1 Introduction
IAM (Identity & Access Management) remains at the core of enterprise IT infrastructures when it comes to protecting digital corporate assets. IAM, as the name states, is about managing identities and their access. This involves managing user accounts and their entitlements across the variety of systems and applications in use in organizations.
IAM environments are becoming increasingly complex for organizations to manage. New trends such as digital transformation are introducing new types of identities to manage, forcing organizations to evolve and adapt their digital infrastructure. Market observations show that delivery models and architectures are changing, service variety is increasing, enterprise landscapes are becoming more agile, IT is being centralized, and organizations are starting their own Zero Trust journeys. However, there is still a long way to go for organizations to adapt all the major areas of IAM to bolster their identity and security landscape. As observed in the graph below, just over one third of the organizations from the survey are equipped with all the major areas for a comprehensive IAM solution.
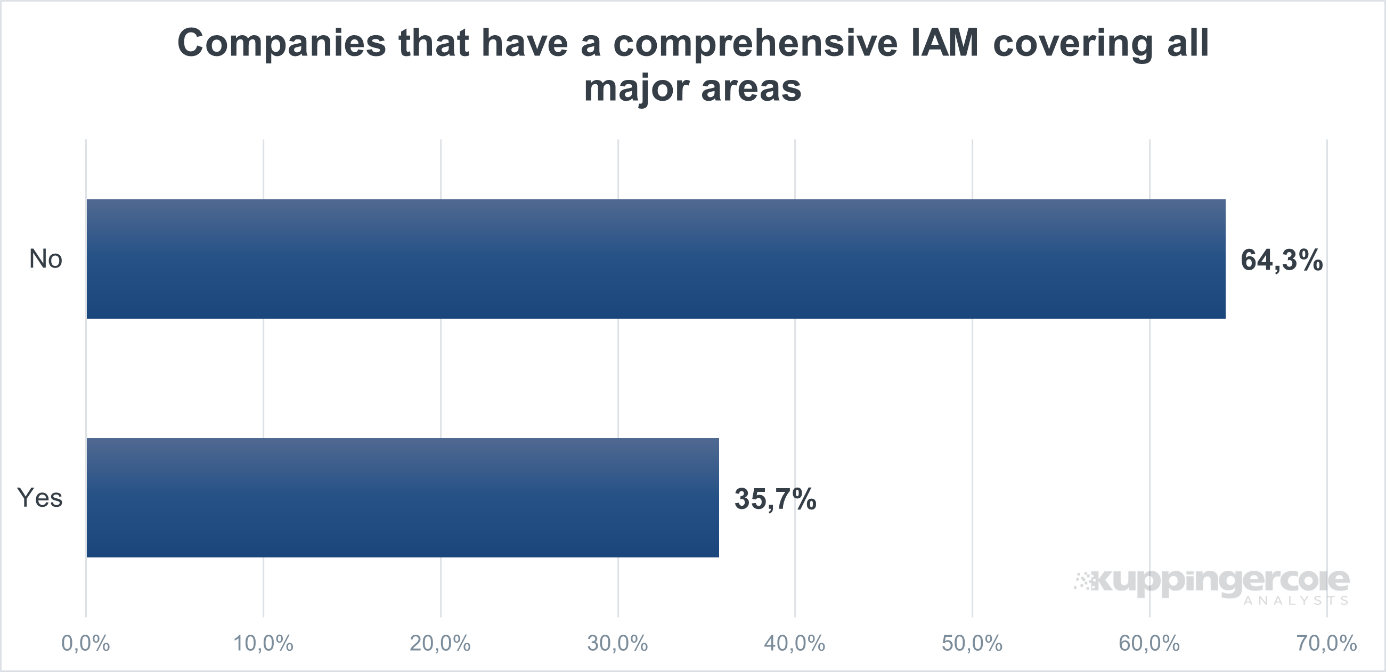
Figure 1: Companies having comprehensive IAM covering all major areas
New threats are posing a challenge to an organization’s security posture. The differentiating factor separating an internal network from the outer world does not have the same relevance it had before, with mobile users accessing internal systems, with integrating business partners and customers into business processes, and with the shift to cloud applications. The value and relevance of digital corporate assets and intellectual properties has increased. There has been a shift to connected things and towards smart manufacturing, with digital assets becoming “crown jewels” even among more traditional businesses, such as mechanical engineering. Protecting these digital assets along with the systems, and applications in an IT environment of growing complexity and of a hybrid nature while facing ever-increasing attacks, involves several actions by organizations. Protecting against internal and external threats requires a well-thought-out understanding of risks and countermeasures.
IAM can be found among the core elements of every IT infrastructure. IAM done right ensures that identities, their user accounts and passwords, and their access entitlements are well-managed. IAM thus reduces the attack surface by helping organizations move towards the “least privilege” principle. IAM provides the tools to automate processes around managing users and access entitlements, but also for regularly reviewing these and identifying excessive entitlements, for example.
IAM also plays a vital role for business enablement, when it comes to the need of employees, contractors, business partners, and customers to access certain applications, systems, and data. IAM is the tool for implementing the workflows and automated processes for onboarding users and granting them access. Again, if done right, IAM can enable organizations to optimize onboarding and changing processes, while also ensuring that entitlements are revoked, and accounts are deleted or deactivated once they are no longer required.
Under the umbrella of IAM, we can differentiate between the “core IAM” or– as it is called frequently today – IGA (Identity Governance and Administration), and the broader definition of IAM which includes additional capabilities such as Privilege Management, Web Access Management, Identity Federation, and more. IGA is a dual term for the two core elements of IAM, which are Identity Provisioning and Access Governance. Identity Provisioning supports automating processes for creating and managing user accounts and their high-level entitlements across a variety of systems and applications, while Access Governance adds a governance layer for analyzing entitlements, regular reviews, and recertification, as well as efficient access request workflows.
These core capabilities of Identity Provisioning and Access Governance frequently are available in combined products or in suites with a good level of integration between the various technical components. For the Access Governance part, it is essential for supporting the cooperation between business and IT. Business requests and approves the relevant access, which must be mapped to technical entitlements. Creating that interface well, from the definition to the ongoing management and reviews of entitlements, is challenging. Furthermore, tools must support requirements such as Segregation of Duties controls, and also have insight into high-risk combinations of entitlements.
Having an infrastructure for Identity Provisioning and Access Governance in place is the cornerstone for successfully managing identities, their accounts, and their entitlements across the heterogeneous and increasingly hybrid IT infrastructure of organizations. Enabling and protecting the Digital Transformation requires IGA.
One of the vendors in that space is Eviden (an Atos business). Eviden is one the largest European IT service providers and amongst the global top 5 players for digital services. As part of their portfolio, Eviden delivers various IAM services and products. Amongst these, there are the DirX products, including DirX Identity as an IGA offering.
















































