1 Introduction
“Identity Security” has established itself as a term. It stands for approaches that understand “identity” as a major element of cybersecurity initiatives. “Identity” is about the digital identities, their lifecycle and authentication, but also the access they have and the authorization of access. When analyzing known cyber-attacks, attackers commonly try to gain access to highly privileged accounts, which give them access to sensitive information or further systems in the attack chain.
Research by KuppingerCole Analysts on one hand indicates that there is a wide range of attacks organizations are concerned of. However, most of these attacks are fully or partially related to digital identities and their access. Be it advanced attacks on critical infrastructures as a type of targeted, persistent attacks, be it malicious insiders, be it software supply chain attacks: All these attacks rely on attackers gaining access to privileged identities and, through these, gaining access to critical resources.
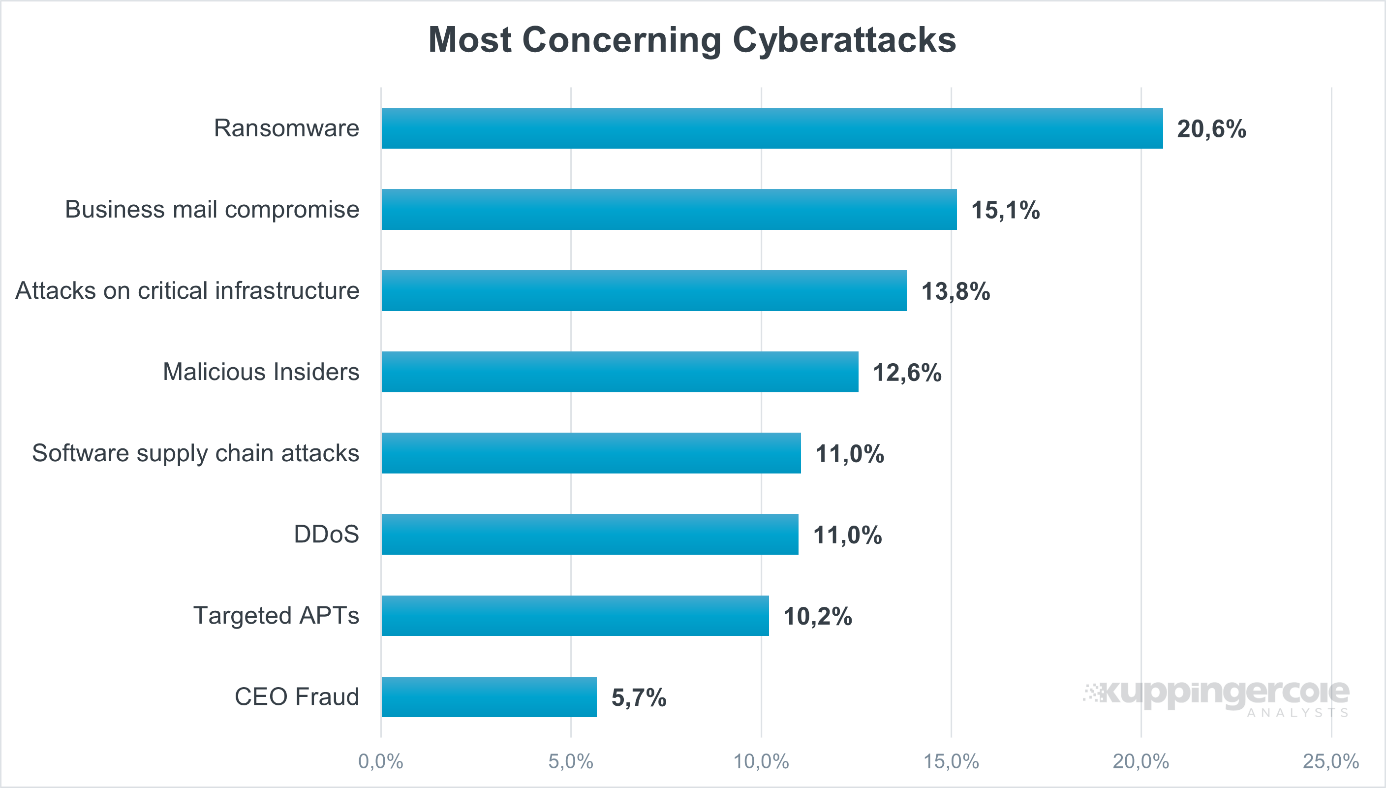
Figure 1: Most of the critical types of cyberattacks are related to digital identities.
Identity-related threats thus are a major challenge for organizations. They require adequate responses. Unfortunately, the common approaches within IAM are primarily targeting on only a few aspects:
- Managing the lifecycle of users, their accounts in target systems and applications, and their entitlements.
- Reviewing the (static) entitlements in recertification processes.
- Mitigating risk during authentication by strong, multi-factor authentication, including analyzing the context risk.
- Specific measures for restricting and securing privileged access.
Granting, managing, and reviewing access entitlements is still mostly done via complex, manual processes, based on roles. These lead to a high degree in complexity. Combined with the fact that role models tend to be complex, but also many critical systems come with their own complex, multi-layer entitlement models, it is hard to keep control about who is entitled for what.
Furthermore, looking at static entitlements, it is just the tip of the iceberg when it comes to Identity Security. Way more relevant is the analysis of outliers in the behavior of users, based on information about how these are using the entitlements. Additionally, with more and more dynamic workloads and non-human (“silicon”) accounts being used, static approaches are no longer sufficient for controlling access to critical resources.
New approaches for managing such workloads are one part of the solution. The other are solutions for ITDR (Identity Threat Detection & Response) that enable organizations to detect threats by human and silicon identities, by gathering information about static entitlements as well as the concrete access to systems, applications, and services, and based on that, identifying anomalies. Based on AI/ML (Artificial Intelligence/Machine Learning), such approaches help in identifying critical threats related to identities and their access.
The ITDR solution by Sharelock provides such specialized approach that can be added to the existing IAM infrastructure and deliver the insight needed to identify and respond to identity-related threats.
















































