1 Introduction
Many successful cyberattacks involve the misuse of privileged accounts, enabled by inadequate Privileged Access Management (PAM) software, policies, or processes. Malicious activities that must be detected and controlled include abuse of shared privileged credentials, misuse of elevated privileges by unauthorized identities, the theft of privileged credentials by cybercriminals, and abuse of privileges on third-party systems accessed via the cloud. PAM is a critical part of the Identity & Access Management (IAM) lifecycle.
Privileged status has traditionally been given to a small set of administrators who needed access to perform maintenance and upgrade tasks, mostly on networks on-premises or local area networks (LAN). In some cases, senior employees may have also been given elevated access rights for specific tasks. It is fair to say that this is no longer the case. Privilege management use cases now extend across entire organizations, with users and machine identities requiring task-based access to data, services, and applications on legacy systems but also fast growing, multi-cloud-based infrastructures.
PAM has evolved into a wider cyber security and identity management discipline as digitalization has increased the attack surface to include cloud, multiple endpoints, home working, and no secure perimeters. It brings significant benefits to every major digital business initiative, including securing applications and data in the cloud, privileged user behaviour analytics to detect anomalous privileged behaviour and supporting endpoint threat protection.
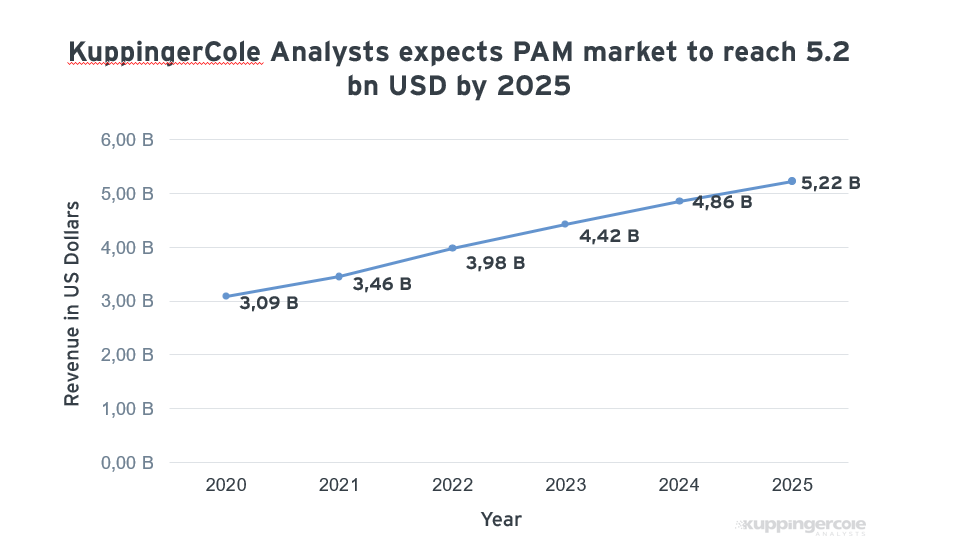
Figure 1: KuppingerCole expects to see further growth in the PAM market as software emerges to serve different types of business.
More recently, several PAM vendors have started to accommodate capabilities that support Cloud Infrastructure Entitlement Management (CIEM) for cloud-based resources, and critical cloud-based workflows such as DevOps and CI/CD projects. While there is overlap here, the demand for traditional PAM capabilities (password vaulting, credential management, full analytics, admin access, etc.) remains robust and vendor efforts to improve on those capabilities continue to drive competition.
Support for the demands of digital organizations is becoming a competitive differentiator in the PAM market. Interest in Least Privilege and Zero Trust informed architectures and policies has also grown as organizations look to secure multi-cloud environments. Buyers are increasingly aware that a well-configured and modern PAM platform can be an integral part of a Zero Trust architecture.
The PAM market continues to mature and grow (see Figure 1) with larger PAM vendors providing a full-service platform while newer entrants to the market are offering niche platforms for customers with more specialized PAM requirements. The trade-off is that full-service platforms are often more complicated to deploy and manage but the simpler niche products do not offer the same level of capabilities -so far. Buyers need to undertake due diligence before deciding on which platform is right for their business with one eye on future requirements. Some vendors, such as Devolutions featured here, offer a choice of modules that offer certain capabilities individually and full interoperability between modules for more comprehensive PAM feature sets.
















































