1 Introduction
This report is an overview of the market for Privilege Access Management (PAM) solutions and provides a compass to help buyers find the solution that best meets their needs. KuppingerCole examines the market segment, vendor functionality, relative market share, and innovative approaches to providing PAM solutions.
1.1 Market segment
Privileged Access Management (PAM) solutions are critical cybersecurity controls that address the security risks associated with the use of privileged access in organizations and companies. Traditionally, there have been primarily two types of privileged users.
Privileged IT users are those who need access to the IT infrastructure supporting the business. Such permissions are usually granted to IT admins who need access to system accounts, software accounts or operational accounts. These are often referred to as superusers.
There are now also privileged business users, those who need access to sensitive data and information assets such as HR records, payroll details, financial information or intellectual property, and social media accounts.
The picture has become more complicated with many more of these non-traditional users requiring and getting privileged access to IT and business data. Some will be employees working on special projects, others may be developers building applications or third-party contractual workers. With the onset of digital transformation, organizations have seen the number of privileged users multiply as new types of operations such as DevOps have needed access to privileged accounts.
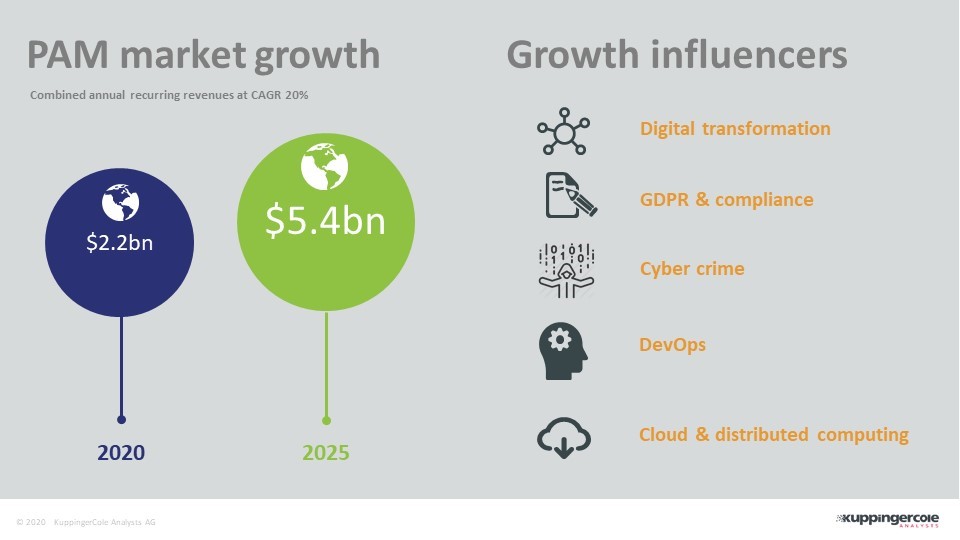
In recent years, Privileged Access Management (PAM) has become one of the fastest growing areas of cyber security and risk management solutions. KuppingerCole estimates that the number of major vendors in the space is around 40 with a combined annual revenue of around $2.2bn, predicted to grow to $5.4bn by 2025 (see Figure 2).
That growth has largely been driven by changes in business computing practices and compliance demands from governments and trading bodies, as well as increased levels of cybercrime. Digital transformation, regulations such as GDPR, the shift to the cloud and, most recently, the growth of DevOps in organizations looking to accelerate their application development processes are all adding to the growth.
The reason for this mini boom is that all these trends have triggered an explosion in data and services designated as business critical or confidential and a concurrent rise in the number of users and applications that need to access them. IT administrators realised that without dedicated solutions to manage all these, the organizations would be at great risk of hacks and security breaches. Hackers and cyber criminals have long targeted unprotected privileged accounts as one of the easiest routes to get inside an organization.
In recent years, PAM solutions have become more sophisticated making them robust security management tools in themselves. While credential vaulting, password rotation, controlled elevation and delegation of privileges, session establishment and activity monitoring are now almost standard features, more advanced capabilities such as privileged user analytics, risk-based session monitoring, advanced threat protection, and the ability to embrace PAM scenarios in an enterprise governance program are becoming the new standard to protect against today’s threats. Many vendors are integrating these features into comprehensive PAM suites while a new generation of providers are targeting niche areas of Privileged Access Management.
With the attack surface expanding and the number of attacks increasing every year, an integrated and more comprehensive PAM solution is required – one that can automatically detect unusual behavior and initiate automated mitigations. A successful attack can be conducted in minutes; therefore, a PAM solution must be capable of thwarting this attack without human intervention. Although we see more comprehensive PAM suites and solutions being offered, vendors are taking different approaches to solve the underlying problem of restricting, monitoring, and analyzing privileged access and the use of shared accounts. Overall, it’s one of the more dynamic and interesting parts of security and access management.
















































