Insights
Research
Advisory
Events
Videos
KC Open Select
Company
KuppingerCole's Advisory stands out due to our regular communication with vendors and key clients, providing us with in-depth insight into the issues and knowledge required to address real-world challenges.

Optimize your decision-making process with the most comprehensive and up-to-date market data available.
Compare solution offerings and follow predefined best practices or adapt them to the individual requirements of your company.
Configure your individual requirements to discover the ideal solution for your business.

Meet our team of analysts and advisors who are highly skilled and experienced professionals dedicated to helping you make informed decisions and achieve your goals.

Meet our business team committed to helping you achieve success. We understand that running a business can be challenging, but with the right team in your corner, anything is possible.
Radiant Logic, the market leader for unified identity solutions, provides the cornerstone for complex identity architectures in today’s digital world. Radiant delivers a single source of identity truth, connecting many disparate data sources across legacy and cloud infrastructures. Our solution creates a solid identity foundation that speeds the success of initiatives, including single sign-on, M&A integrations, identity governance and administration, cloud directory deployments, and hybrid/multi-cloud environments. From the Fortune 1000 to the public sector, global organizations rely on Radiant to deliver meaningfully faster time-to-value, while building a secure, future-proof identity infrastructure that meets real-world business demands.

Cloud computing and mobile workforces have resulted in an expanding attack surface and a complex web of identify information. This means that traditional perimeter-based security models are no longer effective. A Zero Trust model of strict access control for every user and device enables businesses to be connected and secure, but an effective identity-focused approach is essential.
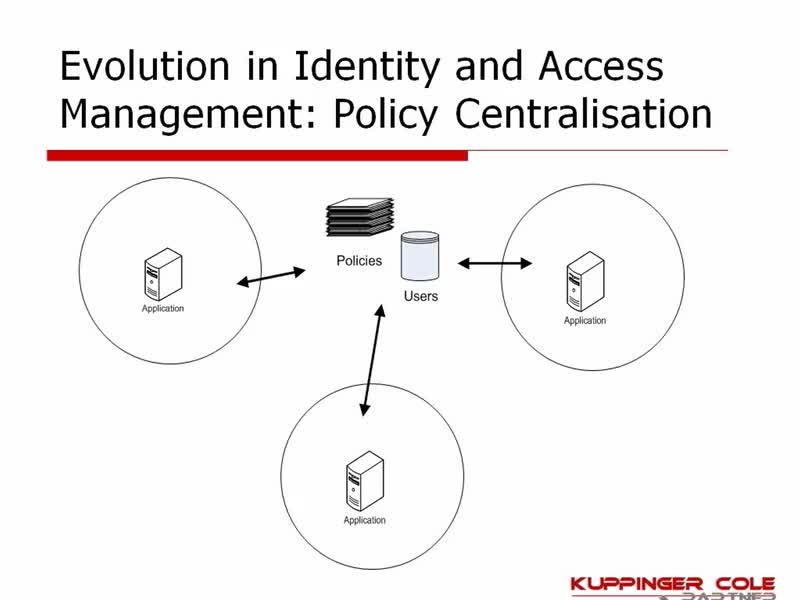
Identity sprawl is a challenge facing most modern enterprises as a result of inorganic growth, piecemeal identity solutions, and more recently, a loss of control due to unplanned remote work. This sprawl leads to tremendous technical debt and has turned identity and access management into a roadblock for many organizations.