Insights
Research
Advisory
Events
Videos
KC Open Select
Company
KuppingerCole's Advisory stands out due to our regular communication with vendors and key clients, providing us with in-depth insight into the issues and knowledge required to address real-world challenges.

Optimize your decision-making process with the most comprehensive and up-to-date market data available.
Compare solution offerings and follow predefined best practices or adapt them to the individual requirements of your company.
Configure your individual requirements to discover the ideal solution for your business.

Meet our team of analysts and advisors who are highly skilled and experienced professionals dedicated to helping you make informed decisions and achieve your goals.

Meet our business team committed to helping you achieve success. We understand that running a business can be challenging, but with the right team in your corner, anything is possible.
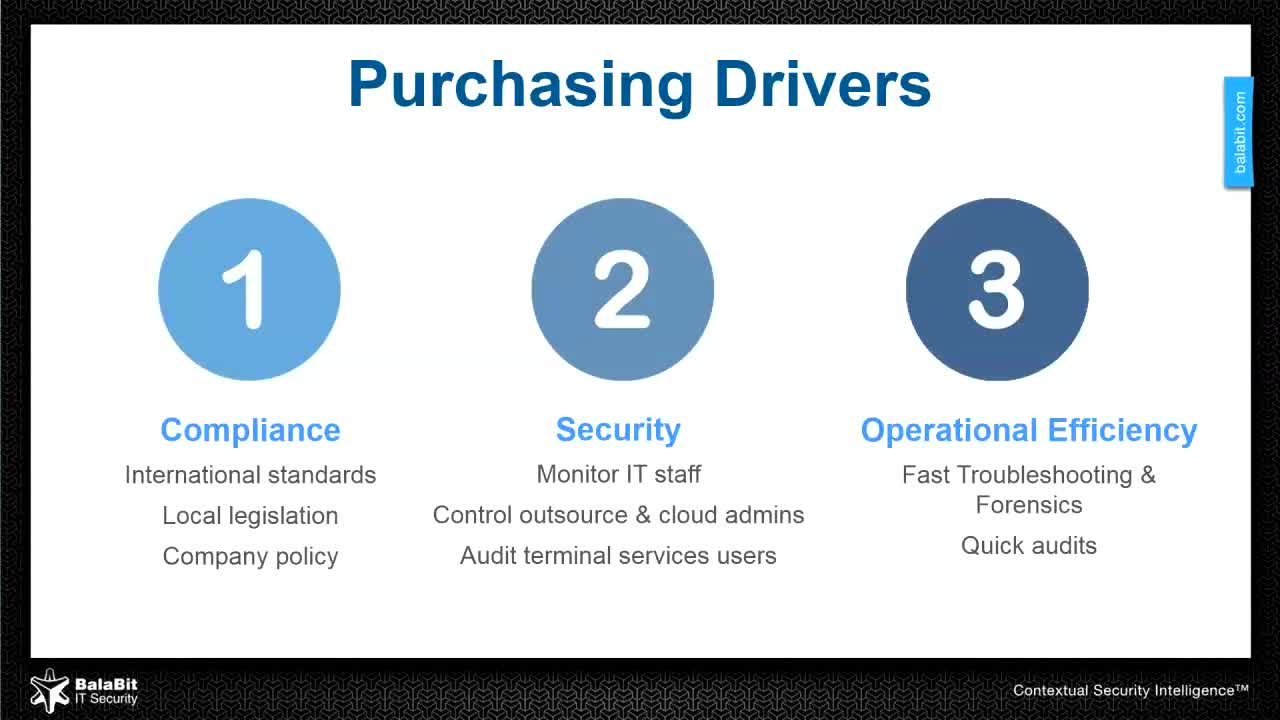
Balabit’s Contextual Security Intelligence Suite protects organizations in real-time from threats posed by the misuse of high risk and privileged accounts. Solutions include reliable system and application Log Management with context enriched data ingestion, Privileged User Monitoring and User Behavior Analytics. Together they can identify unusual user activities and provide deep visibility into potential threats. Working in conjunction with existing control-based strategies Balabit enables a flexible and people-centric approach to improve security without adding additional barriers to business practices. Founded in 2000 Balabit has a proven track record including 23 Fortune 100 customers amongst over 1,000,000 corporate users worldwide.

The IT landscape is undergoing its biggest change at least since the introduction of the PC. Cloud services and mobile devices stand for the hyper-connected enterprise, where everyone has access to everything, and where services reside somewhere, in the organization and in the cloud. Attackers are trying to gain access to privileged accounts, hijacking these. A key element of counter-measures is implementing a Privilege Management infrastructure that helps monitoring, recording, and analyzing sessions.

Today, the Security Operations Center (SOC) is at the heart of enterprise security management. Security analysts in most SOCs are still relying on traditional SIEM systems as a core platform for their daily operations. These are the primary tools to monitor and analyze security alerts coming from the various systems across the enterprise and to take actions against detected threats. However, the rapidly growing number and sophistication of modern advanced cyber-attacks make running a SOC an increasingly challenging task even for the largest enterprises with their fat budgets for IT security.
From statistical correlation methods to machine learning algorithms, from risk models to behavior profiling, from threat intelligence to cognitive technologies – there is a lot of exciting new developments going on in information security, which promise to dramatically improve the efficiency of your SOC.

The biggest mistake you can make it assuming you cannot, or will never, be breached – the challenge for any company is to have a strategy that meets their risk appetite, security measures with a known ROI, a detection plan so that you know before your customers and a mitigation strategy for when the worst happens.