Commissioned by Oracle
1 Introduction / Executive Summary
Ransomware is an evolving global threat that can wreak havoc on businesses, governments, and citizens with billions of dollars in damages. More than half of organizations have been affected, and often, the consequences are immeasurable, which is why it is critical to put in place the safeguards to help prevent a successful attack, minimize negative outcomes, and strengthen operational resiliency in the face of a breach.
Dealing with the aftermath of a ransomware attack can be complicated and costly. Most organizations experience significant business impacts, from financial loss to business disruption. According to the Internet Crime Complaint Center IC3, a division of the FBI, between 50% and 80% of organizations that have paid ransom demands in the past were subject to subsequent attacks, often by the same threat actors1.
Ransomware is unique among cybercrime because in order for the attack to be successful, it requires the victim to become a willing accomplice after the fact.
― James Scott, Institute for Critical Infrastructure Technology
Most security experts recommend against paying the ransom: not only is there no guarantee to get the data back, but it also encourages future ransomware attacks. Studies conducted both in the United States (by Coveware2) and Europe (by Veeam3) show that many victims never hear back from their attackers after paying the ransom, and even among those who do get their data back, over 30% find it incomplete or damaged.
In this paper, we will expand our view of ransomware and demonstrate how treating it as an isolated security challenge is not a sustainable approach. We will show why prevention is the best foundation for managing risk and consider some strategies to combat common ransomware tactics. A breach affects every part of the enterprise because it is not an isolated cybersecurity problem; it is an everyone’s problem.
We will discuss cybersecurity guidelines along with some recommended best practices. And we will look at key focus areas to start implementing these strategies to help reduce the risk of ransomware. As we explore Oracle’s layered approach to security with an emphasis on automation and building security into their products, we will find that defending against ransomware means defending against any cyberattack.
2 Key Findings
- Ransomware has become a highly lucrative business for cybercriminals, providing high rewards and low risk with minimal investment. Contrary to a popular belief, ransomware attacks are usually not creations of elite hacker groups or state-sponsored actors: even novice cybercriminals can launch a successful attack with minimal resources.
- Even though the criminal actors behind ransomware attacks are clearly driven by profit, the extent of the damage caused by their activities can reach tens of billions, far greater than any potential profits from the ransom collection.
- Many organizations still see ransomware as an isolated problem in its own field of cybersecurity, which requires special tools and technologies to protect against. This is not true. Ransomware does not exist in a vacuum—a malicious payload can be delivered using a multitude of attack vectors exploiting vulnerabilities in various environments.
- Either through negligence or with malicious intent, users have been the cause of many large-scale data breaches and ransomware attacks. Preventing users from making costly mistakes should be a major line of defense against those.
- Disruption of access to critical business data causes the biggest problems for organizations, even though recovery time is usually spent restoring various kinds of infrastructure. Data-centric security offers an alternative approach toward protecting your crown jewels – instead of trying to protect every kind of infrastructure with separate efforts and tools, organizations should focus on protecting data itself.
- Oracle offers a broad range of capabilities that can help reduce the risk of disruption or loss from a breach and help enable you to implement best practices outlined by organizations such as the National Institute of Standards and Technology.
3 Understanding Ransomware
Ransomware is a type of malicious software (malware) designed to disrupt the victim’s access to their data or systems with the intent to extort a payment from the victim. Let’s look at how it has evolved, the cost of a breach, and dealing with an attack.
Early strains of ransomware were simple lockers that restricted access to infected computers until the ransom was paid, but today, many leverage cryptoviral extortion tactics that have more severe consequences. And ransom demands are on the rise with the explosive growth of cryptocurrencies such as Bitcoin. The pseudonymity behind cryptocurrency transactions makes it even more difficult to track and find the perpetrators. With relatively minimal investment, seemingly little risk, and proven high reward, it is no wonder ransomware incidents continue to grow in both size and frequency. According to SonicWall4, in 2021 alone the frequency of ransomware attacks has doubled, with another record set by the largest ransomware payout made for $40 million5.
3.1 An evolving threat
Previously, cybercriminals focused on encrypting an organization’s systems and data to make them unavailable, but lately, they’ve added a twist—extortion. Cybercriminals exfiltrate system data with the threat of publication or sale and can escalate to double extortion by threatening to supply insider information based on exfiltrated data.
Next, attackers started to target system backups so they could not be recovered. Attackers are playing a long game by using compromised system credentials to alter data so that if recovered, it would be inaccurate, and the victim would not know what or when changes were made.
Each variation of ransomware surfaced in response to mitigation and remediation measures. Previously, businesses focused on endpoint protection products to manage malware, but as extortion became a more popular method of ransomware, businesses improved their backup processes and technologies so they could restore systems quickly to resume normal operations. However, given the evolution of ransomware tactics, this was no longer sufficient to combat double extortion threats or issues with altered data.
With many organizations moving to mobile devices and cloud environments, new challenges have surfaced. Ransomware has not only become easier to deliver, but it is no longer just about protecting your own network security; it can just as easily come through one of your software suppliers with a single vulnerability in their code. And if history is any indication, we can expect the risk of ransomware and the tactics used to continue evolving.
3.2 The cost of ransomware
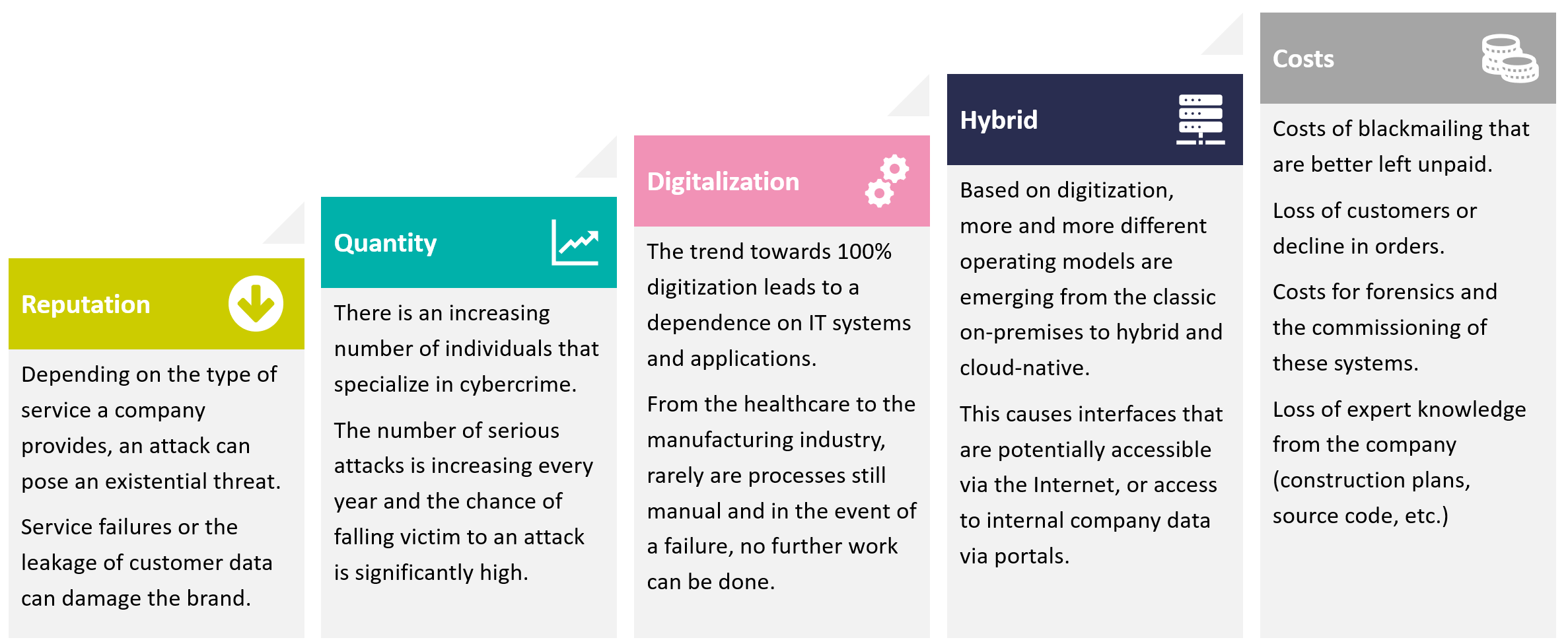
As modern enterprise IT infrastructures no longer resemble the traditional castle-and-moat architectures with clearly defined security perimeters, the complexity of protecting an organization has increased, and the damage reverberates beyond our own boundaries. The potential damage is often far beyond what meets the eye. What is apparent is the financial impact of the disruption of critical business operations, costs associated with incident response and mitigation efforts, lost productivity, and of course, the ransom payment itself, should the victim choose to pay, to name a few.
However, there are longer-term impacts that include diminished business revenue, damage to brand reputation, loss of key executives and workforce reduction, loss of customers and strategic partnerships, and even in some circumstances, the viability of the business altogether.
After an attack, organizations invest in security measures to prevent a repeat attack, often focusing on the type of breach they experienced. This includes implementing a security operations center, introducing security awareness training for their users, deploying endpoint protection, data backup and recovery, and email scanning – needless to say, having these measures in place before being targeted would have prevented the attack in the first place.
And though many organizations have relied on cyber insurance for indemnification, it does not always guarantee their ability to recoup losses associated with a breach. Today, cyber insurers are dramatically raising their requirements for indemnification with higher levels of mitigation controls. With repeat attacks being common, insurance companies have learned that it takes cybersecurity investment to not only recover from an attack but to prevent a future incident, resulting in cyber insurers being much more diligent and discriminating against insured entities.
3.3 Dealing with a ransomware attack
Preparation and proactive protection are key areas of ransomware resilience and the primary focus of this paper, however, once you’ve been attacked, you must focus on your remediation plan to limit the further propagation of a malicious payload. The most time-critical measures include:
- Isolating the infected systems and removing them from all networks.
- Addressing all file-sharing vulnerabilities in a timely fashion and taking any unsupported operating systems offline.
- Reviewing the chain of trust between IT systems to prevent the cascading effect of a malware outbreak.
- Segregating networks and databases to help isolate malware outbreaks and limit the operational impact of a compromise.
An incident response plan should be prepared in advance and reviewed regularly to account for any changes across the IT infrastructure and new developments with external threats. This plan clearly defines organizational, technical, legal, and other responsibilities for all persons involved in response to a breach.
Next, proactive hardening of your corporate IT systems and other resilience measures are vital in preventing a successive breach. While most of these tools are already in place, you will need to adjust their scopes and ensure that they are all operated in accord, and governed by centrally established security, compliance, and access policies.
4 Addressing common ransomware tactics
US government agencies have developed a framework and best practice controls to guide organizations with ransomware mitigation and recovery. Let’s look at how these best practice controls apply to data exfiltration, blocked availability, targeted backups, and altered data.
The NIST Cybersecurity Framework Profile for Ransomware Risk Management has five functions, each critical in developing a layered security approach. For example, if protection controls are circumvented then ideally detection mechanisms will identify the breach so it may be contained before spreading to other systems and environments.
Hardware is easy to protect: lock it in a room, chain it to a desk, or buy a spare. Information poses more of a problem. It can exist in more than one place; be transported halfway across the planet in seconds; and be stolen without your knowledge.
― Bruce Schneier
4.1 Data exfiltration
Most organizations have relied on disk encryption to provide encryption for data stored on these devices. The benefit of storage encryption is that it provides encryption at the storage level for any structured and unstructured asset, which makes it easy to manage, but also easy to subvert. Compromised credentials are one of the most common methods to infiltrate systems, which is why a Zero Trust architecture and multifactor authentication should be utilized. If assets are encrypted regardless of the storage device it resides on, then the control is sustainable.
For example, if a PDF document is stored on an encrypted device, anyone with access can remove the document. However, if the originator encrypted the document and created a key that would provide decryption, then the encryption control would have been sustainable even if the document no longer resides on the encrypted device. This sustainable control is requisite in mitigating the threat from data exfiltration.
If a threat actor exfiltrated assets from an encrypted device, they would not be able to access the data contained within these assets without the encryption key. It is equally important that the encryption key not be stored persistently on the same device as the asset. This segmentation helps to mitigate the risk of both being compromised and stop threat actors from using any exfiltrated data.
4.2 Availability
Threat actors seek out critical systems for an organization and block access by encrypting an organization’s systems and data. To increase the likelihood of receiving a ransom payment, attackers may seek an opportunity to block availability during a critical time with the highest impact. Some may even seek systems that provide safety capabilities for critical organizations, which could have effects greater than monetary damages alone.
This attack tactic is more complex to resolve than data exfiltration. There are two primary methods to recover from such a tactic. The first is to pay the ransom, get the encryption key, and then, ideally, the systems are operational again. The second method is to recover the systems with your backups. This is done with some level of uncertainty, as attackers may have tampered with the hardware and operating systems, in which case some may then choose to recover with newly purchased hardware.
But each of these decisions can mean added downtime, and for some critical systems, it may not be an option. Several best practices can help reduce the amount of downtime, such as leveraging highly available instances in a separately segmented network in the cloud or optimizing segmentation and different security controls across all environments, which reduces the probability of a compromised instance.
4.3 Backups Targeted
Another common tactic we see is attackers targeting an organization’s backups. With corrupt backups, an organization is cornered into paying the ransom since they cannot run recovery from trusted backups. There are several methods to accomplish this; attackers can delete backups or change settings for how long backups should be retained.
In this case, it is recommended that your security strategy considers the following aspects:
- Sub-second Recovery Point Objective (RPO).
- Ensure that the backups are protected and locked, even from administrator credentials
- Real-time tamper detection of transactions.
- Protecting the backup catalog from changes by the production administrator.
- If backups become non-recoverable for any reason, a high-priority alert must be raised immediately.
4.4 Altered data
Organizations started to implement controls to mitigate data exfiltration and optimize their recovery processes. In response, some attackers focused on the ability to alter data within a system. Already adept at compromising credentials, they began to target privileged credentials. Privileged credentials, such as that of a database administrator, can potentially provide unlimited abilities to alter data without detection. Organizations must find the balance between security controls and operational performance, which is often inversely related.
It is not surprising that some have hesitated in enabling heavy auditing of data within a database. Even if auditing is enabled for privileged accounts, the attacker could potentially disable the auditing to make changes and enable it again once it is completed. And since this type of attack is performed at the database layer, the application auditing will not record or detect the changes. For example, an attacker can change data elements like bank routing and account information so that they will receive payments instead of the intended supplier. To add complexity, if sensitive data is altered, decisions may be made upon false assumptions leading to negative outcomes.
Privileged accounts are necessary for applying patches and performing maintenance for the database. In addition, many third-party solutions may be using privileged accounts for these databases to collect data needed to fulfill their objectives, as was observed with the Solar Winds incident. Some recommended best practices to prevent altered data through compromised privileged accounts are:
- Strong authentication mechanisms to supplement multifactor authentication, such as certificates or biometric data as well as attribute-driven authentication like time of day, IP address, etc.
- Applying least privilege and a zero-trust approach for privileged credentials and access ensuring they only have granted permissions necessary for performing their job function. And if a job function requires the ability to alter data, ensure that this credential does not also have the ability to disable auditing.
- Centrally managing and monitoring these accounts to ensure that deprovisioning is performed in a timely manner.
- Segmenting the audit records for privileged users’ activities into a separate repository and environment that the privileged user does not have access to and cannot alter.
5 Preventive strategies for risk reduction
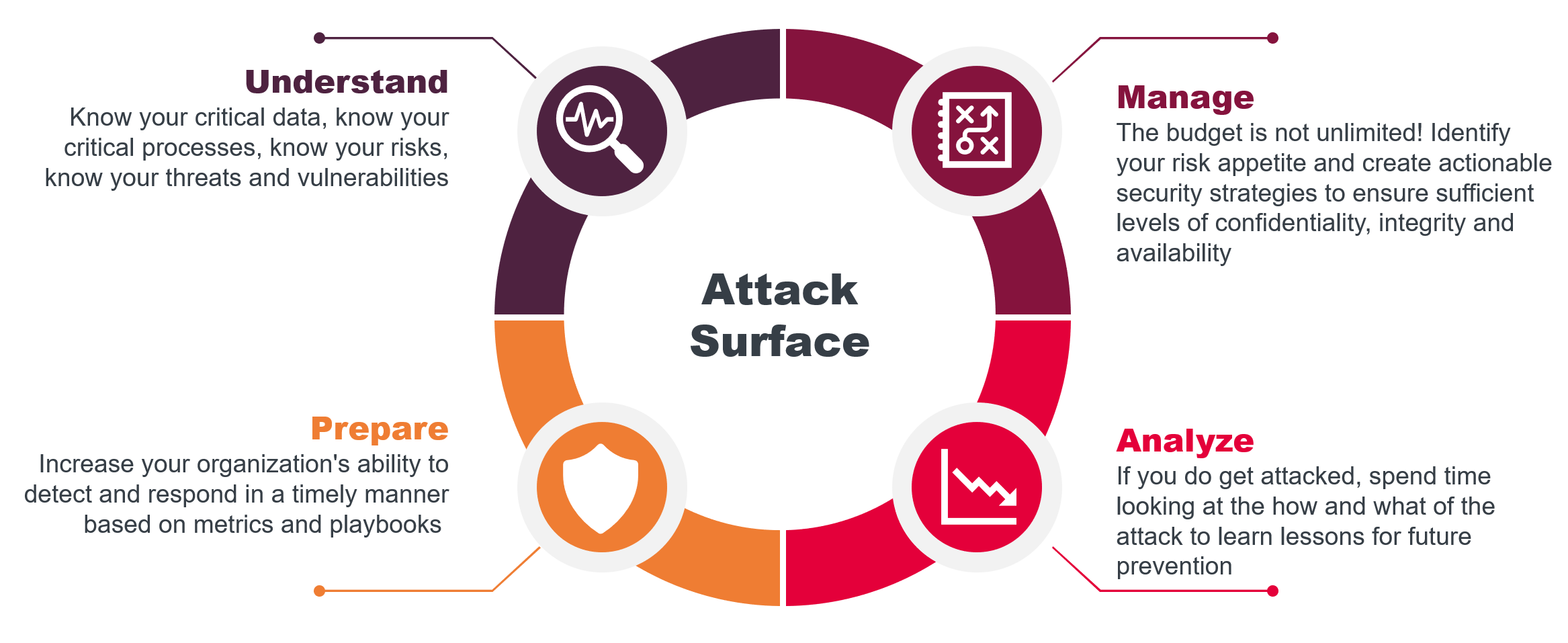
When it comes to dealing with ransomware attacks, we find ourselves in a paradoxical position. The awareness of its dangers is extremely high, most organizations are ready to invest resources to stay protected against it, and yet, ransomware attacks continue to cause massive damage even to the largest and smartest companies. What are we doing wrong?
It may seem obvious to have basic security tools set up, yet we hear of ransomware incidents where it was preventable had the organization completed updates and patching on time, or it was due to a lack of strong MFA in the face of stolen credentials. it is worthwhile to review some basic preventative measures and focus areas such as network segmentation, zero trust, and data protection and how each of these approaches can help keep your organization safe.
5.1 Basic preventive measures
As previously mentioned, traditional methods tend to focus on endpoint protection, but it has its limitations. A tried-and-true preventive measure that is vital to any security strategy is a well-established vulnerability management and patching plan. Recently, several incidents, such as those caused by the security hole in the Log4j logging framework, prove that regardless of how strong your internal security posture is, your organization could still be hacked via your supply chain.
One vulnerability in a third-party software tool or even a bug in an open-source library could lead to a breach. Some of the biggest ransomware attacks, such as NotPetya, could have been prevented, had organizations deployed security patches in time. Additionally, proper backup solutions with multiple copies, offsite backup locations, and regular testing decrease the downtime from the recovery phase of an attack.
Still, arguably the weakest component in every security architecture is the human factor. Whether through negligence or with malicious intent, users have been the point of entry for many attacks, which is why it is crucial to educate and train users on security best practices. Technical safeguards can and should be put into place as well: for example, email security solutions that can not only detect ransomware, but also other types of potential compromise—spam, phishing, and social engineering attacks. It is important that their protection applies retroactively, for example, by automatically scanning delivered emails and removing malicious ones from mailboxes.
5.2 Zero Trust Access
Implementing network segmentation with a Zero Trust architecture is a critical measure that helps prevent or limit the spread of ransomware and minimize its impact. As a concept, Zero Trust prescribes several basic requirements such as ensuring that every access attempt from a specific user to a specific resource is strongly authenticated, encrypted, and continuously monitored for behavior anomalies. More importantly, it establishes that every access is governed by the principles of “least privilege” and “segregation of duties”.
Combined with a dynamic policy engine that makes every access decision in real-time, fed by signals from endpoint security, network detection, or cloud security posture management tools, it helps ensure, among other things, that no cybercriminals can access or compromise your systems and data. Although there is no single out-of-the-box solution for implementing a Zero Trust architecture, a vendor (such as a cloud service provider) can offer the tools and services to align the various capabilities needed with centrally managed policies to help organizations advance toward building a strong Zero Trust architecture.
5.3 Data protection
A data-centric security approach sounds deceptively simple, but it is a little more complicated. Data does not exist in a vacuum. Data at rest generates no value. To power any business process, data is constantly created and transformed, moving between systems and environments. To ensure its consistent availability, integrity, and confidentiality, an organization must not just have policies in place, that govern access to this data on premises, in the cloud, and anywhere in between, but it must also have the necessary tools and controls to enforce these policies throughout the whole lifecycle of the data.
On the organizational side, communication is key, and involves regularly educating users as well as informing executives on risks and mitigation plans. To gain executive buy-in for possible capital investments for security, begin by making the board aware of the risks of ransomware. Identify how it would impact your operations and business.
― John Tolbert, KuppingerCole Analysts AG
Most IT specialists see the cloud as a more secure alternative to their existing on-premises infrastructure. This can be especially true for smaller companies with limited IT security staff, as all cloud service providers invest heavily in the security and compliance of their infrastructure and offer their customers a large portfolio of security solutions and services. Since customers no longer have visibility or control over the operations of a cloud service provider, they must trust their provider in defending their data.
6 NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) provides guidance with a standards-based risk management approach that delivers a framework for effective security controls.
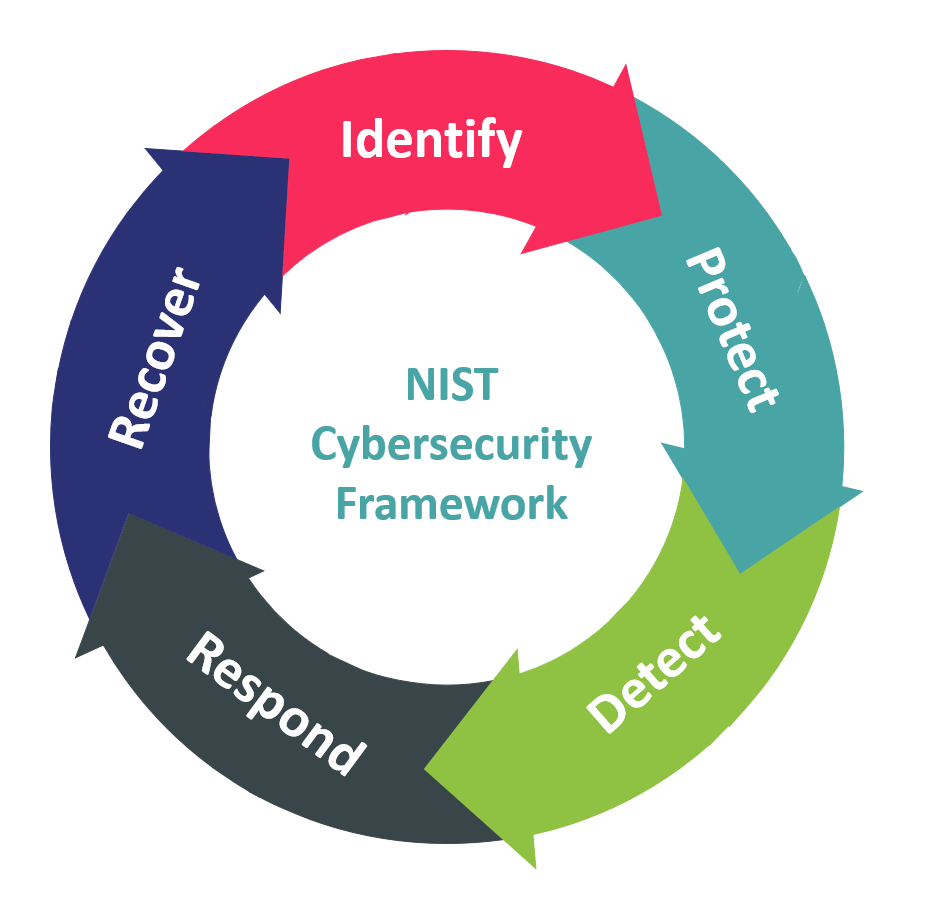
Implementing the NIST cybersecurity framework can be challenging, but it could be critical to protecting your organization. A key aspect of the framework is that it bases guidance on outcomes while helping organizations stay compliant with the latest regulations.
Additionally, the framework supports communication between technical and business stakeholders, which is key for successful outcomes. This chapter outlines the security controls recommended by NIST related to ransomware risk management. In the following chapter, we’ll demonstrate how products and services offered by Oracle align with these recommendations and help implement them efficiently and securely.
The Identify function encourages one to identify and develop an organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities with some outcomes in mind, such as asset management, business environment, governance, risk assessment, and your risk management strategy. Doing so lays the groundwork for what cybersecurity-related actions to take and helps you determine what is needed to successfully implement controls that suit your cybersecurity needs without hindrance to your business objectives.
The Protect function proactively focuses on safeguards to ensure critical infrastructure delivery by stopping or limiting the impact of a potential breach. Some outcomes to consider for this phase are identity management and access control, awareness and user training, data security, information security protection processes and procedures, maintenance, and protective technology. These outcomes help dictate what protocols and policies need to be employed to reduce the risk of a breach.
The Detect function enables the timely discovery of cybersecurity events. It is a critical part of a robust cybersecurity strategy as the faster an event is detected, the faster it can be mitigated. Some key outcomes include:
- Anomalies & Events: detect unusual activity and understand the impact of any events.
- Security & Continuous Monitoring: monitoring information systems and environments at specified intervals to identify cyber events.
- Detection Processes: procedures and processes for detection are implemented and tested to ensure awareness and understanding of cyber events.
The Respond function is focused on your planning for a breach and what to do should one occur. Having a response plan in place helps with limiting the impact of a breach. Outcomes that NIST encourages you to seek are response planning, communications, analysis, mitigation, and improvements. Continuous improvements are key to your response planning, as it must reflect today’s threat landscape and current business needs. In addition to a response plan, a mitigation plan can supplement with steps to remediate identified risks.
Finally, the Recover function focuses on maintaining plans for resilience and restore any impaired capabilities or services due to a cybersecurity event. The goal is timely recovery to normal operations and reducing the impact of a cybersecurity event. Key outcomes include:
- Recovery Planning: recovery procedures are tested, executed, and maintained to mitigate the effects of an event as quickly as possible.
- Improvement: recovery planning and processes are continuously improved.
- Communication: effectively communicating and coordinating for optimal organization, planning and execution.
7 Resilience Against Cyberthreats
Oracle offers customers a broad range of security and identity management products and services and has built security capabilities into its products. The company’s strategy has been to offer security capabilities integrated directly into its flagship products such as databases, business applications, and cloud infrastructure. With layered security across infrastructure, applications, and data, Oracle customers can rely on these to reduce their exposure to vulnerabilities, thus minimizing their attack surfaces and reducing the potential impact of cyberthreats.
We will discuss some examples of how Oracle helps organizations implement the guidance provided by the NIST cybersecurity framework.
7.1 Identify
An example of how Oracle helps their customers address a few of the Identify outcomes is with their database offerings. Oracle Data Safe is a unified control center for your Oracle databases. It empowers organizations to understand data sensitivity, evaluate risks to data, mask sensitive data, implement and monitor security controls, assess user security, monitor user activity, and address security compliance requirements, both on premises and in the cloud. Moreover, it can highlight which Oracle databases are at the highest risk of damage from an exfiltration attack and provide insight into the potential risks for a particular instance.
The Oracle Database Lifecycle Management Pack provides discovery and inventory tracking for Oracle database instances. It also provides change management capabilities: which patches are pending for a particular instance and what is their level of severity. Configuration management is also included to ensure that configurations properly align to policies for the respective instance. Another database tool that helps achieve these outcomes is Oracle Database Security Assessment Tool (DBSAT), which provides a point in time assessment to assist with identifying areas where your database configuration, operation, or implementation introduces risks and recommends changes and controls to mitigate those risks.
With the Oracle Vulnerability Scanning Service (VSS), your OCI Compute instances and container images are checked routinely for components known to include vulnerabilities, as well as open ports by assessing and monitoring Compute instances. The service generates reports with metrics and details about these vulnerabilities, with scan results published to Oracle Cloud Guard. The scanning service also identifies exploitable OS configurations and compliance against industry-standard benchmarks published by the Center for Internet Security (CIS).
7.2 Protect
For both on-premises and cloud environments, the Oracle Database provides Transparent Data Encryption (TDE) to ensure data at rest is encrypted and will maintain its encryption if exfiltrated. With Oracle Key Vault, organizations can ensure that encryption keys are not stored persistently on the database server and therefore, the confidentiality of sensitive data is maintained even if the database is compromised.
OCI Vault enables organizations to manage the encryption keys centrally to help protect their data and the credentials that are used to access resources securely. Vaults stores master encryption keys and secrets that you might otherwise store in configuration files or in code and are backed by highly available and durable hardware security modules (HSM) that meet Federal Information Processing Standards (FIPS) 140-2 Security Level 3 security certification.
Oracle Database Vault also contained within the Oracle database assists with mitigation for privileged compromised credentials by providing the least privileged access for privileged accounts. In addition, Database Vault can utilize attributes such as time of day, IP subnet and many others to either restrict or limit access to the database. These capabilities are beneficial in combating ransomware attacks, since research reveals that compromised privileged credentials are one of the most common tactics used.
Another preventative measure includes Oracle Autonomous Linux, which automates the installation of Linux patches and updates, while Oracle Autonomous Database ensures that the database platform and database software are automatically updated. This capability of automatically applying patches limits an organization’s exposure to known vulnerabilities where patches exist. A key distinction of Oracle’s autonomous solutions is that they are configured according to industry best practices by default and do not require a customer to enable security controls manually.
In fact, the distinction between autonomous solutions as opposed to more traditional “automated” ones is that all management controls to a system or database are sealed, and all human access to them is eliminated. Thanks to a combination of secure cloud infrastructure, intelligent automation, and patented technologies like Ksplice, Oracle customers get maximum uptime and security with minimum administration, while their IT expert can focus on higher-value projects.
Segmentation capabilities offered by Oracle provide virtual firewall capabilities at both the subnet and VNIC levels, with ingress and egress rules that specify the types of traffic allowed in and out. This delivers the ability to segment networks and use micro-segmentation of hosts to limit an attacker’s lateral movement and can prevent access to and from known bad networks, while route tables ensure connections from only trusted networks and provide segmentation of network routes.
Security Zones are a preventative control designed to help prevent poor implementation choices by enforcing security rules (recipes) for their respective compartment (zone). When you create and update resources in a security zone, these operations are validated against the list of policies defined in the security zone recipe. If a security zone policy is violated, then the operation is denied.
OCI Private DNS allows organizations to control how network addresses are resolved and helps prevent resolution to known bad networks. And with a newly released OCI Network Firewall, Oracle offers a natively integrated service powered by Palo Alto Networks that enables advanced network security controls for east-west (flowing within a private network) and north-south (flowing between private and public networks) traffic, further restricting lateral movement.
Oracle has a long history with Identity and Access Management, which enforces access control policies within an Oracle tenancy. And unsurprisingly, the default posture for logical access is "deny all”. It also provides robust MFA and can federate with your SAML 2.0 identity provider to provide SSO capabilities.
There is no anonymous access anywhere in the Oracle Cloud. Console access or API access requires an authenticated request/session. Once authenticated, an access control policy dictates the level of access to OCI resources. The policies are assigned to compartments/tenancy and are based on user group memberships.
Compartments are unique to OCI and provide identity boundaries for groups of cloud resources. They allow an organization to distribute management responsibility for cloud resources based on its business and operational model. Compartments deny access by default until policies are written to allow access to the resources within it.
Policies enforce access privileges to cloud resources in compartments. OCI’s policy language is natural language-based, easy to understand, and powerful. This allows you to create very fine-grained access to all your cloud resources, including the ability to prevent the modification and deletion of storage.
Using all these IAM controls together, customers can enforce role-based, least-privileged access, help prevent credential theft and limit lateral movement in their environment.
7.3 Detect
There are several examples of how Oracle can help achieve the Detect outcomes described earlier:
Oracle Cloud Audit Service contains a log of all actions taken within a tenancy, whether via the console, command line, or API. The contents cannot be altered or deleted.
The Logging Service represents an aggregation of the Audit log and OCI Service logs, which are emitted by OCI native services, including VCN Flow Logs. Custom Logs (for example, application logs or security tool logs) can also be sent to the Logging service. Once captured by the service, the logs cannot be altered or deleted. Logs can also be exported via the Streaming service, where they can be consumed by your SIEM or other security tools.
Oracle Cloud Logging Analytics allows organizations to index, enrich, aggregate, explore, search, analyze, correlate, visualize and monitor all log data, including external logs.
The Oracle Cloud Monitoring Service provides metrics, which relay data about the health, capacity, and performance of your cloud resources.
Cloud Guard is a cloud-native service that examines the configurations of cloud resources and actions taken via the Audit log and evaluates the logs against the custom detection rules you define to uncover security weaknesses within your tenancy. Upon detection, Cloud Guard can suggest, assist, or take corrective actions, based on your configuration, or this alert can be forwarded to your SIEM for further analysis or action.
7.4 Recover
Oracle understands the recovery of critical databases is a key component of any cyber protection strategy. The ZDLRA (Zero Data Loss Recovery Appliance) was purpose-built by Oracle specifically to help provide the best level of recovery protection possible for critical Oracle Databases. The ZDLRA leverages proprietary features built into the Oracle Database to provide an integrated solution with unique benefits, such as:
- Near-Zero Data loss – The ZDLRA leverages the High Availability technology to help immediately protect transactions for recovery. This provides both a sub second RPO and real-time tamper detection of database transactions.
- True incremental forever backups – By cataloging database backups and leveraging recovery algorithms, the ZDLRA can provide full database backups from incremental backups. This helps provide the fastest possible recovery with limited impact on the Oracle Database Workload. In a cyber vault environment, this provides full recovery protection with minimal replication traffic.
- Locked backups – The ZDLRA protects the recovery window to ensure that the backups are protected and locked even from administrator credentials.
- Recovery Protection – The ZDLRA internally simulates a restore test of all Database Backups. This helps provide the best protection possible independent of database clients, even in a cyber vault implementation.
- Separation of Duties – The ZDLRA manages the Oracle Database backup catalog internally and protects that catalog from changes by the Database Admin. This integration is unique to the ZDLRA.
- Reporting and alerting – The ZDLRA reports the validated recovery status of all databases and will alert if any databases are unprotected.
Once a backup is created, the Database or Recovery Appliance Administrators are unable to reduce the retention time or delete the backup. Storing immutable backups and performing self-contained validation and anomaly detection on multiple layers helps assure that backups will be ready in case of a cyber-attack.
Other Oracle services can help further improve the degree of automation and interoperability of your backup operations. Active Data Guard automates the replication of databases for business continuity and disaster recovery. Oracle GoldenGate replicates data from databases and other sources to target databases, facilitating business continuity and disaster recovery. Finally, Oracle Recovery Manager (RMAN) running on your on-premises Oracle Databases can be backed up directly to Oracle cloud Object Storage.
All these services help ensure that organizations, even with the most complex, hybrid, and multi-cloud deployment requirements, data protection and recovery operations are working in accord, fulfill compliance requirements, and are tuned to a high degree of automation, providing you peace of mind knowing that your organization’s future operations may not be disrupted by ransomware.
8 Recommendations
Ransomware has been a cybersecurity threat for many years, and it continues to be a growing concern. Thus, organizations should actively work to reduce their risk as much as possible by following the latest guidance and best practices, investing in a strong security posture with prevention at its foundation, and cultivating robust detection, response, and recovery capabilities.
Ransomware does not discriminate, and if it is successful, the impact it has on an organization could be significant with far-reaching effects. As the threat landscape evolves, so does ransomware. The nuances in the strategies to cope with ransomware will also evolve, but focusing on designing a comprehensive, multi-layered security architecture to address ransomware and any other kind of cyberattack across every environment you operate in, could be key to keeping your organization safe.
Implementing preventative measures, good risk management, and contingency plans will help minimize impact and downtime. While focusing on key areas such as network segmentation, a Zero Trust architecture, and strong data protection protocols could block most ransomware attacks, it is important to bundle this with well-established cybersecurity guidelines and best practice controls such as those prescribed in the NIST Cybersecurity Framework.
Continuously improve upon each outcome in the five functions: Identify, Protect, Detect, Respond, and Recover. And most importantly, remember that you do not need to do it alone – look for trusted advisors and competent vendors that will support you along your mission to defend against ransomware or any other threat.
9 Related Research
Leadership Brief: Defending Against Ransomware
Advisory Note: Understanding and Countering Ransomware
Buyer’s Guide: Ransomware Protection
Blog: Dark Side Ransomware Attacks
Blog: Ransomware During the Pandemic Crisis
Blog: Software Security and Cyber Supply Chain Risk Management
Insight: Business Resilience
Whitepaper: Key Criteria for Assessing Cloud Service Provider Security
10 Copyright
© 2024 KuppingerCole Analysts AG all rights reserved. Reproduction and distribution of this publication in any form is forbidden unless prior written permission. All conclusions, recommendations and predictions in this document represent KuppingerCole's initial view. Through gathering more information and performing deep analysis, positions presented in this document will be subject to refinements or even major changes. KuppingerCole disclaims all warranties as to the completeness, accuracy and/or adequacy of this information. Even if KuppingerCole research documents may discuss legal issues related to information security and technology, KuppingerCole does not provide any legal services or advice and its publications shall not be used as such. KuppingerCole shall have no liability for errors or inadequacies in the information contained in this document. Any opinion expressed may be subject to change without notice. All product and company names are trademarks ™ or registered trademarks ® of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
KuppingerCole Analysts support IT professionals with outstanding expertise in defining IT strategies and in relevant decision-making processes. As a leading analyst company, KuppingerCole provides first-hand vendor-neutral information. Our services allow you to feel comfortable and secure in taking decisions essential to your business.
KuppingerCole Analysts AG, founded in 2004, is a global, independent analyst organization headquartered in Europe. We specialize in providing vendor-neutral advice, expertise, thought leadership, and practical relevance in Cybersecurity, Digital Identity & IAM (Identity and Access Management), Cloud Risk and Security, and Artificial Intelligence, as well as for all technologies fostering Digital Transformation. We support companies, corporate users, integrators and software manufacturers in meeting both tactical and strategic challenges and making better decisions for the success of their business. Maintaining a balance between immediate implementation and long-term viability is at the heart of our philosophy.
For further information, please contact clients@kuppingercole.com.
-
https://go.veeam.com/ransomware-trends-executive-brief-2022-emea ↩
-
https://www.sonicwall.com/news/sonicwall-threat-intelligence-confirms-alarming-surge-in-ransomware-malicious-cyberattacks-as-threats-double-in-2021/ ↩
-
https://www.businessinsider.com/cna-financial-hackers-40-million-ransom-cyberattack-2021-5 ↩
















































