1 Introduction
Over the course of the past few years, the threat of cyberattacks has been on a constant rise. There are no signs that this will change in the foreseeable future. Organizations must defend themselves against such attacks, which is a challenge for several reasons. Among these reasons are a dynamic, ever-increasing attack surface, but also the fact that attacks remain unknown for a certain period, until someone detects them. On the other hand, the need for exchanging information constantly increases in the hyperconnected business world we face in the age of Digital Transformation. New and better solutions for cyber-defense are a must nowadays.
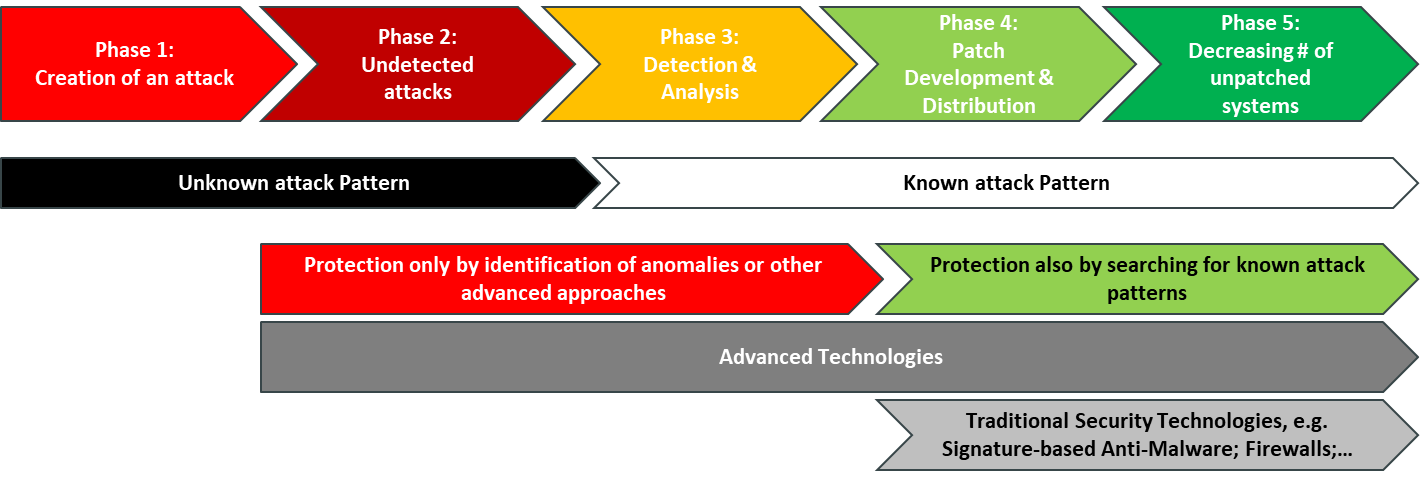
When we look at the phases of attacks, there is a period where these attacks are unknown, and it takes additional time to protect against attacks once they are identified. The most critical phase is what is indicated as phase 2 in figure 1, the time where attacks are run but haven’t been identified. This period can be very short, e.g. in the case of many ransomware attacks that become immediately visible, but also can run for years. But even in phase 3, after identification, it takes from a couple of hours to days or even longer until effective protection by traditional approaches is available, during which time other less skilled attackers can create new attacks exploiting the same vulnerabilities.
In other words: Traditional security technologies such as signature-based Anti-Malware that protect against the “known” can only be one element in a protection strategy, as they are not sufficient anymore. The need is for additional security technologies that go beyond detection and protect against so called “zero-day attacks”, which are attacks using a yet not known attack pattern.
The second reason why organizations must act is the ever-growing attack surface. This dynamic attack surface is due to the rise of the IoT, the increase in communication, the distributed and hybrid IT infrastructures using cloud services, and so on.
Factually, exchanging information with business partners, customers, and consumers is at the core of the Digital Transformation. Organizations must be able to share information and receive information, without being constantly exposed to threats. Establishing a track record for guaranteeing its customers, business partners, and users access to clean, secure business content is essential in the age of ever-increasing cyber-attacks. Providing secure data is about removing barriers for successful collaboration.
When we look at approaches for protecting against the unknown, we observe several ways to support organizations. There is the emerging field of “Cognitive Security”, where AI (Artificial Intelligence) and other advanced technologies are applied to, e.g., identify anomalies. On the other hand, we observe a growing number of approaches for isolation, which provide a separate environment for dangerous activities such as web browsing. Other technologies – marketed as Content Disarm and Reconstruct – try to analyze content and strip everything that could be part of an attack vector. These approaches are not contradictory but compatible elements of an IT security infrastructure that is better suited to protect against the unknown. Organizations need to look at these new techniques and enhance their traditional IT infrastructure for mitigating the risk imposed by cyber-attackers.
Content Threat Removal as a rather new approach goes one step further. It focuses on analyzing content to find the useful business content, discarding everything else, and then building new data to carry the information safely to its destination. By doing this, everything that could be malicious is simply left behind.
Securing content by transformation is not a simple challenge, given that attacks can be woven deep into content, such as macros that are required to work with office documents. However, we see vendors appearing on the market that deliver on that promise. Even while there remains some trade-off, the potential increase in security makes it worth evaluating such tools and adding them to the IT security infrastructure.
Deep Secure is a UK-based cybersecurity software provider, delivering its products to a variety of sectors including leading defense and intelligence agencies. The company was founded back in 2009 and currently employs over 50 staff. Since its establishment in 2009, Deep Secure started catering to customers in UK. Over the past years, Deep Secure has started international expansion, now also serving customers in Europe, the US, Middle East, and the APAC region. Deep Secure provides a sophisticated solution for Content Threat Removal, which protects a variety of content such as PDF files, image formats, and others.
















































