In my presentation at the KuppingerCole's cyberevolution 2023 conference in Frankfurt, entitled "Beware of Easy Paths: The Journey Towards NIS2 Compliance", I focused on the complexities of the revised Network and Information Systems Directive (NIS2) issued by the European Union. While I am neither a lawyer nor an auditor (so they might be important peers to talk to on your NIS2-journey), my focus is on the practical implications of this crucial piece of cybersecurity legislation. As a critical component of the EU's cybersecurity strategy, NIS2 extends its influence across various essential sectors, encompassing energy, transport, banking, and health. This directive marks a significant shift in the cybersecurity landscape, setting forth new challenges and requirements for organizations, particularly for medium-sized and large companies, as they strive to align with these evolving regulations.
Understanding NIS2
NIS2 is a pivotal piece of legislation issued by the European Union, aimed at fortifying cybersecurity measures across its member states. This directive serves as a cornerstone in the EU's strategy to enhance resilience and response capabilities in the face of growing cyber threats. NIS2 applies broadly within the EU, encompassing a variety of sectors deemed critical for the economy and society. These sectors include energy, transport, banking, health, digital infrastructure, and public administration, among others.
Crucially, NIS2 came into force on January 16, 2023. However, its practical application involves a multi-stage process. First, member states are required to transpose the directive into national law. This aspect underscores the need for harmonization of cybersecurity standards across different jurisdictions while allowing for some degree of customization to address national specifics. Second, the organizations within the scope of NIS2, particularly those categorized under KRITIS (Critical Infrastructures), are mandated to comply within a 21-month period. This staged approach aims to provide a structured and feasible pathway for entities to adapt and align with the directive's requirements.
The Scope and Impact of NIS2
NIS2 significantly expands the framework of cybersecurity obligations compared with its predecessor. It encompasses a wider range of organizations by categorizing them as either "essential" or "important" entities. This distinction is critical, as it brings a greater number of companies under the purview of NIS2, particularly those that were not previously subject to such stringent cybersecurity regulations.
For essential facilities, the level of criticality and obligations is higher. Important institutions, although new to this level of regulatory scrutiny, now also fall under the ambit of NIS2. This expansion significantly broadens the range of affected companies and organizations, moving beyond the traditional sectors of critical infrastructure.
Moreover, NIS2 introduces specific thresholds for determining which companies are considered medium-sized or large, making many more companies subject to these regulations. Medium-sized companies are defined as having 50-250 employees and a turnover of €10-50m and/or a balance sheet of less than €43m. Large companies are those with more than 250 employees and a turnover of €50m and/or a balance sheet of €43m. The implications of these thresholds are substantial, especially for medium-sized companies, which may find themselves grappling with a massive tightening of cybersecurity requirements.
Requirements and Enforcement under NIS2
NIS2 introduces a blend of specific and generic requirements to ensure comprehensive cybersecurity across various sectors. Article 21 of NIS2, for instance, lists several specific mandates, particularly focusing on risk management, incident response, authentication, and other measures. However, NIS2 also emphasizes adherence to current best practices, certifications, and a generally high and appropriate level of security. This dual approach allows for flexibility while maintaining a baseline of cybersecurity standards.
The enforcement of NIS2 is marked by firm oversight and significant sanctioning power. Supervisory bodies are designated at the national level to monitor and enforce compliance. This includes strengthened supervisory measures ensuring entities' adherence to cybersecurity protocols and the introduction of severe penalties for non-compliance. Cross-border collaboration is a key feature, enhancing cooperation between member states for consistent enforcement. And requirements for transparency and disclosure are stipulated, mandating clear communication regarding cybersecurity incidents and measures. NIS2 encourages initiatives exceeding minimum requirements, fostering a culture of cybersecurity excellence, and promotes public-private partnerships to enhance overall cybersecurity resilience.
Focusing on Compliance: A Tailored Approach
From KuppingerCole’s perspective, a key aspect of complying with NIS2 is recognizing that there is no one-size-fits-all solution, no matter what vendors, consultancies or whoever tells you. Each organization must define and implement NIS2 compliance in a manner that reflects its unique context and challenges. This tailored approach is crucial, considering the diverse range of sectors and company sizes affected by the directive.
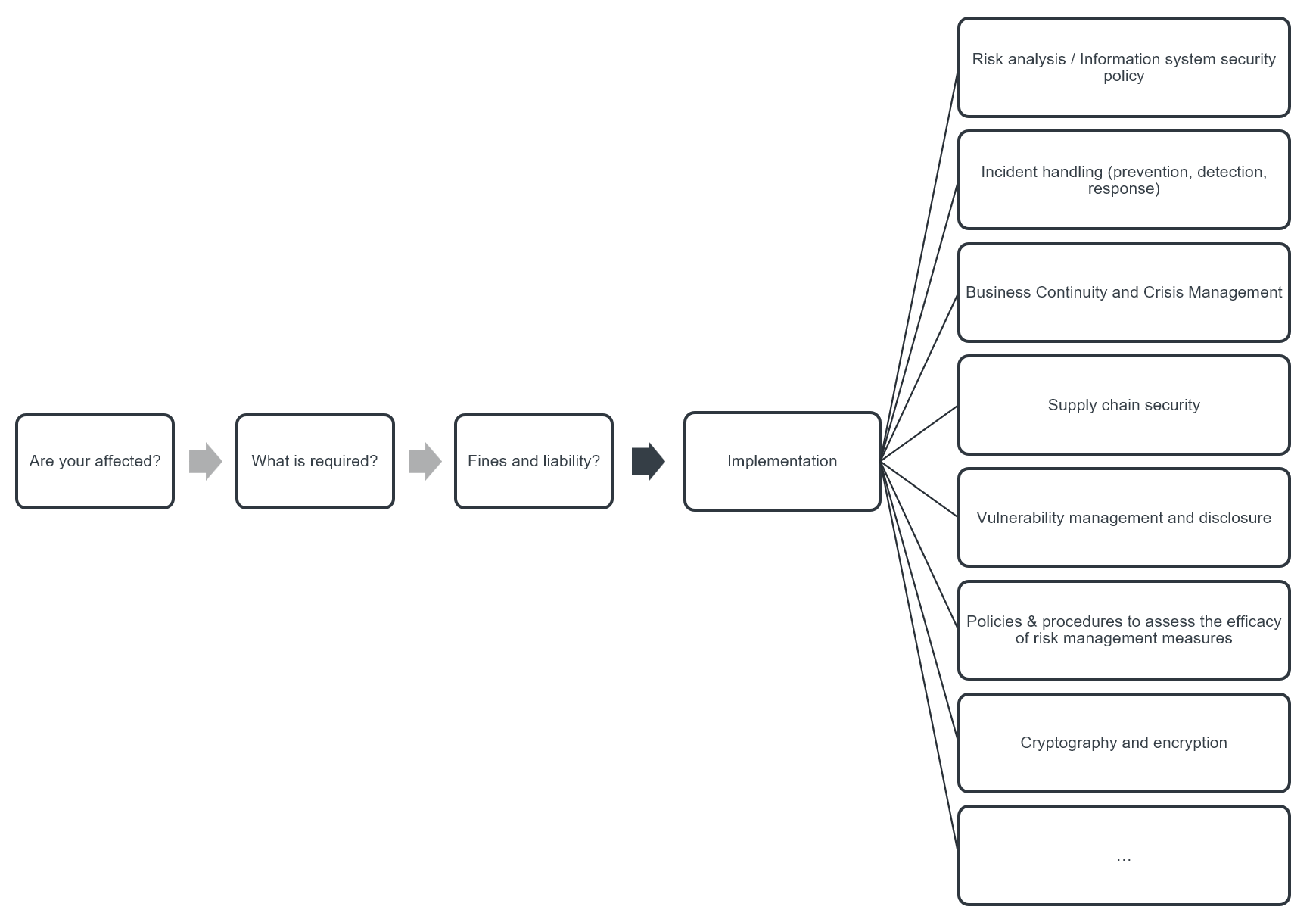
Image: NIS2 - From Initial Assessment to Continual Implementation
Organizations should prioritize a risk-based approach to cybersecurity, as advocated by NIS2. This involves not only identifying and assessing cyber risks unique to their operations but also developing bespoke strategies to mitigate these risks. Compliance, therefore, becomes a dynamic and continuous process, necessitating ongoing adjustments and improvements in line with the evolving cyber threat landscape and organizational changes.
Key areas of focus include risk management, incident reporting, supply chain protection, and cyber hygiene. Each of these areas requires a detailed and customized strategy, taking into account the specific needs and capabilities of the organization. For instance, incident reporting protocols must be efficient yet sensitive to the particular operational context of the business.
Practical Implementation Strategies
For practical implementation, especially for SMEs, the focus should be on developing manageable and cost-effective cybersecurity strategies. SMEs often face resource constraints and skill gaps, making it imperative to find solutions that balance cost with effectiveness. Simplifying compliance processes and tailoring strategies to the operational realities of SMEs can significantly aid in meeting NIS2 requirements. Collaboration and community initiatives can also play a pivotal role, allowing SMEs to pool resources and share knowledge to enhance their cybersecurity posture collectively.
In summary, the implementation of NIS2 demands a thoughtful, customized approach, particularly for smaller organizations facing unique challenges in their compliance journey.
Navigating NIS2 Compliance
NIS2 marks a significant shift from the conventional checkbox compliance to a more integrated approach, embedding cybersecurity, compliance, and resilience into the very fabric of organizational processes. It prompts a departure from the simplistic, procedural adherence to regulations, focusing instead on a comprehensive assessment of risks. The directive advocates for a customized journey to compliance, one that is not generic but tailored to the specific needs and risk profiles of individual organizations, underscoring the need for a strategic and nuanced application of its mandates.
In addressing NIS2 compliance, it is clear that a uniform solution is not feasible. Each organization must approach compliance in a manner tailored to its unique context. Seeking assistance from a range of professionals, including peers, consultants, analysts, lawyers, and the enforcing bodies is advisable for navigating this complex regulation. Collaboration with these experts can provide the necessary insights for effective compliance strategies.
At KuppingerCole Analysts, we focus on offering realistic strategies for NIS2 compliance. We understand the challenges involved and aim to provide pragmatic solutions, recognizing that each organization's journey towards compliance is distinct.
In conclusion, while the path to NIS2 compliance is intricate and requires a bespoke approach, there are resources available to guide organizations through this process, ensuring a secure and compliant digital environment.
















































