1 Introduction / Executive Summary
Fraud is a major cost to businesses worldwide and this has been exacerbated by the worldwide Covid pandemic. Banking, finance, payment services, and retail are some of the most frequent targets of fraudsters. However, insurance, gaming, telecommunications, health care, cryptocurrency exchanges, government assistance agencies, travel and hospitality, and real estate are increasingly targeted as cybercriminals have realized that most online services trade in monetary equivalents. After years of being the focus of cybercriminals, banking and financial institutions are more likely to be better secured than other industries, meaning that fraudsters are increasingly likely to attack any potentially lucrative target if given the opportunity. Fraud perpetrators are continually diversifying and innovating their Tactics, Techniques, and Procedures (TTPs).
The most prevalent types of fraud businesses, non-profit organizations, and government agencies experience today are:
- Account Takeover (ATO) Fraud - occurs when fraudsters use breached passwords and credential stuffing attacks to execute unauthorized transactions. Additional means for account takeover fraud are malware attacks (man in the middle and man in the browser) as well as the use of Remote Access Tools via Trojan or social engineering scams.
- Account Opening (AO) Fraud – also called New Account Fraud or Synthetic Fraud, often happens as a result of using stolen identities or assemblages of personal information to create synthetic digital IDs. Such fraudulently created accounts can be more difficult to detect, which is an advantage for the attackers. This type involves gathering complete sets of or bits of PII (Personally Identifiable Information) on legitimate persons to construct illegitimate accounts. Educational, financial, government, employment, and medical records and social media can be sources of PII used for assembling fake accounts, which are then often used to abuse promotions and instant loans and/or used as mule accounts to move money around. Various financial regulations require validation of users at registration time for Anti-Money Laundering (AML), Know Your Customer (KYC), US Office of Foreign Asset Control (OFAC), Politically Exposed Persons (PEP) validation, and other sanctions screening.
Many other types of online fraud exist and they continue to proliferate and evolve. Examples are listed below based on categories:
Phishing/Smishing/Vishing threats, many of which can be perpetrated by bots:
- Shopping scams
- Caller ID spoofing detection (app-based)
- Fake investment opportunities (crypto, gold, real estate, etc.)
- Fake push notifications
- Fake delivery notices
- Fake utility, telco, broadband cutoff notices
- Fake invoices
- Malicious invoice payment redirection
- CEO/CFO email impersonation for sending fraudulent payments
- Financial institution impersonation misdirecting customers to transfer funds for safety
- Fake Drivers’ License offers
- Fake government welfare signup and collection notices
- Fake tax refund notices
- Fake student loan offers
- Fake notices from utilities, medical providers, pharmacies
- Fake tech support scams
- Fake “questionable charge” scams impersonating credit card companies or merchants
- Travel deal scams
- Travel refund scams
- Vacation rental scams
- Event ticket scams
- Fake vaccine cards (and scams)
- Lottery/inheritance/customs advance fee scams
- Realtor/mortgage email impersonation for escrow payment redirection
- SMS OTP harvesting
- Romance site scams
- Dox bots
Issuer issues:
- Card-Not-Present (CNP)
- Counterfeit (Skimmed or cloned)
- Stolen cards
Website operator issues, most of which are caused by bots:
- Malicious credential/payment skimmer code
- Inventory hoarding / Grinch bots
- Jingle bots (add to cart and abandon)
- API inventory checking bots
- Competitive price checking bots
- Headless browsers
- DDoS
- Fake reviews and comments
- Malicious link and ad insertion bots (comments, reviews, forums, etc.)
- Social media bots
- Ad Fraud/Click bots
- Account creation bots
- Credential stuffing bots
- File downloading bots
- Event ticket purchase and scalping bots
- Gift card cracking
- Malicious “overlay” apps
- SEO poisoning
- SIM swap (SMS OTP redirect)
- Email address harvest for spam bots
- Fake job postings
- Fake goods on auction sites
- Fake car, truck, and RV listings
Cryptocurrency
- Fake ICOs
- Fake coins
- Fake wallet aggregators
- Fake exchanges
- Cryptocurrency address / clipboard hijacking malware
The chief mitigation strategies against these types of fraud employ real-time risk analytics and decisioning. Risk-based Multi-Factor Authentication (MFA) can eliminate a substantial portion of ATOs by increasing authentication assurance levels. Risk-based MFA often evaluates credential intelligence, device intelligence, user behavioral analytics, and behavioral/passive biometrics. To decrease NAF/AO/Synthetic Fraud, increasing identity assurance at registration and authentication time with identity vetting services are recommended. Bot detection and management can also be helpful at cutting other types of fraud.
Risk-based MFA and transaction processing solutions operate optimally when integrated with or informed by Fraud Reduction Intelligence Platforms (FRIPs). FRIPs provide to risk-based MFA and transaction processing systems the information needed to make more accurate decisions on whether or not transactions should execute. FRIP solutions generally provide up to six major functions:
- Identity proofing
- Credential intelligence
- Device intelligence
- User behavioral analysis
- Behavioral/passive biometrics
- Bot detection & management
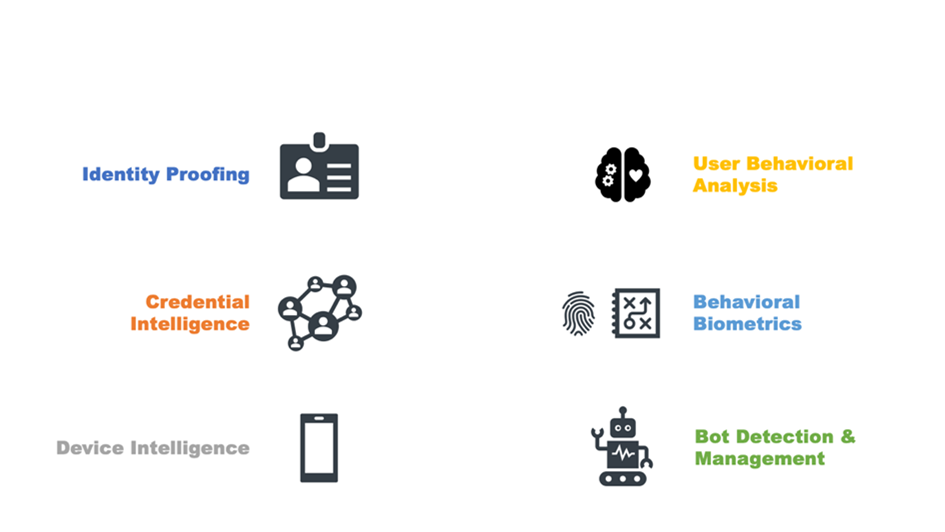
Figure 1: The Six Major Fraud Reduction Techniques
1.1 Highlights
- Fraudsters continue to innovate, deriving additional techniques from existing ones and developing new methods delivered across all channels.
- Vendor solutions exhibit an increased emphasis on providing identity proofing services, either within their platforms or through OEM or technical partnerships.
- Call center integration, while not common across all FRIP vendors yet, is a growth area given the multi-pronged nature of fraud attacks. Vendors offering call center integration report that it is highly sought after by customers compared to just a few years ago.
- More FRIP vendors are using internal and third-party sources of compromised credential intelligence to prevent ATOs.
- Device intelligence is a mature capability utilized by most solutions; in some cases, FRIP service providers are members of the intelligence supply chain of other vendors.
- Bot detection and management have become more central to deterring many types of fraud attempts, since many forms of fraud are automated by bots. Vendors are improving their abilities to detect, classify, and provide options for handling bots.
- The Overall Leaders in Fraud Reduction Intelligence Platforms are Akamai, BioCatch, Experian, F5, Forter, GBG, Group-IB, HID Global, IBM, LexisNexis Risk Solutions, Outseer, and Transmit Security.
- The Product Leaders in Fraud Reduction Intelligence Platforms are Arkose Labs, BioCatch, Experian, F5, Forter, Group-IB, HID Global, IBM, ID Dataweb, LexisNexis Risk Solutions, Outseer, and Transmit Security.
- The Innovation Leaders in Fraud Reduction Intelligence Platforms are BioCatch, Experian, F5, Group-IB, HID Global, Human Security, IBM, ID Dataweb, LexisNexis Risk Solutions, and Transmit Security.
- The Market Leaders in Fraud Reduction Intelligence Platforms are Akamai, Broadcom, Experian, F5, Forter, GBG, HID Global, Human Security, IBM, LexisNexis Risk Solutions, Outseer, and Sift.
















































