1 Introduction
Fraud is a major cost to businesses worldwide. Cybersecurity Ventures estimates that cybercrime costs will reach $10.5 trillion by 2025. Fraud has been exacerbated by the Covid pandemic. Banking, finance, payment services, and retail are some of the most frequent objectives of fraudsters, as expected. However, insurance, gaming, telecommunications, health care, cryptocurrency exchanges, government assistance agencies, travel and hospitality, and real estate are increasingly targeted as cybercriminals have realized that most online services trade in monetary equivalents. Moreover, after years in the sights of cybercriminals, banking and finance in general are better secured than other industries, so fraudsters attack any potentially lucrative target of opportunity. Fraud perpetrators also continually diversifying and innovating their Tactics, Techniques, and Procedures (TTPs).
The most prevalent types of fraud businesses and government agencies experience today are:
Account Takeover Fraud (ATO) - occurs when fraudsters use breached passwords and credential stuffing attacks to execute unauthorized transactions. Additional means for account takeover fraud are malware attacks (man in the middle and man in the browser) as well as the use of Remote Access Tools via Trojan or social engineering scams.
New Account Fraud (NAF) – also called Account Opening (AO) Fraud, often happens as a result of using stolen identities or assemblages of personal information to create a synthetic digital ID, and can be more difficult to detect but has advantages for attackers. This type involves gathering complete sets of or bits of PII (Personally Identifiable Information) on legitimate persons to construct illegitimate accounts. Educational, financial, and medical records can be sources of PII used for assembling fake accounts, which are then often used to abuse promotions and instant loans and/or used as mule accounts to move money around.
Other common fraud types that are encountered include:
SIM Swap Fraud – a SIM swap is a special type of ATO involving a change within Mobile Network Operator’s (MNO’s) device mapping database that points a phone number to a specific SIM card installed in customer phones. SIM Swap Fraud occurs when malicious actors convince MNO employees to associate victims’ mobile phone numbers with the fraudsters’ devices. Fraudsters may try to get information directly from victims or may buy victim info on the dark web in order to set the stage for these kinds of attacks. In this sense, it is a special kind of ATO fraud that relies upon social engineering and/or insider fraud.
Insider Fraud - includes not only financial theft by employees, contractors, or partners, but also the theft of intellectual property (IP), which may include customer information from CRM systems
Screen Scraping – programmatically scraping information entered into web forms by consumers and sending to other web services. This technique is (unfortunately, because it is insecure) sometimes used for legitimate purposes.
Inventory Skimming or Depletion – perpetrated largely by bots that buy up a retailer’s inventory to re-sell.
Fraudulent Insurance Claim Submission – insurance agents’ and brokers’ credentials are captured and used to authorize fraudulent insurance claims.
Real Estate Escrow Mis-Direct – real estate agents’ credentials are captured and used to send emails to customers to have them transfer large sums (down payments) to fraudsters’ accounts. These transfers are usually unrecoverable and can be devastating to home buyers.
Banking Overlays – malicious apps that look like login screens for mobile banking apps, designed to harvest credentials and hijack transactions.
Travel Site Overlays - malicious apps that look like login screens for mobile travel apps, designed to harvest credentials and hijack transactions.
The chief mitigation strategies against these types of fraud employ real-time risk analytics and decisioning. Risk-based Multi-Factor Authentication (MFA) can eliminate a substantial portion of ATOs by increasing authentication assurance levels. Risk-based MFA often evaluates credential intelligence, device intelligence, user behavioral analytics, and behavioral/passive biometrics. To decrease NAF/AO/Synthetic Fraud, increasing identity assurance at registration and authentication time with identity vetting services is recommended. Bot detection and management can also be helpful at cutting other types of fraud.
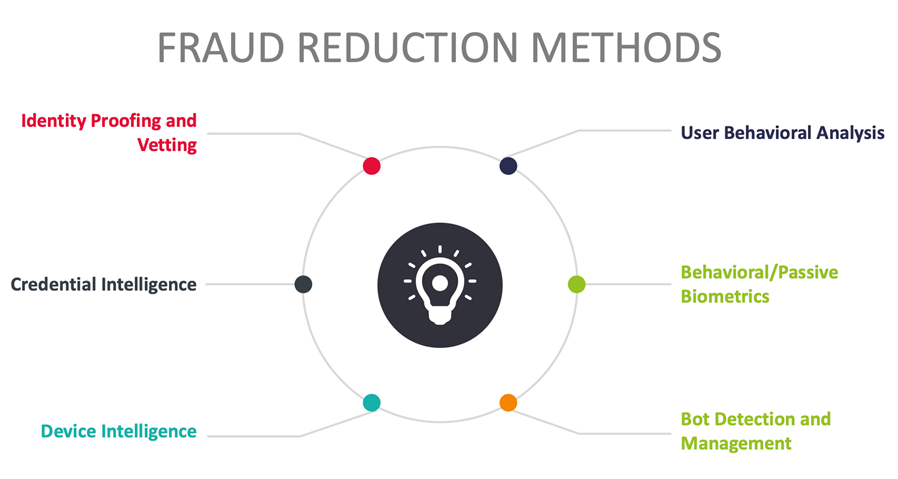
Risk-based MFA and transaction processing solutions operate optimally when integrated with or informed by Fraud Reduction Intelligence Platforms (FRIPs). FRIPs provide to risk-based MFA and transaction processing systems the information needed to make more accurate decisions on whether or not transactions should execute. FRIP solutions generally provide up to six major functions:
- Identity proofing/vetting
- Credential intelligence
- Device intelligence
- User behavioral analysis
- Behavioral/passive biometrics
- Bot detection & management
This report covers solutions that aggregate multiple fraud intelligence sources and provide advanced analytics services for customer organizations to augment their applications with the goal of reducing costly fraud.
1.1 Highlights
- Fraud Reduction Intelligence Platforms are increasingly sought after by consumer facing businesses in all industries. Account takeovers and new account fraud has been rising for years but has been exacerbated by the Covid pandemic.
- More FRIP solutions incorporate identity proofing directly and/or allow customers to extend identity vetting by enabling connections to 3rd-party authoritative attribute providers. The most innovative platforms offer remote identity verification apps and/or SDKs.
- Compromised credential intelligence is not ubiquitously used. Most vendors use credential intelligence from among their customer bases but sharing and consumption of external sources is not common.
- User behavioral analysis capabilities are expanding and getting more detailed in terms of transaction level attributes.
- Device intelligence, as a key indicator of fraud, is more widely collected and used effectively by FRIP service providers.
- Behavioral biometrics are catching on as more FRIP vendors provide built-in capabilities or partner with specialists to add this to their portfolios. Behavioral biometrics are a leading driver of innovation in the FRIP market.
- Bot detection capabilities are essential, and this is reflected by the fact that most vendors in this space now have at least basic bot detection functions. Advanced bot management is not commonplace yet within FRIP solutions.
- The product leaders are ID Dataweb, Transmit Security, Experian, BioCatch, OneSpan, IBM, Broadcom, and Arkose Labs.
- The innovation leaders are ID Dataweb, BioCatch, IBM, Transmit Security, Experian, OneSpan, and Arkose Labs.
- The market leaders are Broadcom, Experian, Neustar, Outseer (RSA), IBM, OneSpan, and Transmit Security.
















































