Introducing DREAM (Dynamic Resource Entitlement and Access Management)
Paradigm for managing all access of everyone and everything to all resources consistently in a multi-cloud multi-hybrid environment. Policy-based, automated, consuming the current state of services & infrastructure. Shifting from identity & security siloes to a holistic, integrated concept. Start tactically now with CIEM, PAM, etc., but go on to strategic measures.
Managing identities, managing entitlements, and managing access has become way more complex than ever before, in dynamic, multi-cloud, multi-hybrid IT environments. In the past, servers and applications were rather static, and entitlements too were static. But this has changed. Entitlements and access in today’s cloud environments are dynamic, just like workloads.
Additionally, most organizations must deal with a multi-cloud, multi-hybrid IT. Different clouds, such as Microsoft Azure, AWS, or GCP, are very different in the way they deal with and manage identities, resources, access, and entitlements. With private clouds, managed IT, Edge Computing, and on-premises IT, different approaches on delivering IT are there to be managed, all different in the technology as well as the split between provider and tenant responsibilities.
Security as Code Can’t Be the Answer
However, the answer can’t be in security as code, because this would require developers to care for security (and infrastructure management), instead of setting the focus on their specialized skills and letting them work on what they are best in. The answer also can’t be in having specialized solutions for different parts of the IT environment, such as cloud-only approaches. Organizations need a comprehensive approach, covering the breadth and depth of their multi-cloud, multi-hybrid IT reality.
DREAM takes this broader approach, beyond just cloud-focused management of entitlements and access, looking at all types of identities, workloads, and all elements of IT. Additionally, DREAM is well-integrated with SODAS and BASIS, delivering a comprehensive set of methods and models for moving to agile delivery of secure services in multi-cloud, multi-hybrid IT environments.
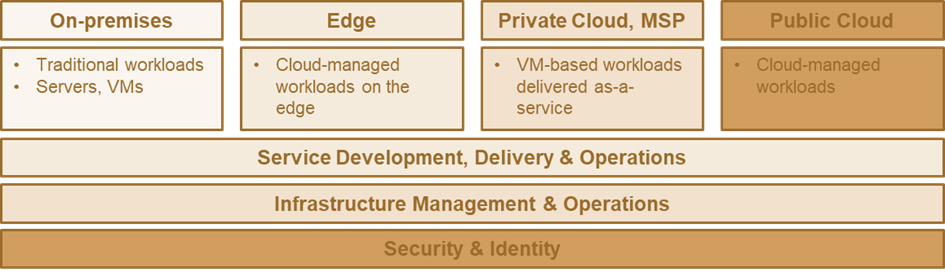
Fig. 1: DREAM integrates security & identity across all parts of multi-cloud, multi-hybrid IT environments, closely aligned and integrated with service development, delivery & operations as well as infrastructure management & operations (KuppingerCole SODAS).
Cloud-First Approach Will not Lead to a Uniform Environment
As outlined, most organizations today have a mix of different types of IT. While “cloud first” is a valid strategy, it will not lead to a uniform environment. While the ratio of cloud workloads will (and must) grow over time, it will be multi-cloud and thus not uniform. Edge Computing appeared as a response to the need to shift workloads back closer to the on-premise environment. However, there was a reason for private clouds to appear, as well as for keeping parts of IT on-premises.
In manufacturing and other industries, on-premises IT will never disappear. Multi-cloud, multi-hybrid is the reality, here to stay. It will differ in the ratios of what is done where, but it will not disappear for many organizations, and the shift will be slow (slower than frequently expected) and gradual for most organizations.
This requires, as described in KuppingerCole SODAS (Secure Operations & Development of Agile Services), an integrated approach to development, infrastructure management, operations, and security & identity. DREAM focuses on the Security & Identity layer within that concept and how to manage identities, entitlements, and access uniformly across the entire IT, powered by policy-based automation.
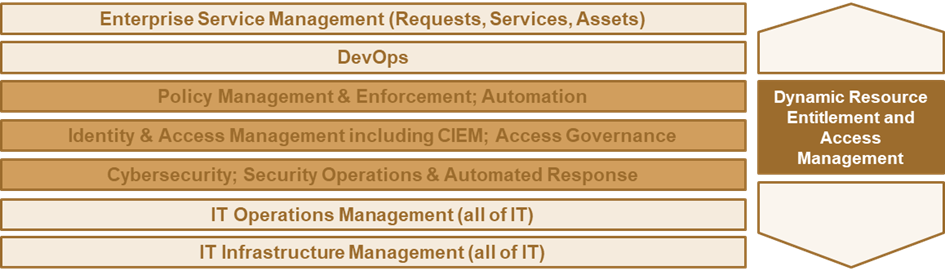
Fig. 2: DREAM focuses on IAM, including CIEM, Access Governance, and PAM, as well as Cybersecurity and SOAR, and aligns with the other elements of a modern IT stack for delivering agile, secure services.
Managing Identities and Entitlements with the DREAM Approach
DREAM is an approach for managing all types of identities, both human and non-human. Human identities span everyone from the consumer to the employee, while non-human identities cover devices, things, services, resources, etc., as well as the complex relationships between the various types of identities.
DREAM focuses on managing entitlements and unifying this management across different environments such as the various public clouds, private clouds, VM (virtual machine) environments, and servers in traditional IT.
Based on a comprehensive , uniform approach, it puts identity and security in one responsibility and a unified technical solution, also enabling consistent governance across the entire IT environment. This also includes supporting modern concepts such as SOAR (Security Orchestration, Automation, and Response) that build on SIEM (Security Information and Event Management), and monitoring what happens in terms of security across all of IT as well as reacting to this.
DREAM Integrates CIEM, IGA, IAM, and PAM
DREAM also integrates concepts such as the evolving concept of CIEM (Cloud Infrastructure Entitlement Management), IGA (Identity Governance & Administration) as part of IAM (Identity & Access Management), and PAM (Privileged Access Management) for supporting every identity, every entitlement, and the access across the entire breadth and depth of IT.
This requires utilizing information about the state of services, applications, resources, identities, etc. It builds on virtual repositories that gather and expose that information so that it can be analyzed – this is where AI & ML come into play – and policy-based automation of the entire management of identities and security then build on these repositories.
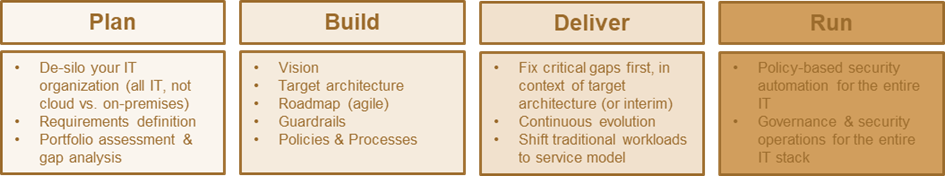
Fig. 3: The key actions to take in delivering to the DREAM model.
To move forward with DREAM, the first step is – if not already done – the de-siloing of IT. Don’t treat cloud differently from on-premises or private clouds. Don’t split responsibilities. Workloads might run here or there, they will shift. For application and service delivers, you need a unified approach. You need it even more for comprehensive, strong security and efficient management of identities and access, and, last but not least, for (access) governance, complying with regulations, and mitigating risks. This initial step also requires a portfolio assessment and gap analysis, to understand what you have, what you need in addition, and what you should best retire.
From there, based on a vision involving the KuppingerCole models for Identity Fabrics and Security Fabrics, you need to define the target architecture, a roadmap that evolves over time, the guardrails, and the policies and processes.
Running DREAM Environments
Roll-out should be tactical and phased, focusing on fixing the critical challenges first. This might include opting for a specialized CIEM solution first (even while most already go well beyond cloud only, and beyond infrastructure entitlements only) to fix the pressing challenges of managing entitlements and access in the dynamic, volatile cloud environments.
But all should be done with the vision and target architecture in mind, not as tactical, isolated, non-integrated activities. DREAM will evolve continually. For more efficient management, and again being part of unification as described in KuppingerCole BASIS, this also involves shifting delivery of traditional workloads to a service model – making your traditional IT work as if it were another cloud.
In running DREAM environments, policy-based automation is at the core. It is about shifting to well-defined policies (proposed and optimized by AI and ML) that work on the dynamic data, instead of manual administration. This limits errors and increases speed in responding to permanent changes in the agile IT of today. It is also the foundation for governance and consistent security operations, and automated response across the IT environments.
Guiding principles for DREAM:
- Business requests IT Services
- Unified view on IT Services – one IT, across multi-hybrid, multi-cloud environments
- Policy-based automation instead of manual administration or coding
- Development is agile, consuming identity & security APIs, delivering status/requirements back to central repositories, and to the operations management to be ready supporting new and changing applications and services
- Automation of identity, security and infrastructure setup & management
Our recommendation is to think beyond solutions that cover just multi-cloud, but integrate across multi-cloud multi-hybrid IT. Focus also on integration with the IAM and PAM (Privileged Access Management) infrastructure you have in place. Look at the overarching DevSecOps (KuppingerCole SODAS) model; and the model for agile service delivery in a modern, multi-cloud, multi-hybrid IT (KuppingerCole BASIS) for a comprehensive approach.

















































