1 Introduction
Identity & Access Management has come a long way since the inception of directory services and it is still activity evolving.
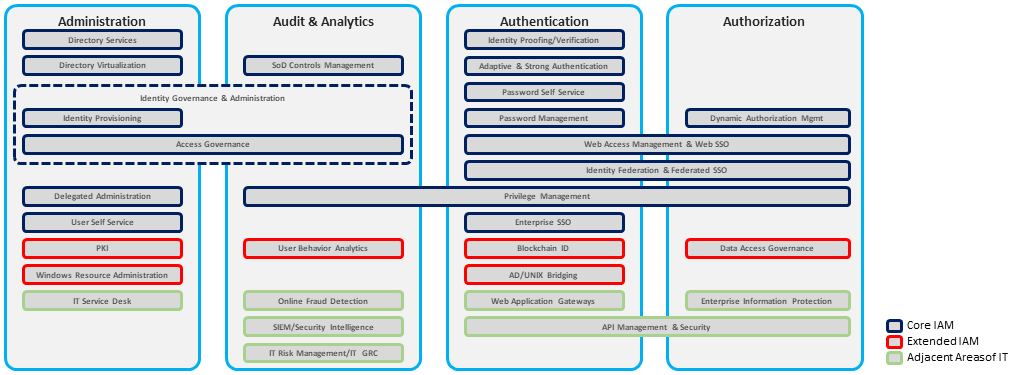
KuppingerCole’s view of IAM over time begins with an IAM in whose primary purpose was to prevent unauthorized access to secure resource. With its focus on access administration, the IAM core technology started to include Identity Provisioning as well as the core capabilities to authenticate, authorize and audit.
A further generation of IAM not only tried to prevent unauthorized access to a resource, but it also added the capability to detect it. Access Governance was included as a core technology for IAM with a focus on administration with business participation, and the ability to detect was partially due to integrations with Security Information and Event Management (SIEM) products making its way onto the stage.
In this latest iteration, IAM adds to its ability to prevent and detect by also providing the ability to respond to the security threats. New IAM technologies included Access Analytics and Intelligence. Analytics gives the ability to perform data analysis of historical data and uncover trends or pattern that can be used to improve the decision-making process, while Intelligence gives the ability to make access decisions that can be acted upon based on the patterns and trends found through data analytics. Together, access analytics and intelligence provide the ability not only detect, but to also respond to unauthorized access attempts. These new capabilities helped to fulfill the requirements of not only business but governance, compliance, and administration too. Integrations with Adaptive Authentication & Authorization, Real-Time Security Intelligence, Software Defined Environments and Privilege Management also needed to be supported by IAM today.
As the landscape of information security threats changes, so do the IAM capability requirements.
Founded in 2000, Evidian is the Identity and Access Management (IAM) software suite of Atos Group. Atos Evidian has more than 900 customers with over 5 million users within the Finances Services, Manufacturing, Retail, Transport, Telecom, Media, Utilities, and Public Health sectors.
















































