Running an application or a service implies covering a large set of diverse responsibilities. Many requirements have to be fulfilled: the actual infrastructure has to be provided, which means that bare metal (computers, network and storage devices) as the foundation layer has to be installed and made available. On the next logical level operating systems have to be installed and appropriately maintained, including patches and updates. Appropriate mechanisms for virtualization have to be implemented.
Any layer of the provided infrastructure has to be implemented in an adequately scalable, stable, available and accessible way, at an at least sufficient level of performance. Service level agreements have to be defined and met which involves responsibilities for availability, accessibility, again scalability. This also requires the allocation of appropriate administrative or user services, e.g. implementing help desks and/or self-service infrastructure.
Security is of utmost importance for every application, service or infrastructure. This includes for example platform security, the reliable and robust management of users and privileged accounts and their individual roles, fine-grained access control and network security including intrusion detection. In a shared, virtualized environment this also demands strong requirements for the separation of individual, parallely operated platforms and the isolation of software, processes and data across the network, the storage and the computing environments. The provisioning of appropriate management interfaces, the implementation of change processes and maintaining stable, reliable and auditable systems operation procedures is a key responsibility within an application system or infrastructure environment.
The aspect of overall application security defines another set of responsibilities which focuses on logical and functional aspects and the business processes implemented. Ensuring all required aspects regarding the IT security of an application or infrastructure system, including the confidentiality, integrity and availability of the computer system and a proper implementation of the underlying business processes are important challenges, no matter which deployment scenario is chosen.
Whenever an application or a service is running on premises, determining who is responsible for which aspects of the infrastructure typically is a straightforward task. All vital building blocks ranging from the infrastructure to the operating system and from the application modules to the stored data and the underlying business processes is in the responsibility of the organization itself, i.e. the internal customer. Many organizations assign individual responsibilities and tasks along the lines of the ITIL service management processes with typical roles like the "application owner" or the "system owner", reflecting different functional aspects and responsibilities within the organization.
Moving services into the cloud or creating new services within the cloud changes the picture substantially and introduces the Cloud Service Provider (CSP) as a new stakeholder to the network of functional roles already established. Cloud services are characterized by the level of services provided. Individual services in the cloud are organized as layers building upon each other. Although the terms are not used consistently across different CSPs, cloud service offerings are often characterized as e.g. "Infrastructure as a Service" (IaaS) or "Platform as a service" (PaaS). Depending on the fact which parts of the services are provided by the CSP on behalf of the customer and which parts are implemented by the tenant on top of the provided service layers, the responsibilities are to be assigned to either the Cloud Service Provider (CSP) or the tenant.
The following image gives a rough overview which responsibilities are to be assigned to which partner within a cloud service provisioning contract in which cloud service model. While an "Infrastructure as a Service" (IaaS) scenario puts the responsibility for only the infrastructure on the Cloud Service Provider (CSP), the only responsibility left to the tenant in a "Software as a service" (SaaS) scenario is the responsibility for the actual business data. This is obvious as the data ownership within an organisation is an inalienable responsible and thus cannot be delegated to anybody outside the actual organisation.
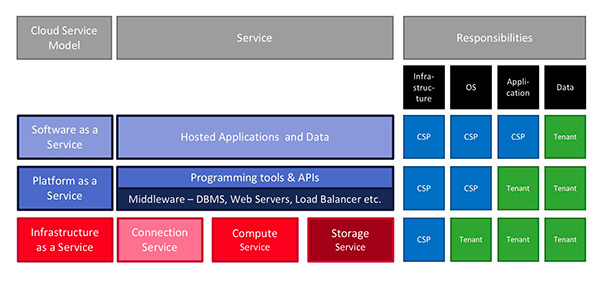
Shared responsibilities between the Cloud Service Provider (CSP) and the tenant are a key characteristic of every deployment scenario of cloud services. The above image gives a first idea of this new type of shared responsibilities before between service providers and their customers. For every real-life cloud service model scenario all responsibilities identified have to be clearly assigned individually to the adequate stakeholder. This might be drastically different in scenarios where only infrastructure is provided, for example the provisioning of plain storage or computing services, compared to scenarios where complete "Software as a service" (SaaS, e.g. Office 365) or even "Business process as a Service" (BaaS) is provided in the cloud, for example an instance of SalesForce CRM. A robust and complete identification of which responsibilities are to be assigned to which contract partner within a cloud service scenario is the prerequisite for an appropriate service contract between the Cloud Service Provider (CSP) and the tenant.
This article has originally appeared in KuppingerCole Analysts' View newsletter.
















































