Functions, Differences, Overlappings
The OT environment is transforming at a rapid rate; it is the enabling technology for bewildering array of new applications. As prices have tumbled over the past decade, and devices have become more sophisticated, numerous applications of OT are now economically viable.
Operational Technology (OT)
Operational Technology is a wide and diverse topic that is rapidly expanding as new devices, and IoT application are brought to the market. Devices are now available that have built-in logic, reducing the need for PLCs; PLCs now have human-machine interfaces (HMIs), reducing the need for controllers; and telemetry circuits that used to be copper-based, now have an array of radio options from low-power wide-area network (LPWAN) to 5G.
This has led to terminology confusion that makes it more difficult to understand the components of an OT configuration and how they work. This document seeks to clarify the issues and reduce the confusion. Operational Technology (OT) refers to computing systems that are used to manage industrial operations as opposed to administrative operations. Operational systems include applications such as production line management, mining operations control, oil & gas monitoring, etc.
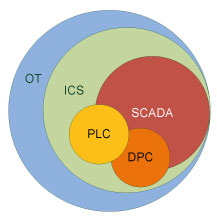
Industrial Control Systems (ICS)
Industrial control systems (ICS) represent a major segment within the operational technology sector; they comprise systems that are used to monitor and control industrial processes. This could be for a mine site conveyor belt, an oil refinery cracking tower, power consumption monitoring on an electricity grid, or a building information system management.
Most Industrial Control Systems are either a continuous process control system, typically managed via programmable logic controllers (PLCs), or a discrete process control system (DPC), that might use a PLC or some other batch process control device. Industrial Control Systems are typically mission-critical applications with a high-availability requirement.
Supervisory Control and Data Acquisition (SCADA)
Industrial control systems (ICS) are often managed via a Supervisory Control and Data Acquisition (SCADA) system that provides a graphical user interface for operators to easily observe the status of a system, receive any alarms indicating out-of-band operation, or to enter system adjustments to manage the process under control.
Supervisory Control and Data Acquisition (SCADA) systems provide a human-machine interface (HMI) that displays the process under management and provides access to control functions.
What Are the Main Components?
The configurations of the components used in an OT deployment are multitudinous and diverse. Each OT installation will deploy the components needed for its specific application. While devices may perform multiple functions, it is still beneficial to break a configuration down into the basic building blocks of an OT deployment.
OT System Components
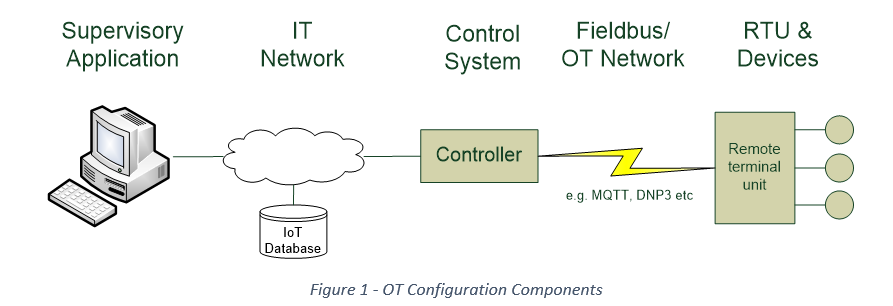
The Components of an OT system include:
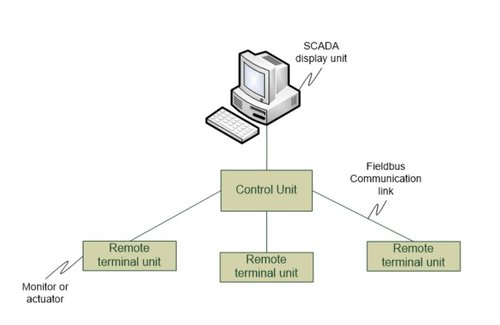
- A SCADA display unit shows the process under management in a graphic display with status messages and alarms shown at the appropriate place on the screen. Operators can typically use the SCADA system to enter controls to modify the operation in real-time. For instance, there might be a control to turn a valve off, or turn a thermostat down.
- Control Units attach the remote terminal units to the SCADA system. The Control Unit must pass data to and from the SCADA system in real-time with low latency. In the absence of a SCADA display, the control unit will have an HMI to allow configuration and management changes to be made.
- Remote terminal units (RTUs) are positioned close to the process being managed or monitored and are used to connect one or more devices (sensors or actuators) to the control unit. A PLC can fulfil this requirement. RTUs may be in the next room or hundreds of kilometers away.
- Communication links can be Ethernet for a production system, a WAN link over the Internet, or a twisted pair. Increasingly public or private radio is being employed for telemetry links to equipment in a remote area with limited communications facilities.
Examples of a typical configuration are:
- In a plant automation environment the sensors and actuators are attached to, or embedded in, machines used in the production process; the controller is a system mounted at the end of a production line; the telemetry link is often Ethernet; and the SCADA machine, or more likely a human-machine interface (HMI) computer, is located in the production manager’s office.
- In a wind turbine electrical generation environment, the sensors are mounted high up on the turbine. The RTU typically resides in an equipment shed in or near the turbine tower and comprises PLCs that monitor the generator condition, manage the gearbox controls, and take it off-line in the event of a grid anomaly or excessive wind. The control unit is typically located near the turbine farm; it provides monitoring of the turbines and manages the power entering the grid. It may use a SCADA system to do this.
- In a water utility installation, sensors will typically exist at each property under management, sensors and actuators will be located in pumping stations or pipeline control sites, which will also house the controllers. Water management systems typically do not use SCADA systems.
The Role of Distributed Control Systems
A distributed control system may be the preferred configuration if your OT system covers multiple locations e.g. water management with multiple pumping stations, or if it involves remote installations of devices e.g. electricity grid. But there are some pitfalls to be avoided.
Putting Control at the 'Coalface'
- The sensors and actuators are installed in remote locations e.g. utility distribution systems. It is generally not acceptable to rely on remote control systems in an OT environment because it introduces an avoidable risk. If a process is controlled over a communication link and the link is disrupted, or compromised, the processes could fail. Most remote installations will utilize programmable logic controllers to place the control function as close to the devices as possible.
- The processes being monitored/controlled cannot tolerate network latency e.g. plant automation systems. Many OT installations require real-time control signals with millisecond response. A conveyor belt used for product distribution might require several event messages a second, a machine shut down command can’t wait for the message to transit a network from head office, it must be locally controlled.
- Large amounts of data are being collected e.g. Building Information Management. It makes no sense to send raw data back to a central management point because of the cost of doing so. Modern edge computing technology limits the data communicated over remote links to only that essential for management purposes.
-
Distributed control systems in the OT environment are, of course, susceptible to the same vulnerabilities that distributed systems in the IT environment experience. They must be protected from compromise and data exfiltration. This is not easy for a distributed control system that is not part of the organization’s SOC or SOAR solution, but normal controls such as patching operating systems, logging authentication attempts, alarming on out-of-band events and responding to alerts, need to be maintained.
Why Air-Gapping Is Not the Solution
One way of protecting an OT environment from attack and corruption is to ensure that there are no connections to the IT environment. But isolating your OT environment fraught with difficulty and will hinder the opportunity to leverage systems in the IT environment.
Physical or Virtual Isolation?
Isolating your OT environment increases the difficulty of managing it. If you cannot leverage the corporate identity management system for authentication to OT systems you must manually manage access control to the components of the OT environment. A separate administrator must add and remove accounts in the OT environment, even though the same personnel are already managed in the IT environment. This often results in a failure to remember to remove exiting staff from the access control lists in the OT environment, causing orphaned accounts, and the associated security risks.
An isolated OT environment can also result in poor technology choices, Because OT systems are not reachable via the corporate network OT personnel will often install remote access technology on remote devices to enable them to login for administrative purposes. This generates a vulnerability, as experienced by a water treatment plant outside Orlando in early 2021; if an observant staff member had not noticed unauthorized modification of the device settings to the ‘lime additive’ controller, significant contamination of the water supply for many citizens might have occurred.
If air gapping is not mandated by government or industry regulation, there are better ways of protecting your OT infrastructure. Air gapping brings with it shortcomings that result in expensive duplication of administration services and removes the ability to benefit from advancements in better threat protection.
If air gapping is mandated, all is not lost. There are opportunities to utilize other technological solutions and these should be explored. Unidirectional firewalls are one technology that you might consider. Such devices can be used to allow for the periodic upload of specific files. For instance delta changes could be made to the identity data store once a day. This would allow the application of corporate access control policy to the OT environment.
Zero Trust and Operational Technology
Zero Trust has taken the IT sector by storm over the past few years but it is not a solution or technology. Zero Trust is a corporate strategy, it’s a reference architecture, it’s a foundational belief. You construct a zero-trust environment by adhering to set of practices that will, over time significantly reduce the vulnerability of your organization’s business operations.
'Zero Trust' Requires a New Mindset
By definition, Zero Trust requires a holistic approach to controlling access to protected resources across an organization. Extending this to the OT environment is a good idea but may not be easy. If it can be achieved, one benefit will be consistency between the access control policies that are applied on the OT side and those applied in the IT environment. Another benefit of a Zero Trust architecture is the application of risk management to your access control events that will ensure the appropriate level of authentication is applied to a user’s request for access in the OT environment. Since OT systems typically demand a high level of authentication, a Zero Trust approach can ensure the requesting user credentials are supported, and verifiable, before access is granted.
One of the key elements of a Zero Trust approach is the application of the Principle of Least Privilege. This is sometimes not supported in legacy OT environments that often rely on a single user group to manage entitlements, because that’s easier than managing a more fine-grained approach. But in an OT environment there will typically be a hierarchy in the access control restrictions. For instance, a process control technician will not enjoy the same level of access as an operations manager. To support this requirement the OT environment might need to be upgraded to provide a suitably fine-grained access control mechanism.
Another inhibitor to a Zero Trust approach in an OT environment is isolation. Air-gapping will frustrate the deployment of a consistent approach across the organization, but it’s not impossible. You can still apply similar policies, even though the same access control technology applied on the IT side will not be employed. In some cases the OT environment will rely on a strictly controlled manual IAM process or it may employ a dedicated PAM solution to protect the sensitive systems and devices. Provided the OT environment applies consistent policies and adheres to similar principles, a Zero Trust deployment can be achieved.
What Cybersecurity Experts Can Learn from NotPetya
There are three broad categories of cyber exploits when it comes to OT infrastructure: attacks at the device level, unauthorized access to control systems, and corruption of OT data stores. Account-take-over attacks such as NotPetya will generally not be able to attack at the device level. They may gain access to a control system, but the real vulnerability is to operational technology data stores.
Device-Level Attacks
It is extremely unlikely that a sensor or actuator will be individually attacked. Not only are they often in tightly-controlled or inhospitable environments, they are typically static devices with no way to gain access to anything that can be changed or updated. It is possible that a man-in-the-middle attack could occur, but this would require a sophisticated telemetry capability and internal collaboration. The data stream from the sensor, or communication to the actuator would need to be infiltrated.
More likely, is unauthorized access to a PLC. The firmware in PLCs can be periodically updated; an event that must be carefully controlled. The ability to insert nefarious code during a firmware update is a very real vulnerability. Sufficient oversight across the update process, with code reviews and PKI controls to ensure no code modification has occurred, is recommended.
Control System Infiltration
An obvious attack vector in any OT system are systems that provide a human-machine interface (HMI). These include controllers that concentrate device data and provide a management capability, or SCADA systems that provide a control as well as a monitoring capability.
It is these systems that are potential targets of an account-takeover attack. Protection ranges from the very basic: e.g. ensuring no email access or remote management software is installed, to the sophisticated: e.g. advanced threat protection or user-behavior analysis.
Data Corruption
A common mistake in organizations with OT environments is to apply protection to the OT infrastructure but then store the OT data in a repository with inadequate access controls. This exposes potentially sensitive data to unauthorized access.
For instance, a plant automation database may include production information that competitors might want, or a smart cities installation might store parking information in a database that could be intentionally corrupted. Any IoT data to be made publicly available should be anonymized and delivered via a controlled download.
Conclusion
An OT environment presents a special case for the cybersecurity practitioner. To the degree possible, OT protection should leverage the increasingly powerful controls implemented on the IT infrastructure and, to the degree possible, adopt the zero-trust approach of the organization.
It’s a Culture Thing
When it comes to Operational Technology adoption of good governance will largely be a function of the culture that exists within the corporate operations environment. Most established OT environments suffer from legacy management practices that frustrate the application of corporate governance oversight.
Personnel tasked with managing OT infrastructure might consider IT personnel as not competent in understanding operational issues and including IT personnel in decisions regarding OT infrastructure as dangerous. In such an environment the OT infrastructure will be opaque to the CIO and will exist outside the organization’s normal control boards and review processes.
In some cases legacy OT infrastructure is managed by external personnel. Often the technology supplier is under a support contract to maintain the environment. Establishing a consistent approach to cybersecurity across an organization will be difficult in such circumstances. Managing the corporate culture is therefore core to adequately protecting distributed control systems, managing air-gapping requirements, deploying a zero-trust approach or mitigating account-takeover risks.
As companies accelerate the adoption of OT infrastructure, to improve customer service and reduce operational costs, management must focus on the corporate culture and ensure consistent application of company policy and control mechanisms.
















































