Commissioned by Devolution
1 Introduction
The pressure on organizations to transform and digitize to create new products and services has meant different processes and technologies are entering the workplace, and some are creeping in without a strategy to manage them. These include trends such as Cloud, AI, Process Automation, IoT, DevOps, and XaaS (Anything as a Service). These trends are not confined to large enterprises but companies of all sizes, including Small to Medium sized Businesses (SMBs).
Taken together, these trends and technologies offer big opportunities for companies and organizations to ensure they remain competitive, but they also need to manage them and ensure they do not increase security and data risks. This is especially true of the massive increase of data and access points offered by these technologies which while enabling the digital change needed, can also increase the risk of access being hijacked by hackers, criminals or hostile state actors.
The modern infrastructure therefore requires access be granted to data and IT services to a wide variety and increasing number of stakeholders. These include traditional line employees, admins and managers but now also individuals from partner organizations, contractors and even customers. Some of these will request and need access to critical assets in order to fulfill their roles: these are known as privileged users.
Identity and Access Management (IAM) systems have long been used to manage access to data and services for less critical parts of the business: enabling employee sign on to workstations is one example. From IAM came a subset technology called Privileged Access Management (PAM) which was originally designed simply to manage passwords or two factor authentication (2FA) for critical assets across the organization. Until recently those with privileged access and more basic access were easy to manage as roles and access requests did not change all that much.
Digital transformation has changed the landscape. Today data access is lot less binary and much more fluid. Employees and other stakeholders may need privilege access to complete a certain task and then no longer need it. Contractors may be onsite for a short time also needing privilege access accounts, or when working remotely or at a subsidiary site. The increased exposure to data and critical assets has meant the threat of unauthorized access has been elevated, and modern PAM solutions must do as much as possible to prevent security breaches, as well as provide efficient speedy access to those who need it, when they need it – and more importantly deny it when no longer needed. It goes without saying that the digital landscape has made this a much more challenging market for PAM vendors and has transformed PAM into something much more than a simple administration tool. Done well, a PAM investment installation can increase business efficiency and competitiveness for an SMB.
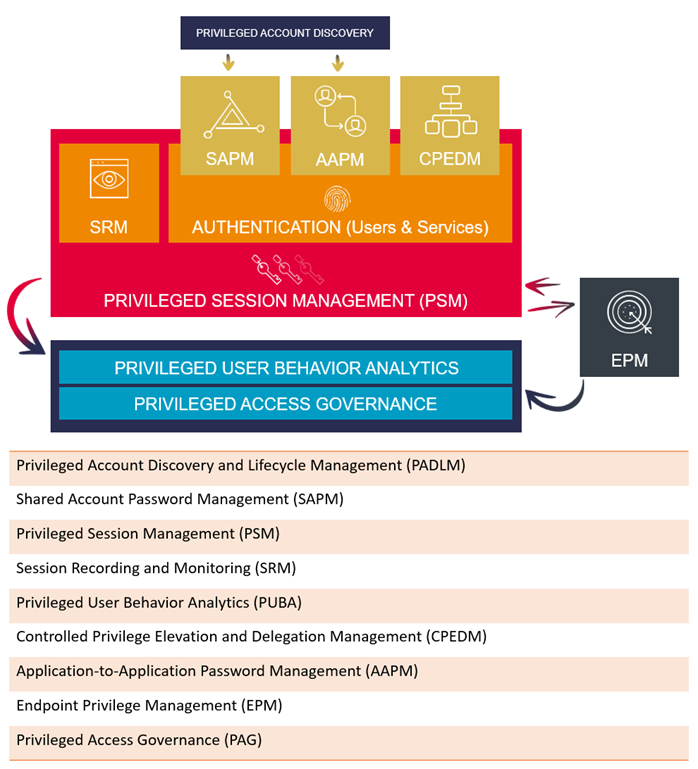
Given the complexity and speed of change of the modern organization any PAM solution must do more than simply provide privileged account access. It needs to be capable of monitoring access from an easy to understand central database and be able to reach into the extended network so that third parties, contractors and remote workers are monitored and given the right access when they need it. The best PAM solution must also go further and allow different tiered access of privilege so that line managers can grant access to certain employees and groups.
While credential vaulting, password rotation, controlled elevation and delegation are important, modern PAM should also offer privileged user analytics, risk-based session monitoring and advanced threat protection. It should also be able to flag suspicious behavior with blocking procedures automatically activated by PAM without need for human intervention, once red flags have been set.
In recent years, the perception of Privilege Management has changed considerably, and many vendors have entered the market. Many obviously target the large enterprise market but the SMB market is now also being catered for. While the scale may be different, smaller businesses are undergoing similar digital changes as bigger companies and in unique ways. Often, they act as the pivot between one organization and another and act as vital partners in digital supply chains. Therefore, they have similar identity and access challenges as they also seek to manage privileged accounts for their own employees, contractors and those of the businesses they are working with. Some SMBs will of course also be serving as managed service providers to bigger organizations, in which case security of data is paramount.
But while the PAM challenges might be similar, the solutions for smaller businesses may need to be different in scale and feature set. This whitepaper sets out why SMBs should now consider PAM, what are the essential components of PAM for SMBs and how new features and trends are making PAM easier for SMBs. It also provides SMB decision makers an overview of best practice in deploying and running a PAM solution that is fit for purpose and scalable.
















































