Insights
Research
Advisory
Events
Videos
KC Open Select
Company
KuppingerCole's Advisory stands out due to our regular communication with vendors and key clients, providing us with in-depth insight into the issues and knowledge required to address real-world challenges.

Optimize your decision-making process with the most comprehensive and up-to-date market data available.
Compare solution offerings and follow predefined best practices or adapt them to the individual requirements of your company.
Configure your individual requirements to discover the ideal solution for your business.

Meet our team of analysts and advisors who are highly skilled and experienced professionals dedicated to helping you make informed decisions and achieve your goals.

Meet our business team committed to helping you achieve success. We understand that running a business can be challenging, but with the right team in your corner, anything is possible.
Delinea is a leading provider of Privileged Access Management (PAM) solutions for the modern, hybrid enterprise. The Delinea Platform seamlessly extends PAM by providing authorization for all identities, controlling access to an organization’s most critical hybrid cloud infrastructure and sensitive data to help reduce risk, ensure compliance, and simplify security. Delinea removes complexity and defines the boundaries of access for thousands of customers worldwide. Our customers range from small businesses to the world's largest financial institutions, intelligence agencies, and critical infrastructure companies.


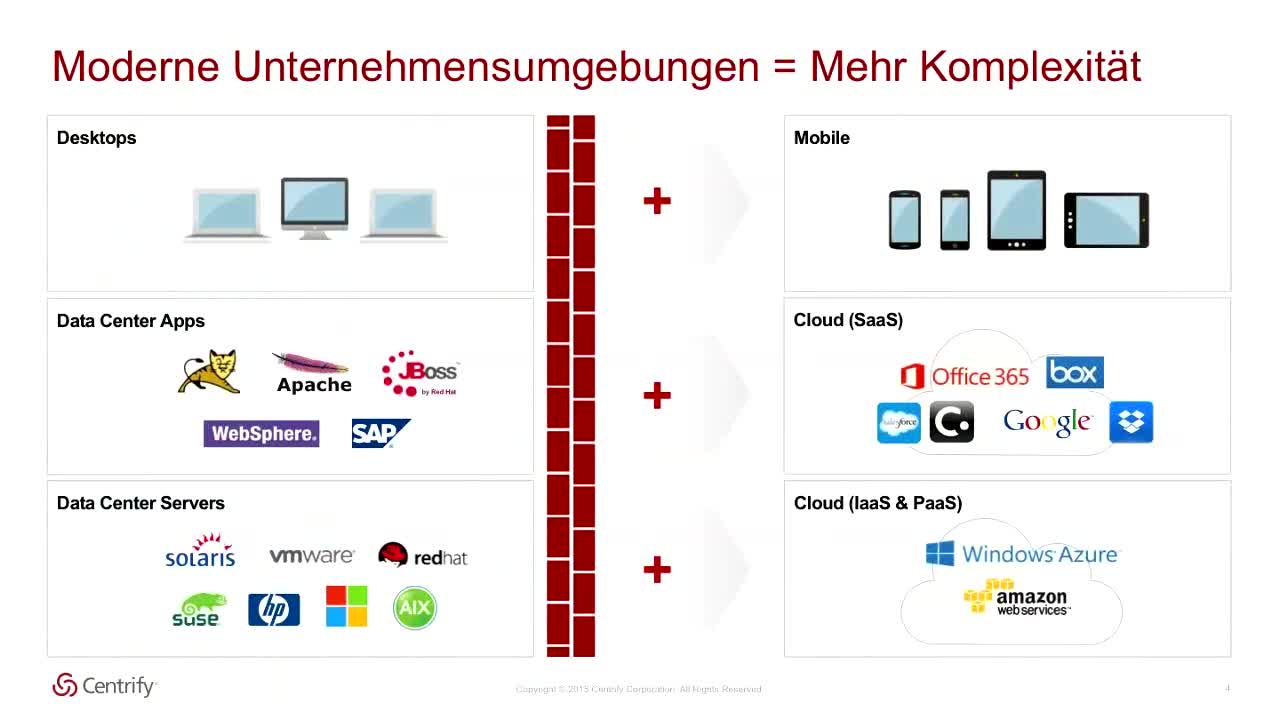
Although companies are constantly increasing their cybersecurity budgets, this does not seem to help much: each day we learn about new large-scale data breaches. Considering that over 80% of hacking-related breaches leverage compromised user credentials, it’s mindboggling why so many organizations are still focusing on securing their network perimeters.

As organizations continue to move their data and application functions into the cloud for obvious business reasons like improved flexibility and scalability, reduced time to market and cost savings, protecting their sensitive data across both on-premises and the cloud is becoming increasingly complicated. To ensure consistent and secure access management to for these data and applications across a heterogeneous IT landscape from any device and location is a massive challenge, further complicated by new compliance regulations such as GDPR, which makes the cost of a mistake extremely high.
Unifying Identity and Access Management for on-premises and cloud services and outsourcing it to a cloud service provider provides multiple immediate benefits: driving user productivity up thanks to a seamless single sign-on experience, increasing IT efficiency thanks to reduced maintenance efforts and improving overall security thanks to centralized monitoring and management.

Most of today’s organizations store even their sensitive data in the cloud. Moving workloads to the cloud results in improved flexibility, elasticity, and reduced time to market for organizations. Nevertheless, companies have to realize these benefits painlessly, while keeping sensitive data secure. Applying an on-premises security model for infrastructure and apps in the cloud can achieve this. When it comes to on-boarding thousands of business partners quickly, engaging with millions of customers easily, or simply providing a single sign-on experience to new Cloud applications, new approaches are also required.

Big Data technologies were invented to store and rapidly process the vast amount of data available today into useful “Smart” Information. What is common across these technologies is that their initial aims are focused on data processing capabilities rather than security and compliance. One particular concern is the lack of control over identity and access especially in the area of administration. This was fine when the application of the tools was confined to experimental or small scale usage. Now that they are being widely deployed for commercial purposes this is no longer satisfactory.
Big Data technologies need to be managed and secured in the same way as the other components in the IT infrastructure.