Commissioned by Imperva
1 Introduction
Digital Transformation has profoundly changed our entire society within a relatively small timeframe. Every year, organizations produce staggering volumes of data that is not just critically important for their business processes but can be a lucrative digital product on its own merit. Back in 2017, an article in The Economist proclaimed that the world's most valuable commodity is no longer oil, but data. It is really difficult to argue with the "data is the new oil" claim: after all, the world's largest tech companies - Amazon, Apple, Facebook, Google, and Microsoft - all deal in digital data, generating billions in profits every quarter. However, accepting this comparison at its face value can lead many people to wrong conclusions.
After all, all oil in the world is more or less the same, and stockpiling too much of it can, in most cases, cause no harm to its owners. Not so with data! The biggest challenge of dealing with vast quantities of digital information is that unless it is acquired, classified, stored, and then processed according to very specific and complicated rules and regulations, its intrinsic value will be almost zero. Even worse, storing the wrong kind of data improperly and then losing it to a malicious actor, or even worse, negligence, can cause much more harm to an organization than any potential value that information had in the first place. Thus, one could claim that for modern businesses, data can be anything from "the new gold" to "the new garbage" or even a dangerous kind of "digital poison".
Unfortunately, once acquired, data of any kind must be protected. Valuable intellectual property, manufacturing parameters, or confidential financial records - losing any of these could disrupt critical business processes, devastating a company. Dealing with sensitive or personal information leads to another danger - regulatory compliance frameworks like the European Union's General Data Protection Regulation or California's Privacy Rights Act. Heavy fines imposed by respective governments on companies not properly protecting their customer's PII can be crippling.
With the average cost of a data breach exceeding $4M, direct financial losses alone can be catastrophic for many companies. High-profile "mega-breaches" that expose millions of sensitive data records can drive these costs up to hundreds of millions of dollars, but even the victims of smaller ones can be facing harsh compliance penalties. Massive reputation damage after a public breach disclosure only adds insult to injury. Everybody agrees, but clearly, whatever organizations are doing today to protect themselves from data breaches is not working, as evidenced by a growing number and scale of reported data breaches.
What are we, as a collective of IT and cybersecurity workers, doing wrong? After all, the market for data protection solutions is growing exponentially, with vendors offering a broad range of amazing innovative technologies to protect data stores from numerous cyber threats and potential attack vectors. Many databases now come with full stacks of security controls integrated into their cores. Cloud providers offer a multitude of managed security services to their customers. And yet, the number of breaches does not show any trend for improvement...
A critical consideration that many organizations fail to grasp is that information protection cannot be treated as a one-time "set and forget" event but must be a continuous process that follows the full lifecycle of digital information. This information protection life cycle begins at the moment data is created, discovered, or otherwise acquired with establishing the business value and risk associated with each piece of it and ends no sooner than the data is properly disposed of (either deleted or put into secure archival storage). Data must be properly managed and adequately protected at all times, and this protection is based upon a variety of tools and processes that must be applied during the whole active use life of the data.
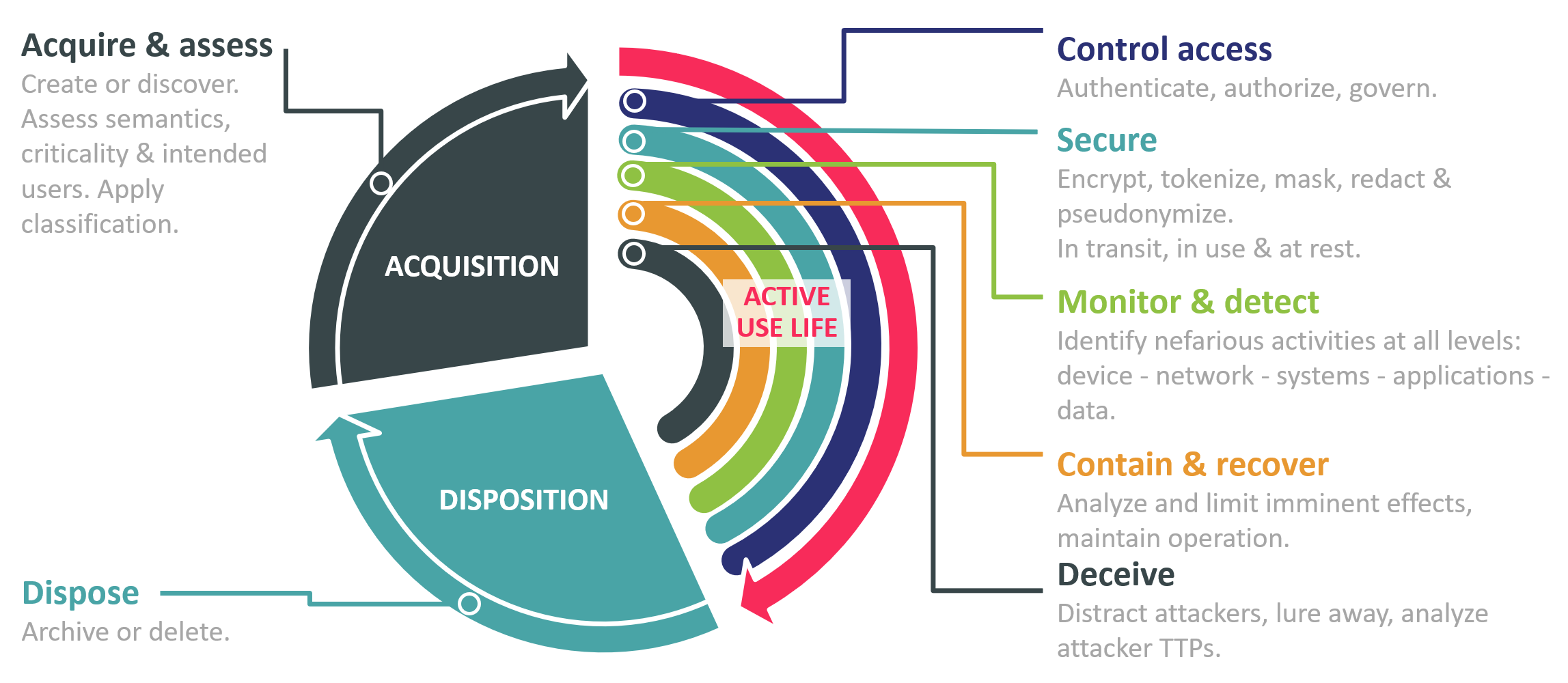
Data-centric security is an alternative approach toward information protection that has emerged as a direct response to the increasingly obvious failure of trying to focus on protecting IT infrastructures with tools like firewalls or DLP. Introduced by American security researcher Rich Mogull in 2014, the concept itself looks deceptively simple:
- Data must be self-describing and self-defending
- Security policies and controls must account for the business context
- Data must remain protected as it moves
- Policies must work consistently across different data management and security layers
Unfortunately, until we reach a stage when all our data somehow reaches self-awareness, translating these principles into a working architecture is more difficult than it looks. It requires a careful strategic approach toward building a multi-layered data protection architecture that combines multiple existing technologies with centralized policy management and enforcement. In this paper, we will look at various challenges we have to overcome during the journey to data-centric security and demonstrate how Imperva's portfolio of data protection solutions aligns with this approach, helping you secure not just your data, but all paths to it.
















































