What Is Vulnerability Management, and Where Do I Start?
Vulnerability management is a dynamic cyclic process of identifying, accessing, reporting on, remediating and managing identified vulnerabilities across an IT ecosystem, with the ultimate goal of reducing the overall count of identified or unrealized vulnerabilities.
All it takes is a single Vulnerability
Since the onset of the Covid-19 pandemic, the rise in cyberattacks has increased immensely. If you’re a company that is connected to the internet your chances of becoming a target for a cyber-attack are high. Hoping for the best is not enough.
Proactively fighting potential threats is much better than scrambling to pick up the pieces. That is where Vulnerability Management (VM) plays the lead.
Before diving into vulnerability management, let’s start with what vulnerability is. A vulnerability is a weakness in an IT system that could be exploited by a threat source (for example a cyber attacker). These weaknesses can lie in the system security procedures, internal controls, or implementations.
IT systems are highly interconnected and can be attacked from any point. The methods of attack are becoming more and more sophisticated and targeted every day. Vulnerabilities provide loopholes that can then be combined to perpetrate a successful attack by installing ransomware, stealing data breaches or committing fraud. We will refer to the entirety of these loopholes or vulnerabilities as the attack surface.
So, where do I start?
To make a start in designing a VM program, you need to first know exactly how vulnerable your IT ecosystem is. You can get a good idea by working through the following steps:
- Identify the elements that make up your IT ecosystem and security infrastructure– especially assets and applications. Here, a bird’s eye view is sufficient to decide how you can create or refine your asset inventory.
- Understand the complexity of your systems to comprehend individual factors contributing to security vulnerabilities. Some examples of such factors are probability of missing patches, incompatibilities, misconfigurations, design flaws and bad system management.
- Know the risk appetite of your organization. Your industry and / or company has guidelines or regulations provide guidelines about the acceptable levels of risk tolerance
These help you to understand the vulnerabilities which could be exploited by attacks.
What about teams and tools?
A vulnerability management tool is key to running your vulnerability management program. It manages, process and reports all vulnerability related data and standards needed to get a wholistic view of the vulnerability landscape. There are many such tools in the market that help aggregate such data and act as the single source of truth for all vulnerabilities in your organization. The VM tools’ source tools and teams act as various streams of data on servers, compliance, containers, and other security aspects need for further decision-making and management of the vulnerabilities. We will discuss the VM tool in the coming chapters. But before choosing a tool, it is important to assemble a VM team and identify who will use this tool. This team is normally part of the information security teas as key source tools also need to be deployed and instrumented. Thus – collaboration becomes a key component of the VM program.
Risk management and Security operations center (SOC) teams are also involved in analyzing vulnerability data. This tool is also integrated with patch management, Security Information and Event Management (SIEM) and other security teams. Mike provides more information on these interdependencies in his Leadership brief on Prepare and Protect against Software Vulnerabilities.
Why Is a Vulnerability Management Program Necessary for Your Business?
The purpose of VM program is to minimize this attack surface, usually with the help of a VM tool. Such a program explores the journey of a vulnerability from detection to remediation, and the cases of how to strengthen the resilience of an organization’s IT ecosystem.
Look after your money and reputation
This article mostly talks about cyberattacks as a motivation for having a VM program. The need for a VM program results from the increasing need for cyber resilience achieved through improved security hygiene standards. But this program also helps to protect your organization from fines and penalties due to regulatory non-compliance – thus saving money and keeping your reputation intact. An example of cyber resilience expectations for the financial sector in Europe are the ones stated by ENISA. There are of course other federal regulations based on geography (example: SoX, HIPAA, CoBIT, GDRP, CCPA, ISO 27001,and BaFin) and industry sectors, the impact of which is especially relevant to multinational institutions.
The pressure from regulators to handle exploits, especially in the post COVD-19 era, has increased the importance of managing vulnerabilities. Many potential business clients and partners also demand audit reports of 3rd party vendors when negotiating a deal. Many organizations have already risen to this and are now responding. Regulators and industry standards bodies are major sources defining the baselines for your cybersecurity hygiene.
Another obvious source of reputational damage is that your organization has been the victim of a cyber incident. Reputational damage due to an incident can directly affect your business with your vendors, clients by either being part of the attack or by reducing the level of trust in your organization. A vulnerability management program not only helps manage responsible disclosure when an incident occurs , but also avoid such an incident in the first place.
The rise in cost of breaches
These losses to an organization following a data breach arise from direct costs such as handling the breach, compensation to affected stakeholders and, fines. Other Indirect costs arise from system down time, communication expenses, etc. There is also the cost of lost opportunities because of reputational damage. There might be other cost factors that go unaccounted. Recent findings show that compliance failure and security system’s complexity are normally found in organizations that encounter higher costs of breaches. Moreover, research also indicates that using an incident response system helps decrease this cost.
A VM program involves regular patch cycles instead of ad-hoc ones, thus the costs of missed patches are avoided and backlogs are reduced. It also prioritizes focus on important assets, the potential breach of which are associated with high risk factors. This helps better utilization of your organization’s cybersecurity resources.
Improve your overall security posture
A VM program help identify legacy security gaps in the network which are often exploited by cybercriminals. It helps to mature your overall security through better alignment between security teams. This program shifts your business’s attitude about cybersecurity from a reactive to a proactive one.
In addition, it enhances your visibility of your attack surface via reporting on the operational efficiencies. This in turns help you move towards improved standards security practices. Key metrics certainly help build a roadmap for obtaining future operation efficiencies by planning automation in the right areas.
In conclusion – A vulnerability management program is cost effective way to give you a business edge by enhancing your stakeholder relationship, reducing cost of breaches and maintaining a future proof secure posture for your business.
What Is Vulnerability Management Lifecycle?
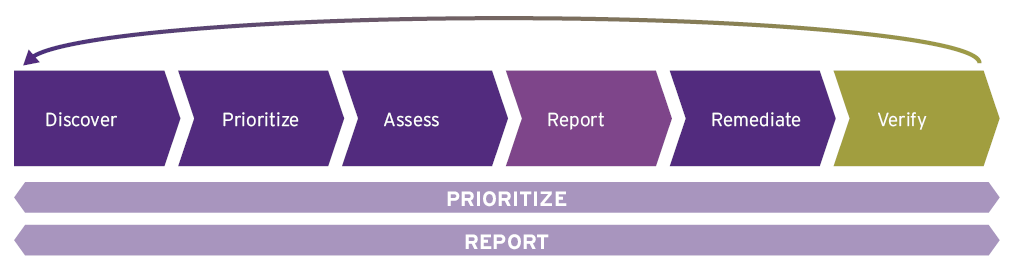
In the words of the famous proverb – “An ounce of Prevention is better than a pound of Cure”, finding and remediating vulnerabilities is better than suffering the consequences of an attack. This can be achieved by a dynamic precautionary cycle. The Vulnerability management lifecycle is best described as continuous cycle of Discover, Prioritize, Assess, Report, Remediate and Verify.
Foresee and manage cyberattacks with the vulnerability lifecycle management
New vulnerabilities are being discovered all the time and these pose a special threat. If the cyber attackers find them in your systems before you have taken action, the result will be reputational and financial loss and damage to your systems.
The most widely practiced and effective approach is Vulnerability Lifecycle Management. Its phases cover all the way from discovering a vulnerability to remediating it and verifying the fix. If executed efficiently, this cycle not only enables better management and handling of vulnerabilities, but also improves the overall posture of your organization’s cybersecurity by allowing collaboration with other relevant IT teams.
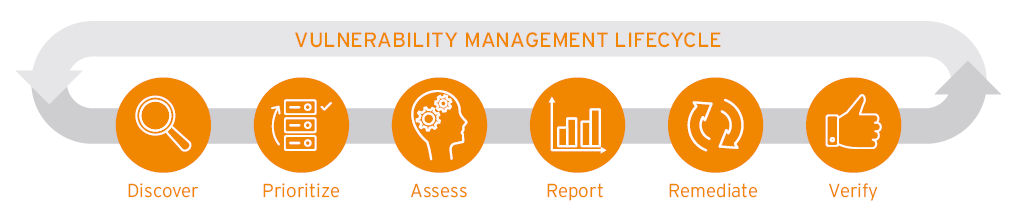
As you can see, there are multiple stages to the vulnerability lifecycle. It is iterative and ongoing since older vulnerabilities may recur and pose a threat to the security of Organization’s IT systems. This chapter briefly introduces each stage. More details on these stages are given in further chapters.
Discover
The Discover stage has two phases – vulnerability discovery and vulnerability monitoring. Both these phases are largely covered by scanning tools. Having an asset inventory is crucial to this stage since this determines the scope of that will be checked for vulnerabilities.
By finding these vulnerabilities, you obtain actionable information on flaws in your IT ecosystem.
Prioritize
The US National Vulnerability Database (NVD) identified more than 18000 vulnerabilities in 2021 alone. To reduce your attack surface effectively, prioritizing vulnerabilities is a major step. Without prioritization, it is impractical for any organization to deal with all the newly discovered vulnerabilities after each scan. Over time, these vulnerabilities would pile up in thousands, or even more.
Assess
In this stage, a baseline risk profile is determined using asset criticality, vulnerability threat and asset classification. The assessment stage measures the business risk associated with your assets.
Report
Once the data on discovered vulnerabilities is prioritized and assessed, these are then reported as individual tickets. Progressing further in the VM lifecycle, a security plan can now be formulated and documented in parallel.
Remediate
Finally comes the most awaited stage - taking action. Even though the stage is called Remediate, we will be covering all other options to handle vulnerabilities in this stage. The action to be taken is based on the results of the risk from the vulnerability. The usual list of actions is:
- Remediate,
- Mitigate, or
- Accept
Verify
This stage covers the post remediation follow up audits and measures the success of your actions. This is done by measuring the reduction in attack surface and exposure of assets to any threat.
What Is Vulnerability Scanning, Prioritization and Assessment?
Vulnerability scanning is a crucial part of the Discover stage, where different components of an IT landscape are scanned to discover vulnerabilities. This is followed by the Prioritize stage. The prioritize stage involves cataloging all vulnerabilities based on the CVE score (explained below). In the Assess stage, also called as vulnerability assessment, all the vulnerability scan data is aggregated and further structured and enriched contextually.
Discover, Prioritize and Asses stages help create insights for various audiences
Normally, vulnerabilities in different segments of the organization’s IT ecosystem are identified using multiple scanning tools. This is part of the Discover stage in the VM lifecycle management. Some of the areas that can be scanned are :
- Network and wireless scans
- Application scans
- Database scans
- Host-based scans
- Source code scans
- Cloud scans
These tools use a repository of known vulnerabilities that is periodically updated. When deployed in your IT environment, these also help monitor vulnerabilities using regular scans that check your environment against their updated repository.
Independent organizations performing security research also publish vulnerabilities, which are included in the well-established repositories. The most prominent example is (Common Vulnerabilities and Exposures) CVE® Program.
How do I prioritize?
Vulnerabilities are given severity ratings based on how easily a vulnerability can be exploited, and what the impact of exploiting this could be on your organization. The good news is NVD already does the prioritization for you, once aa new vulnerability is discovered. Every vulnerability is assigned a Common Vulnerability Scoring System (CVSS) score that lies between 1 to 10, 10 being the most critical.
The not so good news is – this score is static and does not have context. Hence organization specific factors need to be considered to measure the risk to your organization. Many scanning tools simply repackage CVSS score. But there are scanner tools that offer scoring and prioritization based on your organization’s individual risk factors.
The final assessment
Vulnerability assessments leverage data from tools like vulnerability scanners. In addition to the detection of vulnerabilities, scan tools also provide an analysis with possible details on root cause and source of the individual vulnerabilities, which is an additional information on the profile of each vulnerability found.
Once these vulnerabilities are found, analyzed and scored according to a predefined score range by the respective scan tool, they are used by the VM tool. The VM tool sanitizes and standardizes all data received from the various tools. In addition, based on what it already received, the tool automatically enriches the collected information with severity, recommended actions, assignee, remediation timelines and other pivotal information wherever required.
Reporting
The adequacy of security measures through remediation, mitigation or acceptance is determined during the Assess and Prioritize stage. Once adequate information and measures are decided upon, we report the vulnerabilities. All this compiled information on a vulnerability profile results in a Vulnerability Report or a ticket. Reporting is an important step towards deciding upon the action to be taken to manage the vulnerability.
How Do I Remediate Vulnerabilities Once Identified?
Once a vulnerability has been prioritized and assessed post scans and has been recognized as a potential risk for the organization, it enters the remediation phase. In this phase a vulnerability ticket is assigned, the vulnerability is remediated or treated as an exception. Once vulnerabilities have been dealt with, the actions taken are verified to make sure that the associated risks are now acceptable.
The default case of Remediation
The Remediate stage usually has two process flows, one of which is aimed at fixing a vulnerability based on its severity and priority, while the other deals with the exceptions to the first flow.
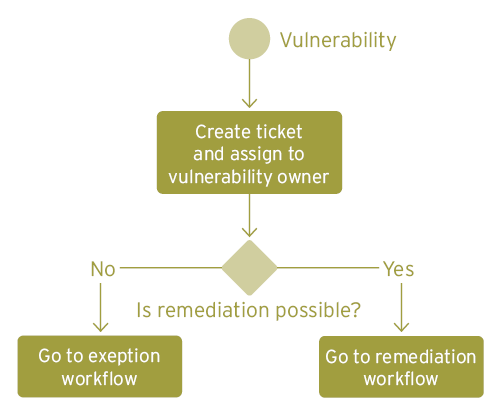
Each reported vulnerability ticket is assigned to a vulnerability owner (asset owner, security lead, etc.) who checks whether the vulnerability needs an urgent action or is a false positive. He or she accordingly adds the remediation steps needed to the action plan.
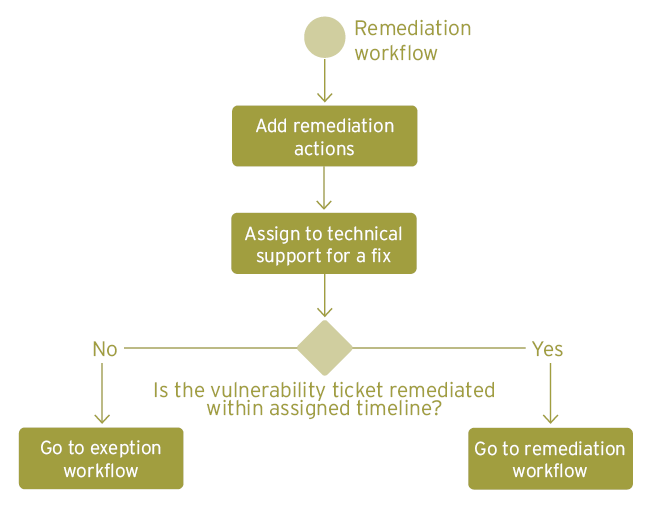
Following this flow, the respective vulnerability owner assigns this ticket to the technical support team responsible. A predefined timeline based on severity and priority then defines the due date for this fix. The patch management team is heavily involved here, and it is important to have a positive relationship with them to meet your goals of reducing overall attack surface.
Ideally, the fix should take place within these timelines. Nevertheless, a process flow for overdue tickets is a good idea because the longer you wait to fix a vulnerability, the higher the risk factor associated with it.
One important issue that needs to be considered is change controls. Changes to IT resources can often have negative consequences and many organizations will not allow changes to the resources supporting critical business systems without prior testing. The urgency for change based on the potential impact of the vulnerability needs to be offset against the risk of disruption. In general, delaying patching usually poses more of a risk.
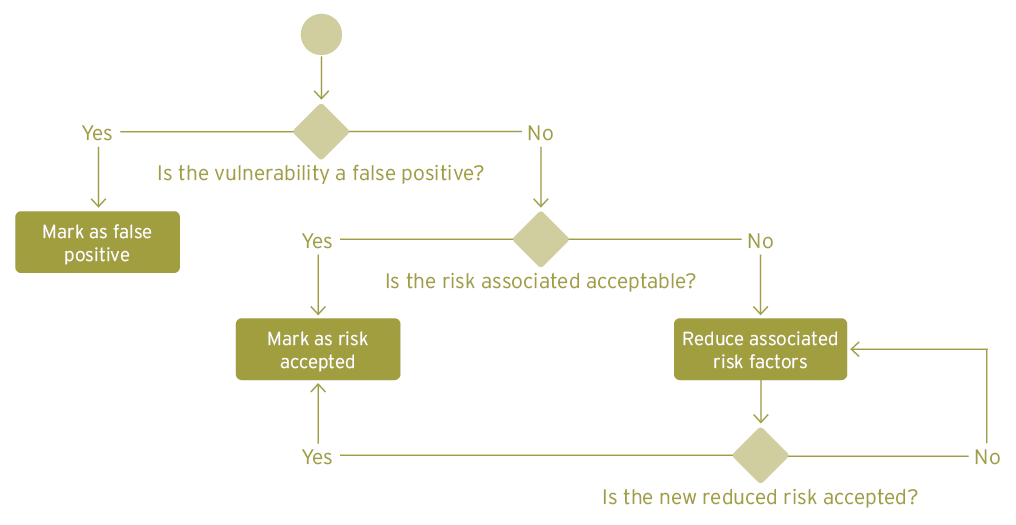
Dealing with exceptional cases
In the rare case that the vulnerability owner comes across a false positive, finds that a patch is not yet available, or cannot take any action because of other reasons due such as high remediation expenses, or low risk, etc. - then the exception flow comes into place. This can broadly be divided into mitigation and acceptance.
When and what to mitigate?
Instead of remediating a vulnerability, it may be possible to lessen the impact and associated risk of a vulnerability by adopting certain measures. This could be done for example by isolating the relevant network or by going offline. Such measures can buy more time for a remediation plan and a patch.
What to accept?
Another alternative is for the organization to accept the risk of leaving the vulnerability unpatched. There will be scenarios where the risk factors involved are considered to be sufficiently important to warrant the costs of making the changes. Sometimes, budget constraints may force the organization to accept the risk associated with some vulnerabilities. Vulnerabilities considered to have negligible or low impact may be accepted for reasons of better resource and efficiency management. Hence an workflow for such cases is also needed.
How can I be sure that the vulnerability is gone?
The Verify stage follows the remediation or mitigation and its objectives are to make sure that the vulnerability is either eliminated or no longer poses a sever risk . In the case where a vulnerability’s risk has been accepted, it is important that there is an approval process to check it against your organization’s risk appetite..
In general, every scan tool has a recurring scanning cycle, and the next scan post remediation will provide information on whether the vulnerability is still detected or not. This provides an automated process to update the latest information on all vulnerabilities. Many companies also pair VM with penetration testing to gauge the effectiveness of the overall remediation patches and actions.
How Do I Deal With Zero Days / Emergency Patches?
Your organizational systems may have many internal vulnerabilities that have not yet been identified, or that scored low for priority and severity, and thus could the damage. Then there are also some vulnerabilities such as the ones associated with Log4j that are not even system specific. Clearly, a defensive strategy is needed that practices urgency for patching and mitigation to improve the response when such information is received by your organization.
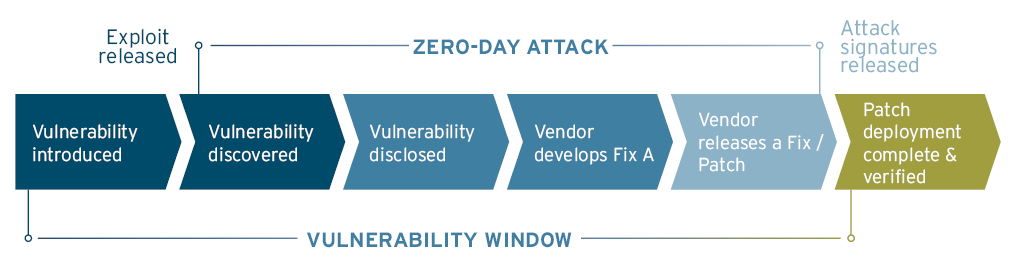
Important terms related to Zero days
A zero day vulnerability is one that was previously unknown and one that poses a high risk. If a cybercriminal manages to exploit such a vulnerability before it has been remediated or mitigated – this is known as the zero-day Exploit or attack. Zero-Day Exploits reached an all-time high in 2021, most of them being state-sponsored attacks. Vendors such as Google, Microsoft and Apple face such exploits more frequently due to their popularity.
A zero-day patch is a patch that is delivered by the vendor and deployed by the organizations at risk on the same day that the vulnerability is disclosed. Once such a vulnerability is identified, an emergency patch process triggers urgent countermeasures to reduce the possibility for exploits to a minimum.
How should I react to a zero-day vulnerability?
A response to such emergencies can be handled by an Incident Response Plan that is specifically designed for this purpose. This process is intended to bypass the normal organizational processes to rapidly respond to the vulnerability. Control in such cases is quickly transferred from the VM team and other teams to the incident response team.
This team rapidly analyses the organizational assets impacted by the zero-day vulnerability and works with the support engineers or other stakeholders to address them. Hence the plan is depends upon clear communication channels to operate effectively. Once all stakeholders and relevant information is in place, an immediate predefined action plan is triggered. In many cases, a targeted patch is created and rapidly but safely applied. The entire timeline of executing the incident response plan is ideally 0-2 days, based on the risk posed by the vulnerability. Other mitigation actions can simply be for example, isolating the respective network segment until a patch is available. Christopher talks about classification of such incidents, the preparation needed, and gives some recommendations on Incident response management in his Leadership brief.
What follows a zero-day patch?
Once the vulnerability is either mitigated or remediated, it is good practice to check that the production systems or isolated networks are back to normal functioning. Restored systems and networks should be tested and monitored by their respective owners or teams as they are back in the driver’s seat again. All stakeholders involved should also complete documentation that was skipped during the response process, further investigate the scope of such a vulnerability, and identify areas that need improvement in the response plan. Check out the KC Master Class for more in depth knowledge on the art of incident response management.
Zero-day vulnerabilities are much easier to deal with if your organization is in a good state of operational readiness. Dealing with a high-profile vulnerability can be confusing and difficult, and thus lead to chaos. It is important to make sure that all endpoints are up to date and working smoothly prior to an emergency response – otherwise the overhead is hard to manage. A continual improvement to your VM program can also significantly contribute to mitigating overall possibility of a zero day or emergency patches.
How to Improve Your Vulnerability Management Program?
Around 60% of security breaches happen due to vulnerabilities for which patch were available but was yet not applied. A Zero-day vulnerability is an unwanted scenario that must also be included in plans. So why not be smart about it? Your best bet is to make sure that you have an effective VM program that is in place to avoid any vulnerability being left unpatched. This chapter suggests a couple of tips and tricks to improve your VM program.
Monitor continuously and create visibility
Good reporting is important to help to provide an overview of an entire program and to check on progress and efficiency. Implementation of a security plan for dealing with vulnerabilities establishes control and demonstrates progress. The VM lifecycle not only has successive stages but also provides an overarching template. Up to now this has only considered the reporting of individual vulnerabilities and their components. KPIs (Key Performance Indicators) of an aggregated vulnerability assessment data are essential to help you to improve. These help you to:
- Understand your status quo for compliance audits
- Know how efficiently vulnerabilities are being fixed
- Determine if you are within your acceptable limits for risk.
- Identify areas for improvement in various procedures– technical and collaborative, especially regarding patch management and scan coverage
- Create a baseline against which you can measure progress
These are just a handful of benefits that can help improve security plans for your organization. Such reports are mandatory in some business sectors, as compliance standards may demand them. in addition, there are numerous ways to take advantage of vulnerability data. Such as, for Cyber Threat Intelligence (CTI).
Some examples of KPIs in these reports are scan coverage, vulnerability re-open rate, number of exceptions granted, time to resolution and graph representing rise/ fall of total number of vulnerabilities over a defined period.
Leveraging the Verify stage
Even though it is the last stage, the Verify stage is where you can find out if new vulnerabilities had not been introduced as a result of mitigation. Moreover, a brief analysis on the sources of false positives can indicate either human error or wrong instrumentation of the scanning tools or the VM tool(s). VM heavily relies on technology used for effectiveness and productivity of the VM program, and thus the analysis done during this stage can improve overall performance.
Ensure a complete inventory
Having a complete inventory is vital to help to identify vulnerabilities. Without this you will never be able to fully secure your systems. Integration with an complete asset inventory ensures timely access and avoids wasting time on false positives with lack of credible sources for scanning.
















































