1 Introduction
The KuppingerCole Leadership Compass provides an overview of vendors and their product or service offerings in a certain market segment. This Leadership compass focuses on the market segment of Identity-as-a-Service (IDaaS) with a focus on IGA (Identity Governance and Administration, i.e. Identity Provisioning and Access Governance) technologies. IDaaS IGA, as the market is termed, has observed a significant growth in terms of new IAM (Identity and Access Management) purchases and is ermerging as one of the fastest-growing markets of IAM characterized by cloud-based delivery of traditional IAM services.
The overall IDaaS market, driven largely by web-centric use-cases in its early days, now offers full-fledged delivery of IAM capabilities irrespective of application delivery models. The significant growth of the IDaaS market can be attributed to the ever-increasing demand of organizations to achieve better time-to-value proposition over on-premises IAM deployments and to extend IAM capabilities to meet the security requirements of growing SaaS portfolio.
1.1 Market Segment
IDaaS is a growing market segment of IAM characterized by delivery of traditional IAM services in an as-a-service model, with immediate to at least very rapid deployment and standardized capabilities, in contrast to individual implementations per customer. The market, driven largely by cloud-centric use-cases in its early days, now offers full-fledged delivery of IAM capabilities irrespective of application delivery models. The IDaaS market has registered significant growth over the last few years primarily driven by the need of organizations to:
- Achieve better time-to-value proposition over on-premises IAM deployments
- Extend IAM capabilities to meet the security requirements of growing SaaS portfolio
- Adopt global IAM standards and practices with access to industry expertise
- Reduce internal IAM costs and efforts to keep up with the market trends
- Limit internal IAM failures in project delivery and ongoing operations
IDaaS vendors have originated from distinct backgrounds and therefore their abilities to support the primary IDaaS use-cases vary significantly. Most of the IDaaS vendors come from different backgrounds including:
- Access Management vendors that offered broader IAM capabilities required for large IAM implementations but could not easily extend these functions to support rapidly emerging cloud and consumer access use-cases.
- IGA (Identity Governance and Administration) vendors that traditionally offered support for identity administration and access governance on-premises but neither could extend these capabilities to applications in the cloud, nor could support access management beyond basic authentication and authorization
- Traditional SSO (Single Sign-On) vendors that have evolved over time to support web and cloud access use-cases but are deficient on common Identity Governance and Administration (IGA) functions required by most organizations for basic IAM implementation
The IDaaS market consolidates Access Management functions with IGA and Access Governance capabilities thrown in – all delivered and managed as a service. Today, all IDaaS vendors predominantly deliver a cloud-based service in a multitenant or dedicatedly hosted fashion to serve the common IAM requirements of an organization’s hybrid IT environment. The common IAM capabilities served by most IDaaS vendors can be grouped largely in three categories:
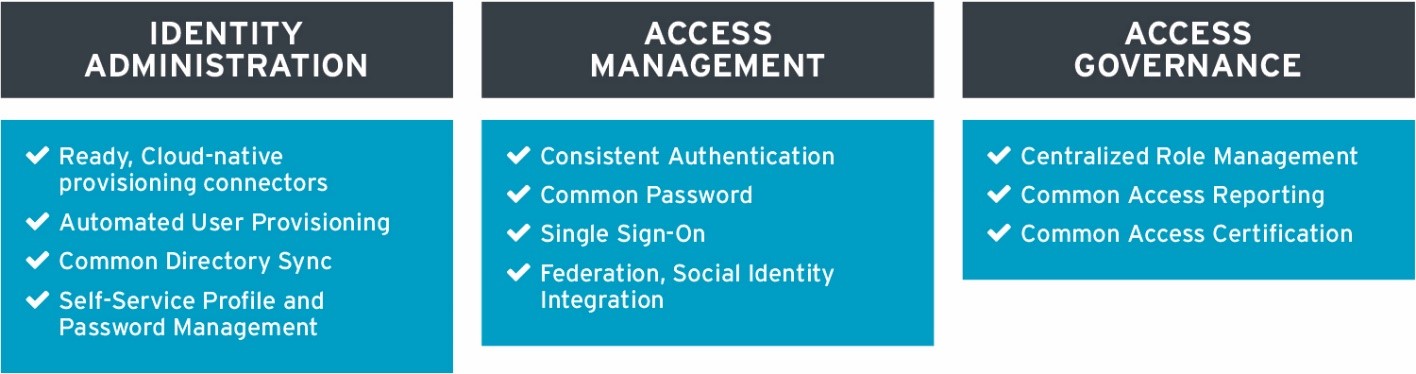
Identity Administration: This represents the group of capabilities required by organizations to administer identity lifecycle events including provision/ de-provision of user accounts, maintaining identity repository, managing access entitlements and synchronization of user attributes across the heterogeneous IT environment. A self-service user interface allows for requesting access, profile management, password reset, and synchronization. Configurable connectors, either cloud-native or based on gateways back to on premises environments, offer automated user provisioning to both on-premises as well as SaaS applications. Other common identity administration capabilities include administrative web interface, batch import interface, delegated administration, SPML, and SCIM support.
Access Management: This refers to the group of capabilities targeted at supporting access management requirements of organizations ranging from authentication, authorization, single sign-on and identity federation for both on-premises and SaaS applications delivered as a cloud service. The underlying support for industry standards such as SAML, OAuth and OpenID Connect can vary but are largely present in most IDaaS offerings. API security and web access management gateways are fast becoming a differentiator for IDaaS vendors looking to offer competitive access management capabilities and so is social identity integration – which now represents a basic qualifier for consumer access use-cases.
Access Governance: Access governance represents the group of capabilities that are least mature and still frequently absent from the portfolio of IDaaS vendors, partly due to architectural limitations and partly due to ownership issues. While many organizations still prefer to keep access governance on-premises for better control and auditing purposes, several others are moving it to the cloud for ease of integration and better time to value as their SaaS portfolio continues to grow. IDaaS vendors may have some serious limitations in how they could support integration with legacy on-prem systems for common access governance capabilities such as auditing and reporting, and so it is important for IAM leaders to ensure they assess their access governance requirements aligned with their IAM vision before starting to evaluate IDaaS vendors for their access governance capabilities.
Generally speaking, supporting hybrid IT environments is amongst the main challenges for IDaaS, across all areas. Connecting back to legacy web applications is more challenging than with most on-premise solutions, and Identity Provisioning as well. This needs to be kept in mind and carefully considered during choosing an IAM solution. The strength and weaknesses of IDaaS solutions in connecting back to on-premise environments are an important factor throughout our evaluation in this Leadership Compass.
As the IDaaS market continues to evolve, its adoption is inhibited by several factors including the concerns of data residency, dependency on providers internal security controls and the ability to address scenarios that require extensive customizations to address organization’s internal process complexity and where organizations believe these could be better solved with on-premises IGA or access governance product deployments. However, we observe a clear trend to shifting also more complex use cases such as access governance to IDaaS.
In the later parts of this document, we also discuss the evaluation criteria important for IAM leaders to help decide whether they should move to an IDaaS platform for their IAM requirements or a conventional on-prem IAM deployment should suffice their IAM requirements in the short to midterm.
Depending on the key focus, architectural type and product origin, which affect their overall ability to support IDaaS functions, most IDaaS vendors can be classified in two major categories - either as Access Management or IGA focussed IDaaS vendors:
1. IDaaS Access Management (IDaaS AM)
There are primarily 2 types of AM focussed IDaaS vendors:
The first type is the traditional SSO vendors that progressed overtime as WAM vendors to mostly address web-centric use-cases along with identity federation but originally lacked the ability to address IAM requirements for cloud-based infrastructure and applications. Over the last few years, these vendors have made significant changes to their product architecture to make them cloud-ready, however, there remain certain limitations in addressing cloud AM requirements.
The second category of IDaaS AM vendors are the vendors that are born in the cloud to primarily manage access management requirements of SaaS and IaaS applications but have architectural limitations in how these could be easily extended to address access management for on-prem applications.
2. IDaaS Identity Governance and Administration (IDaaS IGA)
The IGA focused IDaaS vendors are the ones that have traditionally been offering identity administration capabilities including identity provisioning, lifecycle management and access governance across on-premises IT applications and systems. The key focus of these vendors on managing user identities in an increasingly complex IT environment combined with the demand and adoption trends of identity-centric solutions in the market has led these vendors to focus lesser and lesser on building access management capabilities. The move to the cloud, however, required them to support basic access management functions, in addition, to be able to support the delivery of all IGA capabilities to compete with the new IDaaS entrants. The depth of IGA functions delivered by these vendors in a cloud-based delivery model to support a hybrid IT environment not only remains questionable due to the technological limitations but also due to the consumption archetypes of on-premises IT applications and systems.
The IDaaS market continues to evolve with a significant push from organizations looking to adopt cloud-based delivery of security services including IAM. With IDaaS vendors slowly bridging on the gap with traditional on-premises IAM software in terms of depth of functionalities, particularly IGA, they present a strong alternative for organizations to replace existing on-premises IAM deployments.
Besides replacing traditional on-premises deployments for workforce IAM, IDaaS has evolved as a strong enabler of CIAM offering the required availability and scalability. With IDaaS starting to dominate new IAM purchases for most use-cases across the industry verticals, traditional IAM vendors are gearing up to deliver more cohesive IDaaS capabilities as part of their security services, including tighter integrations with Cloud Access Security Broker (CASB), Enterprise Mobility Management (EMM) and User Behavior Analytics (UBA).
IDaaS is only delivered as SaaS, hosted and managed by the IDaaS vendor itself. Vendors that use the on-premises software provided by other vendors to offer hosted and managed IAM services are not considered IDaaS vendors. Mostly combined in separate service bundles based on adoption and usage trends, most services are priced per managed identity or active users per month. Some functions such as user authentication or fraud detection can be charged on per transaction basis depending on the function’s delivery and consumption.
The use cases for IDaaS technology adoption and their primary characteristics as observed by the industry are listed below:
- Web Access Management - Many organizations have the need to deliver basic authentication and authorization for the variety of internal web applications they have across their IT environment. IDaaS offers basic authentication and session management capabilities including single sign-on, coarse-grained authorization and identity federation required by these organizations to meet the most common web access management demands.
- Hybrid Access Management - Many organizations today have an urgent need to extend internal access management policies to the range of SaaS and IaaS platforms being integrated into their IT application portfolio. IDaaS can provide a seamless extension of on-premises IAM capabilities to the applications and infrastructure in the cloud in an effective and secure manner. There are, however, limitations in how they can support internal legacy IT systems versus SaaS applications.
- Workforce IAM - With most traditional IAM deployments suffering from internal inefficiencies, staffing, and budgeting concerns, IDaaS promises a flexible approach for organizations looking to on-board a workforce IAM program to deliver better time to value and agility. With IDaaS commonly offering capabilities across identity administration, access management and access governance, more advanced features such as access certification, role lifecycle management, SOD controls management etc. may not be adequately supported or entirely absent.
- Consumer IAM - IDaaS delivery model with its significant business value in terms of better flexibility and time to value has become a strong enabler of CIAM – offering the required scalability and availability. Most IDaaS vendors are aggressively building on or acquiring capabilities to better support CIAM use-cases, for eg., Okta acquired Stormpath and Ping Identity acquired UnboudID to strengthen their CIAM features. Most IDaaS vendors today support capabilities required by organizations to support CIAM programs including social identity integration, progressive customer profiling, fraud and risk intelligence as well as identity analytics.
There may be more use cases that are driven by the organization and business-specific access management requirements; however, most will fit well into one of these categories.
















































