Management to define, create and assign roles for users. Role management also includes role mining based on most relevant and efficient grouping of access entitlements. Advanced role management capabilities include pattern and risk analysis as well as role simulations for an efficient policy administration and effective provisioning.
- Attestation and Recertification as a continuous control activity which besides supporting periodic access attestation, allows organizations to detect modifications and invoke ad-hoc recertifications while continuing to analyze the status of access controls in a structured way.
- Auditing and Analysis features which support an after the fact view of access-related events and provide valuable intelligence for enhanced governance.
- Access Request Management as the standard interface for users to request access to IT assets from access catalogue and managers to review and approve the requests. Includes workflow and policy management to define and automate request flows, including automated reconciliation.
- Integrated privilege management features for extending these controls to privileged users, which aren’t typically covered by the standard access governance tools today.
- Support for EAG (Entitlement and access governance).
Over time, a deep integration with Dynamic Authorization Management Systems which are used to centrally define policies for application and system security is required as well. However, there are still few solutions in the market providing even minimal integration.
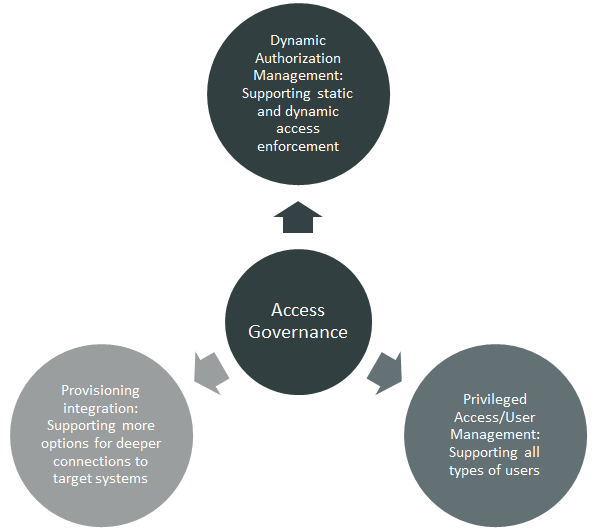
To achieve this, features for role management, policy management, rule definition and analysis, workflows as well as additional functionality are required. Dashboards for executives and extended auditing and reporting capabilities are a part of these tools. Risk management features are recommended but are not a standard feature of products in the market yet.
To connect with target systems, access governance tools should support different types of interfaces:
- Connectors to extract access control status information out of target systems, frequently using flat file exports;
- Interfaces to provisioning systems to use their access management features for active management and, in some cases, to extract access control status information;
- Direct connectors to target systems for changing access control information in these systems;
- Interfaces to Service Request Management (SRM) tools which are used to manually provide information to target systems;
- Workflows providing manual tasks to operators. The execution of these tasks should be automatically tracked by the analysis features of the product.
An increasing number of tools are now supporting these features or building on capabilities to support them. An in-depth analysis of architectural options for access governance is provided in the KuppingerCole Advisory Note