Insights
Research
Advisory
Events
Videos
KC Open Select
Company
KuppingerCole's Advisory stands out due to our regular communication with vendors and key clients, providing us with in-depth insight into the issues and knowledge required to address real-world challenges.

Optimize your decision-making process with the most comprehensive and up-to-date market data available.
Compare solution offerings and follow predefined best practices or adapt them to the individual requirements of your company.
Configure your individual requirements to discover the ideal solution for your business.

Meet our team of analysts and advisors who are highly skilled and experienced professionals dedicated to helping you make informed decisions and achieve your goals.

Meet our business team committed to helping you achieve success. We understand that running a business can be challenging, but with the right team in your corner, anything is possible.
Traditional security defenses are no match for today’s well-funded attackers, while disruptive technologies, like Cloud and IoT, introduce new vulnerabilities to exploit. IBM Security, with 8,000 professionals in 133 countries, delivers an immune system of security technology to detect and prevent threats and respond quickly and completely to breaches. During the past decade, IBM has invested more than $2 billion on security research and development, resulting in 3,700+ security-related patents, and acquired 20 security companies to build out its portfolio. Today, IBM Security addresses the evolving security landscape and 17,000 clients’ most critical needs with AI innovation in the cloud and intelligent orchestration. To learn how, please visit ibm.com/security.

Join security experts from KuppingerCole Analysts and IBM as they discuss the challenges of achieving security and compliance across hybrid multi-cloud environments, and potential solutions, that need to be comprehensive and flexible enough to continuously manage security & compliance posture, protect critical workloads, secure sensitive data, reduce silos, and consolidate tools.
Alexei Balaganski, Lead Analyst at KuppingerCole, will explain the challenges in implementing multi-cloud strategies, and discuss the growing complexity of security tools, the mounting pressure of regulatory compliance, and the scarcity of talent to solve these issues. He will also outline the requirements potential solutions need to fulfil – such as cross-team tool consolidation, intelligent automation, and open, extensible architecture.
Dr. Nataraj Nagaratnam, CTO for Cloud Security at IBM, will discuss the overall security compliance challenges for enterprises and how to approach security and compliance across hybrid multi-cloud with the IBM Security and Compliance Center solution suite.

Join security experts from KuppingerCole Analysts and IBM as they explain how Security Orchestration, Automation, and Response (SOAR) solutions address this and other security challenges. They will also examine different approaches to SOAR, and discuss how to identify SOAR solutions that are a good fit for your organization.
Alejandro Leal, Research Analyst at KuppingerCole and author of the latest Leadership Compass on SOAR will explain the background of the report, discuss the SOAR market, identify the main capabilities of SOAR solutions, and talk about what makes IBM’s QRadar SOAR a market leader.
Oren Shevach, Product leader for IBM Security QRadar SOAR will provide further details and insights into IBM’s SOAR offering, explain how organizations can benefit from its implementation, and give a demonstration to show the solution’s major capabilities in action.

Fraud continues to be a major challenge for many organizations today. Industries such as finance, banks, payments, insurance, gaming, telecommunications, health care, etc. are dealing with increasing amounts of fraud and escalating sophistication of attacks. Account Takeovers (ATOs), synthetic fraud, and bots are a pervasive problem and continue to drain revenue from many businesses.

PAM (Privileged Access Management) has grown over these years to become a crucial set of technologies that addresses some urgent cybersecurity issues today.

Making your service available to everyone, everywhere, without losing control. On their digital journey, businesses are constantly launching new digital services, chased by competitive and innovative pressure.

Many organizations are currently looking into deploying their own CIAM programs, because they recognize CIAM’s potential to provide better marketing insights, improve customer registration experience and increase security. However, in the light of the upcoming data protection regulations like GDPR, which will profoundly change the way personal information collection is regulated, you must be especially careful and well-prepared for hot inter-departmental discussions concerning your future CIAM plans. Remember: even an inadvertent violation of the new compliance regulations can be extremely costly.
Relational databases are still the most widespread technology for storing and managing business-critical digital information. Manufacturing process parameters, sensitive financial transactions or confidential customer records - all this most valuable corporate data must be protected against compromises of their integrity and confidentiality without affecting their availability for business processes. The number of security risks databases are open to is also substantial, covering the information itself stored and processed in databases, underlying computing and network infrastructures, as well as applications accessing the data. Needless to say, databases remain a prime target for cybercriminals, especially in case of sophisticated targeted attacks.
Multiple solutions are available on the market to defend against such attacks, as well as to provide threat detection, activity monitoring, privacy protection, compliance and other aspects of data protection. Combining those individual building blocks into a comprehensive, layered and integrated security architecture is not an easy task. Many companies, especially small and medium businesses, simply have neither resources nor skills to design and deploy a complex suite of security products for protecting their databases from multiple threats across multiple environments.

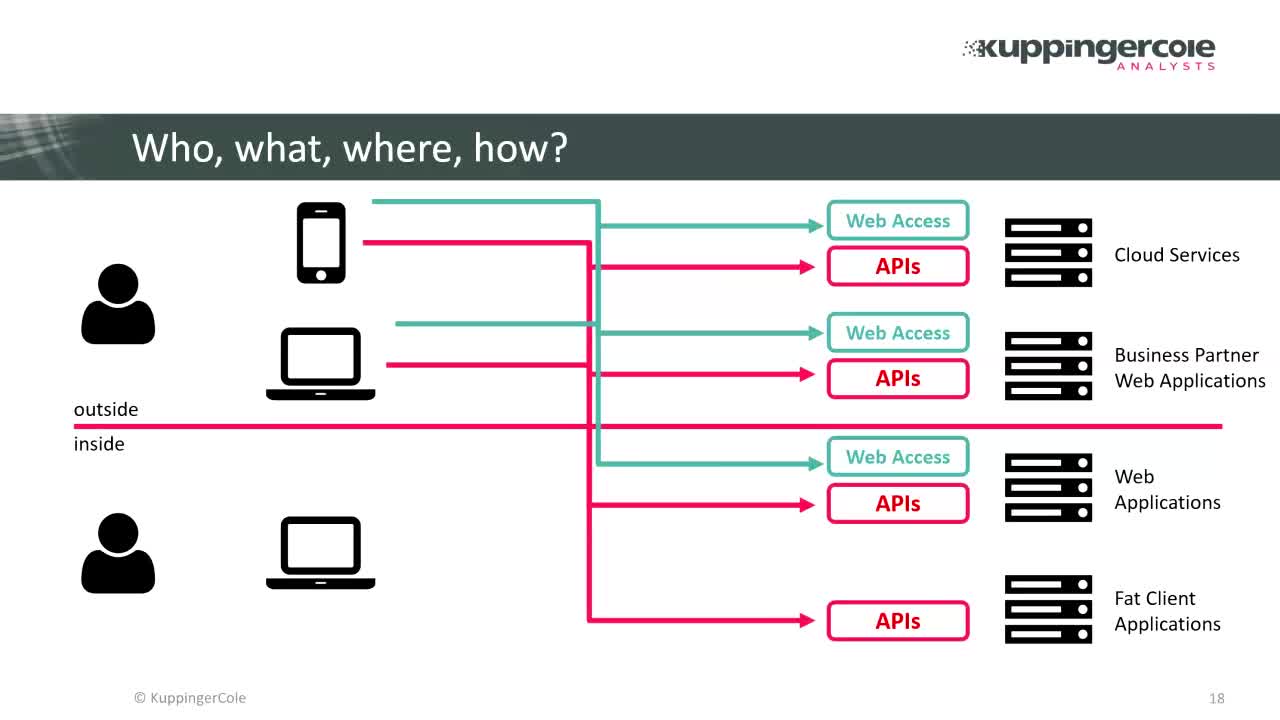
Like any other field of information technology, identity and access management has been rapidly evolving to meet new business challenges created by the Digital Transformation. As modern businesses are becoming increasingly open and interconnected, IAM solutions now need to cover not just employees, but customers, partners and smart IoT devices. They must be able to handle the growing complexity of managing and monitoring access to the company’s most valuable digital assets, regardless of their format, location or scale, while still maintaining compliance and protecting them from cyber risks.
Traditional enterprise IAM solutions still largely follow the siloed approach, with different departments and teams responsible for managing individual IT systems. Increasing complexity of IAM systems, especially for the largest, geographically distributed companies can also substantially reduce other employee’s business productivity, to say nothing about uncovering and mitigating security incidents. Next-generation IAM systems should be capable of utilizing continuous learning and reasoning to support humans in their decision-making and help them perform their tasks more quickly. Applications of cognitive technologies to cyber-security and IAM promise just that.

Adaptive Authentication tailors to what the users want (convenience) and prefer to use (mobile) – all the while adapting appropriately to access risk (smart), by balancing authentication strength with risk information. Today, we find both stand-alone solutions for Adaptive Authentication and integrated solutions, e.g. as part of Web Access Management and Federation tools.

For years, Enterprise Mobility Management (EMM) solutions have been the primary choice for companies to enable secure mobile access to enterprise applications. However, many experts believe that EMMs are the thing of the past, not being able to deal with cloud services and causing too much inconvenience on personal devices.
Cloud Access Security Brokers (CASB) are the one of the currently fastest-growing segments of security, promising a simple solution for the dreaded “Shadow IT” problem, ensuring security and compliance for accessing corporate data in the cloud. But are these two technologies really mutually exclusive?