1 Introduction
Dynamic Authorization Management, sometimes called Entitlement Management, is a superset of the Policy-Based Access Control (PBAC) and Attribute-Based Access Control (ABAC) sectors which is a much needed area of Identity and Access Management (IAM) today. It is the way in which organizations can leverage their identity and access management environment to manage access to restricted resources and data.
Dynamic Authorization meets many of the demands seen by IT organizations today, such as the need to provide finer-grained access controls over data resources, or authorization of data for GDPR compliance purposes. Also, with more organizations exposing digital services over APIs, there is a growing need to externalize dynamic authorization to APIs across multiple platforms and to manage it in a centralized way to ensure compliance.
When role-based models of access controls are no longer sufficient to model the dynamic nature of user access, an ABAC model can be used, which is more flexible than RBAC and can even be used to emulate (and extend) RBAC. Although it is easy to express and maintain business policies using it, moving towards ABAC requires a new understanding of how to deal with authorizations, compared to the well understood RBAC approach. But it provides more flexibility and tighter integration with applications.
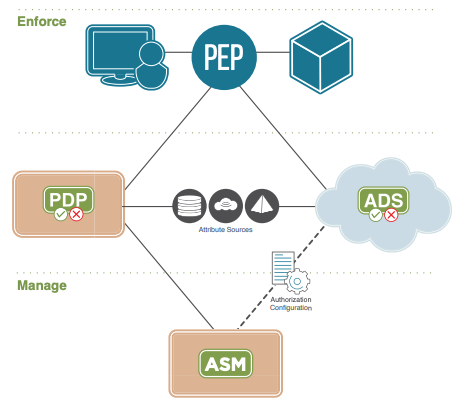
In a typical Dynamic Authorization Management infrastructure deployment, there are five main components:
Policy Decision Point (PDP) – a service that evaluates access requests against authorization policies and responds with a Permit, Deny Not applicable or Indeterminate decision
Policy Administration Point (PAP) – a facility to generate and modify policies
Policy Retrieval Point (PRP) – the location where policies are stored
Policy Information Point (PIP) –the data store of attributes by which decisions are made
Policy Enforcement Point (PEP) – a service that sends an access request to the PDP and enforces its decision.
Using this Dynamic Authorization Management model, access controls to APIs, microservices, and other application resources can now be made in real-time by policies in a centrally-managed “decision point” or PDP, using attributes such as a user id as a subject, a resource type to be accessed, allowed actions on a given resource, or an environmental context such as the time-of-day. The benefits are significant: authorization is externalized, access policies become centralized, and software development is simplified. By externalizing access control decisions, business management is improved, and costs are reduced.
Although when evaluating a dynamic authorization solution, there are a few things that should be considered in order to address some IT challenges:
- The authorization engine needs to be fast when evaluating the many access requests in a centralized manner.
- The solution needs to flexible enough to adapt to different applications or other solutions.
- They need have the ability to integrate with IAM, GRC, and other tools in a consistent way.