What is PAM?
Let’s start by defining privileged access with a real-world example. Do you use a mobile banking app? Imagine it was as open as any other app. Obviously it’s not and for a very good reason – it’s your money in there! So there needs to be some controls.
Preventing Unauthorised Access to Your Bank Account
Before you have access to the app, you must prove your identity to the bank to ensure only you can access your account and transfer cash or pay bills
You will remember that before you could set it up, there were several security steps you had to go through. These will have been securely stored.
And now every time you access the app, it will ask for credentials such as a PIN or password to reconfirm your identity. Alexei and Matthias had a great discussion on the concept of ephemeral credentials and its benefits for privilege management, DevOps and beyond in an episode of the Analyst Chat.
By the way, that is not all that is needed. In the background a set of security processes are also underway to match your login with the right account. So, there you have it, you have privileged access to your own bank account.
Nice.

But What if More People Need Access to Bank Account?
How many people do you think have access to your bank account apart from you? The answer is that there could be several other people who have access such as your account manager, and anyone else that the bank thinks should have the privilege. So, to protect your account, bank employees will also be granted privileged access with stringent security processes attached. Don’t think, however, they will be using the same set of credentials as you.

Hopefully, their access will be managed by PAM – but we will come back to that. For now, just remember that mobile banking (and of course online banking too) is a real-world example of privileged access in operation – every time you check your balance! Easy. Well maybe not, as we shall see.
PAM can become very complex if we let all the different technologies involved overwhelm us too soon. But at its heart PAM has one simple task:
To ensure that access to secrets is as secure as possible and only for those people authorised to see them.
Key PAM Terms Defined
Now you understand the concept, let’s look at some of the key terms used in PAM and the differences between:
- A Privileged User
- A Privileged Account
- Privileged Access
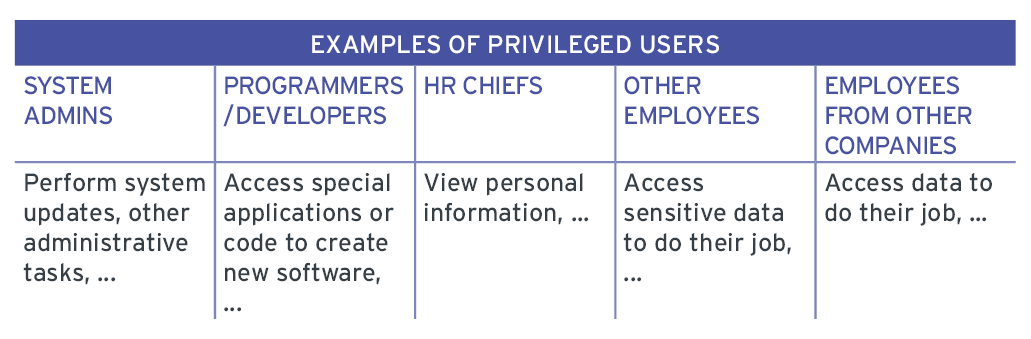
What is a Privileged User?
A Privileged User is anyone who is authorised to have access to secrets. In your company this will often mean system administrators (sysadmins) who can access other employees’ computers in order to perform software updates or other administrative tasks. A bit like the bank employee having access to your bank details.
However, in recent times, the number of privileged users has increased, and the definition has changed somewhat. Privileged users are now just as likely to be other employees who need access to sensitive information to do their jobs. They may be programmers and developers who need access to special applications or code to create new software. Or they may be HR chiefs who are authorised to view personal information. The number and types of employees becoming Privileged Users is changing and increasing all the time. In fact, they may not even work for your company, but are allowed access to your enterprise.
What is a Privileged Account?
Let’s move on to Privileged Accounts. Here is where things get a little trickier as people often mix up Privileged Users and Privileged Accounts. For now, it’s best to view a Privileged Account as something that Privileged Users are given in order to be registered as a Privileged User on the IT system.
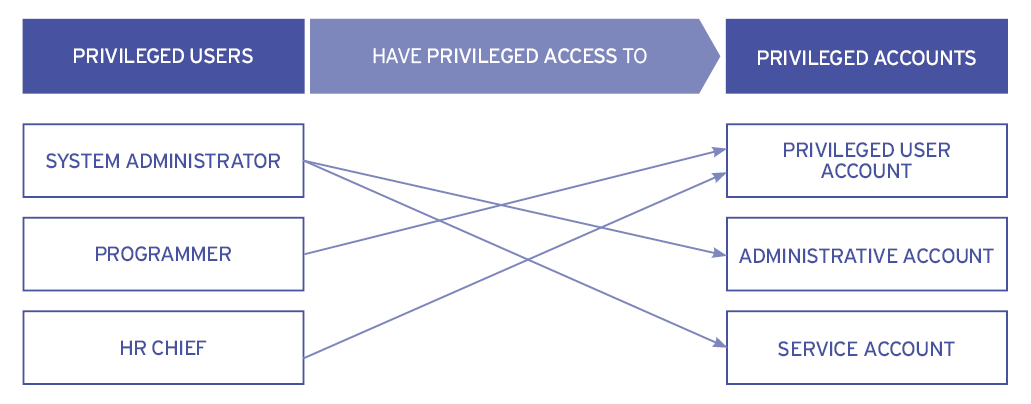
The confusion arises when different types of accounts exist, some for-end users to perform basic IT tasks, some for-admin users, and some for machines that automatically perform IT tasks. There are even some that that allow applications to connect to operating systems, databases or other applications.
These are known as Service Accounts. Altogether, there can be as many as seven different types of privileged account of privileged accounts and users and machines can hold different types at the same time. With this many users getting Privileged Access, you can see that it is already becoming something of a challenge to manage all this, which is why some accounts are shared between different users.
What is Privileged Access?
As we saw in theonline banking analogy, anyone or anything that has access to an account for administration or processing purposes, subject to stringent security processes. By now, hopefully you understand this provides access to secrets and for users to perform certain functions considered risky such as downloading or updating software. As noted above, privileged access can be given not only to human actors, but also to machines and applications.
What’s the password?
Passwords are an important part of PAM, but they can be troublesome too. Traditionally, Privileged Accounts are protected by a password. In the most primitive form of PAM, these passwords may have been written down in an Excel spreadsheet and then given to users when they wished to use the account to access something.
Did you know that passwords have been used for 1000s of years to separate friends and enemies?
The concept of the password can be traced back to the Shibboleth Incident in the 12th chapter of the Biblical Book of Judges. In the battle between the tribes of Gilead and Ephraim, Gileadite soldiers used the word “shibboleth” to spot their enemies. They knew that the Ephraimites pronounced it slightly differently in their dialect. The penalty for an incorrect password was death. “Then said they unto him, ‘Say not Shibboleth’; and he said ‘Sibboleth’; for he could not frame to pronounce it right; then they laid hold on him and slew him at the fords of the Jordan.”
Protecting Passwords From Prying Eyes
Password Managers are better than an Excel spreadsheet- but not by much as this video makes clear. The vulnerability of unprotected passwords being stored in plain sight led to the development of dedicated PAM applications. While passwords were still used to authenticate users in the first PAM solutions, the passwords were randomly generated and rotated by the PAM application.
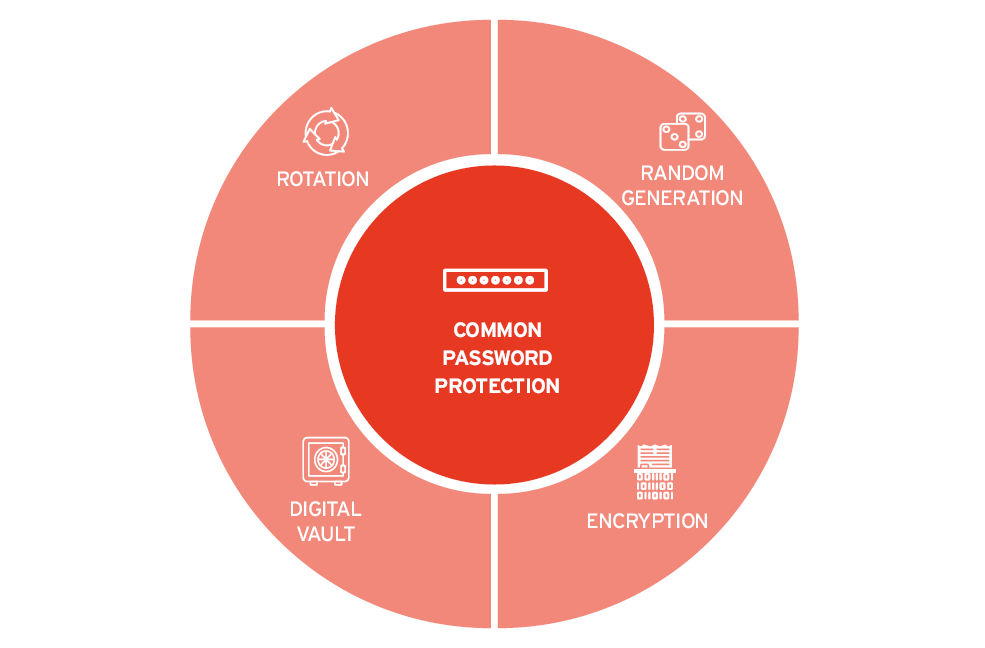
They were also encrypted and stored in a digital vault. The password itself was hidden from view to most users for greater security. Instead, the password would be checked out from the vault to grant access and then checked in again after the user had completed their task. Today, most mainstream PAM platforms continue to rely on vaults and passwords.

However, as usage has increased, some security risks have become apparent as demands on PAM platforms have become heavier:
- Passwords are often shared to facilitate multiple user access to the same resources.
- Passwords can be made visible to PAM admins in certain circumstances, increasing the risk of passwords being misused and shared among co-workers.
- Some passwords given to so-called superusers give almost unrestricted access across the entire enterprise.
- Hackers know that certain employees are Privileged Users and will actively target them and steal their identity
New Developments for Protecting Passwords
The biggest problem for digital passwords and vaults is that they cannot tell if the person checking out the passwords is the right person or entity. To overcome these risks, PAM providers are increasingly looking at alternatives such as ephemeral access to privileged accounts, one-time passwords (OTP) and Just in Time (JIT) access.
Ultimately the goal for PAM is to eliminate permanent privileged status for users or “always on” privileges, which has given rise to the concept of Zero Standing Privilege, which relies instead on a policy-driven process for obtaining privileged access only when it’s needed and scoped only to the job at hand.
So, Why Is PAM Important?
With today’s complex operating environments and interconnected machines, almost everything related to modern business IT will have some need for PAM. Let’s look at why PAM is relevant to some of the major areas.
Key Areas of Business IT That Need PAM
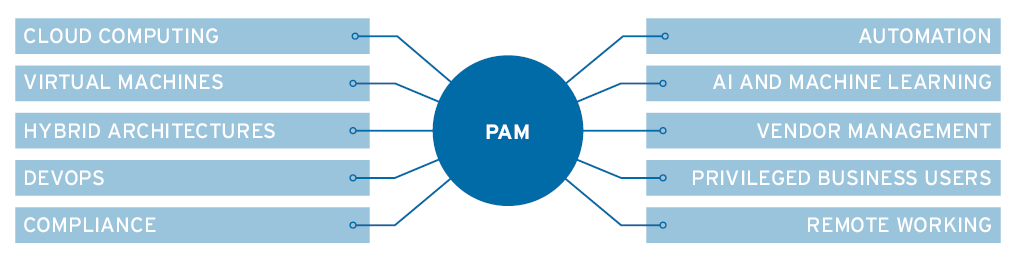
- Cloud computing: Because users need access to critical applications or databases that are stored in the cloud, to cloud platforms for application development, or to SaaS tools used by your business or technical teams.
- Virtual Machines: For the same reasons as cloud computing.
Users need access to thing running in virtual machines, and these can be anywhere.
- Hybrid architectures: Because thesemean that sensitive data and where users reside is even more spread out.
PAM can help keep tabs on access.
- DevOps: Your colleagues in development are avid users of secrets from code to credentials.
Keep them organised, secure and happy.
- Compliance: If a user loses information that contains personal details about customers your company could be fined for failure to comply with data protection rules.
That’s why PAM is increasingly used to contain such threats.
- Automation: Remember how we said that Privileged Users are no longer only human – well here is why.
As organizations become more digital, more processes are handed over to applications and machines. That’s why PAM platforms now support Application to Application Privilege Management (AAPM)
- AI & Machine Learning: This is related to automation.
As processes multiply, it’s harder to maintain control of privileged user behaviour and accounts. By using AI, PAM can learn more quickly about risky behaviour by users (and machines).
- Vendor management: Organizations are increasingly intertwined with the workings of their suppliers and partners – also known as vendors – who may also get Privileged Accounts on your infrastructure.
- Privileged Business Users: As we said right at the start, Privileged Users are no longer just admins and techies, but all sorts of users from across the business.
These need to be managed as well without interrupting their tasks. Remember, Privileged Business Users can even include those working on the official social media account. After all you don’t want everybody tweeting on behalf of the company…especially disgruntled employees!
- Remote working: More of us work from home or remotely these days.
Whatever happens on those devices needs to be monitored so that users don’t abuse privileges through illegal downloads and updates (whitelisting) while at the same time allowing privileged access directly from an endpoint.
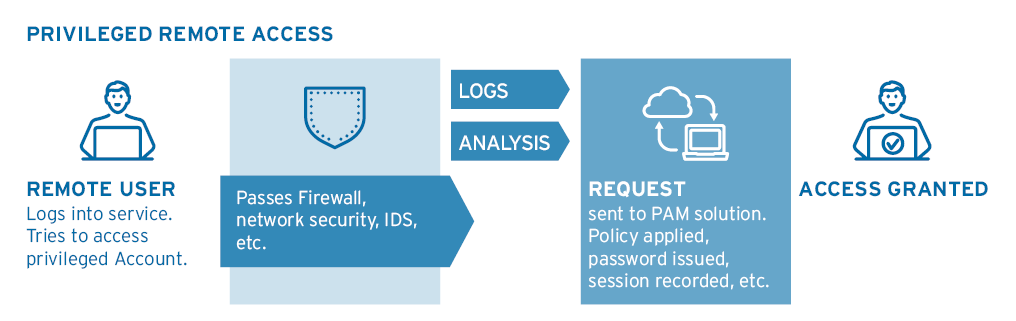
For this you can thank Endpoint Privileged Management (EPM) and Privileged Remote Access (PRM).
Getting Ready For PAM in Your Business
In this chapter we look at some of the steps you should take before you purchase a PAM platform. This will help you understand the specific needs of your business and how ready you are to deploy PAM. This is where we get a bit technical, but there are several tutorials online that will help you.

Make the business case for PAM
There must be valid business cases for the project. For PAM, avoiding costs associated with lost data via privileged accounts is a great business case – but there are others.
Get your budget sorted
Obviously best to get this done before you go ahead!
Decide who is responsible for PAM
In larger organizations, members of the IT security team may go on to become internal “product managers” for PAM solutions and policies. Smaller organizations may rely on an IT leader or Managed Service Provider. In any case, at least one person should be responsible for managing PAM itself.
Decide who will be PAM admins
Those PAM solutions that are managed and operated in-house will need administrators appointed as well as technical leaders to authorize usage and product lifecycles.
Don’t forget guidelines and policies
Ensure that guidelines for Information Security in general and PAM are defined and mapped to business and security policies.
See how PAM fits in with existing enterprise tools
You may already be running security software such as Vulnerability Management or IAM , so check if PAM can play nicely with these. There are lots of opportunities to integrate PAM as Yaron Mazor has shown in his session: The Interplay between SOAR and PAM. Take a look!
Some Good Ideas for Choosing PAM for Your Organization
So, you know now what PAM is about, why it is important in in our increasingly complex IT and business environments, and how to prepare for it. The final step is thinking about how you might choose PAM for your own organization.
One Size Does Not Fit All
Remember, the needs of all organizations are very different.
The good news is there are a growing number of PAM providers out there that can provide the basic requirements of PAM such as password vault and password rotation. Or there are fully comprehensive suites that allow full blown analysis of privileged users and special functions for those working in areas such as DevOps. Read more about the technical differences between PAM platforms here.
Important Stuff to Think About Before You Purchase PAM

1 Deployment
Is the solution available for on-premises installation, as a virtual appliance, hard appliance, or cloud service? Flexibility regarding the deployment models is increasingly important these days because customer needs vary greatly.
2 How soon will it be up and running?
Related to the deployment model, is how quickly a PAM solution can be up and running and deliver value to the organization. PAM vendors will often claim typical deployment times which are useful as a starting guide.
3 Size and reputation of the vendor
Large vendors are not necessarily the best ones, but size matters to some extent. Smaller vendors might react faster to customer demands, have a strong local presence, or might be more innovative in rolling out upgrades. Larger vendors have obvious staying power in the market.
4 Vendor focus
Is the vendor focused on PAM? Do they have subject experts on hand? Vendors with a broad product portfolio, where PAM is not a primary focus, might innovate less in PAM technologies and be less knowledgeable. Thus, ensuring that the vendor has a strategic focus on PAM is an important criterion.
5 Manuals and instructions
Documentation of the product should be current, complete, comprehensive, and available for easy access by business partners and customers. Look out for vendors that provide multi-lingual documentation and support.
6 Cost
Last, but by no means least, price is an important criterion. However, do not simply choose a cheaper option just because its cheap. Look for value and appropriate functionality for your needs.
Top tip: These guidelines work for almost any software deployment, not just PAM
Find out why: Why SMBs need PAM! KuppingerCole has an excellent guide to buying PAM for your business which goes into a lot more detail. You can find it here. So there you go, your quick and easy guide to PAM. Obviously there is much more to learn which is where we can help with choosing and deploying PAM and other technologies in your company.
















































