1 Introduction
As organizations continue their journey to the cloud, CISOs must provide secure, rapid access to IaaS, PaaS, SaaS and DaaS computing environments. While demanding it is essential in order to leverage the benefits of cloud infrastructure, rapid access requires reconsidering traditional approaches to cloud authentication and privilege management to access cloud-based resources.
The complexity of cloud architectures and design found in business today has spawned a cottage industry of self-help books to help IT leaders cope with mind stretching concepts, new forms of authentication, high velocity operational speeds and fast access demands of all types of identities. But the bottom line is that cloud-based computing continues to take over the world for one good reason – business likes it.
“Ultimately, the cloud is the latest example of Schumpeterian creative destruction: creating wealth for those who exploit it; and leading to the demise of those that don’t.”
Joe Weinman, Senior VP – Telx
Joe Weinman’s quote may be about 10 years old, but it remains highly relevant. Cloud environments have multiplied and vast amounts of the world’s economic activity depend on access to Infrastructure as a Service (IaaS) and Software as a Service (SaaS) installations. To service the demand for computing resources within organizations, many now rely on multi-cloud installations from competing IaaS and SaaS providers. Managing secure access to all this requires careful planning and buying decisions. According to Britive, enterprises now operate or have access to 210 cloud services on average. That number increases when one factors in the accounts individuals and departments create to use “personal” SaaS or operate IaaS for special projects.
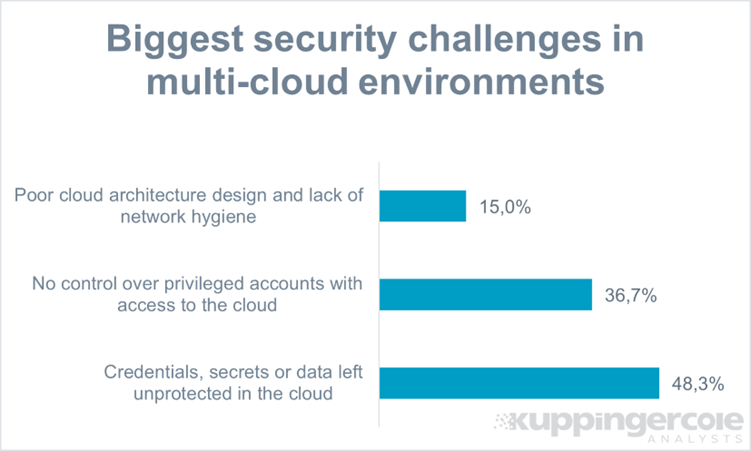
Figure 1: The biggest security challenges in multi-cloud environments (Source: KuppingerCole).
Despite the complexity, the design of cloud-based computing tends to allow progressively more dynamic and rapid access to resources than traditional on premises infrastructure. However, many Identity and Access Management (IAM) software platforms cannot take advantage of this dynamism, and few provide access to cloud resources on a Just-in-Time (JIT) or ephemeral basis. The fact that all major IaaS providers use proprietary IAM systems of their own adds to the complexity and challenges third party access management tools need to address so they can support different protocols from a single dashboard.
But as dynamic cloud architecture begins to dominate enterprise networks and operations, business leaders and IT vendors also start to understand that a different technical approach is necessary for their organizations to compete as fully digital enterprises.
















































