KuppingerCole's Advisory stands out due to our regular communication with vendors and key clients, providing us with in-depth insight into the issues and knowledge required to address real-world challenges.

Optimize your decision-making process with the most comprehensive and up-to-date market data available.
Compare solution offerings and follow predefined best practices or adapt them to the individual requirements of your company.
Configure your individual requirements to discover the ideal solution for your business.

Meet our team of analysts and advisors who are highly skilled and experienced professionals dedicated to helping you make informed decisions and achieve your goals.

Meet our business team committed to helping you achieve success. We understand that running a business can be challenging, but with the right team in your corner, anything is possible.
At Ping Identity, we believe in making digital experiences both secure and seamless for all users, without compromise. That's digital freedom. We let enterprises combine our best-in-class identity solutions with third-party services they already use to remove passwords, prevent fraud, support Zero Trust, or anything in between. This can be accomplished through a simple drag-and-drop canvas. That's why more than half of the Fortune 100 choose Ping Identity to protect digital interactions for their users while making experiences frictionless. Learn more at www.pingidentity.com. On August 23, 2023, Ping Identity and ForgeRock joined together to deliver more choice, deeper expertise, and a more complete identity solution for customers and partners.

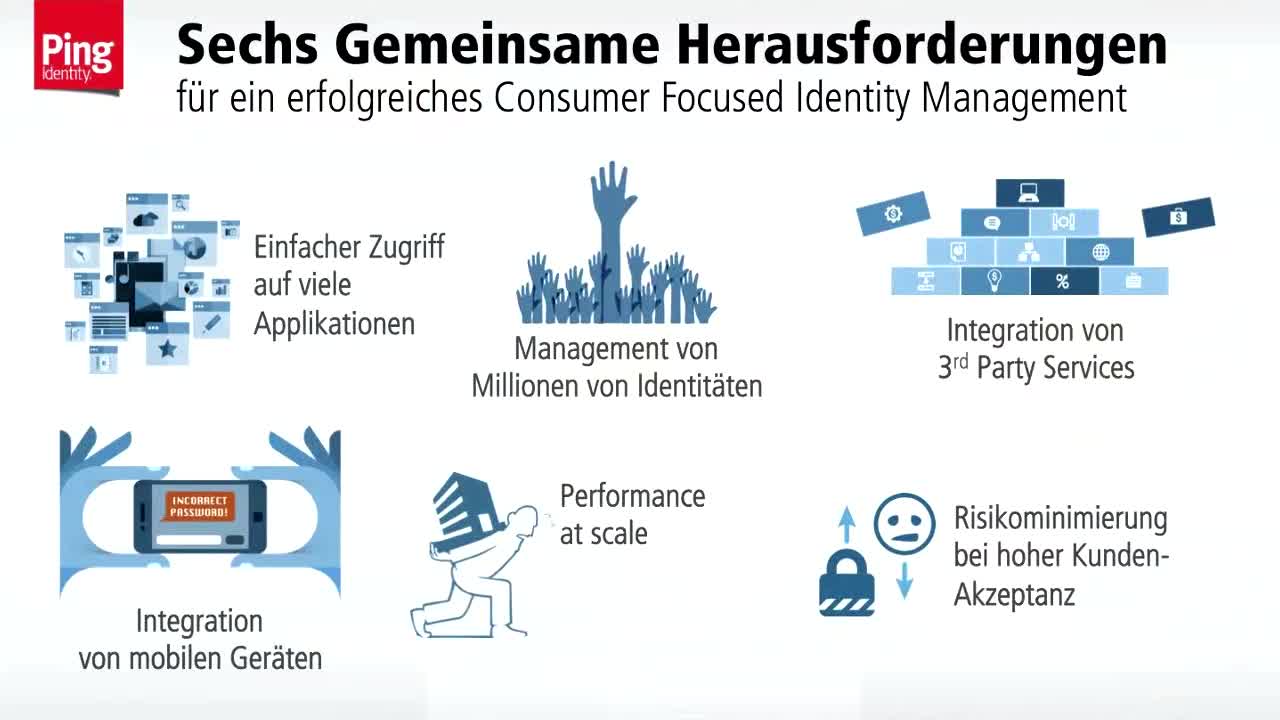
In an era defined by digital transformation, the landscape of identity and access management (IAM) is evolving at an unprecedented pace, posing both challenges and opportunities for organizations worldwide. This webinar serves as a comprehensive exploration of the current state of the identity industry, diving into key issues such as security, compliance, and customer experience. Modern technology offers innovative solutions to address the complexities of identity management.
Martin Kuppinger, Principal Analyst at KuppingerCole Analysts, will share his perspective on the state of the IAM/digital identity market, emphasizing major trends and the implications of the merger between Ping Identity and ForgeRock.
Andre Durand, CEO of Ping Identity, will highlight early product investments, strategic steps post-merger, and the vision for the future. Drawing upon real-world examples showcased at global customer roadshows, he'll outline the trajectory of identity management and the integration of cutting-edge technologies like AI.
Join this webinar to:

Join identity experts from KuppingerCole Analysts and Ping Identity as they unpack the role of decentralized identity in reusable identity verification and credentialing. This session will look at two specific business cases where decentralized identity is reducing fraud while improving user experiences and providing monetization opportunities for issuers.
Anne Bailey, Senior Analyst at KuppingerCole Analysts, will explain the trajectory of decentralized identity, how it supports reusability, and how that unlocks efficiencies for organizations in both customer journeys and verifying its workforce.
Darrell Geusz, Product Lead for PingOneNeo at Ping Identity, will share use cases of real-world customers who leverage identity verification and digital credentialing. He will dive into how they achieve safer, more secure, more affordable, and privacy-enhancing processes for customers and the workforce, through utilizing a trusted first party experience for every transaction.
Join this webinar to learn about:

Success in digital business depends largely on meeting customers’ ever-increasing expectations of convenience and security at every touchpoint. Finding the best strategy to achieve the optimal balance between security and convenience without compromising on either is crucial, but can be challenging.

Verifying what specific applications, files, and data that a human or non-human entity has access to, is at the heart of cybersecurity in the face of increasing theft of data for espionage or other criminal purposes. Authorization, therefore, is extremely important to security, but it is also key to boosting brand trust and improving user experience. Join security experts from KuppingerCole Analysts and Ping Identity as they discuss the challenges of authorization in modern IT environments, market trends and changes, and how a modern approach to authorization can address the challenges, including how to cater for consumers and other external parties.
Osman Celik, Research Analyst at KuppingerCole will look at the business and security benefits of moving to policy-based access controls (PBAC), how this supports a Zero Trust approach to security, and how PBAC can be practical and scalable in hybrid and multi-cloud IT environments.Adam Rusbridge, Senior Product Manager at Ping Identity will highlight the main authorization use cases that are driving change in enterprise architecture teams. He/She will also share recommendations on how organizations can improve security, enhance brand trust, and deliver better user experiences.

Business success in the digital era depends on delivering seamless and secure customer experiences. Failure to do so can easily result in abandoned shopping carts, fraudulent transactions, and regulatory fines. However, delivering exceptional experiences and keeping pace with the speed of business is challenging.

Consumer Identity & Access Management (CIAM) is about managing access to customer-facing systems. While organizations have typically focused on using CIAM to collect, store, and analyze consumer data to create sales opportunities and inspire brand loyalty, other potential business benefits are being overlooked.

In a single decade, Application Programming Interfaces (APIs) have evolved from a purely technical concept into one of the foundations of modern digital business, delivering operational efficiency, scalability and profitability to companies from various industries. Nowadays, everything is API-enabled: corporate data is the product and APIs are the logistics of delivering it to customers and partners.
From May 2018 when the upcoming EU GDPR (General Data Protection Regulation) comes into force, the requirements for managing personal data will change. Companies collecting such information from their customers will have to adapt to fundamental changes both in the very definition of personal data and in technical requirements around its secure and privacy-enhanced processing, including topics like consent management, data portability and the right to be forgotten. The scope of this regulation is very broad and it affects all organizations, including global enterprises outside of the EU, that collect, hold or process personal data on EU residents. The requirements for maintaining consumers’ privacy are significantly more stringent through this new framework and the fines for compliance violations have been increased accordingly, reaching up to 4% of the company’s annual worldwide turnover. With less than 12 months to go, is your organization ready to comply with these requirements that demand better controls over how it uses and manages the personal data that it holds?

PSD2 and the Open Banking Standard are regulatory mandates being applied to the banking industry by the European Banking Authority (EBA) and Competition & Markets Authority (CMA) across Europe and in the UK respectively. The regulations require that banks operating across the region expose open APIs to allow other banks and third parties to access the data they hold on customers, when the customer has given their explicit consent. Designed to improve choice for customers, create more competition and stimulate innovation in the finance sector, the introduction of 'open banking' in the UK and across the EU will transform banking as we know it.

Many large enterprises operate with a glut of access security platforms and tools that each service a specific silo of applications and resources. Most are proprietary, and many have expensive and time-consuming agent-based architectures. In addition, because they are usually very tightly connected to the applications, it is a hard task to move them to the cloud or access them remotely. Traditional IAM systems were simply not designed to secure apps outside the corporate firewalls.
Modern access management supports secure online access from any device via one single sign-on (SSO) solution. It doesn’t matter if applications are being deployed either on-premises, in a private or in a public cloud, thanks to a centralized and federated gateway the level of control always remains the same. It also enables developers to work with latest identity standards such as OAuth and OpenID Connect in order to support identity for multiple clouds and mobile environments in various combinations. And all of this, thanks to easy integration, without companies having to alter their existing IT infrastructures.