1 Introduction
The term “Identity Fabrics” stands for a paradigm of a comprehensive set of Identity Services, delivering the capabilities required for providing seamless and controlled access for everyone to every service. They support various types of identities such as employees, partners, consumers, or things. They deliver the full range of identity services required by an organization.
Identity Fabrics are not a single technology, tool, or cloud service, but a paradigm for architecting IAM within enterprises. Commonly, the services are provided by a set of tools and services. However, most organizations that are using this paradigm as a foundation for the evolution of their overall IAM tend to build on a strong core platform for delivering major features and complementing this by other solutions.
In this Leadership Compass, we evaluate solutions that can serve as a foundation for customers creating their own Identity Fabrics by delivering a wide range of capabilities in a modern architecture.
Thus, this Leadership Compass analyzes which of the IAM offerings in the market are best suited to form the foundation for an Identity Fabric, in delivering
- a broad range of IAM capabilities, at minimum including a good level in both IGA (Identity Governance and Administration) and Access Management (Identity Federation, Multi Factor Authentication, etc.)
- by providing a comprehensive set of APIs for consuming these services, beyond the admin and end user UI/UX
- this in a modern architecture, following paradigms such as microservices architectures and container-based deployments
- support for different deployment models, serving the needs of customers for options in their operating models
- support for all types of identities, including employees, business partners, customers and consumers, connected things, devices, and services
In sum, solutions must not only deliver functionality and support for all types of identities, but also meet our requirements regarding the architecture, deployment model, and their interoperability with traditional applications, cloud services, and new digital services.
1.1 Market Segment
Digital business has evolved from simple e-commerce websites from the 90s. Modern digital business models are complex, distributed, multidimensional and involve many parties in a variety of roles. This has a direct impact on how communication takes place, how people work together and how services and goods are created and delivered to customers.
Employees, partners, service providers, customers, devices, and processes use and provide services. Access is made from and to any conceivable location to services that are somewhere between on-premises data centers, the cloud, mobile systems.
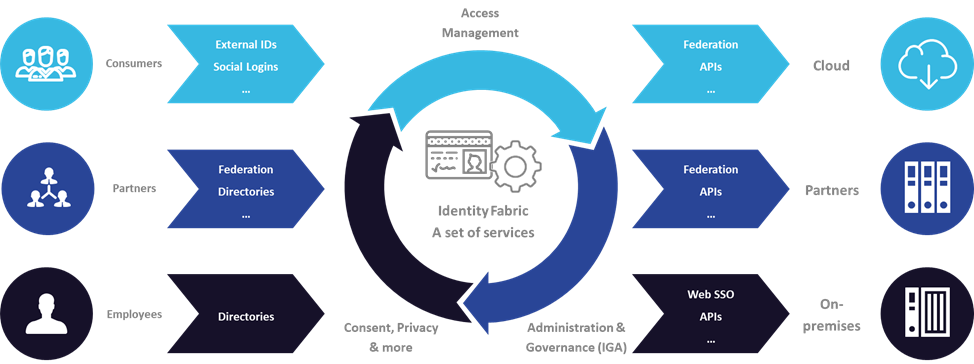
The formerly classic corporate network with clearly defined "inside" and "outside" has given way to a massively hybrid, new IT reality. IAM (Identity and Access Management) is the essential security infrastructure for this and at the same time a facilitator of these new services, models and forms of cooperation.
To make this possible, IAM must be transformed. It needs to be converted into a consolidated portfolio of isolated but corresponding services that enable to connect anything and anyone via a comprehensive architecture, and to make services available to all users everywhere: secure, scalable and without losing control.
“Identity Fabric” refers to a logical infrastructure for enterprise Identity and Access Management. It is conceived to enable access for all, from anywhere to any service while integrating advanced features such as support for adaptive authentication, auditing capabilities, comprehensive federation of services, and dynamic authorization capabilities.
Digital technologies influence and change all areas of an organization, and this fundamentally shapes the way communication takes place, how people work together and how value is delivered.
IT architectures, in turn, are undergoing profound structural changes to enable and accelerate this gradual paradigm shift. This evolution reflects the transformation resulting from the changing challenges facing virtually every organization worldwide for a long time in different contexts. They affect processes and systems alike and the underlying architectures.
In order to remain competitive in this charged environment, companies strive to be as flexible as possible by adapting and modifying business models and, last but not least, opening up new channels of communication with their partners and customers. With the rapid growth of cloud and mobile computing, businesses are becoming increasingly networked. The very idea of a company's outer boundary, the concept of a security perimeter, has practically ceased to exist.
The assumption that previously independent identities (employees, customers, partners, mobile devices, etc.) in an enterprise can be regarded as isolated is no longer valid. The management of identities and permissions in digital transformation is the key to security, governance and audit, but also to system usability and user satisfaction. The demands on a future-proof IAM are complex, diverse and sometimes even conflicting. These include:
- Different types of identities (first and foremost, consumers) must be integrated quickly and securely in user-friendly processes.
- At the same time, users should be able to retain control over their identities by bringing their own identities with them (BYOID).
- Employees (internal and external) should be able to use the devices they prefer.
- Secure access to working environments must be possible no matter where users and systems are located.
- Zero Trust such as continuously verifying access must be part of the capabilities.
- Identities must be linked to reflect relationships within teams, companies, families, or partner organizations.
- Identities maintained in trusted organizations should be directly and reliably integrated and authorized in each organization’s IAM.
- Identities should be able to do business and execute payments.
- All relevant laws and regulations must be observed.
- At the same time, KYC processes are to be optimized, enabling rather than deterring visitors from using the service.
- Existing data should be usable by analytics and artificial intelligence applications.
- All this must apply to all possible identities, beyond people, so that devices, services and networks are integrated into our next generation IAM infrastructure.
- New digital services must be able to consume the identity services, building on a consistent set of services e.g., for onboarding and authenticating users.
Today's IAM systems meet, if at all, only a fraction of current requirements. In many cases these IAM infrastructures stem from traditional enterprise IAM systems, sometimes extended with an additional customer identity system, most probably siloed. At the same time, they are often monolithic in design and implementation, making it difficult to break them down into individual components.
Unfortunately, this is exactly one of the central challenges. In many situations, the path to an identity fabric will pass along the challenge of unambiguously isolating individual functional components and exposing their interfaces through secure and accessible APIs. This applies to source systems that provide identities and enforce permissions, but also to all target systems. And in individual cases it can also apply to one or more legacy IAM systems if a replacement is difficult or not possible in a timely manner.
If organizations need to seamlessly give access to all users, wherever they are accessing from, and provide any digital service to these users, the Identity Fabric must be able to securely mediate that very connection between user and service.
To achieve this, we are shifting away from isolated, singular systems to a logical platform that provides and orchestrates a set of required IAM services and related functions. The way these services are delivered can vary: they may involve existing as-a-service offerings or might be based on existing on-premises services.
These services can be located in a public cloud, they can be web applications with or without support of federation standards, they can be exclusively back-end services only accessible via REST APIs, or even legacy applications encapsulated by some kind of middleware. At the same time, it might be even valid to integrate redundant services for different usage scenarios.
What they all have in common is that they are always part of a consistent framework of services, capabilities and building blocks as part of a well-defined, loosely coupled overall architecture that is ideally delivered and used homogeneously via secure APIs.
However, the agility of the digital journey requires IT to provide seamless access to all these services while maintaining control and security. In parallel, all requirements for scalability, performance and resilience must be met.
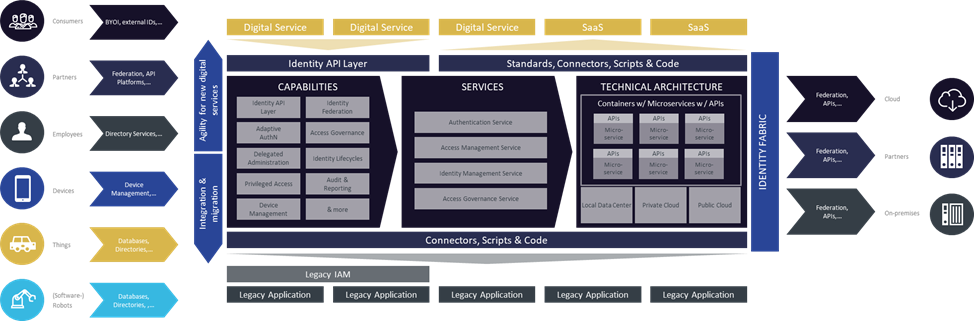
Identity fabrics are not an entirely new concept. They are based on the challenges of a modern workplace and digitalization, which is responsible for almost everything. The resulting tasks, which cannot be solved with traditional IAM paradigms, must be mastered.
They combine current and proven IAM concepts, supplemented by security by design and APIs, a service-oriented IT concept (which can certainly be implemented in microservices) and modern delivery concepts for cloud, hybrid infrastructures, containers and their orchestration or serverless infrastructures.
The way towards the implementation of an Identity Fabric as a strategic, hybrid IAM platform is a company-specific challenge, because the actual requirements and the individual starting points are company-specific.
KuppingerCole recommends the following strategic approach, which should be mapped to meaningful technical, conceptual and project planning measures.
- Define a comprehensive and efficient target architecture, based on microservices architecture and container-based deployment, and work towards its implementation in well-organized individual projects.
- Proceed consistently, step by step and in an integrated manner.
- Provide your company with all the necessary services it needs for its current and strategic identity needs.
- Offer consistent backend services and develop an identity API platform as the foundation.
- Define a clear architecture layer model. Reuse and encapsulate whatever and whenever you can.
- Organically add missing functionality to your target architecture when needed.
- Replace inappropriate components along the way, but if possible, later.
This transformation of your IAM infrastructure into an Identity Fabric does not need to be and is not meant to be disruptive by any means. It can be executed in a way that allows for stable and reliable continuous operations without any kind of “big bang” while augmenting new functions and enabling new categories of access paths, ideally driven by changing corporate demands.
Required technological and architectural building blocks are already available and proven reliable. However, choosing the right components to enable support for individually required new authentication and authorization use cases with stepwise extended platform capabilities demands strict strategic oversight and management.
To clarify it once again: There is no “standard Identity Fabric”. An Identity Fabric is based on the required capabilities and services for digital identities an organization has. These commonly involve certain key capabilities but will always differ slightly. Also, the implementation of an Identity Fabric commonly builds on very few (one or two) main technical components for IGA and Access Management, but is complemented by additional components that provide further services and capabilities. There might be even some level of redundancy, either in migration or for technical or organizational reasons. However, the concept of Identity Fabrics serves well for designing and implementing a modern IAM that is modular, flexible, and provides the capabilities required, including a consistent Identity API layer that allows digital services to consume the identity services.
















































