Insights
Research
Advisory
Events
Videos
KC Open Select
Company
KuppingerCole's Advisory stands out due to our regular communication with vendors and key clients, providing us with in-depth insight into the issues and knowledge required to address real-world challenges.

Optimize your decision-making process with the most comprehensive and up-to-date market data available.
Compare solution offerings and follow predefined best practices or adapt them to the individual requirements of your company.
Configure your individual requirements to discover the ideal solution for your business.

Meet our team of analysts and advisors who are highly skilled and experienced professionals dedicated to helping you make informed decisions and achieve your goals.

Meet our business team committed to helping you achieve success. We understand that running a business can be challenging, but with the right team in your corner, anything is possible.
Axiomatics is the leading provider of fine-grained access control. Axiomatics’ solutions are utilized by government agencies and Global Fortune 1000 companies around the world to enable digital transformation: share and safeguard sensitive information, meet compliance requirements, and minimize data fraud. Axiomatics provides Attribute Based Access Control (ABAC) for applications, databases, Big Data, APIs and microservices. To learn more please visit: www.axiomatics.com or @axiomatics.

As workers become more mobile and workloads move into the cloud, the traditional model of enforcing security at the network perimeter becomes ineffective. A Zero Trust model of strict access control for every user or device protects your organization from advanced security threats enabling you to stay connected, productive and secure.

As opposed to traditional monolithic applications, a (micro)service-based architecture comprises multiple loosely coupled modules (“services”) that serve specific business purposes and communicate over lightweight network protocols. Such services can be developed, deployed and scaled independently on different platforms, which greatly reduces the time needed to bring as new product to market and allows for continuous delivery development process, where small changes to the business logic of an individual service can be quickly introduced and deployed.
However, when designing a (micro)-service architecture, dealing with identity and security becomes a much more complicated task than in traditional monolithic applications: each individual component must know which user is interacting with it and which access rights are granted to him. Externalizing and centralizing access management is a natural choice for microservices systems to ensure consistently secure and scalable authorization. Implementing the authorization service itself as a microservice, providing policy-driven access control for other microservices and APIs seems to be just as natural… Or is it?

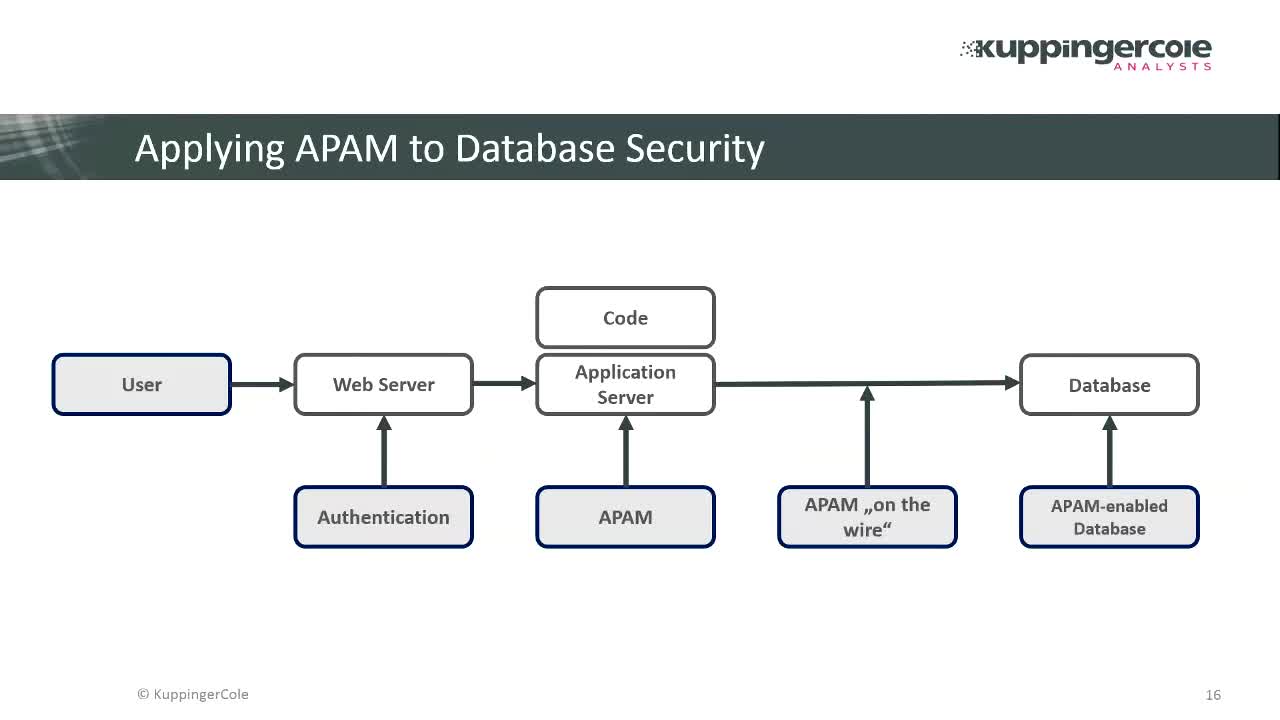
With the growing adoption of cloud computing, Big Data or open APIs, managing, securing and sharing massive amounts of digital data across heterogeneous and increasingly interconnected infrastructures is becoming increasingly difficult. From file servers to relational databases and big data frameworks, to the Internet of Things and entire API ecosystems – each data model imposes its own security controls and separate technology stack for enforcing them. An alternative approach – data-centric security – is in fact nothing new and quite simple in theory: instead of managing access to each individual infrastructure, just focus on protecting the data itself, regardless of its type and location. However, practical implementations of this concept depend heavily on two things: standards and policies. A solution that manages to successfully implement them in a unified, flexible and open manner, could surely be able to bring data security to a new level.

Data-centric security solutions control access via a fine-grained policy approach and focus on securing this content via dynamic and scalable authorization. The data access filtering approach signifies a new generation of database security techniques, based on a combination of two robust and proven technologies: data-centric security and standards-based Attribute Based Access Control (ABAC). On the whole, this method brings database security to a new level.


KuppingerCole Webinar recording

KuppingerCole Webinar recording