1 Introduction
The protection of various types of data used in business processes and stored in the underlying systems is becoming an essential challenge for a constantly growing number of companies. This is especially true when it comes to modern collaboration and data exchange platforms like SharePoint Online in multinational environments.
There are many reasons for this, such as the prevention of data breaches and their negative effects on the actual business, but also the reputation of a company. In view of the very real danger of industrial espionage by international competitors, but also by state actors of different origins, high-technology companies such as pharmaceutical companies, companies in the financial sector or companies in the defense sector in particular must achieve the highest level of protection and governance for sensitive data, such as intellectual property.
On 16 July 2020, the European Court of Justice ruled that the EU-US "Privacy Shield" is invalid (ECJ, Case C-311/18). This decision has once again highlighted the fact that for personal data, specifically for any data processed in the US, there is not sufficient protection against access by US security authorities NSA and FBI in the context of criminal prosecution and beyond.
A multitude of new data protection regulations have begun to influence companies worldwide more than ever before. In recent years, the EU-GDPR (European General Data Protection Regulation) was introduced with considerable attention, which raised the protection of personal data to a uniform and significantly higher level across Europe. But this is only one example of a worldwide development, whereby the GDPR is in many cases also used in part as a blueprint.
One of the more recent regulations in this series is the California Consumer Privacy Act (CCPA). The CCPA came into force on January 1, 2020 and raises the bar for the processing and sale of personal data for companies that do business in California but will have more far-reaching implications beyond the state of California. As early as 2013, Singapore passed the Personal Data Protection Act (PDPA), which includes regulations on how companies in Singapore can store and process personal data of individuals.
In addition, an increasing number of regulations include a data residency requirement, i.e. the obligation to store selected data within the respective country or regional borders. As a result, the transfer of personal data, for example, across national borders (e.g. for the EU, Russia, the United Arab Emirates, the UK, Switzerland or China) is not or not easily permitted.
These are just a few examples of regulatory requirements. The amount of internationally applicable laws and regulations is constantly growing. Without going into detail of similarities and differences between these regulations: there is a significant overlap, and while GDPR overall can be considered the strictest of these regulations, all of these privacy regulations come with fundamental changes to the way many businesses treat personal data today. Sanctions and remedies are substantial, so businesses should take action to comply, but also to adequately protect personal data and to avoid becoming a victim of a data breach.
Two additional factors add further complexity: First, many regulations have an extraterritorial scope. For example, the GDPR applies to all organizations within the EU member states and to all who do business with EU residents. Consequently, this also affects companies outside the EU. Therefore, it does not matter where the company is located, but where the individual lives and the business takes place.
Secondly, larger international companies potentially have to meet a multitude of regulatory requirements, some of which differ with or even contradict each other. Thus, these companies have to comply with a multitude of fragmented data residency requirements. This poses a challenge for corporate governance and regulatory compliance processes. However, it is also a substantial technological challenge that must be handled with a maximum level of security. Apart from all these requirements the usability for IT administrators and user-friendliness of the systems used must not be neglected.
In parallel, modern businesses across all verticals continue their rapid digitalization. The need to store, process and exchange data securely is an essential part of doing business for almost any company. At the same time, virtually all companies are reinventing their infrastructures in many application areas, opting to use cloud infrastructures. Cloud services offer many benefits, including the ability to meet changing demands and the flexibility to deliver new business solutions faster. This applies in particular to the critical areas of communication, all types of workflows, and the exchange of documents including collaboration, using systems like SharePoint Online as Software as a Service (SaaS).
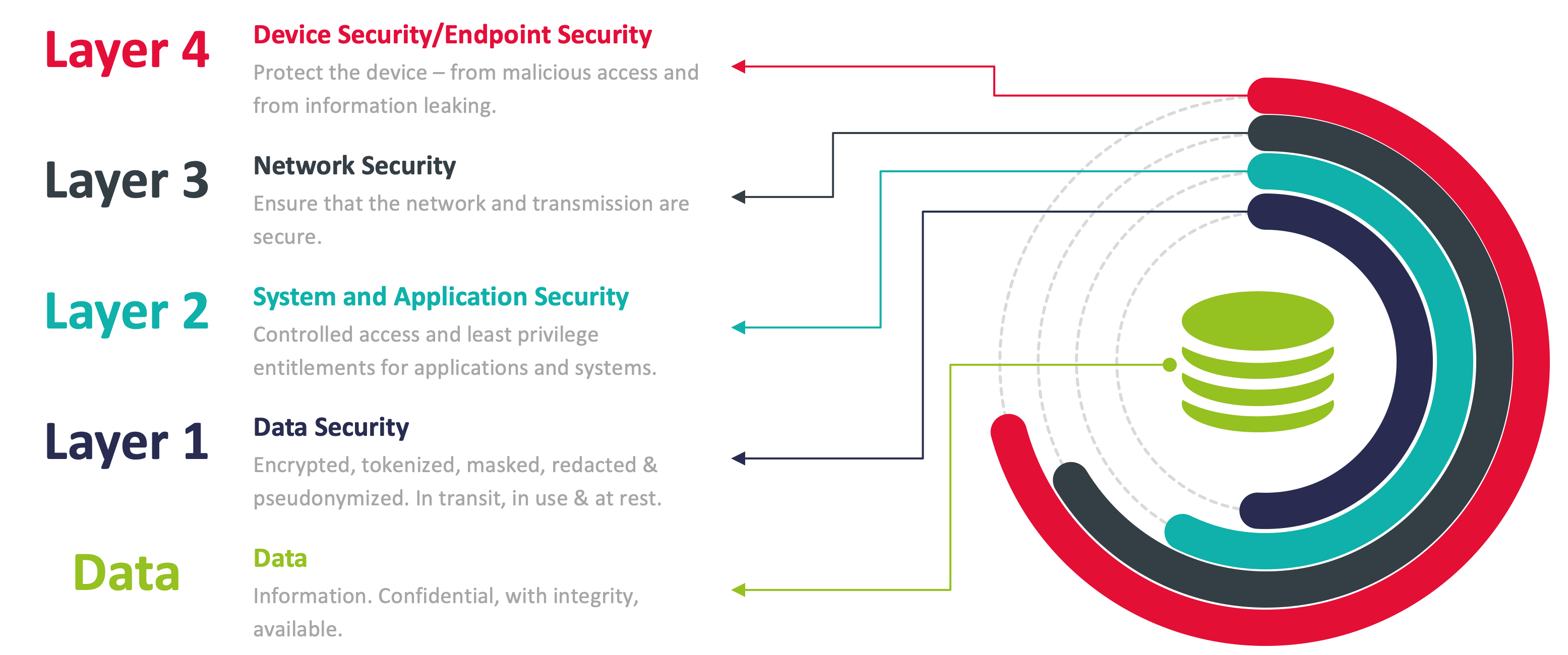
Traditional cybersecurity typically focuses on protecting networks, systems, applications, servers and endpoints in general. But platforms that are neither self-operated nor self-managed cannot be adequately protected. Instead, the focus is on protecting the data itself even in potentially insecure environments. Data-centric security focuses on the data objects and payloads rather than storage and transmission elements. Other tiers can be added as part of a multi-layered security approach that covers multiple dimensions of cybersecurity.
Key strategies for data-centric security include the avoidance/reduction of data in cloud systems, regulatory compliant localization of data storage, and encryption and/or obfuscation that ensures that data cannot be restored to its original form by unauthorized persons under any circumstances. Meeting the requirements imposed by national and multinational laws and regulations in the context of online collaboration and file sharing demands scalable, intelligent and secure solution approaches.