What Is a Decentralized Identity?
At its most basic, decentralized Identity is about giving the control of your data back to you with a digital identity.
Usually your data (sometimes called attributes, identifiers, and credentials, for example your birth date) are stored in a centralized location If you make an account on a company website, the data is likely stored by the company. You don’t hold your information and therefore you have less control over it.
So How Does Decentralized Identity Give the Data and Control Back to You?
Decentralized Identity stores your data in a digital format that cannot be tampered with, duplicated, or stolen. The storage of your data is designed to be controlled only by you so you can choose to share the minimum amount of information with a service provider (let’s take the example of a a car rental agency, where you are trying to reserve a rental car online). The identity is cryptographically secured and cannot be tampered with.
You show the car rental agency (service provider) the necessary information to rent a car. The company can have access to that information for a certain defined period of time, but you also have the control to revoke your information afterward the transaction.
Some important players in a decentralized identity ecosystem are the issuer and the verifier. The issuer is a third-party organization that issues you a credential (for example, a government authority that issues you a driver’s license, or a university that issues you your degree). The verifier is the third party that you are trying to interact with (for example, the car rental agency that needs proof that you are eligible to drive a car). Both the issuer and verifier are decoupled from your identity, meaning that the issuer does not hold your digital credential, nor does the verifier. You are the one holding your decentralized identity.

Why Decentralized Identity Is Important
Decentralized identity is a small part of a larger topic – digital identity, which is an essential way to respond to the changing world where many services are shifting online or to digital formats. This changes the way we apply our identity to access services, or to interact in our places of work.
It’s now quite common to create an account to access a service like joining a social media platform, to purchase train or plane tickets more quickly, to manage your bank accounts, to access health services… the list goes on.
For some of these services, we only need to present a few identifiers, like your name, date of birth (DOB), and email. For others, identifiers must be verified to a certain level of assurance to make sure you are who you say you are: your driver’s license, passport, tax ID number, etc.
The question is, how do we share an identity document like a passport or driver’s license digitally?
Scanning a picture of your passport and sending it as an email attachment is a terrible idea – both for your privacy, and for whoever is on the other end processing it. You have just replicated information that should be kept out of the public eye, and now it sits in multiple places: on your desktop, in the email server, and in the files of whoever you’ve sent it to.
And the receiver now has to figure out if what you’ve sent them is really valid. Is it fraudulent? Has it been tampered with? Is that document even of you?
They have none of the benefits of examining the passport in person to check the holograms, or have it in a digital-friendly format to check any embedded biometric information.
There certainly are better ways of shifting to using and sharing digital identities, which is the reason a digital identity is really necessary.
Decentralized identity works solve the need for digital identity by providing a way to build trust in digital identity through the way it is issued, stored, and exchanged.
Decentralized Identity Benefits
There are three primary benefits for Decentralized Identity with many more possibilities.
Privacy
Decentralized Identity enables you to keep your information with you safely in a “wallet” that you hold, usually in your mobile phone. The concept of holding and having control over access to your identity information is sometimes referred as “Self-Sovereign-Identity” (SSI). More privacy benefits include being able to only share portions of your identity data, such as the fact that you are over 18 without actually sharing the exact date of birth. This supports privacy principles like data minimization.
User Experience
The user experience of signing up for a new service could tremendously benefit from Decentralized Identity solutions. Often when signing up for a new service, you need to fill in the same information about yourself: name, email, phone number, and so on. When the user holds their decentralized identity credentials in their own wallet, they could share the information needed by the service provider in a format that is trusted and readable (saving all that time typing and filling in registration forms). This is a work in progress – decentralized solutions are increasing the number of service providers that could issue and accept them, but there must be a more widespread interoperability for this technology first before you can expect it everywhere.
Digital identity portability
Another, perhaps futuristic, benefit of decentralized identity is the ability to move your information (and eventually your content) at will. Currently, if a blogger or social media influencer posts content and builds a following on one site, it is impossible to bring your content (and following) to another platform – you would have to do the hard work of building up your reputation all over again. But holding your digital identity under your own control is the first step towards enabling your content, following, reputation, and much more to be held under your control. As interoperability between different decentralized identity providers increases, the portablility of your decentralized identity (and in the future of digital assets) becomes more of a reality.
Where Is the Blockchain?
Decentralized identity functions uniquely because it is supported by a blockchain or other decentralized ledger.
But before we start talking about the blockchain, you should know the different actors that interact with a decentralized identity.
The Players
You: Hopefully you know who you are. You are a person (or a device, that’s okay too) with unique attributes that make up your identity.
As soon as the decentralized identity scheme kicks off, you are the holder of your identity credentials, which you typically keep in your digital wallet on a smart device.
An issuer: Comparable to an identity provider (IdP), which issues a credential describing you.
It could be your employment credential, your driver’s license credential, or an academic credential like a master’s degree.
The issuer is the entity that is responsible for that credential, thus would be your employer, a DMV, or your academic institution.
A Credential: This is a claim that an issuer makes about you (the DMV claims that you have earned your driver’s license).
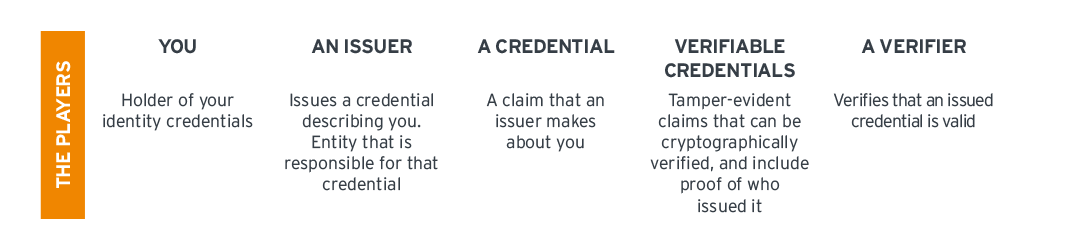
You’ll often hear about verifiable credentials, which are tamper-evident claims that can be cryptographically verified, and include proof of who issued it.
These can contain a decentralized identifier (DID), which is globally unique, cryptographically verifiable, and resolvable with high availability.
These cryptographic pieces are what are anchored to a blockchain, or other decentralized ledger.
Both Verifiable Credentials and DIDs are important standards that are shaping decentralized identity.
A Verifier: This entity is one that verifies that an issued credential is valid. But it makes more sense when it’s put into a scenario.
You present your employment credential to access an app you use every day for work.
That service provider verifies that the credential is valid, and you are granted access.
That service provider is the verifier, like a car rental agency is the verifier when you present your driver’s license credential to rent a car, etc.
Decentralized Ledgers
Decentralized ledgers are critical to delivering decentralized identity.
Blockchains are part of that, but so are blockchain variants like consortiums or sidechains, and “blockchain-like” architectures like directed acyclic graphs.
It helps to know a bit about why blockchains can be trusted to fully appreciate why decentralized identity can work. If you want to read more, go here.
Decentralized Identity Model vs. Traditional Identity Management
Here we look at the progression of IAM from centralization to decentralization and unpack some of the pain points along the way.
Later as we get into decentralization, CIAM becomes more relevant, handling the processes to issue and manage customer identities.
Centralized Identity Management
Creation, storage, and management was originally handled centrally by service providers or identity providers (IdPs), the organization issuing credentials to employees.
This means that a company’s servers holds the identity information, while each individual employee is issued a key to access the resources they need.
The storage is centralized and control is centralized, with the user being dependent on the decisions of the IdP.
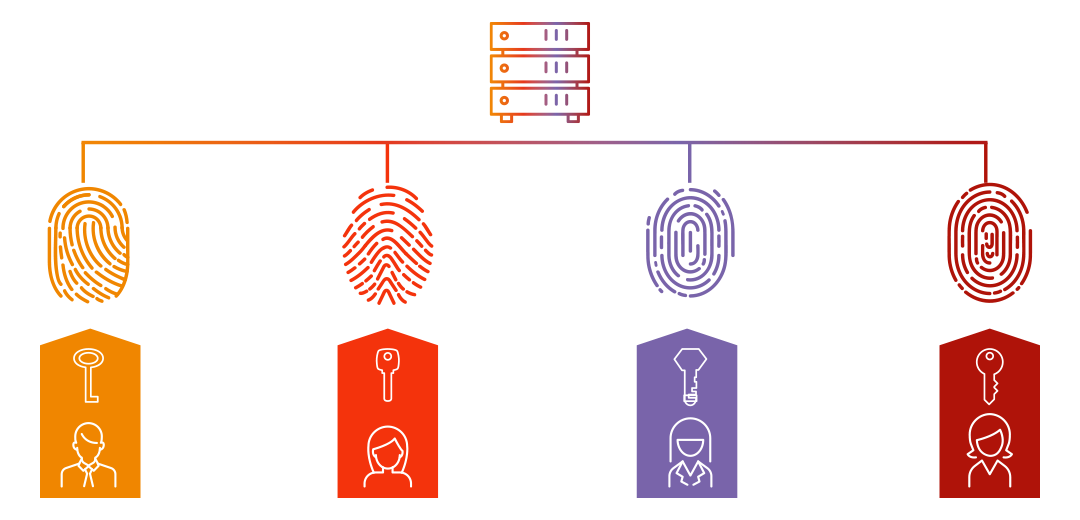
One of the downsides is that each IdP becomes a “silo”, an isolated, unconnected storage of information that cannot be efficiently used anywhere else.
It’s also a security hazard, since a data breach here would compromise all of the identities it contains.
Federated Identity Management
There are challenges in a centralized model in using one organization’s credential in another context (for example, if you the employee are hired as a contractor in another organization).
To ease the processes of checking the identity credentials issued by another organization, the federated identity model came on the scene.
This is where trusted partners establish a pathway for identity credentials to be accepted. This is centralization, but with a hub and spoke model.
Here, identities are stored and managed by the IdP, but multiple organizations and service providers can accept it.
CIAM and the Push for User Experience
Challenges still remain with federated identity models.
As CIAM enters the picture and identities are created for customers as well as employees, ease of use sometimes outweighs security.
Logging into an account with your social media or email account is an example of federation, intensifying the impact of a data breach on such a data silo; if your email is compromised, countless other accounts are also compromised because they are all connected.
There are of course other challenges, and if you want to read more about the privacy, security, and interoperability challenges, go here.
The Alternative? Decentralized Identity
Decentralized identities are using a different model entirely.
Instead of placing the organization in the center, the individual is the one holding their own identity credentials.
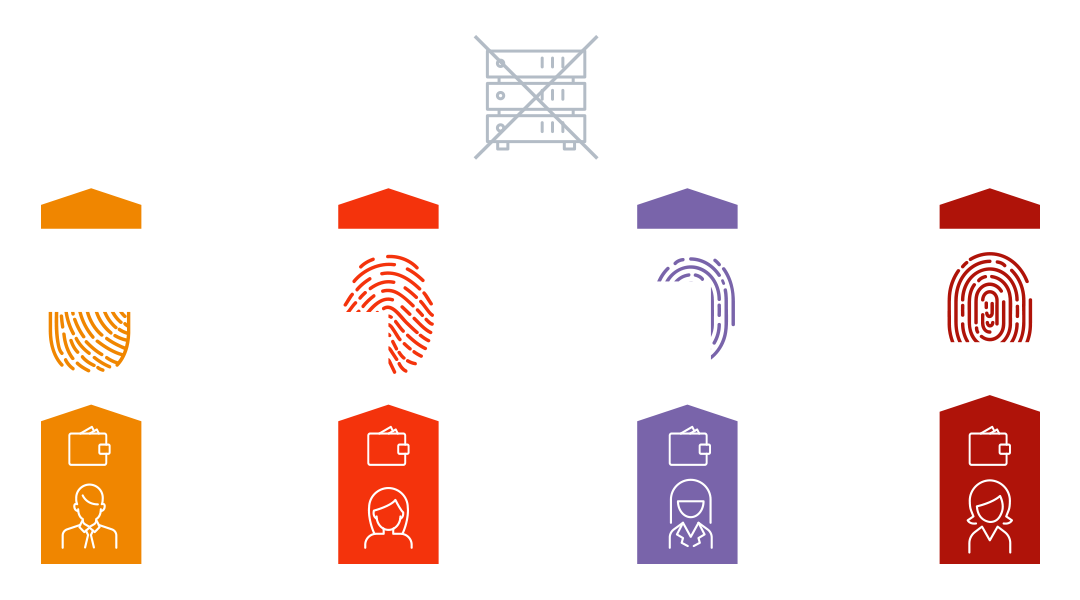
There is no data silo, meaning no location where all identities for all users and employees are stored. Instead, when the user wants to access a service, they present the credentials which they own and hold to the organization to approve.
Information is shared on a need-to-know basis, eliminating the problem of your personal information being held by all service providers that you come in contact with.
A key architectural piece here is the user wallet.
This is the digital app that holds the private keys to control the digital identities being stored there.
If you want to know more about these, go here.
So in short, traditional identity management models but the organization at the center – they hold all identity data.
Decentralized identity models put the user at the center.
Roadblocks and Concerns on the Way to a Decentralized Ecosystem
Decentralized identity sounds good, and is definitely offering improvements for the user and customer side of identity management.
So why is it not mainstream yet?
Despite the benefits, there are still challenges to overcome. Read on for an overview and to see how these are being addressed.
Some Challenges to Overcome
First, the roadblocks. Organizations trust in order to shift from a traditional identity management to a decentralized identity solution.
They need to trust the identities that individuals and employees bring with them are valid, to be willing to test and explore solutions using DIDs and Verifiable Credentials.
Watch the recoding of Annie Bailey's presentation from the KCLive Event Unlocking Decentralized Identity to learn more about future requirements of identity.
And most importantly, they need a way to make these external, decentralized identities interoperable with their current systems, and to enable access management polices to work with them.
Revocation of credentials is a challenge, but is one that is being solved.
Scalability is an ongoing conversation, and each vendor is addressing this challenge differently.
A large challenge for organizations is that because decentralized identities are user-centric, adoption may also be driven by individual user choices to manage their identity differently.
That leads to a slow transition from traditional identity management to decentralized, and the need to balance differing systems.
Vendors are designing solutions that interoperate with directories and authentication sources, so to find out more about removing this roadblock go here.
Other roadblocks that are being solved include using the decentralized identity offline, synchronizing an identity wallet across a user’s many devices, and options for data recovery if a user’s device is lost or stolen.
Most vendors have addressed these challenges in some way, so go here to see how these roadblocks are being addressed.
How Does Privacy Fit In?
Early in the blockchain days there were severe privacy concerns about PII and private information being written to the blockchain.
Because as you know, anything written to the blockchain cannot be removed and PII data stored there would be a severe breach of the GDPR and other privacy regulations.
This is being addressed through a series of privacy-protecting steps.
Decentralized Identifiers (DIDs), often written to a blockchain or decentralized ledger, become a mediating step between the private identity information and private keys stored on the user’s device.
The public key is stored in the DID document to facilitate the exchange of information in peer-to-peer communications channels.
No private information should be stored in the DID document, since this is one of the aspects that is stored on the blockchain/decentralized ledger.
In this way, a foundational piece of the private information is stored on the immutable, tamper-proof ledger (the public key), ensuring and proving that the private data it corresponds to has not been changed without ever writing the identity information itself to the blockchain.
Verifiable Credentials support this in a similar way, proving that the identity information has been verified by an authoritative entity without storing that particular identity information in the blockchain.
This is standard now for most decentralized identity solutions, in proving GDPR compliance, such as who the data controller is.
Anne Bailey and Matthias Reinwarth take on Verified Digital Identity in an episode of the Analyst Chat podcast. Listen in and explore what these are, why they are becoming increasingly important and where they add new aspects to the concept of digital identity.
The advancement of technology means that solutions that are currently available – like decentralized identity – are a few steps ahead of the current legal conversation surrounding data privacy, and are thus misaligned with the requirements of some privacy regulations.
Consider the Uses
Ethical concerns exist as well. In the early blockchain days, mining bitcoin was and still is a huge environmental cost, using massive amounts of electricity.
Decentralized identity typically uses different consensus mechanisms and ledgers to sidestep this problem.
More closely related to decentralized identity are immunization passports, or Verifiable Credentials that prove and individual’s COVID-19 immunization status to access services, such as international travel, entrance to conferences, and much more.
There are concerns that this can create preference for those how are immunized, and may unethically par individuals from accessing services that they are entitled to.
This question does not have decentralized identity at its foundation, but rather social equality and is a question of governing the tools that we do have.
Listen to Anne Bailey and Matthias Reinwarth discussing how decentralized identities and verifiable credentials help respond to the pandemic by powering contact tracing applications, immunity passports and other important use cases in their episode of the Analyst Chat Podcast.
Industries and Use Cases: Where Does Decentralized Identity Shine?
Proof of concepts and first customer experiences are demonstrating the many ways that decentralized identity can offer optimizations, savings, and advantages for security and privacy.
Enabling Employee-Owned Identities
Employee Onboarding, Authentication, Access Management: Verifiable Credentials for identification documents, diplomas, and more can be accepted by enterprises for new employee onboarding, making remote onboarding possible.
The enterprise can then issue Verifiable Credentials to the new hire for use within the company: an employee ID, as belonging to a particular department, etc.
These can be used as a form of authentication and as credential-based access control.
Integrations with systems like SAML and LDAP enable decentralized identity to become part of the traditional IAM structure.
Employee Mobility: During the height of the COVID-19 crisis, hospitals were hard-pressed to have enough staff in the right locations to keep up with spikes in COVID cases.
Decentralized identity solutions enabled health staff to carry their employment credentials, qualifications, and access rights with them on their smartphone in the form of Verifiable Credentials. This allowed a nurse to be quickly transferred to another hospital in another city, and for that nurse to prove that she was not an imposter without brining mountains of paperwork and sloughing through bureaucratic processes when time was of the essence.
Identities Held and Managed by the Individual
Digital Citizenship and Access to Government Services: Decentralized identity solutions are being used by governments to issue citizens Verifiable Credentials that allow them to present and prove their identity, citizenship, tax-ID number, and more in order to access government services and exchange these credentials in the private sector quickly, privately, and digitally.
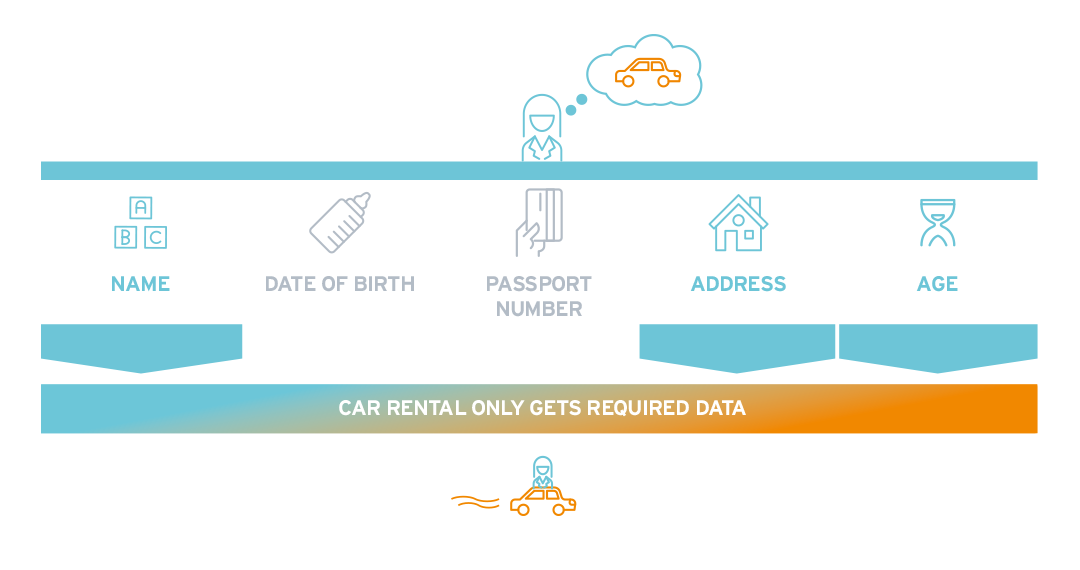
New User Onboarding: At the moment, most users have far more accounts with many different service providers than they can securely manage.
Decentralized identity brings so many security and privacy advantages to the user in opening and managing accounts with the many service providers that they interact with, but also for the organization to offer a great user experience (no more filling out registration forms) and relieves the pressure of enterprises storing user data.
Selectively sharing identity attributes: This is data minimization in action.
A user can share only the identity attributes that are needed for a transaction.
If a user must be over a certain age to rent a car, the user doesn’t have to share their birth date.
They can show a “zero-knowledge proof” that they are above the required age.
Users no longer have to overshare their data, and service providers no longer have to hold data that may not be compliant with data minimization requirements.
Market Overview
This is a very dynamic market space. Get to know some of the vendors who initially rocked the boat and those who are leading the charge in decentralized identity.
There have already been a lot of vendors who have come and gone from this space, but some of the first movers who remain are Evernym, Consensys Mesh, and SecureKey Technologies.
Where the Action Is
The approach to delivering decentralized identity has changed in the years since.
Rather than leading with the buzzword concepts of self-sovereign identity and blockchain, vendors have put significant effort towards interoperability between decentralized identity solutions (becoming blockchain agnostic, accepting credentials from other decentralized ecosystems) and for use in enterprise systems (support for standard authentication sources such as OpenID Connect and SAML, and for use in standard directory systems like Azure AD, Active Directory, LDAP, and more).
Thus the aim is centered on fulfilling the use case of delivering a verifiable, portable identity.
The fact that the solution uses blockchain or other decentralized ledger technology, and supports self-sovereign concepts becomes a side story.
These vendors are a combination of startups and of more familiar players like 1Kosmos, esatus, Microsoft, and Ping Identity.
Deploying Decentralized Identity: What to Do and Where to Start
Decentralized identity projects can seem overwhelming, especially knowing where to start.
But there is plenty you can do to start your decentralized identity journey as an enterprise.
Hybrid Security Buyers’ Guide
We have a few recommendations on how to get started with decentralized identity.
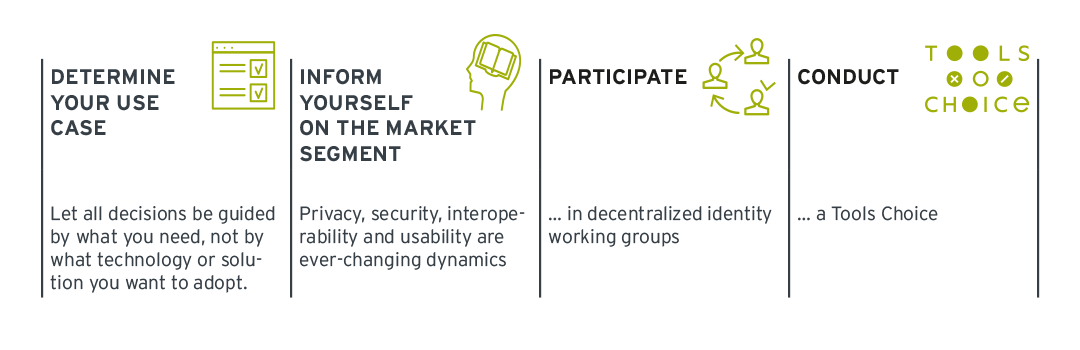
- Determine your use case: Let all decisions be guided by what you need, not by what technology or solution you want to adopt. Once it is clear what is needed in your organization, be it authentication solutions, onboarding procedures, verification, or any of the other compelling use cases, then you can really start to consider if a decentralized identity solution is a good fit.
- Inform yourself on the market segment: Privacy, security, interoperability and usability are ever-changing dynamics in the decentralized identity space. Stay current on these topics and critically ask how they impact your use case.
- Participate in decentralized identity working groups: When you’re interested in getting up close and personal with decentralized identity, join one of the many working groups as an observer or participant in developing open standards and shaping the conversation surrounding decentralized identity.
- Conduct a Tools Choice: When you’re really ready to pursue a decentralized identity solution, follow a structured process to determine a longlist, shortlist, request for information, proof of concept, and eventually decide on the vendor and solution that best fits your use case. You can find more information about that here.
















































