1 Introduction / Executive Summary
As businesses embrace Digital Transformation and become increasingly cloud-native, mobile, and interconnected, the corporate network perimeter is gradually disappearing, exposing users to malware, ransomware, and other cyber threats. Traditional perimeter security tools no longer provide adequate protection from these threats. But even more so, traditional remote access solutions like virtual private networks (VPN) can no longer ensure the scalability and performance needed for the increasingly mobile and remote workforce, especially during pandemic times.
VPN is a typical example of a technology that was never designed for the purposes it is used nowadays. Besides creating potential bottlenecks by forcing companies to backhaul remote users’ traffic to a central location and thus negatively affecting performance and productivity, VPN appliances grant those users full, uncontrolled access to entire LANs. This dramatically expands the attack surface of corporate networks, provides easy lateral movement for potential attackers, and enables uncontrolled access to internal resources with implicit trust.
Unsurprisingly, Zero Trust is rapidly gaining popularity as a modern alternative to traditional perimeter-based security. An infrastructure designed around this model treats every user, application, or data source as untrusted and enforces strict security, access control, and comprehensive auditing to ensure visibility and accountability of all user activities.
Back in 2009, John Kindervag, then with the analyst firm Forrester, came up with the idea that networks should be designed without implicit trust, enforcing strict identity verification and least-privilege access policies for every user, device, or application, regardless of whether they are located in the former local area network or somewhere on the Internet. His ideas on eliminating the very concept of “trusted systems” from corporate networks helped popularize the catchy term “Zero Trust”, which had been first introduced over 15 years before.
In the same year, Google introduced BeyondCorp, a security framework created as a result of a sophisticated cyberattack on their internal infrastructure and aimed at preventing similar breaches in the future. BeyondCorp shifted access controls from the perimeter to individual devices and users, thus dramatically reducing the potential attack surface for future hackers and making it much more difficult for them to perform lateral movements, compromising one system after another.
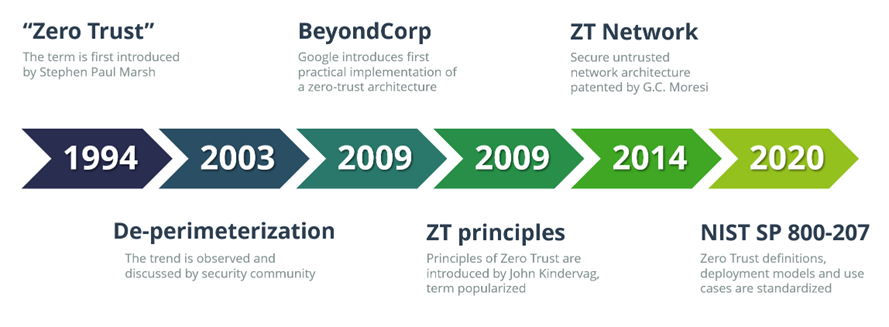
This has essentially started the Zero Trust “gold rush”, with numerous organizations eagerly looking for a possibility to buy into the new trend and with quite a few vendors quickly repackaging their existing products with new “Now with Zero Trust” labels.
One of the fundamental misconceptions the industry experts are still struggling to explain to the public is that Zero Trust is not an off-the-shelf product, but a journey that begins with a long-term business strategy and focuses on a step-by-step implementation, using existing or readily available tools and technologies, while maintaining the continuity of business processes and avoiding adding even more complexity to the existing architecture
However, even if the concept itself turned out to be quite difficult to get hold of, it has created entirely new markets for innovative security, compliance, and identity solutions. Without Zero Trust, we would not have cloud access security brokers (CASB), no Secure Access Service Edge (SASE) platforms, and, of course, no software-defined networking and micro-segmentation technologies that provide the backbone for the whole Zero Trust Network Access market.
As a concept, Zero Trust Network Access is based on the assumption that any network is always hostile, and thus, any IT system, application, or user is constantly exposed to potential external and internal threats. There is no place for a “trusted network” in a Zero Trust architecture, which is radically different from the traditional approach based on the notion of a security perimeter that separates a trusted local network from the rest of the world outside.
In various incarnations, ZTNA has existed for years, and for many early adopters of Zero Trust tenets, it has become the first building block in their long-term ZT strategies. However, the notorious COVID-19 pandemic, which forced the majority of the corporate workforce around the globe to work from home for two years, has provided a huge boost to the worldwide adoption of these solutions as a modern, more flexible and scalable alternative to aging VPN infrastructures.
In this Leadership Compass, we provide an overview of the existing solutions implementing this approach. They might be based on different underlying technologies and focus on different aspects of the Zero Trust methodology, but fundamentally, all of them solve the same problem: enabling secure yet convenient access to business applications and other resources for users regardless of their location, whether in an office, at home or anywhere else.
1.1 Highlights
- In recent years, Zero Trust architectures have gained enormous popularity as a more secure, yet flexible and future-proof alternative to traditional perimeter-based security. By eliminating the very notion of a trusted system, ZT architectures enforce strict identity verification and least-privilege access policies for every user, device, or application, regardless of where they are located.
- Zero Trust Network Access solutions apply this concept to network-based access to existing applications and other systems. By creating a logical identity- and context-based overlay over existing (and presumed hostile) networks and preventing discovery and access of applications for unauthorized users, ZTNA solutions enforce strict, fine-grained policies, thus eliminating the possibility of implicit trust and unchecked access to sensitive resources.
- ZTNA is the key technology that enables modern Zero Trust architectures, together with comprehensive identity management, strong multi-factor authentication, and real-time behavior analytics. Besides dramatically reducing the attack surface and preventing lateral movement for hackers (and thus significantly improving security posture), it has the potential to greatly simplify both the users’ and administrators’ experiences.
- The market for ZTNA solutions is currently experiencing explosive growth. Both large established vendors and small but innovative startups are offering a multitude of solutions that promise to address various usage scenarios: simplified cloud migration, seamless hybrid and multi-cloud architectures, or a modern replacement for VPN.
- The concept of Secure Access Service Edge (SASE) converges network and security solutions into a unified and tightly integrated platform that is entirely delivered from the cloud, dramatically reducing the complexity of corporate network infrastructures, and offering consistent productivity and protection at a global scale.
- The Overall Leaders in Zero Trust Network Access are (in alphabetical order): Absolute Software, Broadcom, Cato Networks, Cisco, Cloudflare, Google, Jamf, Lookout, NetFoundry, Palo Alto Networks, and Perimeter 81.
1.2 Market Segment
Zero Trust Network Access (ZTNA) is an alternative approach replacing the traditional flat networks that is rapidly gaining popularity that essentially replaces the notion of a rigid single, usually hardware-based perimeter of a corporate network with the ability to create multiple dynamic perimeters around individual systems or applications. As opposed to traditional network-centric architectures, ZTNA platforms work completely independently from the underlying hardware, appliances, switches, or other network devices and can be deployed across multiple environments and managed from a centralized control plane.
This approach ensures that access policies can be defined in a much more granular fashion per individual application or service by establishing secured point-to-point tunnels between clients and services. Each of these sessions is always authenticated and continuously monitored to prevent malicious activities. Access and security policies are managed centrally and enforced across hybrid IT environments (on-premises, multi-cloud, or mobile).
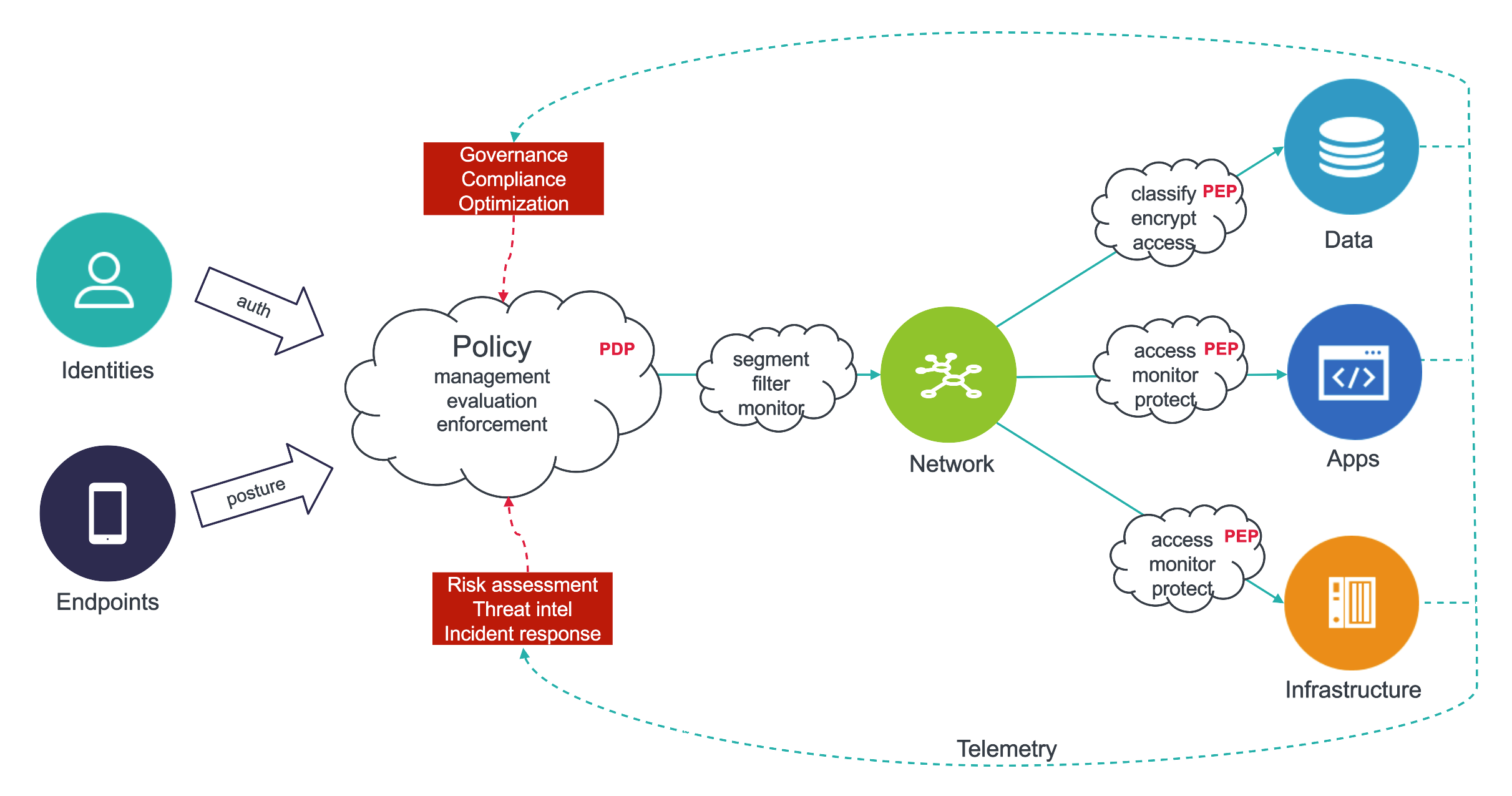
As a result, users are only granted access to the necessary applications and data, greatly reducing the overall attack surface and practically eliminating lateral movement. Since only the control plane is centralized, no bottlenecks are introduced into the data plane, ensuring scalability and consistent user experience. ZTNA architectures provide a unified layer of abstraction that ensures that enterprise application access can be entirely driven by common policies regardless of their deployment – this enables multiple scenarios like simplified cloud migration, seamless hybrid, and multi-cloud architectures, and an additional security layer for mitigating network-based attacks.
ZTNA is the key technology that enables modern Zero Trust architectures, together with comprehensive identity management, strong multi-factor authentication, and real-time behavior analytics. Most recently, the concept of Secure Access Service Edge (SASE) has emerged, which converges network and security solutions into a unified and tightly integrated platform that is entirely delivered from the cloud, dramatically reducing the complexity of corporate network infrastructures, and offering consistent productivity and protection at a global scale.
In this Leadership Compass, we do not plan to cover all aspects of modern Zero Trust and SASE architectures, focusing instead on the solutions implementing the underlying network access layer. We are looking for comprehensive, scalable, and flexible platforms that enable organizations to replace their aging VPNs with fine-grained, secured, authenticated, and audited access to corporate applications and resources that work uniformly across heterogeneous IT environments.
We expect these solutions to implement management on the application, not networking level, maintaining uniform policies regardless of location, even across the public Internet. We presume modern ZTNA solutions to be scalable without practical limitations, based on open identity and security standards, and agnostic to the specific application or network protocols.
Here are just some of the key criteria we expect to be fulfilled by Zero Trust Network Access platforms:
- Application-level, not network-level segmentation
- No reliance on inbound connections
- Separation of control and data planes
- Cloud-only, on-premises, or hybrid deployments
- Scalable, decentralized architecture to reduce latency
- Centralized, unified deployment and management across hybrid networks
- Unified, network-agnostic access policy management
- Encryption of all network connections
- Strict identity verification for each session
- Device posture validation as a prerequisite for access
- Multi-factor authentication, single sign-on support
- Continuous session monitoring, anomaly detection
- Additional threat protection capabilities
- Built-in reporting and compliance audit functions
We explicitly exclude solutions that are based on the coarse-grained access paradigm like traditional VPNs or products not focusing on application-level segmentation. This also includes alternative approaches toward Zero Trust implementation such as reverse-proxy architectures.
We also expect software-defined perimeter solutions not to require deployments of additional specialized hardware or making substantial changes in existing network infrastructures. Finally, we are not covering the overall capabilities of SASE platforms in this report, although we do recognize that some vendors are offering their ZTNA products as a part of a bigger SASE solution.
1.3 Delivery Models
One of the defining features of Zero Trust as a concept is that its tenets are universally applicable to a wide variety of use cases covering nearly every field within the IT industry. On the one hand, it is one of the biggest reasons for its enduring popularity – applying ZT strategically can help to dramatically reduce overall complexity and minimize the technical debt of any organization’s existing IT landscape. On the other hand, it means that most products currently offered under the “Zero Trust” label are only designed to address a specific, often quite narrow selection of those use cases.
Even within the fairly specific segment of ZTNA solutions, we can find products targeted toward solving problems so substantially different that it implies radically different architectures and deployment scenarios. Although “VPN replacement” or rather the enablement of convenient and yet secure remote access to business resources is currently the most popular driver for ZTNA adoption, it is by no means the only one.
Securing access to sensitive data in complex hybrid and multi-cloud environments, securing data flows in distributed cloud-native applications, enabling secure and compliant onboarding of BYOD devices in organizations, and preventing lateral movement of malware and malicious actors – these are just a small subset of popular applications of ZTNA architectures.
Some of these use cases imply a massively scalable, cloud-native architecture that can accommodate complex traffic patterns between thousands of microservices or other cloud workloads. Others might benefit from a fully managed offering delivered as a service. For others still, the ultimate deployment flexibility across hybrid environments is a crucial factor.
Whether such scenarios place more focus on adaptive access management, threat prevention, data loss or security analytics can also greatly affect the choice of the most appropriate solution for your specific ZTNA project.
A fundamental difference between modern ZTNA and legacy VPN solutions is the separation of control and data planes, which can be set up in different environments and still enable a single point of management and visibility across complex deployments. Most vendors offer a fully managed cloud-based control pane for their customers as an option, while some of them even focus on the SaaS delivery as their only offering. However, organizations operating in highly regulated industries or large enterprises might require a fully on-premises deployment even for their control planes, which is addressed by some vendors offering their products in a fully containerized form.
Since the data plane of a ZTNA architecture must by its very nature encompass the whole corporate networking landscape and even go beyond it to accommodate remote workers, vendors usually offer a broad variety of deployment options for their gateway components, which perform traffic routing and access management. These can vary from a simple piece of software to be deployed into an application container to an enterprise-grade customer-managed on-prem gateway setup or even an SDK to be embedded directly into a microservice. The scope of different use cases and deployment scenarios vary between vendors – some would offer a broad range of connectivity options, while others would focus more on the scalability and ease of deployment of their managed cloud-native solutions.
In any case, connecting an end-user device to a ZTNA platform requires an agent, a piece of software not dissimilar from a traditional VPN client. These agents come in various shapes as well. Some are highly specialized, others support multiple connectivity options (to enable coexistence with legacy VPNs, for example), and some vendors even have partnerships with 3rd party companies to include their technology into existing endpoint agents.
Since the minimization of the overall number of agents deployed to endpoint devices is a popular usability requirement, many vendors even include agentless capabilities in their products. However, it is important to stress that this functionality is usually limited to a small number of supported protocols (HTTP for web apps, RDP for remote desktop, and SSH for remote shell access) and, arguably, does not fully conform to the tenets of Zero Trust. Still, it remains a very popular feature that enables additional use cases for ZTNA solutions – such as providing fine-grained and controlled access to contractors and external administrators without any investment into additional infrastructure.
In the end, understanding the balance between the most urgent business drivers and pain points within the organization and the investments and changes required for the strategic implementation of Zero Trust should be the primary decision factor for choosing the most appropriate deployment model. However, one should always keep in mind that the journey toward Zero Trust is a never-ending one, and requirements tend to change quickly. Deployment flexibility determined by the range of the deployment scenarios supported by a vendor is, therefore, an important consideration for any purchase decision.
1.4 Required Capabilities
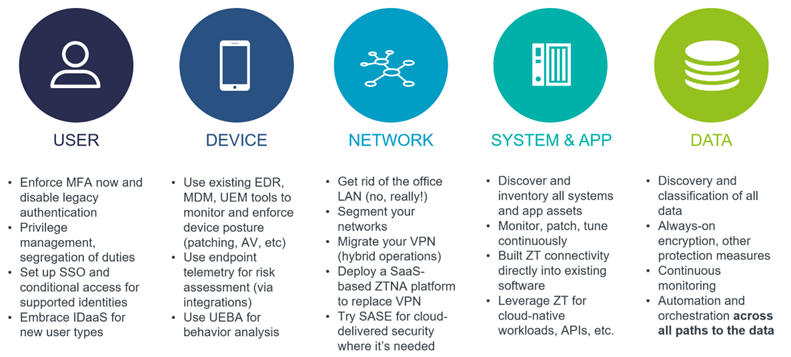
It is worth stressing once again that organizations looking for a ZTNA platform most appropriate for their current and future requirements should not just focus on current market leaders. Instead, they should carefully examine their existing IT environments to see how well they are prepared for the adoption of the Zero Trust approach. Some of the first questions to ask yourself could be the following:
- All ZT implementations are strongly dependent on having comprehensive and modern identity and access management in place. If you have been thinking about switching from legacy on-prem IAM to a modern managed IDaaS solution for years, ZTNA might be just the right reason to finally take the plunge.
- One of the key ZT tenets prescribes continuous monitoring of all assets as well as collecting and analyzing the information about their current state. Do you have a relatively modern SIEM solution in place or have you considered opting for a managed SOC? How well are your corporate devices covered by EDR, MDM, and other security monitoring and management solutions?
- What kind of data protection solutions do you currently operate? How ubiquitous is encryption in your organization, at rest and in transit, and how consistently are the encryption keys managed?
- How big is your current investment in network security infrastructures such as firewalls and VPNs? Are you ready for a rip-and-replace approach, or would you rather continue using at least some of the existing tools?
Of course, one should not focus on networking alone – the principles of Zero Trust must transcend network-layer thinking to be successful. ZT architectures require proper authentication and authorization for each session involving users, applications, networks (including clouds), and data. Other key components of Zero Trust are continuous risk-adaptive authentication and dynamic policy evaluation.
However, Zero Trust Network Access has proven to be the most popular first step towards the strategic adoption of Zero Trust for organizations of all sizes and industries around the world. To a large extent, this rapid growth can be attributed to the pandemic that has greatly amplified the need to modernize legacy VPN-based remote access infrastructures, but it has found much more widespread use because of the ability of existing solutions to remediate a broad range of acute problems simply and affordably: from protecting corporate networks against ransomware to making cloud-native applications secure by design.
In this Leadership Compass, we focus primarily on solutions that can address all of the use cases mentioned above, at least to a sufficient degree. Thus, we have established the following evaluation criteria:
Deployment flexibility: as mentioned above, the more various deployment options - on-premises, in a cloud, managed, or SaaS, a solution can support, the more current or potential use cases it will be able to address for a customer and thus to better align with the long-term goals of your Zero Trust strategy.
Secure connectivity: According to the tenets of Zero Trust, all communications between resources must be secured, regardless of their locations. In practice, this implies end-to-end encryption of any network traffic between resources. The notion of a software-defined perimeter extends this even further by separating the connectivity layer from the underlying networks, rendering the ZTNA invisible and inaccessible to unauthorized users.
Fine-grained access: All access decisions are performed on a per-resource basis, where resources are expected to be not entire subnets, but individual applications or even individual data records. Access to a resource is granted according to the principle of least privilege and on a per-session basis, after an explicit evaluation of trust in the requester.
Strong authentication: Authentication and authorization must be dynamic and strictly enforced. This includes the use of strong multi-factor authentication, scanning for cyberthreats, and reevaluating trust before and during each transaction. It is driven by dynamic policies that continuously evaluate the state of the resource, requester, and other contextual attributes.
Client risk assessment: Each access decision is made based on real-time risk evaluation that may include behavioral analysis, environmental conditions, history of previous accesses, etc. Assessing the device’s security and compliance posture is expected to be performed either using the platform’s own agent or by analyzing the telemetry collected through partnerships and integrations with third-party EDR and other security vendors.
Visibility and monitoring: The information about the current state of assets and their communications must be collected, analyzed, and used to improve the organization’s security posture. The integrity and security of all assets must be continuously monitored and deviations in security posture must be mitigated promptly. In addition, these findings should be fed back into the client risk assessment and authentication routines to further improve their quality.
Audit and Compliance: regulatory compliance is a major challenge and simultaneously a business driver for organizations of any size or industry. Security data retention and comprehensive compliance reporting are the basic capabilities here. Out-of-the-box support for regulatory frameworks like GDPR, HIPAA, or PCI is a major differentiator for many customers.
Integrations: ZTNA platforms provide the backbone for a modernized, secure IT infrastructure and are thus expected to integrate with a wide variety of other security, identity, and networking products – from identity providers and endpoint detection and response platforms to enable fine-grained context-based access decisions to SIEMs and other security analytics to implement visibility. Finally, incorporating ZTNA solutions into Secure Access Service Edge (SASE) solutions is also a popular current trend.
2 Leadership
Selecting a vendor of a product or service must not only be based on the information provided in a KuppingerCole Leadership Compass. The Leadership Compass provides a comparison based on standardized criteria and can help identify vendors that shall be evaluated further. However, a thorough selection includes a subsequent detailed analysis and a Proof of Concept of a pilot phase, based on the specific criteria of the customer.
Based on our rating, we created the various Leadership ratings. The Overall Leadership rating provides a combined view of the ratings for
- Product Leadership
- Innovation Leadership
- Market Leadership
2.1 Overall Leadership
The Overall Leadership rating provides a consolidated view of all-around functionality, innovation, market presence, and financial position. However, these vendors may differ significantly from each other in terms of product features, platform support, and integrations. Therefore, we strongly recommend looking at all the leadership categories as well as each entry in chapter 5 to get a comprehensive understanding of the players in this market and what use cases they support best.
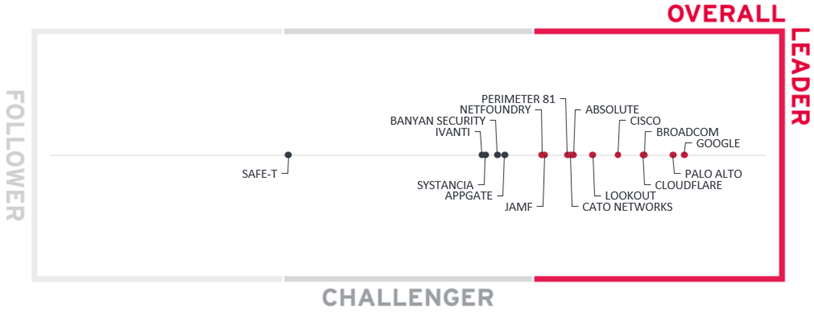
In total, eleven vendors have achieved the Overall Leader status in our rating.
Google is a multinational company specializing in internet-related products and services, known for its search engine, online advertising technologies, and cloud computing services. Google’s BeyondCorp Enterprise platform, introduced back in 2009, is essentially the first practical implementation of Zero Trust that is still recognized as one of the leading ZTA solutions.
Palo Alto Networks is a multi-national cybersecurity company, a leading provider of both traditional network security tools and modern cloud-native security solutions. The company’s Prisma Access solution is an integrated cloud-native security platform that combines advanced “ZTNA 2.0” with a full range of secure service edge capabilities.
Broadcom is a leading American manufacturer of semiconductor and infrastructure software products. Since the acquisition of the Symantec Enterprise Security business in 2019, Broadcom is operating the Symantec Secure Access Cloud, a SaaS solution that enables secure and granular access management and data governance to any corporate resource hosted on-premises or in the cloud.
Cloudflare is an international company specializing in accelerating and protecting internet applications through an intelligent global security cloud without adding hardware or installing software. Cloudflare Access, part of the company’s Cloudflare One platform for Zero Trust and SASE, connects any user to any application or network with fine-grained clientless or client-based access.
Cisco is a multinational technology company that is the world’s largest manufacturer of networking hardware and telecommunications equipment and a leading provider of remote access solutions. Cisco+ Secure Connect, the company’s secure service edge offering, provides customers with a flexible choice of remote access capabilities to align with their requirements and use cases.
Lookout is an American cybersecurity provider of endpoint and cloud security solutions. One of the pioneers in mobile security, Lookout has further expanded its portfolio with a full stack for cloud security with the acquisition of CipherCloud in 2021. Nowadays, the Lookout Security Platform secures mobile endpoints, protects workers from Internet-based threats, provides secure access to private and SaaS apps, and safeguards corporate data.
Perimeter 81 is an Israeli cloud and network security company specializing in secure remote access solutions based on the Zero Trust architecture. Since 2018, the company has been offering its converged networking and security cloud edge to a broad range of customers around the world. Its offering includes corporate application access, as well as Firewall as a Service and a Secure Web Gateway, consolidated with ZTNA in a simple, easy to use SaaS platform.
Absolute Software is an endpoint and network security vendor headquartered in Vancouver, British Columbia, Canada and San Jose, California, USA. After the acquisition of NetMotion, the company now offers Absolute Secure Access, an intelligent platform that delivers secure remote access, protecting users and resources while improving the experience of working remotely.
Cato Networks is an Israeli network security company that operates a global private backbone infrastructure, which combines SD-WAN, secure access, and managed security services in a single, global security cloud. One of the pioneers of secure edge technology, the company’s vision extends beyond ZTNA or SASE, striving to consolidate all network and security functions in its platform.
Jamf is an American software vendor primarily known for device management and security solutions for Apple devices. In 2021, Jamf acquired Wandera, a Zero Trust cloud security company, bringing its technology to a much wider customer base. Jamf Private Access is the company’s entirely cloud-delivered ZTNA platform with a strong focus on a seamless, transparent mobile worker experience.
NetFoundry is a network security vendor based in Charlotte, North Carolina, USA. At the core of NetFoundry’s solution is OpenZiti – an open-source programmable Zero Trust networking stack which can be applied to any use case. On top of this free foundation, the company offers a commercial SaaS platform for centralized deployment and management of ZTNA networks.
Most other vendors can be found in a tight group at the right edge of the Challenger segment. Although they have diverse backgrounds, product visions, and market strategies, they all share the same potential for future improvement: we are looking to see them among the leaders in the next edition of this Leadership Compass. Only Safe-T is staying somewhat behind the rest of the group. Unfortunately, the company is yet to find a substantial customer base to appreciate its capable and robust solution.
In alphabetical order, the Overall Leaders are:
- Absolute Software
- Broadcom
- Cato Networks
- Cisco
- Cloudflare
- Jamf
- Lookout
- NetFoundry
- Palo Alto Networks
- Perimeter 81
2.2 Product Leadership
The first of the three specific Leadership ratings is about Product leadership. This view is mainly based on the analysis of product/service features and the overall capabilities of the various products/services. In the Product Leadership rating, we look specifically for the functional strength of the vendors’ solutions, regardless of their current ability to grab a substantial market share.
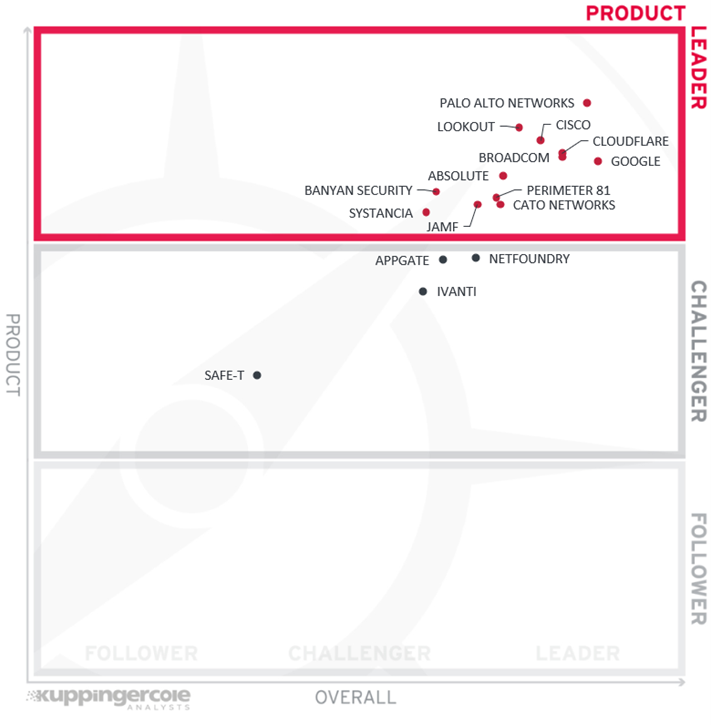
In total, twelve vendors have been recognized as Product Leaders in this rating. Besides the companies already described earlier in the Overall Leadership section, we should mention the following:
Banyan Security is a US-based cybersecurity company providing secure and seamless solutions for remote and on-premises access to corporate resources. With a strong focus on hybrid and multi-cloud deployment scenarios, the Banyan platform can adapt to the requirements of customers of any size or vertical.
Systancia is a French software vendor specializing in secure remote access and workspace solutions. Originally focusing on VDI, the company has expanded into identity management and zero trust access solutions. Systancia Gate is a full-featured private network access solution with a unique double barrier architecture and a strong emphasis on regulatory compliance.
The rest of the vendors can be found among the Challengers. Again, we can observe a tight group of companies that have almost reached a position among the Leaders – we expect them to deliver expanded capabilities shortly.
The only exception here is Safe-T: although we appreciate its unorthodox approach to addressing the network connectivity challenges of Zero Trust solutions, in the strictest sense of the definition, the company’s solution does not fulfill all the tenets of Zero Trust.
Still, there are no Followers in our product rating.
In alphabetical order, the Product Leaders are:
- Absolute Software
- Banyan Security
- Broadcom
- Cato Networks
- Cisco
- Cloudflare
- Jamf
- Lookout
- Palo Alto Networks
- Perimeter 81
- Systancia
2.3 Innovation Leadership
Next, we examine innovation in the marketplace. Innovation is, from our perspective, a key capability in all IT market segments. Customers require innovation to meet evolving and even emerging business requirements.
Innovation is not limited to delivering a constant flow of new releases. Rather, innovative companies take a customer-oriented upgrade approach, delivering customer-requested and other cutting-edge features, while maintaining compatibility with previous versions.
In such a rapidly growing and evolving market segment as ZTNA, vendors have numerous opportunities to implement a unique feature or choose a different approach to a certain capability that sets it apart from all other competitors. It is therefore completely unsurprising to see most of the vendors in this rating being recognized for their high degree of innovation. In total, thirteen vendors have been recognized as Innovation Leaders.
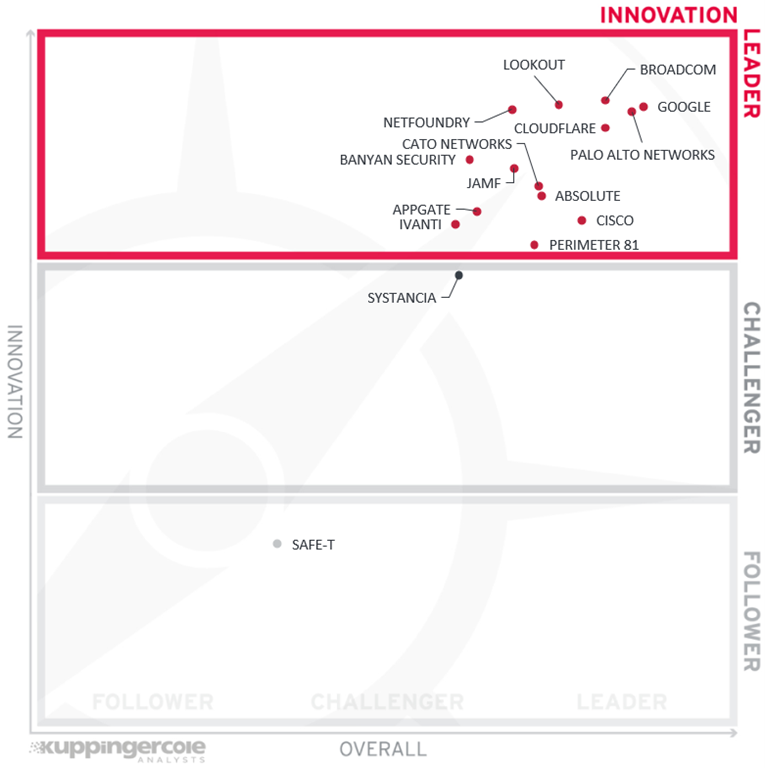
Joining the companies already mentioned above are the following:
Appgate is an American software company developing cloud-ready security and analytics solutions. Previously a part of Cyxtera Technologies, Appgate became an independent company in 2020. Appgate SDP is a comprehensive, flexible, and versatile software-defined perimeter platform with a people-centric focus, powered by an innovative and efficient networking technology.
Ivanti is an American software company specializing in IT security and systems management solutions. In 2020, the company has acquired Pulse Secure, a veteran provider of secure remote access (both VPN and Zero Trust) solutions. Nowadays, this technology forms the basis of Ivanti Neurons for Zero Trust Access, a part of Ivanti’s AI-powered workspace hyper-automation platform.
The only Challenger in our innovation rating is Systancia – ending up so close to the upper border indicates that the company can easily improve its position in the next edition of this Leadership Compass.
The only vendor in the Follower section is Safe-T: with its strong focus on identity and access functions, its solution unfortunately largely dismisses the networking aspect of ZTNA solutions.
In alphabetical order, the Innovation Leaders are:
- Absolute Software
- Appgate
- Banyan Security
- Broadcom
- Cato Networks
- Cisco
- Cloudflare
- Ivanti
- Jamf
- Lookout
- NetFoundry
- Palo Alto Networks
- Perimeter 81
2.4 Market Leadership
Finally, we analyze Market Leadership. This is an amalgamation of the number of customers and their geographic distribution, the size of deployments and services, the size and geography of the partner ecosystem, and the financial health of the participating companies. Market Leadership, from our point of view, requires global reach.
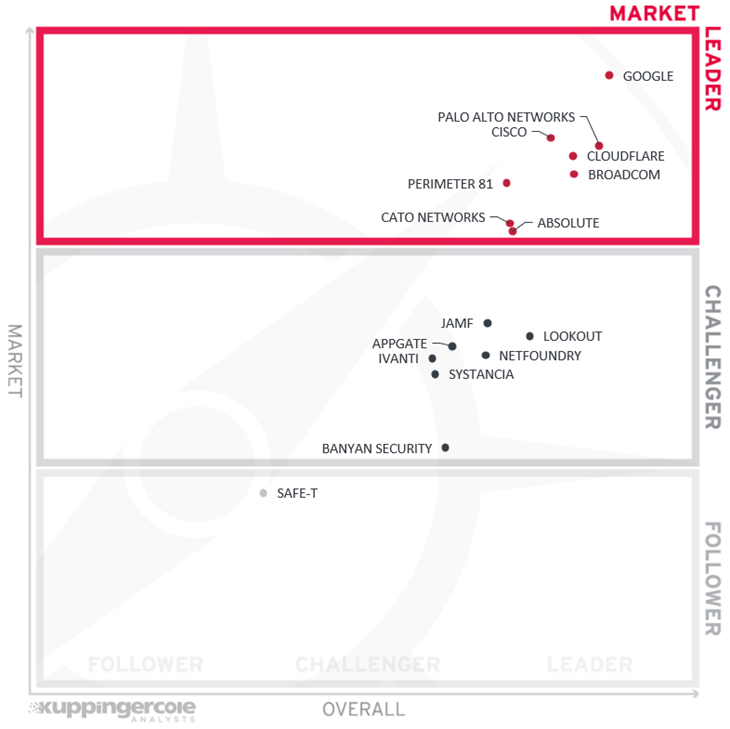
Unsurprisingly, we can find the large, veteran vendors like Google, Cisco, Palo Alto Networks, and Broadcom among the Market Leaders – with their long market presence, global brand recognition, and strong partner ecosystems.
However, they are joined by three much younger and relatively smaller companies. Both Perimeter 81 and Cato Networks can still be considered startups but being early pioneers in the ZTNA and SASE markets, they have already managed to find substantial customer bases and achieve global recognition. Absolute Software, while not a startup, is a newcomer to the ZTNA market thanks to a recent acquisition of NetMotion, but it has already managed to substantially expand the existing customer base of the solution it acquired.
Among the Challengers, we can observe most other vendors. Even large companies like Ivanti, Jamf, and Lookout have not reached the Leader status in our rating, because their large customer bases are primarily served by other, non-ZTNA-related products from their portfolios. Other vendors in this group are still in the startup stage and are working hard to establish a substantial market presence.
Only Safe-T is found in the Follower segment: its customer base is quite small compared to the rest of the analyzed vendors.
In alphabetical order, the Market Leaders are:
- Absolute Software
- Broadcom
- Cato Networks
- Cisco
- Cloudflare
- Palo Alto Networks
- Perimeter 81
3 Correlated View
While the Leadership charts identify leading vendors in certain categories, many customers are looking not only for a product leader but for a vendor that is delivering a solution that is both feature-rich and continuously improved, which would be indicated by a strong position in both the Product Leadership ranking and the Innovation Leadership ranking. Therefore, we provide the following analysis that correlates various Leadership categories and delivers an additional level of information and insight.
3.1 The Market/Product Matrix
The first of these correlated views contrasts Product Leadership and Market Leadership.
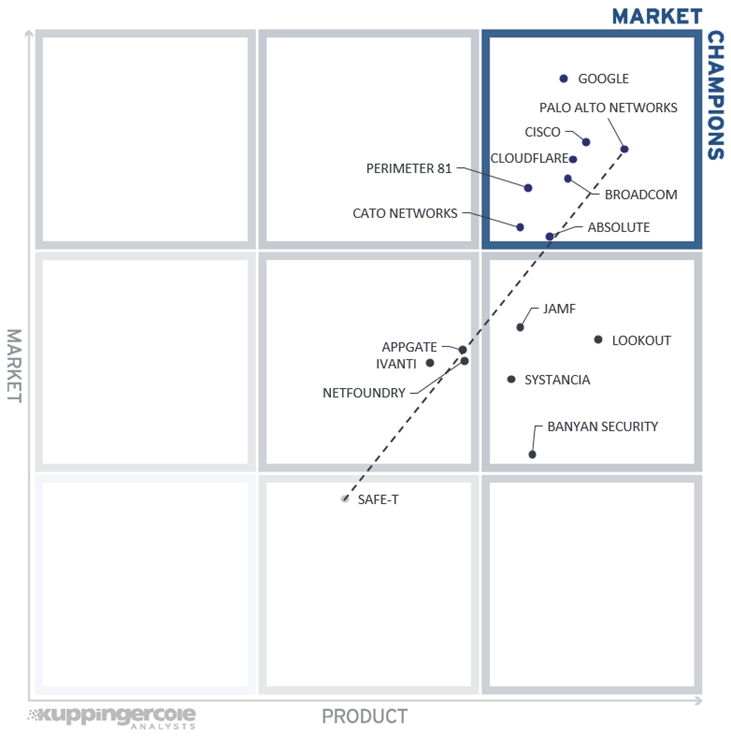
Vendors below the line have a weaker market position than expected according to their product maturity. Vendors above the line are sort of “overperformers” when comparing Market Leadership and Product Leadership. All the vendors below the line are currently underperforming in terms of market share. However, we believe that each has a chance for significant growth. The overall correlation in this market segment is still quite far from ideal, indicating that the ZTNA market is still evolving rapidly and has not reached maturity yet.
The top right segment of the diagram contains the vendors that score well both in product and market leadership, which unsurprisingly means that all of them are also recognized as Overall Leaders.
In the right middle segment, we observe the vendors that, despite their highly capable products, have not yet reached market leadership. This includes Lookout and Jamf, which entered the ZTNA market recently through acquisitions, and Systancia and Banyan Security which are working on expanding their regional market presence to the global level.
Safe-T can be found in the bottom middle segment, indicating its comparatively low market presence at the moment. The rest of the companies are located in the middle segment, reflecting their solid product and market strengths with a potential for future growth.
3.2 The Product/Innovation Matrix
This view shows how Product Leadership and Innovation Leadership are correlated. It is not surprising that there is a pretty good correlation between the two views with a few exceptions. The distribution and correlation are tightly constrained to the line, with a significant number of established vendors plus some smaller vendors.
Vendors below the line are more innovative, vendors above the line are, compared to the current Product Leadership positioning, less innovative. Here, we can see that the overall correlation between the product and innovation ratings is far from perfect, with many vendors appearing away from the dotted line. This is a strong indicator that the market continues to evolve, with different vendors favoring different functional areas and thus making their direct comparison somewhat complicated.
Among the Technology Leaders, we can find the usual suspects like – large companies with the ability to continuously invest in product innovation. However, joining them in the same quadrant is Banyan Security, a company that is still underperforming in its market position. This shows that even smaller, less financially strong companies can focus on innovation.
Again, we should mention Safe-T – a vendor that is unique in this rating in the way how it chooses the technology to address its customers’ needs. While the company’s solution is able to support a wide range of use cases and requires substantially less effort to deploy than many competitors, it is nevertheless very difficult to compare with other vendors due to an entirely different approach toward zero trust implementation.
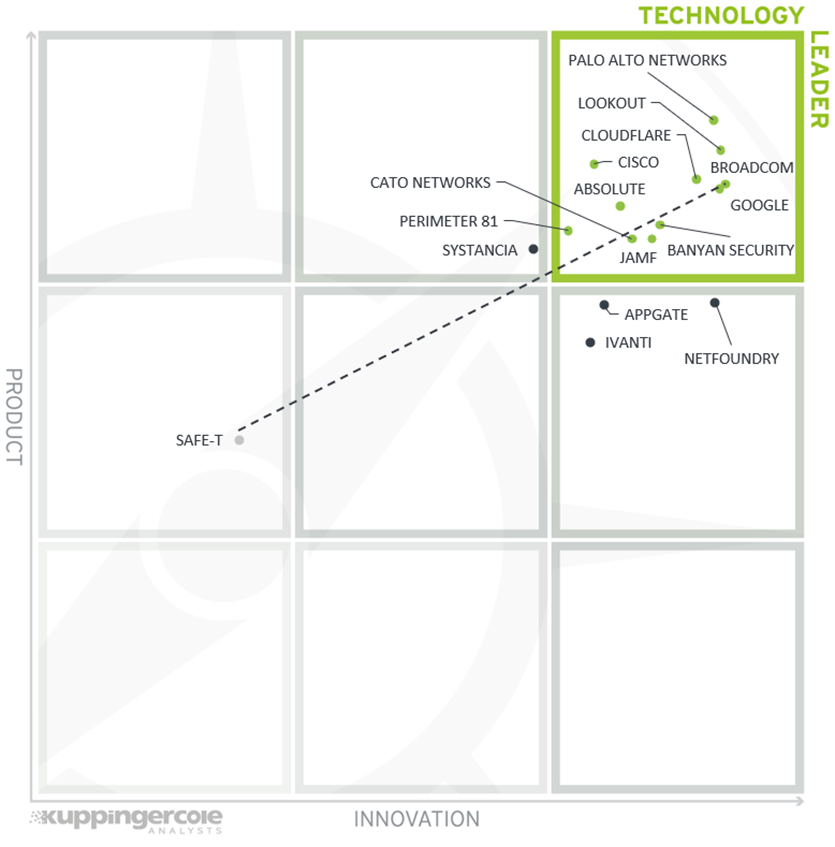
3.3 The Innovation/Market Matrix
The third matrix shows how Innovation Leadership and Market Leadership are related. Some vendors might perform well in the market without being Innovation Leaders. This might impose a risk for their future position in the market, depending on how they improve their Innovation Leadership position.
On the other hand, highly innovative vendors have a good chance of improving their market position. However, there is always a possibility that they might also fail, especially in the case of smaller vendors.
Vendors above the line are performing well in the market as well as showing Innovation Leadership; while vendors below the line show an ability to innovate while having less market share, and thus the biggest potential for improving their market position.
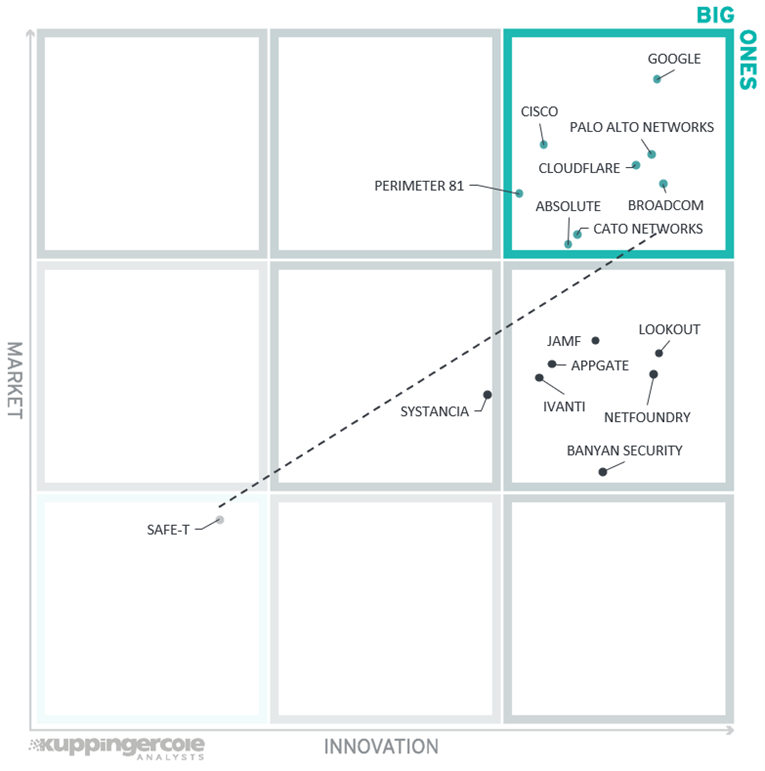
In this graph, we can observe that the correlation is very low compared to many other Leadership Compasses, which indicates the relative immaturity of the ZTNA market.
Again, we find all the large, well-established vendors and other market leaders among the Big Ones, which is completely unsurprising. More attention, however, should be given to the vendors from the middle right segment: Appgate, Banyan Security, Ivanti, Jamf, and Lookout. These companies all provide a strong level of innovation, which is not fully reflected in their market presence, showing strong potential for further growth.
4 Products and Vendors at a Glance
This section provides an overview of the various products we have analyzed within this Leadership Compass. Aside from the rating overview, we provide additional comparisons that put Product Leadership, Innovation Leadership, and Market Leadership in relation to each other.
These allow identifying, for instance, highly innovative but specialized vendors or local players that provide strong product features but do not have a global presence and large customer base yet.
Based on our evaluation, a comparative overview of the ratings of all the products covered in this document is shown in Table 1.
| Product | Security | Functionality | Deployment | Interoperability | Usability |
|---|---|---|---|---|---|
| Absolute Software |  |
 |
 |
 |
 |
| Appgate |  |
 |
 |
 |
 |
| Banyan Security |  |
 |
 |
 |
 |
| Broadcom |  |
 |
 |
 |
 |
| Cato Networks |  |
 |
 |
 |
 |
| Cisco |  |
 |
 |
 |
 |
| Cloudflare |  |
 |
 |
 |
 |
 |
 |
 |
 |
 |
|
| Ivanti |  |
 |
 |
 |
 |
| Jamf |  |
 |
 |
 |
 |
| Lookout |  |
 |
 |
 |
 |
| Netfoundry |  |
 |
 |
 |
 |
| Palo Alto Networks |  |
 |
 |
 |
 |
| Perimeter 81 |  |
 |
 |
 |
 |
| Safe-T |  |
 |
 |
 |
 |
| Systancia |  |
 |
 |
 |
 |
In addition, in Table 2 we provide an overview which also contains four additional ratings for the vendor, going beyond the product view provided in the previous section. While the rating for Financial Strength applies to the vendor, the other ratings apply to the product.
| Vendor | Innovativeness | Market Position | Financial Strength | Ecosystem |
|---|---|---|---|---|
| Absolute Software |  |
 |
 |
 |
| Appgate |  |
 |
 |
 |
| Banyan Security |  |
 |
 |
 |
| Broadcom Inc. |  |
 |
 |
 |
| Cato Networks |  |
 |
 |
 |
| Cisco |  |
 |
 |
 |
| Cloudflare |  |
 |
 |
 |
 |
 |
 |
 |
|
| Ivanti |  |
 |
 |
 |
| Jamf |  |
 |
 |
 |
| Lookout |  |
 |
 |
 |
| Netfoundry |  |
 |
 |
 |
| Palo Alto Networks |  |
 |
 |
 |
| Perimeter 81 |  |
 |
 |
 |
| Safe-T |  |
 |
 |
 |
| Systancia |  |
 |
 |
 |
5 Product/Vendor Evaluation
This section contains a quick rating for every product/service we’ve included in this KuppingerCole Leadership Compass document. For many of the products, there are additional KuppingerCole Product Reports and Executive Views available, providing more detailed information.
Spider graphs
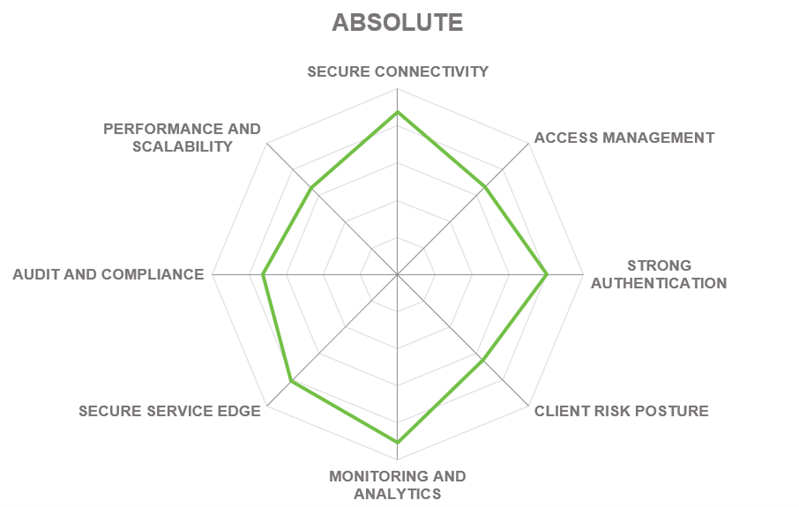
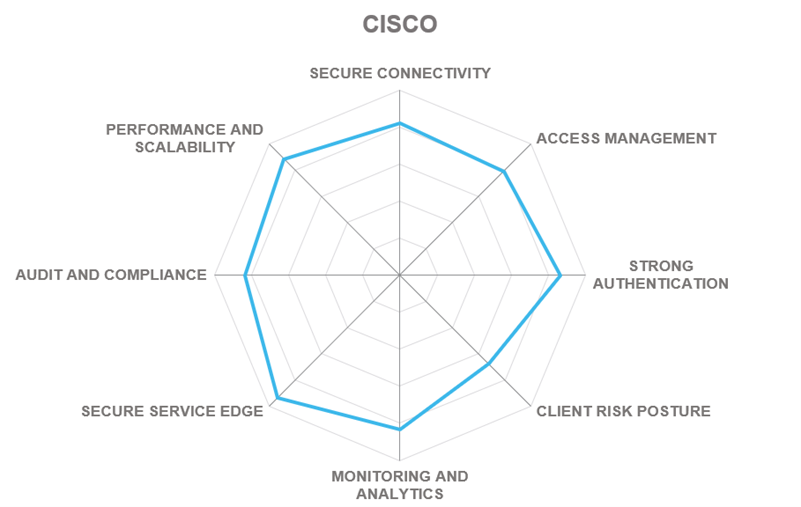
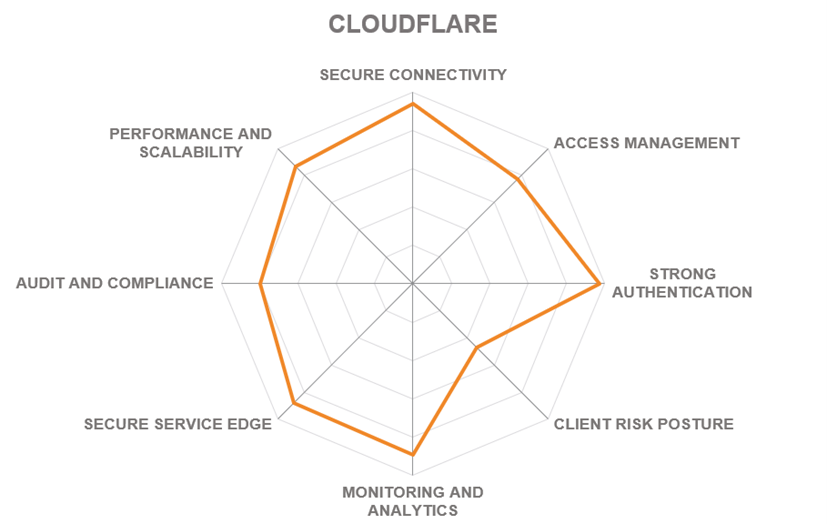
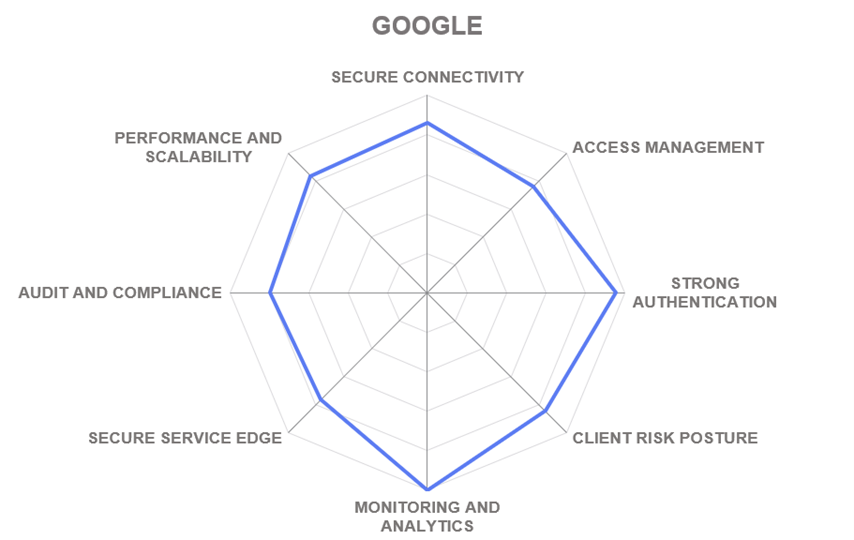
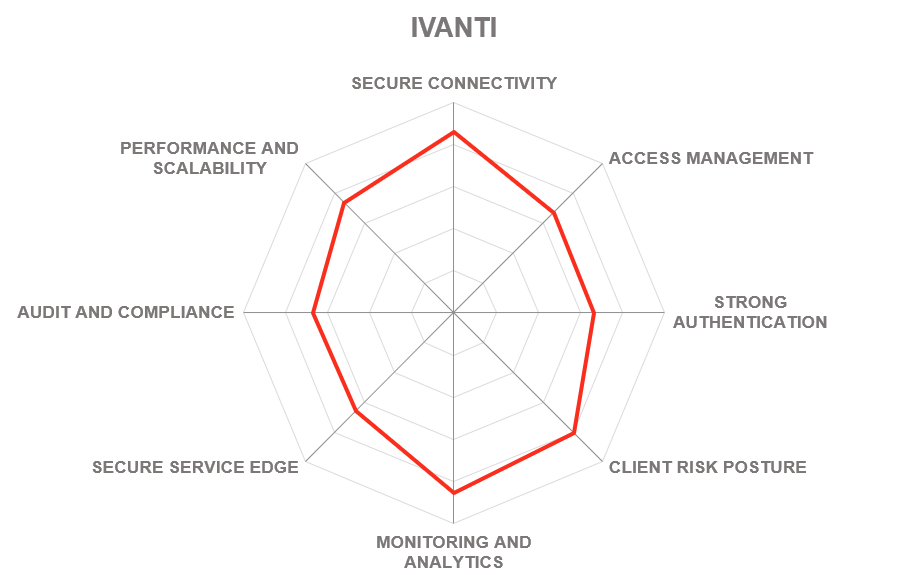
In addition to the ratings for our standard categories such as Product Leadership and Innovation Leadership, we add a spider chart for every vendor we rate, looking at specific capabilities for the market segment researched in the respective Leadership Compass. For Zero Trust Network Access solutions covered in this report, we look at the following categories:
- Secure Connectivity – all communications between resources must be secured, regardless of their locations, using end-to-end encryption of any network traffic between resources. By separating the connectivity layer from the underlying networks, ZTNA-protected resources are rendered invisible and inaccessible to unauthorized users.
- Access Management – all access decisions are performed on a per-resource basis, where resources are expected to be not entire subnets, but individual applications or even individual data records. Access to a resource is granted according to the principle of least privilege and on a per-session basis, after an explicit evaluation of trust in the requester.
- Strong Authentication – must be dynamic and strictly enforced. This includes the use of strong multi-factor authentication, scanning for cyberthreats, and re-evaluating trust before each transaction. It is driven by dynamic policies that continuously evaluate the state of the resource, requester, and other contextual attributes.
- Client Risk Posture – each access decision is made based on real-time risk evaluation that may include behavioral analysis, environmental conditions, history of previous accesses, etc. performed either using the platform’s own agent or by analyzing the telemetry collected through partnerships and integrations with third-party security vendors.
- Monitoring and Analytics – information about the current state of assets and their communications must be collected, analyzed, and used to improve the organization’s security posture. The integrity and security of all assets must be continuously monitored and deviations in security posture must be mitigated promptly.
- Secure Access Service Edge – incorporating Zero Trust Networking into cloud-delivered security platforms is a popular trend among many leading vendors currently. With this rating, we provide our overall assessment of a particular vendor’s SASE portfolio and the degree of integration of their ZTNA solutions into those.
- Audit and Compliance – regulatory compliance is a major challenge and simultaneously a business driver for organizations of any size or industry. Security data retention and comprehensive compliance reporting are the basic capabilities here. Out-of-the-box support for regulatory frameworks like GDPR, HIPAA, or PCI is a major differentiator for many customers.
- Performance and Scalability - ZTNA solutions must be able to withstand massive spikes in demand (such as the one we experienced during the COVID pandemic), adapt to complex, distributed deployments, and, of course, provide native support for cloud and hybrid scenarios.
These spider graphs provide comparative information by showing the areas where vendor services are stronger or weaker. Some products may have gaps in certain areas while being strong in other areas. These kinds of solutions might still be a good fit if only specific features are required. Other solutions deliver strong capabilities across all areas, thus commonly being a better fit for strategic implementations – for example, for powering enterprise-grade security operations centers.
5.1 Absolute Software
Absolute Software is an endpoint and network security vendor headquartered in Vancouver, British Columbia, Canada and San Jose, California, USA. Founded in 1993, the company is known primarily for its products spanning service management, endpoint security, secure access and, most recently, ransomware recovery. However, in 2021 Absolute acquired NetMotion Software, an established vendor of network security and remote access solutions. With Absolute’s endpoint security technology found in the firmware of the vast majority of commercial mobile devices, by combining the platforms, Absolute now offers a completely integrated ZTNA platform from a single hand.
Absolute Secure Access (formerly NetMotion) offers a more intelligent way to deliver secure remote access, protecting users and resources while improving the experience of working remotely. This entails full visibility outside the corporate perimeter, continuous risk assessments using multiple data points to power access policies, and restricted access to enterprise resources, no matter where they’re hosted.
Absolute Secure Access presents rich insights on the real-time experience of remote and mobile workers, providing both proactive and reactive ways of improving it. This covers diagnostics on device and network to empower helpdesk teams, rich analytics on network performance outside the corporate perimeter (from cellular to public Wi-Fi), real-time geolocation dashboards, as well as reputation and categorization of domains visited by remote workers.
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
5.2 Appgate
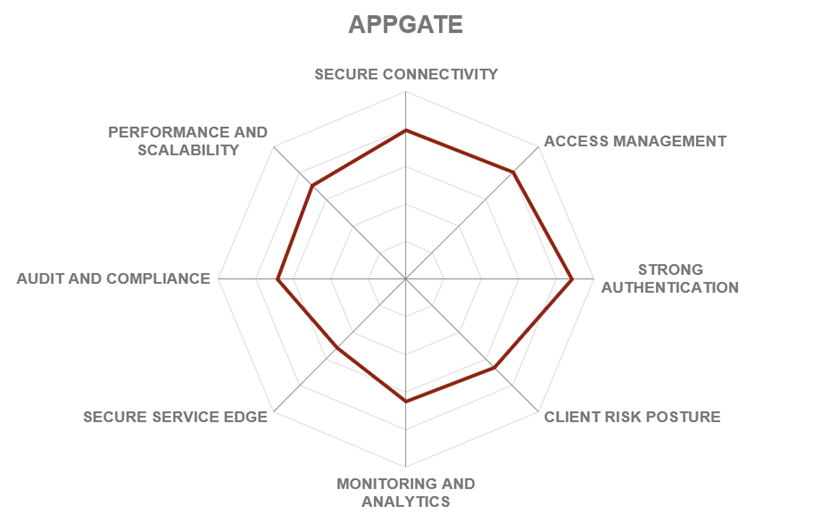
Appgate is an American software company developing cloud-ready security and analytics solutions based in Coral Gables, Florida, USA. Previously a part of Cyxtera Technologies, Appgate became an independent company in 2020. Appgate SDP, the company’s flagship product, is a comprehensive, flexible, and versatile software-defined perimeter platform with a people-centric focus, powered by an innovative and efficient networking technology.
The Appgate SDP implements a network security model that dynamically creates one-to-one network connections between the user and the resources they access. It complies with and extends beyond the three core principles of the Cloud Security Alliance’s SDP specification to deliver a cloud-native, identity-centric, network-enforced perimeter.
Replacing static access rules with dynamic, context-sensitive live entitlements, and enforcing fine-grained access control only to authorized resources, Appgate SDP delivers consistent, automated security and removes the human error factor. The Ringfence feature isolates and protects both the resource and the user device from all inbound connections, limiting exposure to malicious actors.
The whole solution is engineered to operate natively in the cloud, with a completely decentralized, distributed, stateless network architecture. However, on-prem and hybrid deployments are fully supported to enable use cases in highly regulated industries.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
5.3 Banyan Security
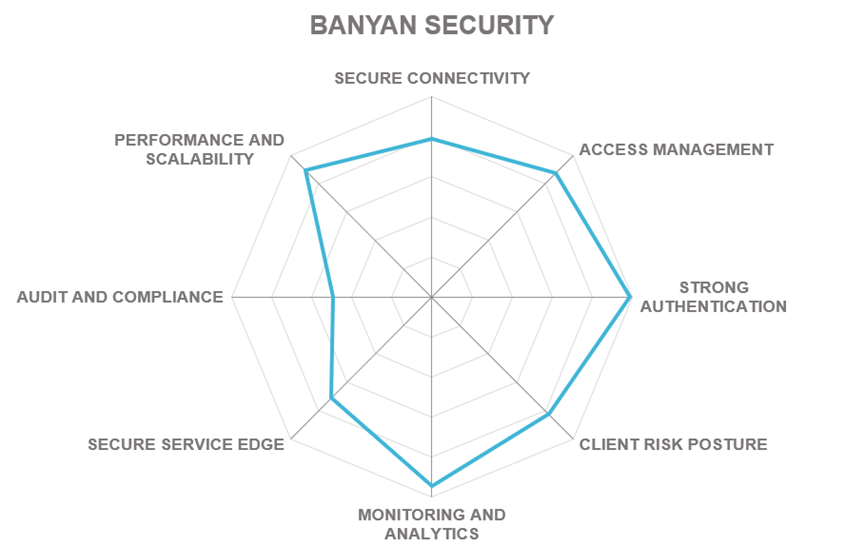
Banyan Security is a US-based cybersecurity company providing secure and seamless solutions for remote and on-premises access to corporate resources. Founded in 2015, it is headquartered in San Francisco, California, USA. With a strong focus on hybrid and multi-cloud deployment scenarios, Banyan’s Zero Trust Remote Access platform can adapt to the requirements of customers of any size or vertical.
Banyan Security’s Zero Trust Remote Access platform is a ZTNA solution that protects company resources by enabling least-privilege access to hosted applications and infrastructure based on real-time contextual factors including user and device trust scoring and resource sensitivity. Banyan is safely and securely enabling remote work for the modern, largely hybrid, enterprise, leveraging a proprietary trust scoring methodology during initial authentication and continuously re-authorizes access based on real-time contextual information.
The Banyan Distributed Access Tier cloaks all corporate assets and provides granular or global, secure access within policy guidelines. The Cloud Command Center provides clear visibility and audit capabilities for IT teams to set and monitor those policies and responds in real-time to changing trust scores. It enables actionable insights through deep visibility into the apps, services, users, devices, and activities that are present.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
5.4 Broadcom
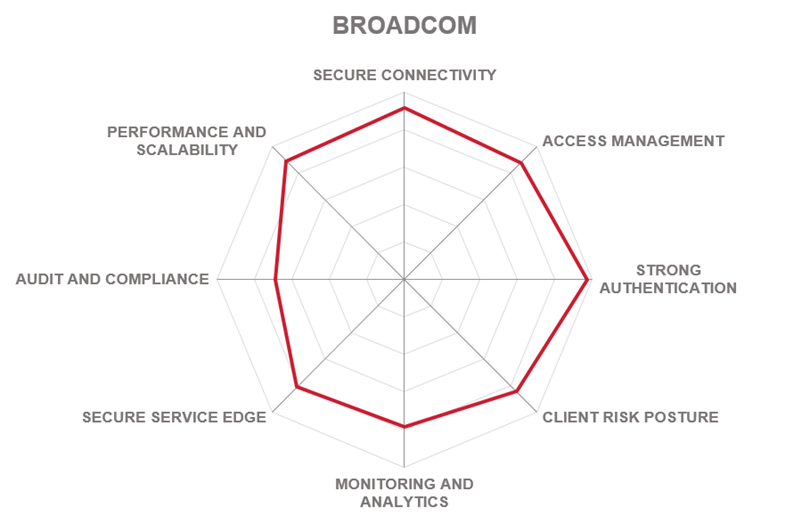
Broadcom is a large US-based manufacturer of semiconductor products and supplier of infrastructure software solutions founded in 1961 and currently headquartered in San Jose, California. In 2018, Broadcom expanded into the cybersecurity market by purchasing CA Technologies and later acquiring the enterprise security of Symantec. Nowadays, the company offers a broad portfolio of security solutions under the Symantec brand. Broadcom is operating the Symantec Secure Access Cloud, a SaaS solution that enables secure and granular access management and data governance to any corporate resource hosted on-premises or in the cloud.
Symantec Secure Access Cloud uses Zero Trust Access principles in delivering point-to-point connectivity without agents or appliances, eliminating network attack surfaces and cloaking workloads from the internet. It is a cloud-native solution that provides fast, agentless, secure access to corporate applications and resources, whether they are located in IaaS environments or on-premises data centers. Granular policies can define access controls based on user identity and device posture, as well as the sensitivity of the application being accessed, and operations performed.
Secure Access Cloud reduces complexity through a simple, agentless deployment, does not require deployment or maintenance of any security gateways or changes to existing security configurations, and easily integrates with existing identity and access management solutions. The platform supports automatic provisioning and deprovisioning of access to VMs, PaaS workloads, and applications using a cloud-native, API-driven, agent-less solution. With an optional endpoint agent, the platform integrates into the company’s broad SASE offering.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
5.5 Cato Networks
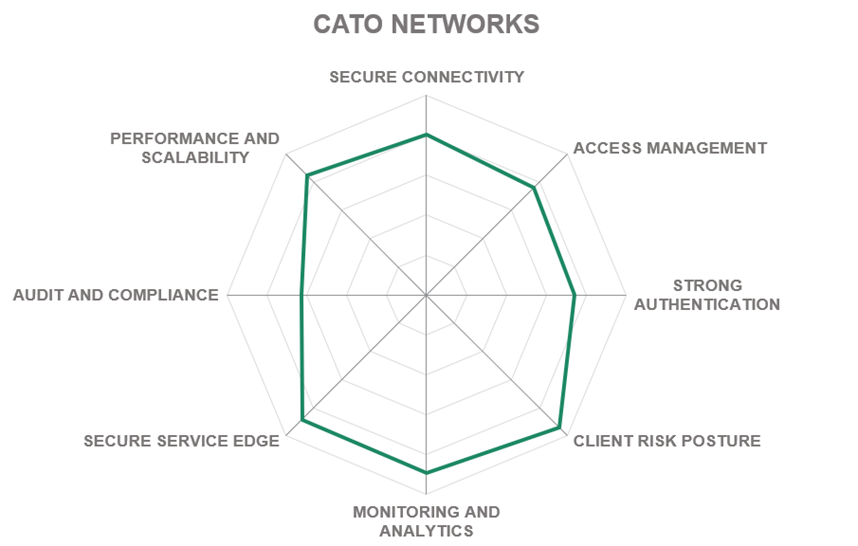
Cato Networks is a network security company founded in 2015 in Tel Aviv, Israel. Cato operates a global private backbone infrastructure, which combines SD-WAN, secure access, and managed security services in a single global security cloud. One of the pioneers of the secure edge technology, the company’s vision extends beyond ZTNA or SASE, striving to consolidate all network and security functions in its platform.
Predating the term itself, Cato claims to be the world’s first SASE platform converging SD-WAN and security into a global, cloud-native service. Cato enables enterprises to move away from a network built with rigid and expensive MPLS connectivity, a bundle of point solutions, and expensive managed services, to a unified, secure, and agile network architecture. The company’s cloud is built to handle a large amount of traffic seamlessly and elastically. With a full range of connectivity options: from agentless individual access to hardware appliances for onboarding whole offices and data centers, Cato can address the demands of the largest enterprise customers.
This new architecture enables IT and the business to rapidly address new business requirements, like global expansion, M&A, cloud migration, and workforce mobility, while reducing cost and complexity. And it enables an optimal security posture with self-evolving defense that seamlessly mitigates emerging threats. Flexible management options are also available. Unlike legacy managed network services, customers can manage the network themselves or use expert managed services from Cato or its partners.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
5.6 Cisco Systems
Cisco is a multinational technology company headquartered in San Jose, California, USA. Founded in 1984 by the pioneers of the multi-protocol network router concept, the company has quickly grown into the world’s largest manufacturer of networking hardware and telecommunications equipment. Cisco+ Secure Connect, the company’s secure access service edge offering, provides customers with a flexible choice of secure remote access capabilities to align with their requirements and use cases.
Cisco+ Secure Connect Now is a turnkey SASE solution that radically simplifies the way companies can securely access applications and resources hosted anywhere – across multiple public and private clouds – from any location at any time. Powered by Cisco Meraki and the Cisco Security Cloud, it allows customers to configure the service within minutes and monitor networking and security traffic in one place. Easy to deploy, use, and manage through a unified cloud dashboard, it can significantly reduce the complexity of an organization’s legacy IT infrastructure.
The solution includes a secure web gateway, cloud-delivered firewall, DNS-layer security, a cloud-access security broker, and data-loss prevention, with real-time proactive threat updates from Cisco Talos Intelligence, keeping users secure while alleviating IT teams from this tedious process. Cisco offers its solutions in packages that make it easy for customers to choose the right level of protection and coverage for their organizational needs.
Cisco+ Secure Connect Choice is a disaggregated SASE solution available today for organizations looking to immediately adopt SASE with flexibility for enterprise use cases. It powers the hybrid workforce and provides secure remote access with cloud security, zero trust access control, clientless access, and unified visibility. This leverages Cisco Defense Orchestrator for unified visibility and management with seamless integration with Cisco Umbrella and Cisco Duo security stack. The solution also offers deeper integration with the Cisco Viptela SD-WAN solution.
Both offers are available for customers to choose from depending on feature capabilities, consumption model, or use case.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
5.7 Cloudflare
Cloudflare is a company focusing on web infrastructure, application security, network security, network services, and serverless compute solutions headquartered in San Francisco, California. Founded in 2009, the company has quickly grown from a simple “firewall in the cloud” to one of the leading providers of website performance and security services, focusing its vision on accelerating and protecting internet, SaaS, and self-hosted applications through an intelligent global security cloud without adding hardware or installing software.
Cloudflare Access, part of the company's SASE platform Cloudflare One, connects any user to any application or network with fine-grained clientless access by enforcing identity- and context-based rules and limiting lateral movement. Users are onboarded with clientless access or via a device client that supports all major OSes (note: more office-based options available with Cloudflare's SASE platform).
Resources are onboarded using public hostnames for a reverse proxy to self-hosted apps (cloud or on-prem), an identity proxy to SaaS apps, or connector software to establish an outbound tunnel to a forward proxy with internal DNS resolution for any web or non-web resource within a private subnet. Plus, an in-browser terminal can render SSH and VNC protocols over HTTPS for simpler, safer remote access.
Connections can be secured with end-to-end encrypted tunnels and optional mutual TLS authentication. You can integrate one or more identity providers to enforce granular authentication requirements to verify user identity, verify device posture natively along with one or more endpoint protection partners, and consistently authorize micro-segmented access based on many dynamic contextual signals.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
5.8 Google
Google LLC is a multinational company specializing in internet-related products and services, known primarily for its search engine, online advertising technologies, and cloud computing services. Launched in 2008, Google Cloud is the company’s suite of cloud computing infrastructure services, which also powers Google’s own SaaS offerings. It is recognized as one of the leading public cloud service providers.
Google Cloud’s BeyondCorp Enterprise solution, based on the BeyondCorp framework introduced over a decade ago, is essentially the first practical implementation of Zero Trust, that has been successfully deployed and operated at a large scale by Google itself, securing access for over 150 thousand full-time employees, not including the vendors/contractors Google works with. A comprehensive ZTA solution, it enables secure access with integrated threat and data protection with a strong focus on a proxyless and agentless implementation: The Google Chrome Browser acts as the platform’s agent, even on unmanaged devices.
Built on the backbone of Google’s cloud infrastructure and global network, BeyondCorp Enterprise is able to provide a seamless and secure experience with integrated DDoS protection, low-latency connections, and elastic scaling even for the largest and most complex enterprise deployments. Among the most recently added capabilities are the client connector, which enables secure access to non-web/thick-client applications and the app connector, which provides secure connectivity to applications hosted in multi-cloud environments (e.g. AWS, Azure).
The platform is designed for quick and easy rollout that does not require additional hardware, software, or network changes and can support most common ZT use cases, such as enabling employees to access SaaS applications safely and securely from virtually any device; supporting contractors, vendors, and other external identities with secure access to corporate resources; and protect endpoint devices from phishing and ransomware.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
5.9 Ivanti
Ivanti is a software company specializing in IT asset and service management, supply chain management, and IT security headquartered in South Jordan, Utah. Although established in 2017, the company’s history can be traced back to the 1980s under the name LANDESK. Through a substantial number of recent acquisitions, the company has created a broad portfolio of solutions for discovering, managing, and securing IT assets. All these technologies are now offered as parts of Ivanti Neurons, a unified workspace hyperautomation platform powered by machine learning.
In 2020, Ivanti acquired Pulse Secure, a provider of secure access solutions ranging from VPN to ZTNA. Nowadays, this technology forms the basis of Ivanti Neurons for Zero Trust Access, a part of the company’s unified endpoint management offering that comprises a full range of secure access options, as well as mobile device management, secure productivity, and other capabilities.
Ivanti Neurons for Zero Trust Access (nZTA) creates a secure connection from the enrolled device to applications on-premises and in the cloud, which enhances security, productivity, and compliance while dramatically improving administrative and end-user experiences. All connections between end user devices, cloud controller and gateways are secured with strong authentication with mTLS. With continuous authentication and fine-grained authorization for devices, and applications according to flexible, business-oriented constraints, it maintains adaptive control, micro-segmentation ability, and a reduced attack surface.
With nZTA, customer data never flows through Ivanti’s infrastructure, reducing the strain on corporate bandwidth and eliminating data charges on SWGs and CASBs. However, integrations with SASE capabilities are supported. A strong focus is placed on flexible coexistence with existing VPNs and gradual, policy-based migration processes that do not affect user productivity.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
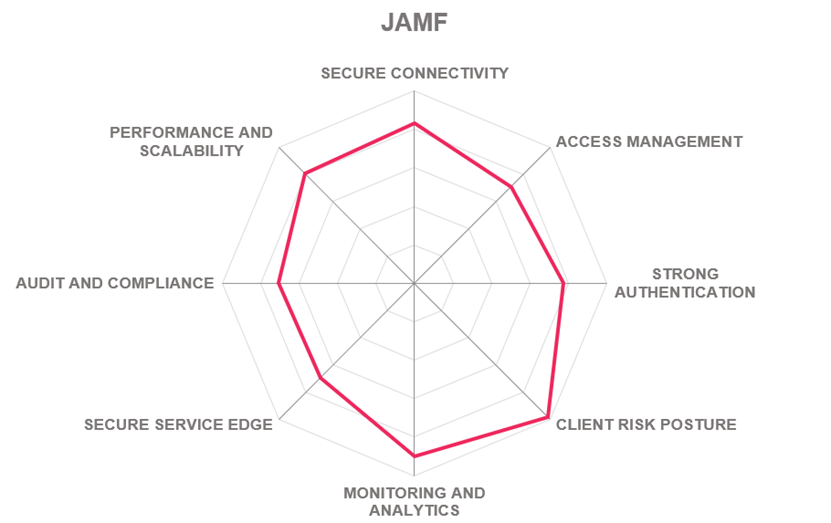
5.10 Jamf
Jamf is a software vendor primarily known for device management and security solutions for Apple devices. Established in 2002, Jamf is headquartered in Minneapolis, Minnesota, USA, serving over 60 thousand customers around the globe and running on over 27 million devices. In 2021, Jamf acquired Wandera, a Zero Trust cloud security company, bringing its technology to a much wider customer base.
Jamf Private Access is the company’s entirely cloud-delivered ZTNA platform with a strong focus on a seamless, transparent mobile worker experience. It provides secure remote access to applications using Zero Trust principles, whether those applications are hosted in the data center or the cloud. The user experience is consistent wherever the application is running, and from whichever device the user connects.
Private Access uses app-level dynamic split tunnels, enabling fine-grained control both at connection establishment and throughout active sessions. Through the least-privilege enforcement and real-time device posture checks, access is granted to each application only for specific, authorized users. Optimized for mobile workers, Private Access makes connecting security fast, versatile, and lightweight, by providing a silent and seamless service even if the user is working while on the move.
The platform offers a broad range of real-time statistics that provide insight into unusual activity, session duration, or bandwidth requirements. Comprehensive visibility allows administrators to monitor inappropriate content, detect malware and identify data leaks.
Jamf’s notable differentiator has always been its long-term strategic focus on mobile platforms and specifically, the Apple device ecosystem. However, the ZTNA platform extends support to all major desktop and mobile operating systems, including Android, Windows, and MacOS.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
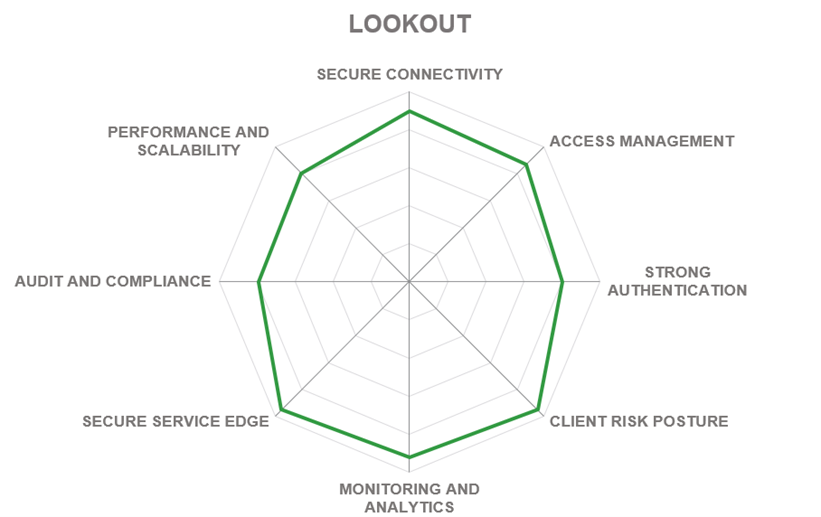
5.11 Lookout
Lookout is a cybersecurity provider of endpoint and cloud security solutions based in San Francisco, California, USA. Originally one of the pioneers in mobile security (established in 2002), over the years, Lookout has grown into an integrated endpoint-to-cloud security company. The acquisition of CipherCloud in 2021 made the company expand into the market for zero-trust network access solutions. Nowadays, Lookout provides a unified security platform that enables secure and protected access to sensitive applications from any device.
Lookout Zero Trust Network Access (ZTNA) is a part of the company’s SASE Platform that delivers a Zero Trust solution for any app that dynamically adapts based on data sensitivity and continuous risk assessment of endpoints and users.
In addition, Lookout ZTNA combines DLP content inspection, threat prevention, and advanced UEBA with popular access controls to private applications. The platform's unique risk-based Continuous Conditional Access enables customers to protect sensitive data, especially against leaks on unmanaged devices.
Lookout ZTNA integrates with multi-factor authentication and identity solutions to reduce user friction and improve overall access controls. The same strong authentication security benefits associated with SaaS applications and web services can be extended to cover legacy, IaaS, and private applications.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
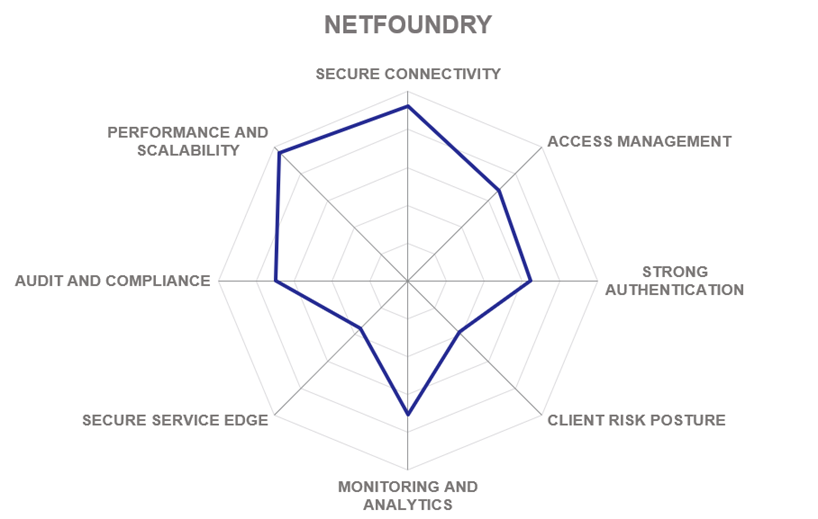
5.12 NetFoundry
NetFoundry is a network security vendor based in Charlotte, North Carolina, USA. The company was founded in 2016 to address a major shortcoming of existing Zero Trust solutions – by making secure networking an innovation enabler that anyone can use (not just network engineers). At the core of NetFoundry’s solution is OpenZiti – an open-source programmable Zero Trust networking stack which can be applied to any use case. On top of this free foundation, the company offers a commercial SaaS platform for centralized deployment and management of ZTNA networks.
NetFoundry is an open core platform built on the OpenZiti project that enables private connectivity to be embedded at the app. OS, or network level for any use case including even VoIP. Endpoinyts use embedded identity (X.509) and authentication/authorization before establishing outbound-only connections from the edge, as well as application micro-segmentation, E2E encryption, metadata obfuscation, and continual authorization that utilizes smart routing on the mesh overlay.
NetFoundry is a fully managed SaaS platform for OpenZiti, backed by SLAs and field-proven performance. This includes automation & orchestration engine, monitoring, enterprise support, global backbone, open APIs, pre-built IAC modules, and integrations. With five levels of abstraction built into the platform architecture, even complex multi-cloud multi-tenant deployments with multiple isolation layers between customers or organizational units can be set up in minutes and operated transparently and securely.
Embedded Zero Trust networking represents a shift in thinking about the relationship between the application and the network. Now every application is able to spawn private, programmable, app-specific, zero-trust overlays, specific to each session – regardless of the underlying network or cloud environment to deliver a secure and transparent user experience.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
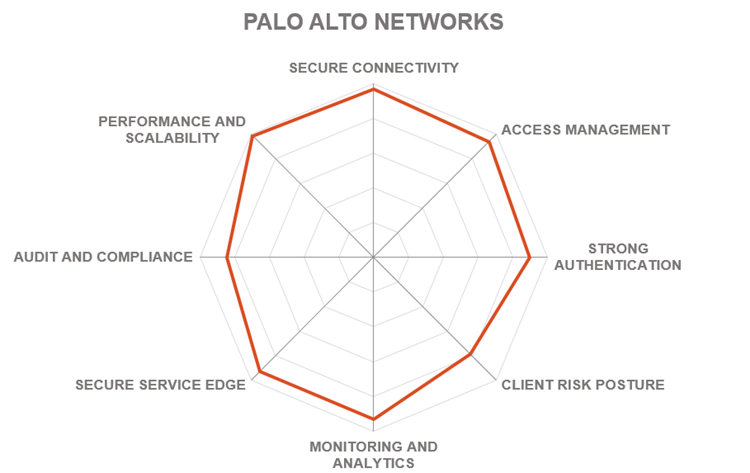
5.13 Palo Alto Networks
Palo Alto Networks is a multi-national cybersecurity company, a leading provider of both traditional network security tools and modern cloud-native security solutions. Founded in 2005, the company is headquartered in Santa Clara, California, USA. Among the company’s products, Prisma Access solution is an integrated cloud-native security platform that combines advanced “ZTNA 2.0” with a full range of secure service edge capabilities.
Prisma Access is a single converged cloud-delivered platform transforming network security and allowing organizations to quickly and easily enable secure hybrid workforces. The cloud-native architecture of Prisma Access ensures on-demand and elastic scale of comprehensive networking and security services across a global, high-performance network. Prisma Access provides the foundation for consistent cloud-delivered security for all users and locations.
The “ZTNA 2.0” paradigm recently introduced by Palo Alto Networks is pushing for an advanced combination of zero trust access and security capabilities that enable more secure and fine-grained access policies, which can, for example, be fine-tuned at the sub-app level or even grant access to specific areas or functions of existing applications. At the same time, Prisma Access is focused on enabling data protection across all enterprise applications (native apps, legacy private apps, and SaaS) with a single DLP policy.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
5.14 Perimeter 81
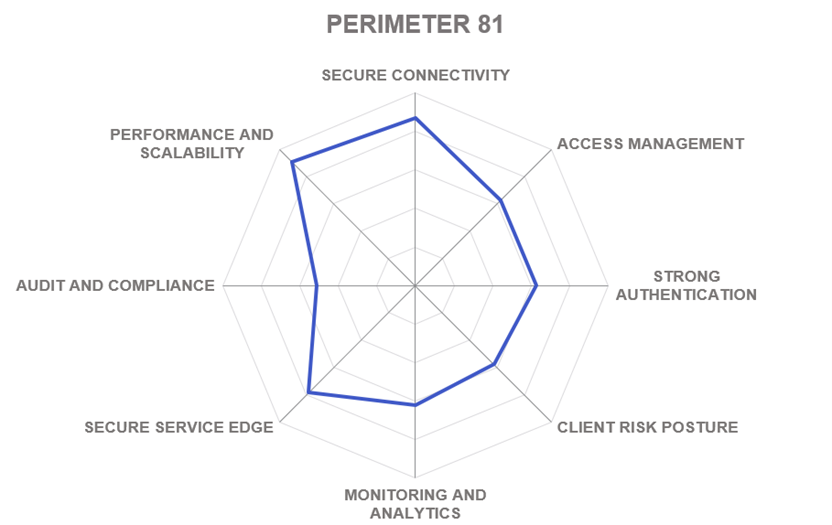
Perimeter 81 is a cloud and network security company specializing in secure remote access and internet security solutions solutions based on the Zero Trust architecture headquartered in Tel Aviv, Israel with offices on both East and West coasts in the USA. Since 2018, the company has been offering its converged networking and security cloud edge to a broad range of customers around the world. Perimeter 81 supports integrations with many 3rd party vendors and a wide variety of devices and operating systems. Its offering includes Zero Trust corporate application access as well as Firewall as a Service and a Secure Web Gateway consolidated with ZTNA in a simple, easy-to-use SaaS platform.
The Perimeter 81 Platform provides a cloud-based SaaS networking and security platform delivered and managed over a multi-tenant cloud, providing a secure and highly scalable network for organizations everywhere. The platform implements user-centric ZTNA functionality, allowing easy security and network policy implementation based on integrated IdP functionality. Agent and agentless access are supported, and all policies and networks can be administered in a single console.
Security functionality currently includes Firewall as a Service, Device Posture Security, DNS filtering, Secure Web Gateway and more. However, the company is working hard on adding other capabilities (such as cloud access security broker, and endpoint security) into the platform. We expect Perimeter 81 to formally introduce its own SASE offering later this year.
Perhaps the biggest Perimeter 81’s differentiator is its large and passionate customer base. The company is recognized for the quality of its customer engagements, technical support, and responding to new feature requests.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
5.15 Safe-T
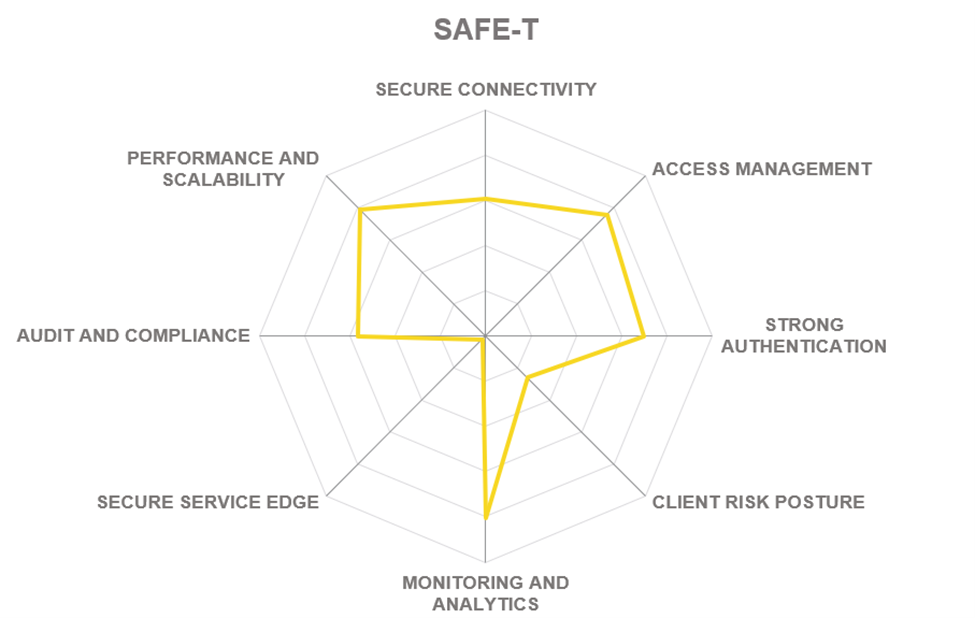
Safe-T is a software vendor providing secure remote access solutions that mitigate attacks on critical enterprise applications and sensitive data. Founded in 2013 and based in Herzliya, Israel, the company is focused on delivering on a vision of a universal secure access solution that is fully protocol-agnostic, always clientless, and ready to address any customer scenario.
Safe-T ZoneZero is a device-agnostic clientless solution built and designed to support Bring Your Own Device (BYOD) and allow users to connect from any endpoint. With ZoneZero, organizations can implement secure and transparent access to any internal application, service, or data source either in parallel to, or instead of, an existing VPN.
Safe-T’s unique alternative approach towards ZTNA is dispensing with traffic management completely and instead, implementing access control to applications and resources using local gateways controlling port forwarding. While this arguably limits the potential use cases for the solution (for example, there is no possibility to package it as a SaaS offering), ZoneZero’s ease of deployment and management in on-prem scenarios is unbeatable.
The platform offers secure and transparent access for all types of entities (people, applications, connected devices) to any internal application, service, or data source, supporting any TCP-based protocol. Recently, Safe-T has partnered with Terrazone and DreamVPS to launch Virtual Private Workforce as a managed service that aims to enable secure and seamless collaboration for remote R&D teams and programs.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
5.16 Systancia
Systancia is a software vendor specializing in secure remote access and workspace solutions based in Sausheim, France, making it the only European vendor in our rating. Founded in 1998 and originally focusing on virtual desktop infrastructure (VDI), the company has expanded into identity management and zero trust access solutions through later acquisitions. Systancia is the only software vendor combining ZTNA and PAM within the same platform, as an extension to each other. Additionally, VDI/RBI type technologies are leveraged in cybersecurity for “isolation” of the user device from the organization’s IT.
Systancia Gate is a full-featured private network access solution with a unique double barrier architecture and a strong emphasis on regulatory compliance. Systancia delivers its offering as software products or as a cloud service platform, often in hybrid deployment models.
Certified by the French cybersecurity agency ANSSI, Systancia Gate offers a single portal for secure access to all applications, on-premises, or in the cloud. Based on this foundation, the company also offers cyberelements.io – a fully managed SaaS platform to provide all types of users with seamless and immediate access (standard, privileged, local, remote) to all resources they need to work. Combined with other Systancia’s products for virtual desktop, privileged access, and IAM, these form a broad portfolio of services to enable secure remote work certified for the most regulated industries.
The platform allows customers to solve multiple use cases ranging from simple VPN replacement and privileged access audit to complex problems of business continuity, service provider access, and cloud migration. Systancia’s differentiating feature is the double barrier architecture, which introduces additional mediation servers between control and data planes. This allows for more simplified, yet highly available deployments compared to traditional ZTNA architectures.
Both users and privileged admins are served by the same universal access portal that provides a consistent user experience, universal management and visibility into all activities, and strong authentication – all without the need for a dedicated agent. Recently, the company has invested a lot of effort into AI-powered behavioral analytics and threat detection that serves as the feedback loop for continuous authentication within the platform.

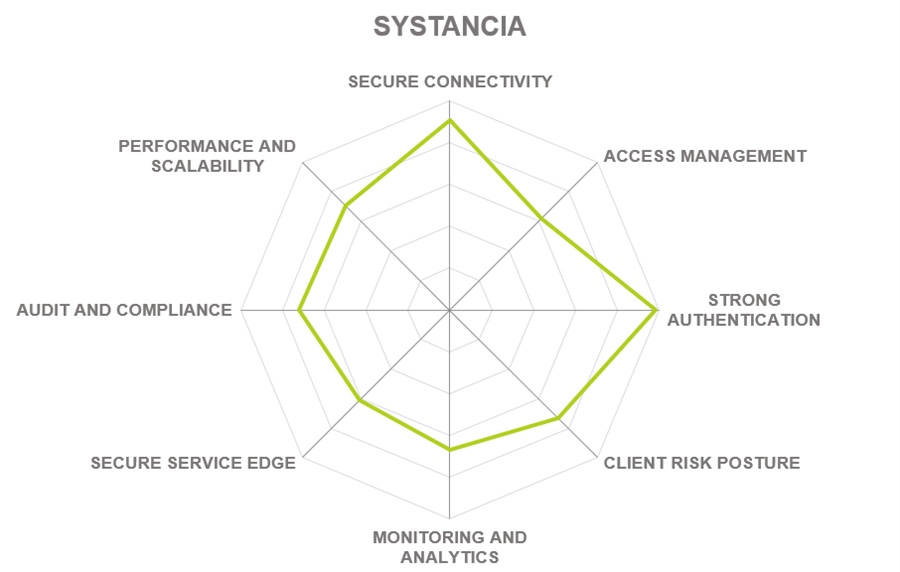
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
6 Vendors to Watch
Aside from the vendors covered in detail in our rating, we also observe other vendors in the market that we find interesting. Some decided not to participate in this KuppingerCole Leadership compass for various reasons, while others are interesting vendors that do not fully fit into our definition of the market segment or are not yet mature enough to be considered in this evaluation. We provide short descriptions of these vendors and their respective products below.
6.1 Akamai
Akamai Technologies is a content delivery network and cloud service provider headquartered in Cambridge, Massachusetts, USA. Founded in 1998, the company is one of the veteran players on the market, providing a broad range of performance-, security- and even productivity-related services through its content delivery network (CDN), one of the world’s largest distributed computing platforms within direct reach of over 90% Internet users around the world.
Why worth watching: with its massive global edge infrastructure, integrations with all notable identity providers, and a strong focus on programmatical application onboarding, Akamai Enterprise Access is uniquely suited for large enterprises with hundreds of business applications and complex business requirements.
6.2 Citrix
Citrix Systems, founded in 1989 and headquartered in Fort Lauderdale, Florida, USA, is a well-established cloud computing and virtualization vendor with a strong customer base. Citrix has a global partner ecosystem and continues to innovate its solutions in the areas of workspaces, virtual apps and desktops, as well as optimizing the delivery of applications over the Internet and private networks.
Why worth watching: As a leader in providing solutions for supporting hybrid workforce productivity, Citrix offers full access and security coverage for enterprises, which covers unmanaged and BYOD devices as well. Citrix Secure Private Access is part of the company’s portfolio that implements cloud-delivered ZTNA to support these scenarios.
6.3 Forcepoint
Forcepoint is a cybersecurity corporation headquartered in Austin, Texas. Although established in 2016, the company traces its roots back to Websense, a major provider of network security solutions since the late 1990s. In 2015, the company became a subsidiary of Raytheon, a major US defense contractor, but became private again in October 2020. Forcepoint offers a range of “human-centric” data protection, network, and cloud security products.
Why worth watching: Forcepoint ONE is an all-in-one cloud-native security platform that consolidates threat protection and data security, access policy management, and enforcement, and a range of cloud-delivered security solutions like SWG, CASB and ZTNA built on the common foundation.
6.4 Fortinet
Fortinet is an American cybersecurity company with headquarters in Sunnyvale, California, USA. Established in 2000, it provides a wide range of network security and SD-WAN, switching and wireless access, network access control, authentication, public and private cloud security, endpoint security, and AI-driven advanced threat protection solutions for carriers, data centers, enterprises, and distributed offices. Its solutions are integrated into the Fortinet Security Fabric.
Why worth watching: Fortinet’s product strategy is based on the concept of Cybersecurity Fabric, an integrated, automated platform that unifies networking, security, and access capabilities in a mesh-like architecture. Fortinet Zero Trust Access solution delivers all the necessary components of ZTNA from this unified portfolio.
6.5 Menlo Security
Menlo Security is a cybersecurity vendor headquartered in Mountain View, California, USA. The company’s portfolio of solutions is based on an integrated isolation-powered cloud security platform. It utilizes a broad range of security capabilities like secure web gateway, e-mail isolation, firewall-as-a-service and private access to separate any kind of malicious content from users entirely.
Why worth watching: predating the notion of a secure service edge, Menlo security platform goes beyond the popular idea of SASE by offering a fully integrated cloud-native platform that combines web security, secure remote access, and security operations into a single product that grows with customer requirements.
6.6 Netskope
Netskope, founded in 2012, is a cloud-native security vendor based in Santa Clara, California with offices across the US, UK, Australia, India, Singapore, and Japan. Netskope’s Security Cloud combines comprehensive visibility, data protection, and threat prevention for websites, cloud services, and enterprise applications.
Why worth watching: Netskope Private Access, the company’s ZTNA offering, is delivered as an integral part of Netskope Secure Service Edge, a cloud platform that combines CASB, SWG, FWaaS, and ZTNA with a single client, a universal policy engine, and a unified management console.
6.7 Proofpoint
Proofpoint is a security and compliance company founded in 2002 and based in Sunnyvale, California. The company offers a range of solutions for data loss prevention, advanced threat protection, and compliance. More recently, the company has expanded its portfolio to cloud security, offering solutions for cloud app protection and secure access.
Why worth watching: Proofpoint Zero Trust Network Access is the company’s enterprise-level, people-centric ZTNA platform focusing on solving popular business cases like accelerating cloud migration, segmenting access to critical application, and facilitating mergers and acquisitions.
6.8 Sophos
Sophos Group is a security software and hardware vendor headquartered in Abington, UK. Founded in 1985 as one of the pioneers of the antivirus market, Sophos currently offers a broad portfolio of cybersecurity tools, including solutions for endpoint, mobile, and network security, as well as unified threat management. Sophos provides a single integrated cloud-based management console, Sophos Central, for all its products and services.
Why worth watching: Sophos ZTNA is the company’s cloud-managed zero-trust network access solution; its major benefit is the high degree of integration with the company’s endpoint security platform, Intercept X. Customers only need to deploy a single agent and can manage the whole portfolio using a single console.
6.9 Tailscale
Tailscale is a software-defined networking vendor headquartered in Toronto, Canada. Since 2019, the company is offering a point-to-point secure mesh network service, which is based on the open-source WireGuard protocol complemented by a cloud-based management interface. The solution is based on the freemium model, supporting any customer tier, from personal use to large enterprise deployments.
Why worth watching: Tailscale provides a “next-gen VPN” service that requires no configuration, can be deployed in minutes and integrates with a wide range of identity providers. The solution supports a hybrid configuration combining traditional subnet access with Zero Trust, making step-by-step migration easy.
6.10 Twingate
Twingate is a software company with a home base in Redwood City, California, USA and a largely remote international team based in both North America and Europe. Founded in 2019, the company has a mission of making implementing Zero Trust easy, secure, and performant.
Why worth watching: Twingate was designed from the beginning to be fully distributed and decentralized with native automation capabilities. No single component can independently make a decision to allow traffic to flow to another component or resource in your remote networks. Twingate’s SDP implementation rivals not only traditional VPN solutions but even other SaaS platforms considered legacy for their high level of centralization.
6.11 VMware
VMware is an international cloud computing, virtualization, endpoint security, and software-defined network vendor headquartered in Palo Alto, California. Founded in 1998, the company was an early pioneer in hardware virtualization technology. VMware offers a broad portfolio of security tools.
Why worth watching: VMware Secure Access, the company’s ZTNA solution, is a part of a unified Anywhere Workspace platform that combines distributed workforce management, secure remote access, and comprehensive security capabilities – all delivered from the cloud.
6.12 Zentera
Zentera Systems is a Zero Trust solution vendor founded in 2012 and headquartered in Milpitas, California, USA with most of the R&D taking place in Taipei, Taiwan. Zentera positions itself apart from other ZTNA vendors by offering several unique design approaches to its platform.
Why worth watching: The company’s CoIP Access Platform is designed to bring security capabilities closer to endpoints and applications, as opposed to delivering them from the cloud. In a way, Zentera’s architecture is the direct opposite of the “traditional SASE” solutions, focusing on reducing the management complexity of large deployments and to incorporating cybersecurity and data loss protection directly into the network overlay.
6.13 Zero Networks
Zero Networks is a network security vendor headquartered in Tel Aviv, Israel. Founded in 2019, the company is focused on securing existing corporate networks with a combination of micro-segmentation and multi-factor authentication to enforce least-privilege networking as scale.
Why worth watching: The company’s Access Orchestrator combines fully agentless enforcement with flexible out-of-band monitoring and automation to ensure that only non-risky network access is allowed, while privileged or abnormal activities must be authenticated first. The product is designed to coexist with any kind of network connectivity and to provide uniform protection against lateral movement and ransomware attacks both on-premises and in the cloud.
6.14 Zscaler
Zscaler is a global information security company that provides an integrated cloud-based platform for Internet security, compliance, advanced threat protection, and other information security services. Founded in 2008, the company is headquartered in San Jose, California.
Why worth watching: Zscaler was one of the first vendors to introduce the notion of “security cloud”, currently operating one of the largest specialized cloud security platforms. As one of the most deployed ZTNA solutions, Zscaler offers a combination of multilayered application protection capabilities (even including deception) with a seamless user experience and performance.
7 Related Research
Market Compass: Cloud-delivered Security
Market Compass: Cloud Access Security Brokers
Advisory Note: Implementing SASE
Advisory Note: Firewalls Are Dead - How to Build a Resilient, Defendable Network
Whitepaper: Security Operations in the Age of Zero Trust
Insight: Enterprise Guide to Zero Trust Implementation
Navigator: Zero Trust
Analyst Chat #117: Practical Zero Trust
Executive View: Akamai Zero Trust Security
Executive View: Cisco Zero Trust Security
Executive View: Google's Cloud Identity
Executive View: Safe-T Software Defined Access
Executive View: Zscaler Security-as-a-Service Platform
Blog: Ivanti’s Zero Trust Journey
8 Methodology
8.1 About KuppingerCole's Leadership Compass
KuppingerCole Leadership Compass is a tool which provides an overview of a particular IT market segment and identifies the leaders within that market segment. It is the compass which assists you in identifying the vendors and products/services in that market which you should consider for product decisions. It should be noted that it is inadequate to pick vendors based only on the information provided within this report.
Customers must always define their specific requirements and analyze in greater detail what they need. This report doesn’t provide any recommendations for picking a vendor for a specific customer scenario. This can be done only based on a more thorough and comprehensive analysis of customer requirements and a more detailed mapping of these requirements to product features, i.e. a complete assessment.
8.2 Types of Leadership
We look at four types of leaders:
- Product Leaders: Product Leaders identify the leading-edge products in the particular market. These products deliver most of the capabilities we expect from products in that market segment. They are mature.
- Market Leaders: Market Leaders are vendors which have a large, global customer base and a strong partner network to support their customers. A lack in global presence or breadth of partners can prevent a vendor from becoming a Market Leader.
- Innovation Leaders: Innovation Leaders are those vendors which are driving innovation in the market segment. They provide several of the most innovative and upcoming features we hope to see in the market segment.
- Overall Leaders: Overall Leaders are identified based on a combined rating, looking at the strength of products, the market presence, and the innovation of vendors. Overall Leaders might have slight weaknesses in some areas, but they become Overall Leaders by being above average in all areas.
For every area, we distinguish between three levels of products:
- Leaders: This identifies the Leaders as defined above. Leaders are products which are exceptionally strong in certain areas.
- Challengers: This level identifies products which are not yet Leaders but have specific strengths which might make them Leaders. Typically, these products are also mature and might be leading-edge when looking at specific use cases and customer requirements.
- Followers: This group contains vendors whose products lag in some areas, such as having a limited feature set or only a regional presence. The best of these products might have specific strengths, making them a good or even best choice for specific use cases and customer requirements but are of limited value in other situations.
Our rating is based on a broad range of input and long experience in that market segment. Input consists of experience from KuppingerCole advisory projects, feedback from customers using the products, product documentation, and a questionnaire sent out before creating the KuppingerCole Leadership Compass, and other sources.
8.3 Product Rating
KuppingerCole Analysts AG as an analyst company regularly evaluates products/services and vendors. The results are, among other types of publications and services, published in the KuppingerCole Leadership Compass Reports, KuppingerCole Executive Views, KuppingerCole Product Reports, and KuppingerCole Vendor Reports. KuppingerCole uses a standardized rating to provide a quick overview on our perception of the products or vendors. Providing a quick overview of the KuppingerCole rating of products requires an approach combining clarity, accuracy, and completeness of information at a glance.
KuppingerCole uses the following categories to rate products:
- Security
- Functionality
- Deployment
- Interoperability
- Usability
Security is primarily a measure of the degree of security within the product/service. This is a key requirement. We look for evidence of a well-defined approach to internal security as well as capabilities to enable its secure use by the customer, including authentication measures, access controls, and use of encryption. The rating includes our assessment of security vulnerabilities, the way the vendor deals with them, and some selected security features of the product/service.
Functionality is a measure of three factors: what the vendor promises to deliver, the state of the art and what KuppingerCole expects vendors to deliver to meet customer requirements. To score well there must be evidence that the product / service delivers on all of these.
Deployment is measured by how easy or difficult it is to deploy and operate the product or service. This considers the degree in which the vendor has integrated the relevant individual technologies or products. It also looks at what is needed to deploy, operate, manage, and discontinue the product / service.
Interoperability refers to the ability of the product / service to work with other vendors’ products, standards, or technologies. It considers the extent to which the product / service supports industry standards as well as widely deployed technologies. We also expect the product to support programmatic access through a well-documented and secure set of APIs.
Usability is a measure of how easy the product / service is to use and to administer. We look for user interfaces that are logically and intuitive as well as a high degree of consistency across user interfaces across the different products / services from the vendor.
We focus on security, functionality, ease of delivery, interoperability, and usability for the following key reasons:
- Increased People Participation: Human participation in systems at any level is the highest area of cost and the highest potential for failure of IT projects.
- Lack of excellence in Security, Functionality, Ease of Delivery, Interoperability, and Usability results in the need for increased human participation in the deployment and maintenance of IT services.
- Increased need for manual intervention and lack of Security, Functionality, Ease of Delivery, Interoperability, and Usability not only significantly increase costs, but inevitably lead to mistakes that can create opportunities for attack to succeed and services to fail.
KuppingerCole’s evaluation of products / services from a given vendor considers the degree of product Security, Functionality, Ease of Delivery, Interoperability, and Usability which to be of the highest importance. This is because lack of excellence in any of these areas can result in weak, costly and ineffective IT infrastructure.
8.4 Vendor Rating
We also rate vendors on the following characteristics
- Innovativeness
- Market position
- Financial strength
- Ecosystem
Innovativeness is measured as the capability to add technical capabilities in a direction which aligns with the KuppingerCole understanding of the market segment(s). Innovation has no value by itself but needs to provide clear benefits to the customer. However, being innovative is an important factor for trust in vendors, because innovative vendors are more likely to remain leading-edge. Vendors must support technical standardization initiatives. Driving innovation without standardization frequently leads to lock-in scenarios. Thus, active participation in standardization initiatives adds to the positive rating of innovativeness.
Market position measures the position the vendor has in the market or the relevant market segments. This is an average rating over all markets in which a vendor is active. Therefore, being weak in one segment doesn’t lead to a very low overall rating. This factor considers the vendor’s presence in major markets.
Financial strength even while KuppingerCole doesn’t consider size to be a value by itself, financial strength is an important factor for customers when making decisions. In general, publicly available financial information is an important factor therein. Companies which are venture-financed are in general more likely to either fold or become an acquisition target, which present risks to customers considering implementing their products.
Ecosystem is a measure of the support network vendors have in terms of resellers, system integrators, and knowledgeable consultants. It focuses mainly on the partner base of a vendor and the approach the vendor takes to act as a “good citizen” in heterogeneous IT environments.
Again, please note that in KuppingerCole Leadership Compass documents, most of these ratings apply to the specific product and market segment covered in the analysis, not to the overall rating of the vendor.
8.5 Rating Scale for Products and Vendors
For vendors and product feature areas, we use a separate rating with five different levels, beyond the Leadership rating in the various categories. These levels are
- Strong positive: Outstanding support for the subject area, e.g. product functionality, or outstanding position of the company for financial stability.
- Positive: Strong support for a feature area or strong position of the company, but with some minor gaps or shortcomings. Using Security as an example, this can indicate some gaps in fine-grained access controls of administrative entitlements. For market reach, it can indicate the global reach of a partner network, but a rather small number of partners.
- Neutral: Acceptable support for feature areas or acceptable position of the company, but with several requirements we set for these areas not being met. Using functionality as an example, this can indicate that some of the major feature areas we are looking for aren’t met, while others are well served. For Market Position, it could indicate a regional-only presence.
- Weak: Below-average capabilities in the product ratings or significant challenges in the company ratings, such as very small partner ecosystem.
- Critical: Major weaknesses in various areas. This rating most commonly applies to company ratings for market position or financial strength, indicating that vendors are very small and have a very low number of customers.
8.6 Inclusion and Exclusion of Vendors
KuppingerCole tries to include all vendors within a specific market segment in their Leadership Compass documents. The scope of the document is global coverage, including vendors which are only active in regional markets such as Germany, Russia, or the US.
However, there might be vendors which don’t appear in a Leadership Compass document due to various reasons:
- Limited market visibility: There might be vendors and products which are not on our radar yet, despite our continuous market research and work with advisory customers. This usually is a clear indicator of a lack in Market Leadership.
- Declined to participate: Vendors might decide to not participate in our evaluation and refuse to become part of the Leadership Compass document. KuppingerCole tends to include their products anyway if sufficient information for evaluation is available, thus providing a comprehensive overview of leaders in the market segment.
- Lack of information supply: Products of vendors which don’t provide the information we have requested for the Leadership Compass document will not appear in the document unless we have access to sufficient information from other sources.
- Borderline classification: Some products might have only small overlap with the market segment we are analyzing. In these cases, we might decide not to include the product in that KuppingerCole Leadership Compass.
The target is providing a comprehensive view of the products in a market segment. KuppingerCole will provide regular updates on their Leadership Compass documents.
We provide a quick overview about vendors not covered and their offerings in chapter Vendors and Market Segments to watch. In that chapter, we also look at some other interesting offerings around the market and in related market segments.
9 Copyright
© 2024 KuppingerCole Analysts AG all rights reserved. Reproduction and distribution of this publication in any form is forbidden unless prior written permission. All conclusions, recommendations and predictions in this document represent KuppingerCole's initial view. Through gathering more information and performing deep analysis, positions presented in this document will be subject to refinements or even major changes. KuppingerCole disclaims all warranties as to the completeness, accuracy and/or adequacy of this information. Even if KuppingerCole research documents may discuss legal issues related to information security and technology, KuppingerCole does not provide any legal services or advice and its publications shall not be used as such. KuppingerCole shall have no liability for errors or inadequacies in the information contained in this document. Any opinion expressed may be subject to change without notice. All product and company names are trademarks ™ or registered trademarks ® of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
KuppingerCole Analysts support IT professionals with outstanding expertise in defining IT strategies and in relevant decision-making processes. As a leading analyst company, KuppingerCole provides first-hand vendor-neutral information. Our services allow you to feel comfortable and secure in taking decisions essential to your business.
KuppingerCole Analysts AG, founded in 2004, is a global, independent analyst organization headquartered in Europe. We specialize in providing vendor-neutral advice, expertise, thought leadership, and practical relevance in Cybersecurity, Digital Identity & IAM (Identity and Access Management), Cloud Risk and Security, and Artificial Intelligence, as well as for all technologies fostering Digital Transformation. We support companies, corporate users, integrators and software manufacturers in meeting both tactical and strategic challenges and making better decisions for the success of their business. Maintaining a balance between immediate implementation and long-term viability is at the heart of our philosophy.
For further information, please contact clients@kuppingercole.com.
















































