1 Introduction / Executive Summary
The combined impact of the pandemic driven shift to remote work with a connect-anywhere paradigm and the ongoing digital business transformation has inspired a higher awareness of cybersecurity concerns, requiring a profound change in the way we define access management. The term “Access Management” refers to the group of capabilities targeted at supporting access management requirements of organizations ranging from authentication, authorization, single sign-on, and identity federation traditionally found within Web Access Management (WAM) & Identity Federation solutions. These access management capabilities are well-established areas in the broader scope of Identity and access management (IAM), in which they are continuing to gain attraction due to emerging requirements for integrating business partners and customers.
Web Access Management & Identity Federation began as distinct solutions. (Web) Access Management is a traditional approach which adds a layer in front of web applications and takes over authentication and – usually coarse-grained – authorization management. Tools also increasingly support APIs for authorization calls to the system. Identity Federation allows splitting authentication and authorization between an IdP (Identity Provider) and a Service Provider (SP) or Relying Party (RP). Although Identity Federation can be used in various configurations, most vendors today provide integrated solutions that support centralized access management based on federation protocols such as SAML v2, OAuth, and OIDC.
The selection of an appropriate IAM solution is crucial for organizations as it plays a vital role in effectively managing, securing, and controlling access across their various entities. As a result, the adoption of Identity-as-a-Service (IDaaS) has become the preferred choice of customers and organizations for IAM purchases globally. The IDaaS market, with its ease of adoption and cloud-native integrations, is quickly overtaking the on-premises IAM market. The IDaaS market combines access management functions with Identity Governance and Administration (IGA) and Access Governance capabilities all delivered and managed as a service. Today, all IDaaS vendors predominantly deliver a cloud-based service in a multitenant or dedicatedly hosted fashion to serve the common IAM requirements of an organization's hybrid IT environment.
As an alternative to organizations managing the access management solutions themselves, some vendors provide Managed Services offerings, either by delivering per-tenant installations of on-premises solutions as a service, or by operating Software as a Service (SaaS) offerings. The first type of IDaaS Access Management vendors involve the traditional single sign-on (SSO) vendors that evolved to support web access management and handle web-centric cases along with identity federation but lacked the ability to address IAM requirements for cloud-based infrastructure. The second type of IDaaS Access Management vendors include those that are born in the cloud to manage access management requirements of SaaS and IaaS applications and services but have architectural limitations in how these could be extended to address access management for on-premises deployments.
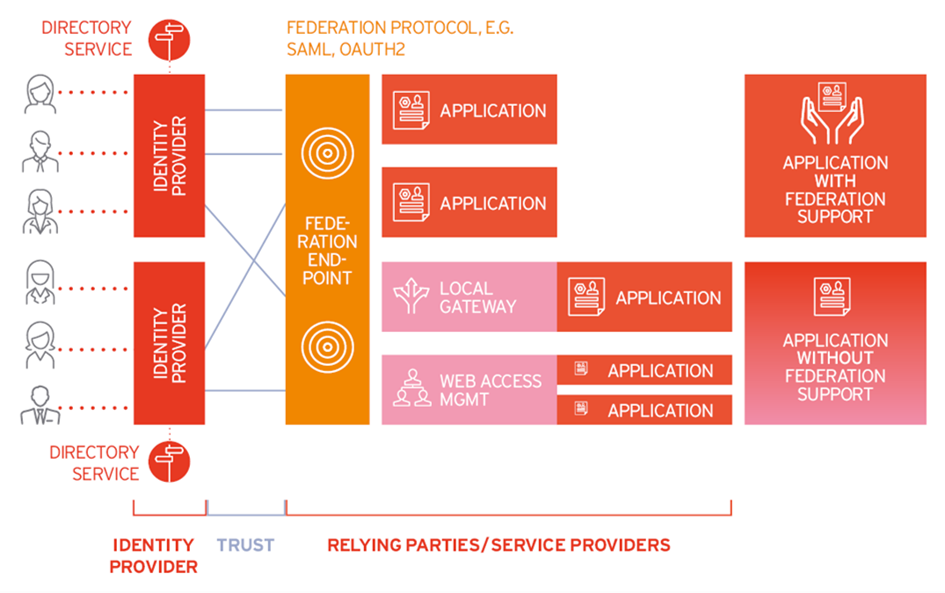
Figure 1: Access Management
Over the last few years, these vendors have made significant changes to their product architecture to become cloud-ready or support extended on-premises applications. These methods include delivering a SSO experience to users across multiple web sites and allow for centralized user management, authentication, and access control. Although traditional on-premises access management solutions was a focus of previous WAM & Identity Federation Leadership Compasses, KuppingerCole sees a convergence of this market with Access Management focused IDaaS solutions. Therefore, this Leadership Compass will consider solutions deployed on-premises, in the cloud, or as a hybrid model. Additionally, solutions offered as a managed service will also be considered, if the technology is owned by the MSP (Managed Service Provider).
As the access management and IDaaS markets continue to evolve and gain maturity, well-established players and innovative start-ups are starting to improve and deliver similar but unique solutions for consumer and enterprise use cases. Fundamental changes and improvements include simplified design of user journeys and enhanced authentication flows. In addition, new contact-free onboarding experiences from the workforce to the customers, the need for managing human-to-device relationships, passwordless authentication as the new normal, decentralized identities as a way of dealing with identities, the impact of policy-based access, and the convergence of IGA and access management are just some of the current trends that we are seeing.
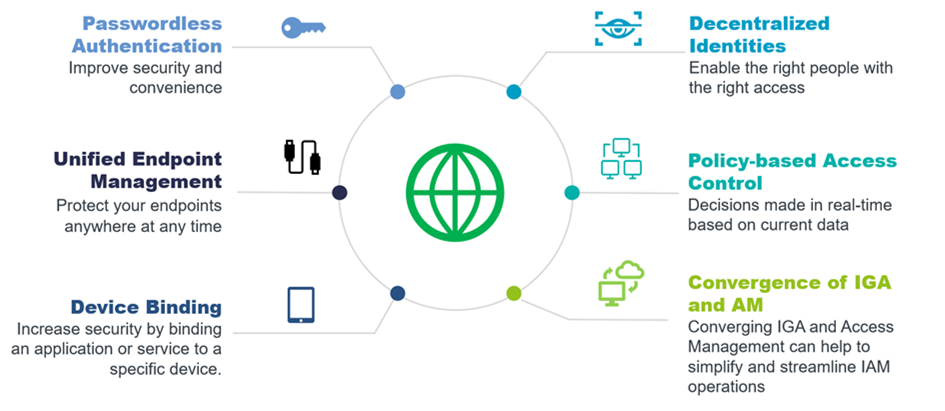
Figure 2: Access Management Trends
A few challenges organizations face, however, include the inability to integrate different authenticators, leverage existing technologies, support hybrid scenarios, and work with fraud detection solutions. In the future, seeing more support for fine-grain policy-based access management might become an expectation of ours. Finally, innovative features such as the ability to incorporate decentralized identities and support for onboarding flows involving identity verification would be a requirement as well. It is therefore important that businesses and organizations pursue greater use of access management solutions as they modernize their authentication systems.
Highlights
- The access management market provides several options to organizations and continues to evolve beyond the traditional capabilities seen in the past.
- Access management and Identity Federation should not be seen as separate segments in the IT market.
- Access management is used in any industry or sector that requires secure access to data and resources, and compliance with regulatory requirements.
- The impact of Covid-19 has accelerated innovation, rapid cloud adoption, and remote work, making the traditional approach of providing access less relevant as employees now access corporate data and resources from multiple locations.
- By implementing a modern access management solution, organizations are likely to reduce maintenance costs and instead rely on a modern platform that will provide organizations with the right tools to manage digital identities.
- The introduction of passwordless authentication solutions and decentralized identities will continue to drive innovation in the access management space.
- The Overall Leaders (in alphabetical order) are CyberArk, ForgeRock, IBM, Microsoft, Okta, One Identity, OpenText, Oracle, Ping Identity, and Thales.
- The Product Leaders (in alphabetical order) are 1Kosmos, Broadcom, Cloudentity, Cross Identity, CyberArk, EmpowerID, Exostar, ForgeRock, IBM, Microsoft, Okta, One Identity, OpenText, Oracle, Ping Identity, SecureAuth, and Simeio.
- The Innovation Leaders (in alphabetical order) are 1Kosmos, Cloudentity, CyberArk, ForgeRock, IBM, Microsoft, Okta, OpenText, Ping Identity, SecureAuth, and Simeio.
- The Market Leaders (in alphabetical order) are Broadcom, CyberArk, ForgeRock, IBM, Microsoft, Okta, One Identity, OpenText, Oracle, Ping Identity, RSA, and Thales.
1.1 Market Segment
Access management and Identity Federation should not be seen as separate segments in the IT market, but these technologies are inseparable. The business challenge is to support the increasingly growing "Connected and Intelligent Enterprise." Businesses require support for both external partners and customers. They need access to external systems, rapid onboarding, and request for access to external services such as Cloud services. Mobile devices are needed for organizations to support their workforce's desires to work anywhere from any device. These are only a few of the challenges organizations must face today.
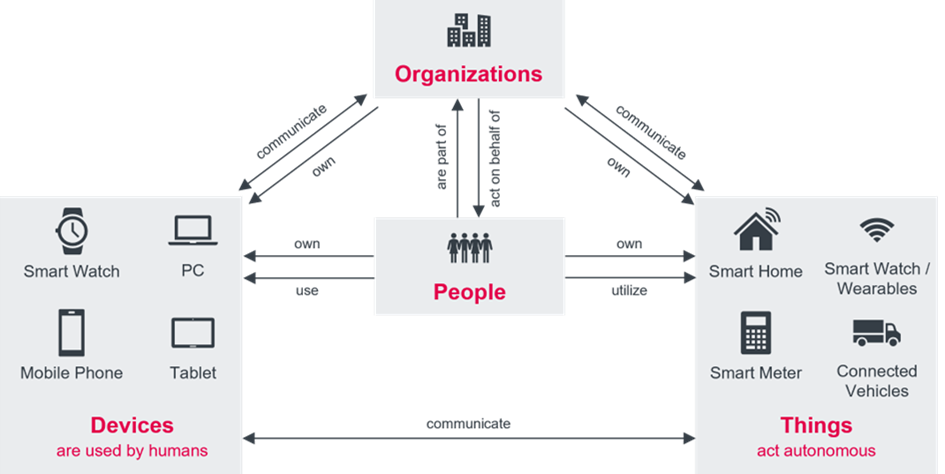
Figure 3: The increasingly connected enterprise ecosystem
The support for open identity standards continues to shape the direction of access management implementations. Some of the most popular authentication and identity federation standards include support for LDAP, Kerberos, OpenID, OAuth, SAML, and RADIUS. Organizations with a need for dynamic authorization management might require support for OPA, XACML or UMA. User provisioning services commonly require support for SCIM. And having access to the Access Management solution's functionality via APIs or other programmable interfaces will go a long way in keeping your IAM flexible and sustainable. API-based platforms typically require a developer-ready solution, providing API toolkits such as Webhooks or SDKs that facilitate rapid development.
Access management continues to evolve beyond the traditional capabilities seen in the past. Increasingly, we see access management solutions providing security for APIs becoming more readily available and driven by the need to meet emerging IT requirements that include hybrid environments that span across on-premises, the cloud, and even multi-cloud environments. And although Fraud Detection solutions, also referred to as Fraud Reduction Intelligence Platforms (FIPS), is often considered a different market with their separate offerings, there has been a noticeable up-tick in access management solutions providing some level of fraud detection capabilities ranging from the detection of identity fraud through Identity Proofing to the detection of unauthorized account takeover, response mechanisms, or support for user and device profiling as some examples. More recently, there has been some indication and interest of access management support for passwordless authentication and verifiable credentials. This Leadership Compass evaluates and reports on the level of fraud detection, passwordless authentication, and verifiable credentials support for each vendor, giving the reader an indication of the extent of this trend in the access management market.
Besides these technical capabilities, we also evaluate participating access management vendors on the breadth of supported capabilities, operational requirements such as support for high availability and disaster recovery, strategic focus, partner ecosystem, quality of technical support, and the strength of market understanding and product roadmap. Another area of emphasis is providing access management capabilities out-of-the-box, rather than delivering functionality partially through 3rd party products or services. Finally, we also assess their ability to deliver a reliable and scalable access management service with desired security, UX, and TCO benefits.
















































