1 Introduction
In today's digital landscape, managing and protecting customer identities and data has become essential for business organizations across the globe. As organizations began reaching out to their customers and gathering information about the consumers using their products and services, they found that they needed to provide a better digital experience using consumer's mobile devices or social networks and providing a more effortless onboarding experience for consumers. Still, they also had to be concerned about privacy compliance, such as GDPR. Because of this, the need for Customer Identity and Access Management (CIAM) solutions has come to the forefront for safeguarding sensitive customer information, ensuring regulatory compliance, and enhancing the user experience.
CIAM systems are designed to provision, authenticate, authorize, collect, and store information about consumers from across many domains. Compared to regular IAM systems, information about these consumers often arrives from many unauthoritative sources. Some solutions in this space provide connections to various identity-proofing services to strengthen the integrity of consumer attributes. CIAM systems generally feature weak password-based authentication, but also support social logins and other authentication methods. Information collected about consumers can be used for many different purposes, such as authorization for resources or for analysis to support marketing campaigns or Anti-Money Laundering (AML) initiatives. Moreover, CIAM systems must be able to manage many millions of identities and process potentially billions of logins and other transactions per day.
Some common features found in CIAM solutions include:
User Registration: CIAM systems register new users by collecting and verifying their identity information, sometimes through integration with identity-proofing services, facilitating the process of email verification, phone number validation, and other identity verification mechanisms. Although self-registration portals are typically provided to consumers to enter their information, progressive profiling can also be used to collect customer information on an as-needed basis rather than requesting it all up front. Increasingly we see organizations looking for higher identity assurance to deter new account fraud during the registration phase. In those cases, remote onboarding via mobile apps that can verify documents with OCR or NFC and do registrant-to-selfie photo matching are preferred.
User Authentication: CIAM solutions often provide a variety of authentication methods such as passwordless authentication, multi-factor authentication (MFA), biometrics, social login, as well as mobile push apps, FIDO, risk adaptive and continuous authentication. Password authentication is still too prevalent in consumer and customer scenarios, but most CIAM solutions offer higher security and more user-friendly options.
Single Sign-On (SSO): SSO allows users to access multiple digital services or applications through federated authentication mechanisms. SSO simplifies user management, can enforce the level of authentication used, and improves user experience by reducing the number of times a user needs to authenticate. SSO is particularly useful for organizations with multiple brands and storefronts, allowing them to offer a much better user experience.
Consent Management: CIAM solutions often include features for managing user consent and preferences regarding data usage and sharing. Consent management is essential when compliance with data protection regulations like EU GDPR, Canada's PIPEDA, and California's CCPA is required. Consumer account dashboards are standard mechanisms for giving users consent monitoring, granting, and withdrawal options.
Security and Business Intelligence: CIAM security systems continuously monitor user activities and employ threat detection mechanisms to identify and respond to suspicious behavior. Including 3rd-party fraud and compromised credential intelligence can provide a runtime evaluation of internal or external cyber threat or fraud risk. Identity analytics within administrative dashboards and reports on common identity attribute activities can include indicators like failed logins, consumer profile changes, credential changes, and registration tracking. For business intelligence, transforming data about user activities into actionable information for marketing and sales teams is a key feature and business driver for adoption.
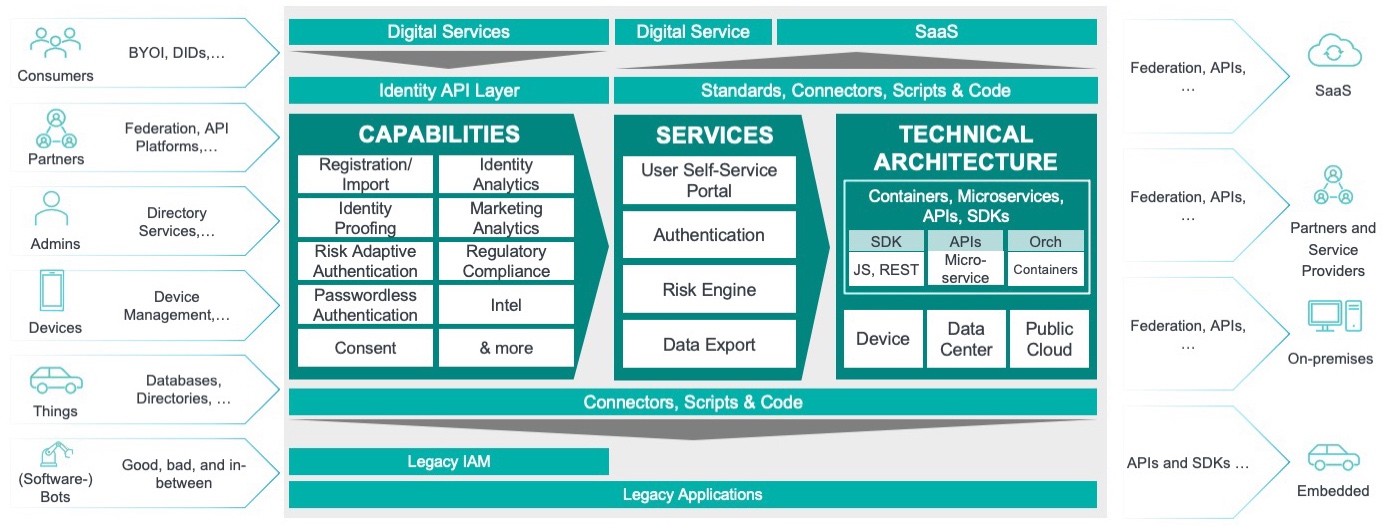
Figure 1: CIAM Identity Fabric
CIAM can be delivered as part of a holistic identity fabric, where individual functions are instantiated as separate services or microservices. Examples of microservices within an identity fabric include registration, identity proofing, discrete authentication mechanism support, consent collection, consent management, SSO, etc. Microservices are generally built in the cloud and delivered as SaaS or as a private cloud. These services can be agnostic about the use cases they serve, meaning that organizations that deploy identity fabrics can leverage their authentication services for enterprise/workforce users as well as Business-to-Business (B2B) customers, and consumers as end users. This leads to greater scalability, more efficient use of services, and helps to future-proof enterprises. Using the identity fabric model also reduces costs associated with CIAM and enterprise IAM. The modularity of the identity fabric approach allows deploying organizations to add and deprecate capabilities in response to changing business requirements more rapidly.
















































