1 Introduction / Executive Summary
For many enterprises, SAP systems are an essential part of the backbone of their corporate IT infrastructure. Critical business information is stored within ERP systems, and the golden source for employee data might still be the SAP HR system. Business processes are implemented through portal solutions relying on SAP infrastructure. Data is held in SAP HANA; the migration to S/4HANA is ongoing, and highly individualized functionality is coded right into the existing standard SAP modules by using ABAP or Java.
Although there are many other systems in place which contain critical information as well, many businesses still rely on the availability of well-designed and well-protected SAP Systems. Traditionally, SAP systems are a major focus area for internal and external auditors. For the successful implementation of adequate controls, it is essential that all existing SAP systems are covered by an effective solution for managing risks, and within that for managing access control and SoD controls and implementing adequate Access Governance.
On the other hand, more and more of critical business systems are following the trend of shifting to the cloud, either to solutions provided by SAP such as SuccessFactors or Ariba, or to other vendors' solutions. Thus, the scope for centralized access controls is expanding beyond the traditional ABAP systems and even beyond SAP. The requirements for solutions are expanding, either by supporting a broader range of systems or by delivering adequate integration points with other solutions covering, e.g., SaaS applications.
This is reflected in this Leadership Compass, where deep support for both SAP environments and other vendor's business applications is in focus. We will also focus on a broader range of supported deployment models, with preference for deployments that include as-a-service models.
1.1 Highlights
- The customer requirements for access control solutions for their business applications are changing rapidly in the context of the journey towards SaaS services, with many organizations needing solutions that cover a range of Line of Business (LoB) applications from different vendors, operated in varying models
- Several customers continue to focus on their traditional SAP environments, with the SAP department being the buyer, looking for deep integration into these environments and familiar user interfaces
- We expect the trend towards supporting a broader range of LoB applications to continue, within SAP's own portfolio, e.g., SuccessFactors, and beyond
- New entrants to the market focus on a deeper integration of cross-system IGA (Identity Governance & Administration), and access control solutions for LoB applications, putting pressure on established vendors
- The number of vendors being backed by Venture Capital or Private Equity has increased significantly, fostering innovation and competition
- For non-SAP solutions, the long-standing experience regarding best practice role models, critical access rule sets, and SoD (Segregation of Duty) role sets is still lacking at most vendors; thus, few are already delivering the depth of support they provide for SAP ECC, and customers should carefully evaluate in their PoCs whether support for other systems delivers on their expectations and requirements
- AI (Artificial Intelligence) and ML (Machine Learning) are gaining momentum quickly, supporting leading solutions in better analytics and recommendations
- Overall Leaders are (in alphabetical order) Appsian, Pathlock, SailPoint, SAP, Saviynt
- Product Leaders are (in alphabetical order) Appsian, CSI tools, Pathlock, SailPoint, SAP, Saviynt, and SIVIS
- Innovation Leaders are (in alphabetical order) Akquinet, Appsian, CSI tools, Pathlock, SailPoint, SAP, Saviynt, SIVIS, and Soterion
1.2 Market Segment
In this KuppingerCole Leadership Compass, we analyze solutions that support managing access controls specifically for SAP environments and other vendor's business applications or LoBs (Line of Business applications). The main focus is on delivering the depth for implementing management and controls across these environments. With the changing landscape of business applications, broader support for implementing controls across all critical business systems has become a focus of our evaluation.
Thus, the segment is expanding in two directions:
- Breadth of supported environments, e.g., SAP Business Suite, SAP HANA and S/4HANA, and business applications that are provided as SaaS applications (Software as a Service) by SAP as well as by other vendors such as Workday, Salesforce, Microsoft, Oracle, and many others, with the expectation that solutions deliver strong support for SAP environments, but also support the broadening range of LoBs in use by organizations.
- Breadth of capabilities, beyond just identifying critical entitlements and SoD violations to a broader scope of mitigating access-related risks in such environments.
Furthermore, deployment models for both the managed services and the solutions are changing, with more SaaS services to manage, and deployment in different ways – as ABAP solution, with SAP Fiori user interface, or separately from SAP as web applications or, becoming the new standard, as SaaS services.
The core of functionality remains in the management of access controls including critical entitlements and SoD conflicts in SAP and other LoB environments. However, solutions frequently also cover additional features such as break-glass access management (firefighter, emergency access), user lifecycle management, role optimization, and more.
The solutions span from solutions targeted at read-only analysis for audits of SAP core systems to comprehensive suites covering a broad range of capabilities around access control and security for a heterogenous set of LoB solutions, including SAP solutions.
1.3 Delivery Models
We did not restrict our analysis in this Leadership Compass regarding the delivery models. We currently find a broad range of implementation models, from pure-play ABAP solutions to ones having a Fiori app added to full SaaS services, but also some SaaS services that integrate with ABAP modules back to SAP. While the trend is towards SaaS solutions, we have covered all types of deployment models in this report.
Generally speaking, our focus in rating is on a maximum flexibility for customers. There are advantages and disadvantages of all approaches. A full integration as ABAP solution is great for supporting the traditional SAP environments, but comes to its limits in supporting other vendor's SaaS solutions. Although, while the user interface still might be favored by experienced SAP users, many users – including experienced SAP users – nowadays prefer modern user experiences.
Fiori as user interface is something some that are familiar with SAP environments might prefer, while others might prefer other web UIs, not limited to the Fiori UX (user experience) paradigms.
Solutions that run separately from SAP environments are better suited for supporting SaaS services and applications beyond SAP solutions. Some of these also excel in user experience, based on modern UIs with high usability.
It depends on the current and future scope of applications to manage, and on the features in focus, which of the various delivery models is best suited for whom. However, the tendency appears clear: Away from traditional ABAP, towards modern user experience, supporting the increasingly heterogeneous business application infrastructure, and being delivered as SaaS.
Factually, solutions can be grouped into four types:
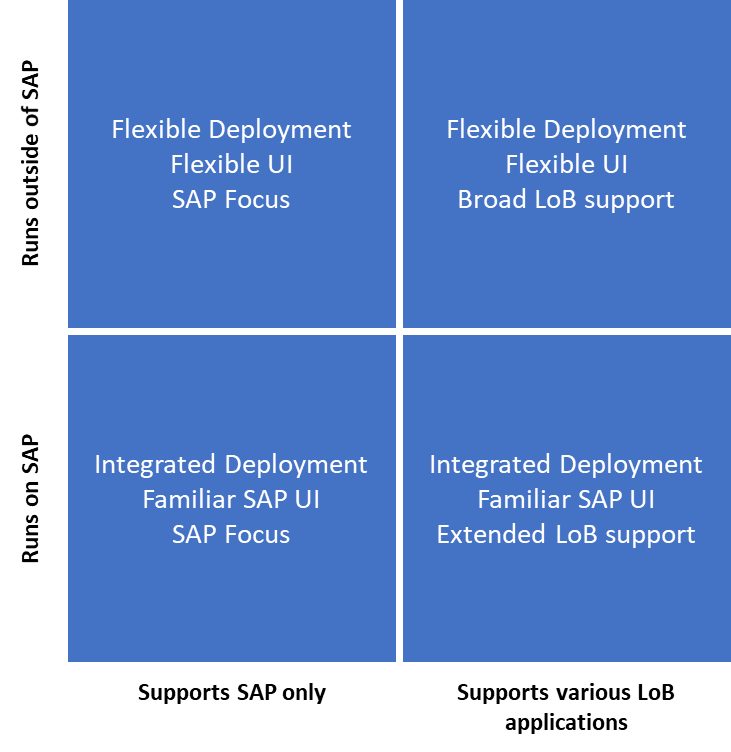
Solutions can run in the SAP ecosystem or outside of it, the latter commonly being deployed as SaaS. They can focus on SAP only or extend beyond that ecosystem. The number of vendors that stick to a SAP-only approach has decreased significantly since the previous edition, with most vendors including SAP adding interfaces and support for non-SAP LoB solutions.
1.4 Required Capabilities
Due to the variety of capabilities provided by the solutions that are currently offered, but also with respect to the changing environments, there is a broad set of capabilities we are looking for, split into baseline capabilities and advanced capabilities. The baseline capabilities dominate the rating, with other capabilities adding to this.
The exception is broad support for systems, beyond the traditional SAP Business Suite. The breadth of support of LoB applications beyond the traditional SAP scope has high impact on our ratings, given the fact that we see increasing demand and strategic changes in the way business system environments look like.
Baseline capabilities we are looking for:
- Flexible deployment models, including as-a-service deployments
- Support for all major SAP systems and versions
- Support for other vendor's business applications
- Analysis of the current status of entitlements/roles at all levels, from transactions to business roles, including Access Risk Analysis
- Role and entitlement management
- Access management, i.e., assignment of entitlements (Access Management)
- SAP super-user management and privileged user management for other LoB solutions (see below)
- Identity Lifecycle Management for the target applications, i.e. creating and managing accounts (User Management)
- SAP Firefighter capabilities, and ideally emergency access management for other LoB applications (see below)
- SoD controls management, check, and enforcement across all supported systems
- Central Reporting and Dashboarding
- Access Review support
Advanced capabilities we are interested in seeing as part of these products:
- Support for hybrid deployment models or pure SaaS deployment
- Automated role optimization
- Support for non-ABAP systems
- Support for SAP cloud solutions such as SAP Hybris, SAP Customer Cloud, Concur, Ariba, SuccessFactors, etc.
- Support for non-SAP business applications, both on premises and SaaS, including Enterprise Service Management solutions such as ServiceNow and Jira
- Go-Life support for SAP systems (specifically S/4HANA) with focus on entitlements, i.e. transferring entitlements
- Password Self Service and Single Sign-On
- Integration capabilities to cross-plattform IGA solutions (covering non-SAP-systems for both Identity Lifecycle Management and Access Governance)
- Auditor support and run-time execution for audits
- Support for specifics of platforms such as SAP BI, S/4HANA, and SAP HANA In Memory Database
- Super user management for other business applications
- Firefighter capabilities for other business applications
- System hardening capabilities
- Capabilities for managing exports and transfers of critical data, such as HR data
Inclusion criteria:
- Solutions covering all or most of the baseline capabilities
- All deployment models – solutions can run on premises as ABAP applications, on premises in other models, hybrid, or as SaaS applications
- Solutions covering only SAP environments
- Solutions not covering SAP environments, if these support a range of other business applications
Exclusion criteria:
- Solutions that only cover singular baseline capabilities such as Firefighter access for SAP only
- Solutions that are targeted on read-only analysis of entitlements and risk analysis for auditors, but don't support active management of users and entitlements
- Solutions that don't support the entire depth of entitlement/roles at all levels, i.e. solutions that e.g. only can assign users to SAP business roles but can't manage entitlements of such roles
We've reached out to a large number of vendors for providing a comprehensive overview of the current state of the market. Picking the right vendor finally always will depend on your specific requirements and your current and future landscape that must be managed.
2 Leadership
Selecting a vendor of a product or service must not only be based on the information provided in a KuppingerCole Compass. The Compass provides a comparison based on standardized criteria and can help identifying vendors that shall be further evaluated. However, a thorough selection includes a subsequent detailed analysis and a Proof of Concept of pilot phase, based on the specific criteria of the customer.
2.1 Overall Leadership
Based on our rating, we created the various Leadership ratings. The Overall Leadership rating provides a combined view of the ratings for
- Product Leadership
- Innovation Leadership
- Market Leadership
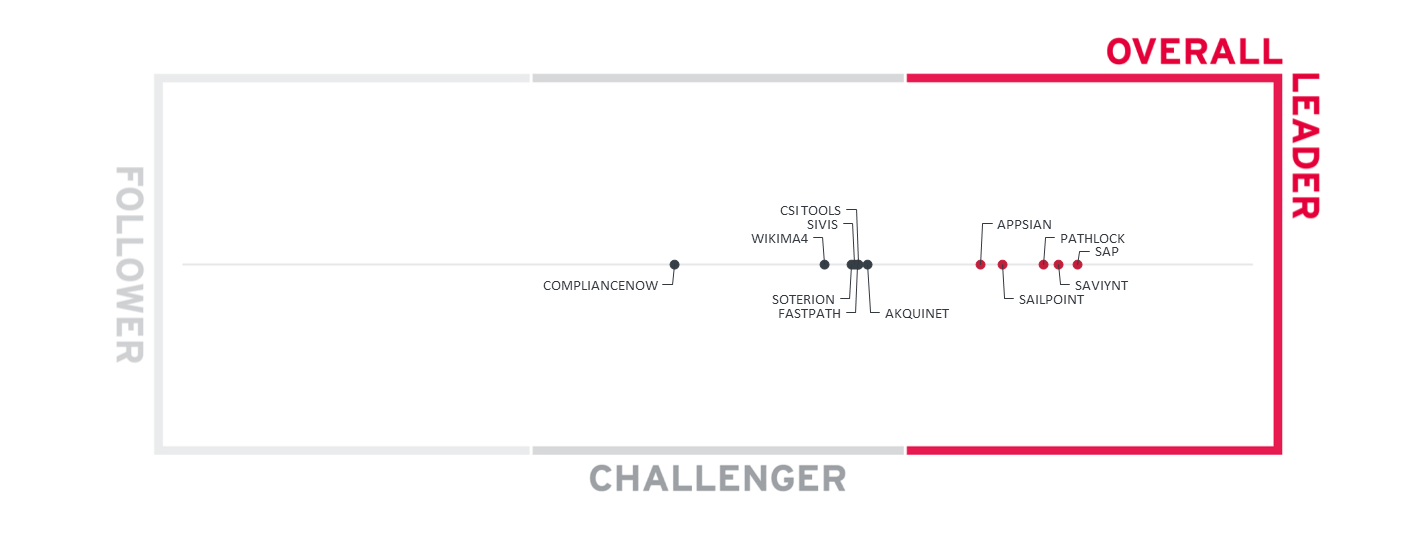
In comparison to the previous edition of this Leadership Compass, which put a stronger emphasis on SAP specific support, and lesser on supporting a broader set of LoB solutions beyond the SAP ecosystem, we see various changes. Additionally, some new vendors have been added to the rating, such as Pathlock and SailPoint. Pathlock has been formerly known as Greenlight GRC and SailPoint came in via the acquisition of ERP Maestro.
In the Overall Leader’s segment, we see SAP slightly ahead of Saviynt and Pathlock, all being placed closely to each other. SAP is, on one hand, the undisputed Market Leader, and is also showing progress in evolving their solutions in this market segment. Both Saviynt and Pathlock have leading-edge product offering with a broad support for a heterogeneous environment of LoB solutions, but also deep support for the SAP ecosystem.
Closely following them we find SailPoint and Appsian. SailPoint provides a comprehensive ecosystem for IGA and has added in-depth LoB support with the acquisition of ERP Maestro, which now became the SailPoint Access Risk Management solution. Appsian has acquired Xpandion and extended the solution portfolio.
In the Challenger section, we find a group of vendors that are very close in the rating, with (in alphabetical order) Akquinet, CSI tools, Fastpath, SIVIS, Soterion, and Wikima4. These vendors are following diverse strategies for this market segment, from a traditional SAP deployment and focus, such as Akquinet, to broadening support beyond SAP and delivery as a SaaS service, such as SIVIS. It requires careful understanding of the own requirements and analysis of the vendors in selecting the right solution provider. Following this group, we find ComplianceNow, part of Nagarro ES, which also takes a traditional approach with tight integration into the SAP environment and focus on the traditional SAP core systems. They provide strong capabilities for the traditional SAP environments, together with the ability to deliver on global scale, backed by Nagarro ES as a leading consultancy.
Overall Leaders are (in alphabetical order):
- Appsian
- Pathlock
- SailPoint
- SAP
- Saviynt
2.2 Product Leadership
Product Leadership is the first specific category examined below. This view is mainly based on the analysis of service features and the overall capabilities of the various services.
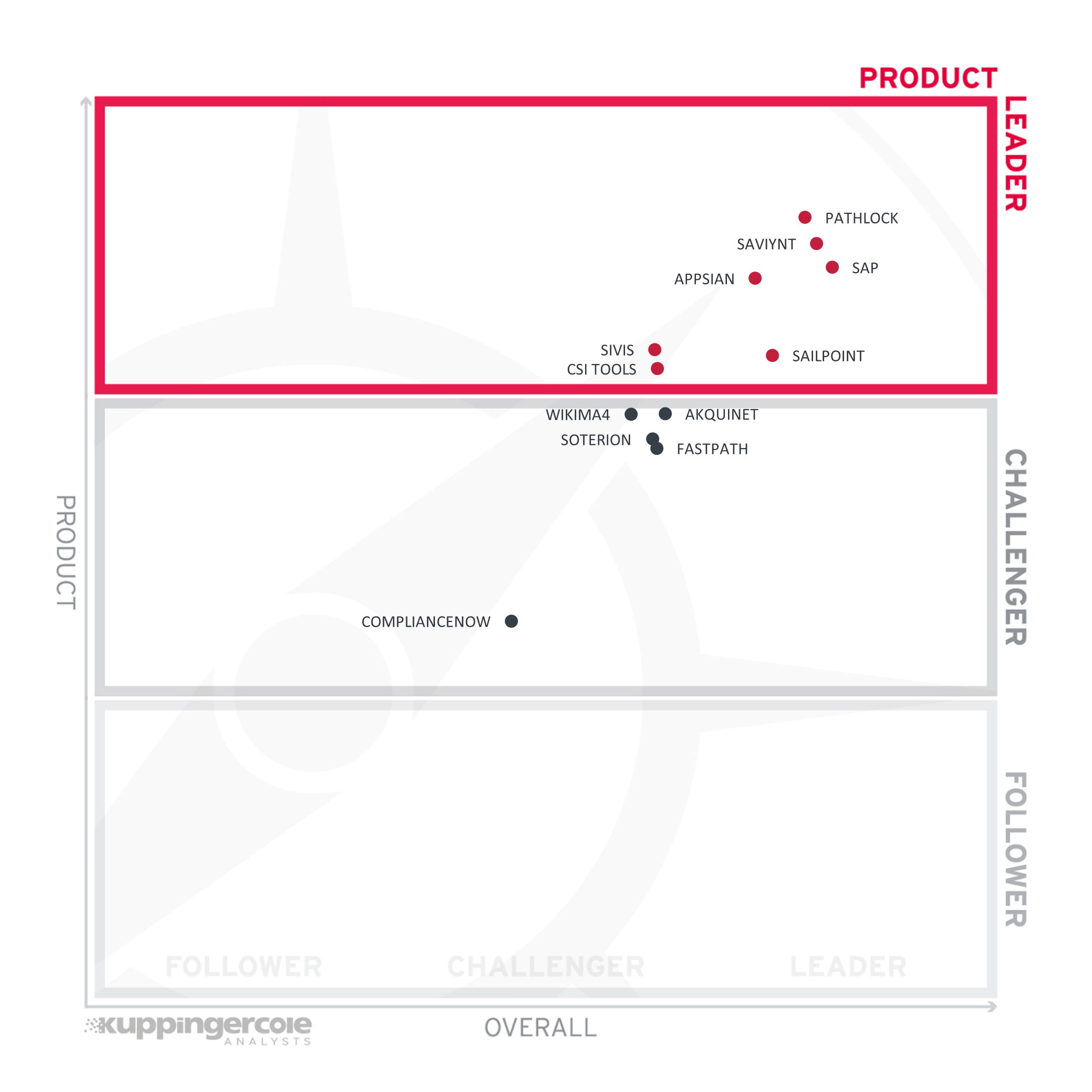
Product Leadership is where we examine the functional strength and completeness of services.
Despite the evolution in the market, we find a significant number of mature solutions with a wide set of capabilities here, leading to a rather packed Product Leader's segment. In the lead we find Pathlock, with excellent support for LoB applications and deep SAP expertise. Saviynt, SAP, and Appsian are following closely, with diverse approaches on addressing the requirements in this market segment, but all with mature and feature-rich offerings. SIVIS, SailPoint, and CSI tools also made it into the Product Leader's segment with their offerings.
Another group of vendors is close to entering the Product Leader's segment, being rated at the upper level of the Challenger's segment. This group consists of (in alphabetical order) Akquinet, Fastpath, Soterion, and Wikima4. Each of these vendors delivers feature-rich and interesting solutions that are good fits to certain customer use cases.
Following them is ComplianceNow, which have a proven and mature offering, but are focused on traditional SAP core systems only, also with limited coverage of the extended capabilities we are looking at in our research. However, for customers that focus on access control solutions for this specific set of SAP solutions, ComplianceNow is a leading-edge solution.
Product Leaders (in alphabetical order):
- Appsian
- CSI tools
- Pathlock
- SailPoint
- SAP
- Saviynt
- SIVIS
2.3 Innovation Leadership
Next, we examine innovation in the marketplace. Innovation is, from our perspective, a key capability in all IT market segments. Customers require innovation to meet evolving and even emerging business requirements. Innovation is not about delivering a constant flow of new releases. Rather, innovative companies take a customer-oriented upgrade approach, delivering customer-requested and other cutting-edge features, while maintaining compatibility with previous versions.
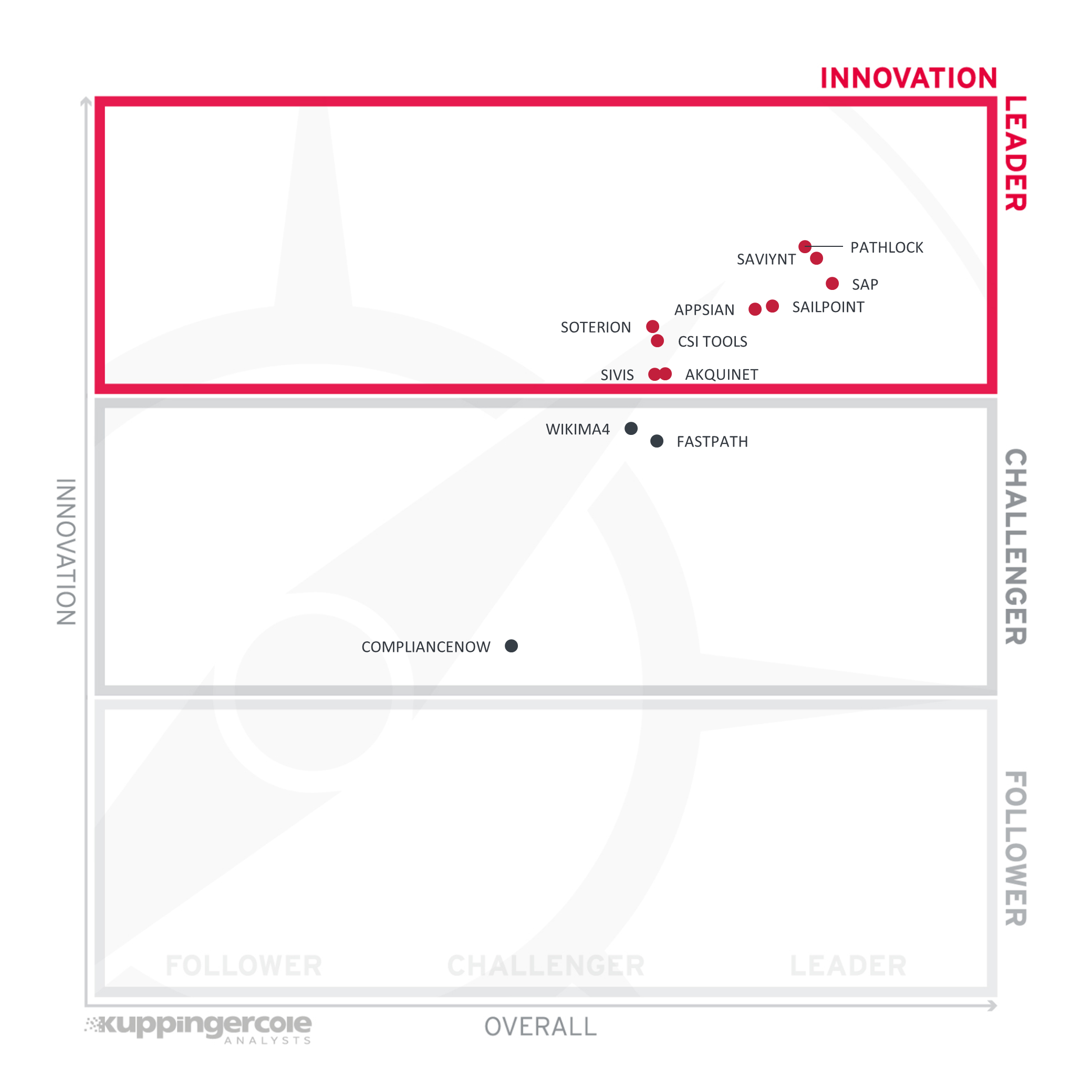
While the market for solutions for managing access controls had been quite stable for some time, this is changing, with the need for supporting a broader range of LoB applications, beyond just traditional SAP systems, and the growing demand for modern deployment models and user interfaces.
The pressure on vendors to innovate is significant, and we see many vendors responding to this. Thus, there are many vendors, who have earned an Innovation Leader's rating in this edition of the Leadership Compass.
Pathlock, closely followed by Saviynt and SAP, takes the lead. Following them is a close group of other vendors, with SailPoint, Appsian, and CSI tools, and Soterion. SIVIS, and Akquinet also have entered the Innovation Leader's segment.
The other vendors are placed in the Challenger's section, with Wikima4 and FastPath being close to the top of this segment. ComplianceNow with their focus on addressing the known demand in traditional SAP environments is following them.
Innovation Leaders (in alphabetical order):
- Akquinet
- Appsian
- CSI tools
- Pathlock
- SailPoint
- SAP
- Saviynt
- SIVIS
- Soterion
2.4 Market Leadership
Lastly, we analyze Market Leadership. This is an amalgamation of the number of customers, number of transactions evaluated, ratio between customers and managed identities/devices, the geographic distribution of customers, the size of deployments and services, the size and geographic distribution of the partner ecosystem, and financial health of the participating companies. Market Leadership, from our point of view, requires global reach.
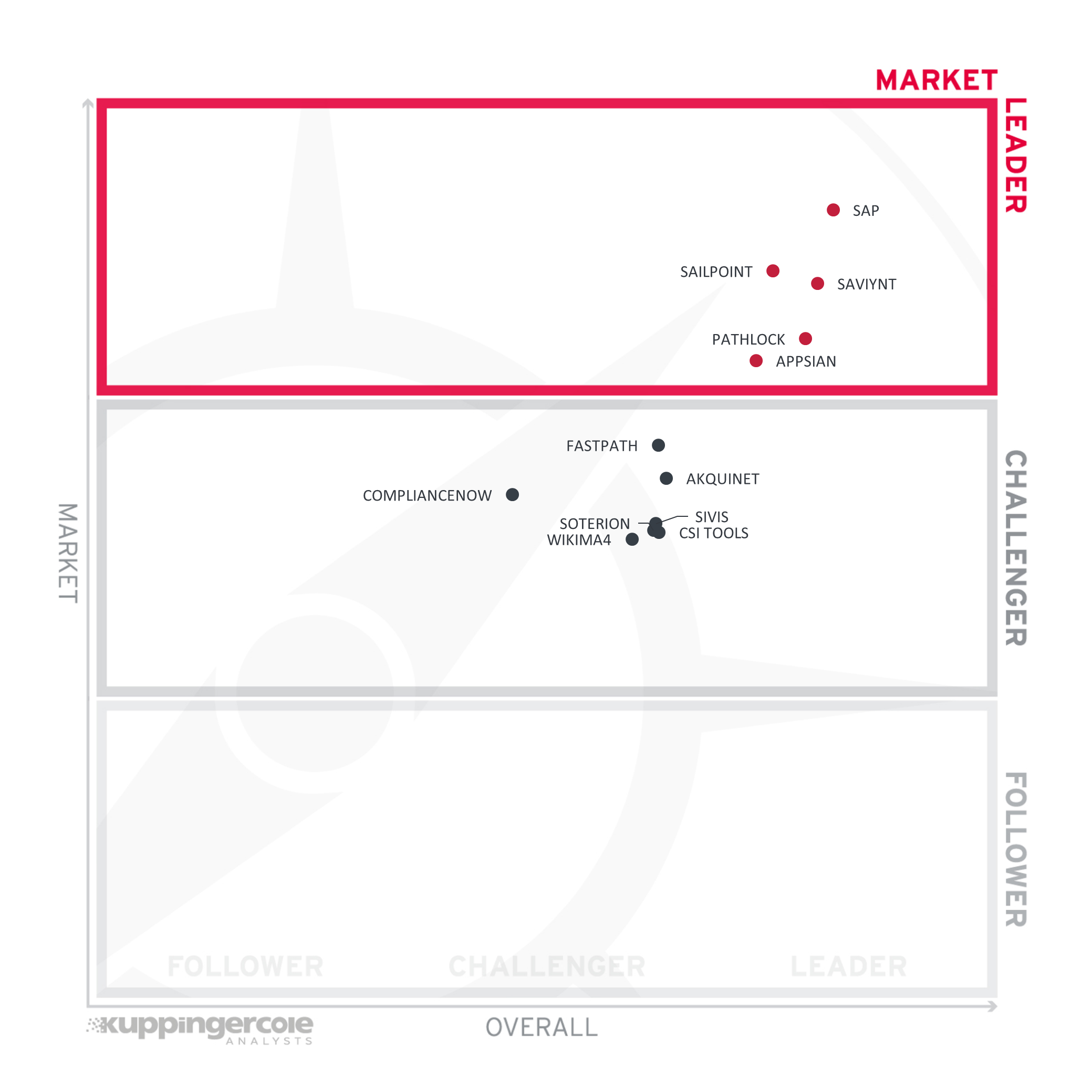
In a market with, historically, one dominating vendor and many specialized vendors, the Market Leader's segment is not as crowded as in other market segments. However, with the market entry of larger vendors from the IGA space as well as an increase in engagements of financial investors, plus the change of the market from a SAP-only focus to supporting more heterogeneous LoB environments, this is about to change.
In the Market Leader's segment, we find SAP ahead of the other vendors. SailPoint and Saviynt, both being leading vendors in the IGA market and now providing offering for the market segment in scope, are following, having a broad global partner ecosystem in place. Pathlock and Appsian as specialists for this particular market also made it into the Market Leader's segment.
All other vendors are placed in the Challenger's segment, with Fastpath on top, and the other vendors all being grouped closely, with (in alphabetical order) Akquinet, CSI tools, ComplianceNow, SIVIS, Soterion, and Wikima4.
Market Leaders (in alphabetical order):
- Appsian
- Pathlock
- SailPoint
- SAP
- Saviynt
3 Correlated View
While the Leadership charts identify leading vendors in certain categories, many customers are looking not only for a product leader, but for a vendor that is delivering a solution that is both feature-rich and continuously improved, which would be indicated by a strong position in both the Product Leadership ranking and the Innovation Leadership ranking. Therefore, we provide the following analysis that correlates various Leadership categories and delivers an additional level of information and insight.
The first of these correlated views contrasts Product Leadership and Market Leadership.
3.1 The Market/Product Matrix
In this perspective, we compare the positioning of vendors regarding their market position and the rating in Product Leadership.
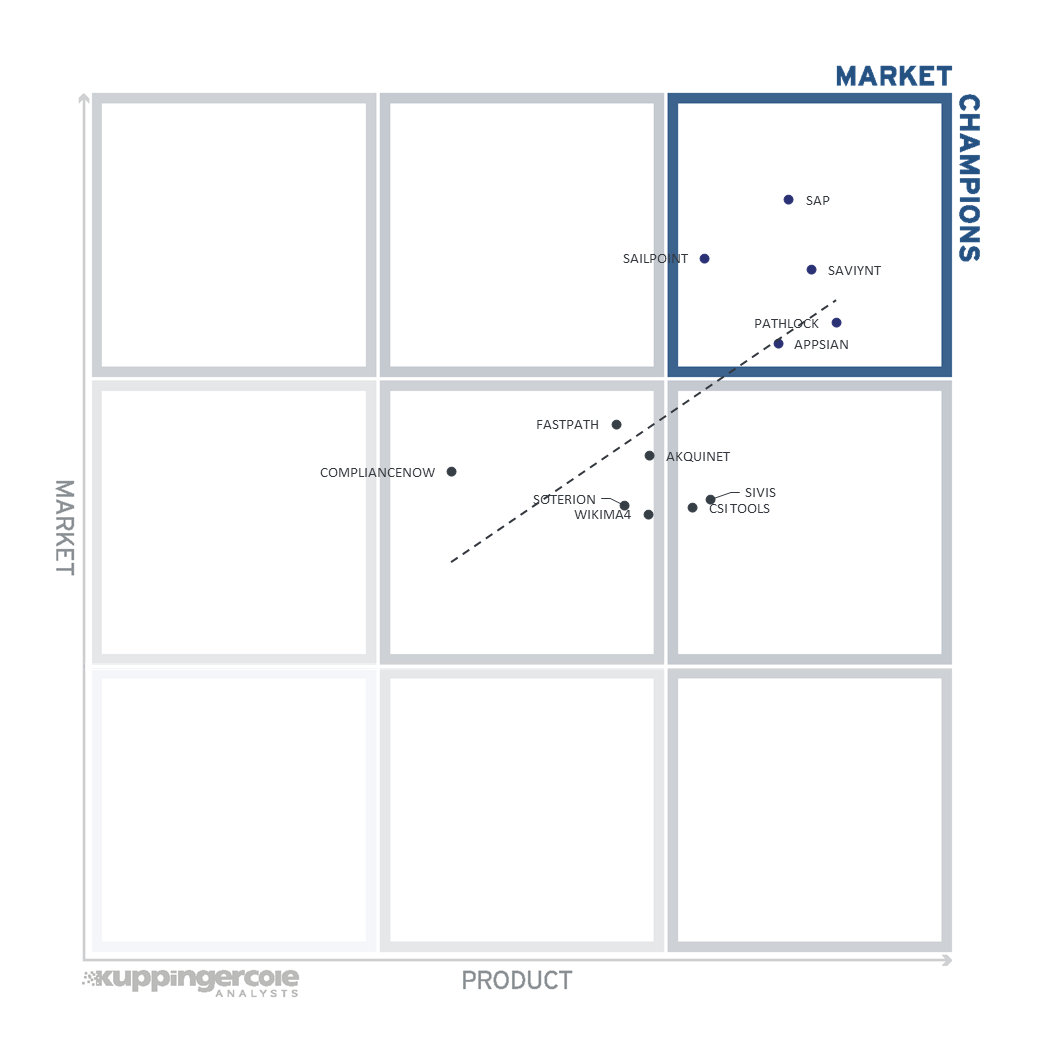
Vendors below the line have a weaker market position than expected according to their product maturity. Vendors above the line are sort of "overperformers" when comparing Market Leadership and Product Leadership.
All the vendors below the line are underperforming in terms of market share. However, we believe that each has a chance for significant growth.
The graphic shows an, overall, good level of correlation. In the upper right segment, we find SAP, SailPoint, and Saviynt benefiting from their strong market presence and ecosystem. In the centre, ComplianceNow has a significant market share due to their good market share in traditional SAP environments. Towards the right sight of the centre segment and in the segment to the right, we find Soterion, WIkima4, SIVIS, and CSI tools that have a significant potential for growth, based on the state of their products.
3.2 The Product/Innovation Matrix
This view shows how Product Leadership and Innovation Leadership are correlated. It is not surprising that there is a pretty good correlation between the two ratings. The distribution and correlation are tightly constrained to the line, with a significant number of established vendors plus some smaller vendors.
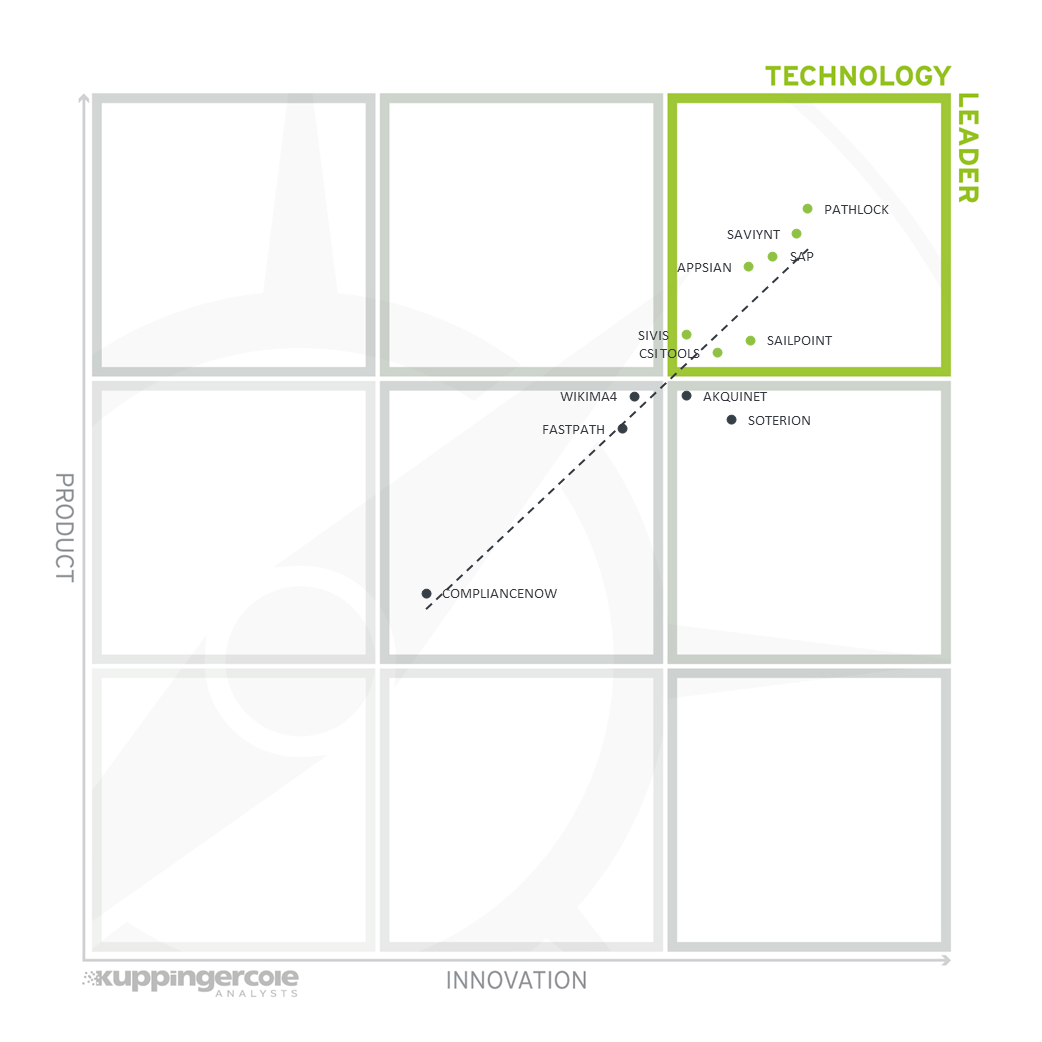
Vendors below the line are more innovative, vendors above the line are, compared to the current Product Leadership positioning, less innovative.
It is not surprising to see such good correlation, because innovation contributes to the product rating, but vendors that are already providing strong capabilities in their products also tend to be more innovative, being able to focus on innovation instead of catching up with the leading vendors.
3.3 The Innovation/Market Matrix
The third matrix shows how Innovation Leadership and Market Leadership are related. Some vendors might perform well in the market without being Innovation Leaders. This might impose a risk for their future position in the market, depending on how they improve their Innovation Leadership position. On the other hand, vendors who are highly innovative have a good chance for improving their market position. However, there is always a possibility that they might also fail, especially in the case of smaller vendors.
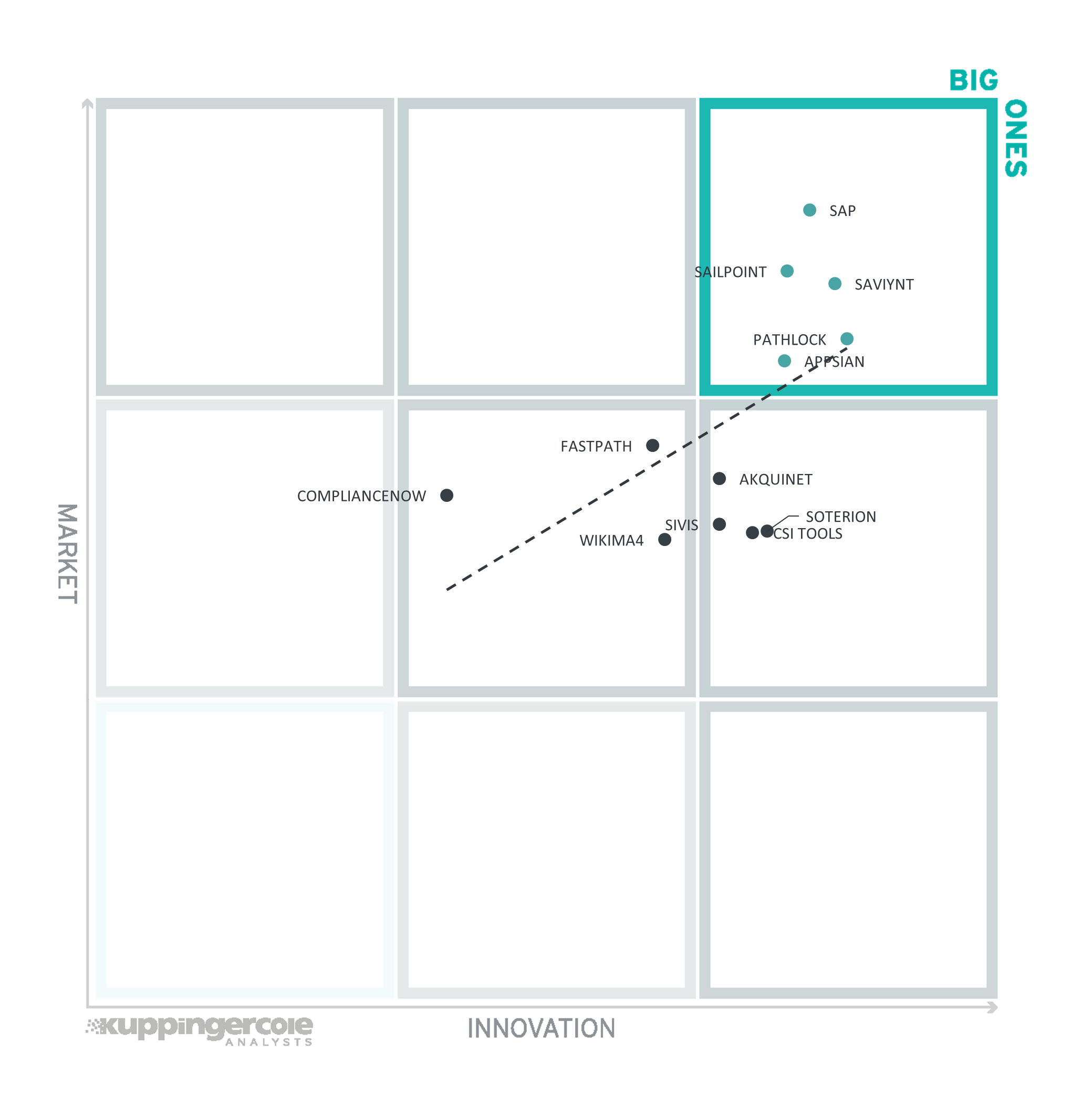
Vendors above the line are performing well in the market as well as showing Innovation Leadership; while vendors below the line show an ability to innovate though having less market share, and thus the biggest potential for improving their market position.
Due to the strong correlation of Product Leadership and Innovation Leadership, this matrix provides, altogether, a rather similar perspective as the Market/Product matrix. In the upper right segment, we find SAP, SailPoint, and Saviynt having a very good market position due to their size, number of customers, and global ecosystem.
In the center, we find ComplianceNow performing well in the market with their focus on traditional, SAP-centric use cases, while some other vendors in this segment and the segment to the right of the center, i.e., Wikima4, Soterion, SIVIS, and CSI tools, show a strong potential for future growth based on their innovativeness.
4 Products and Vendors at a Glance
This section provides an overview of the various products we have analyzed within this KuppingerCole Leadership Compass on Access Control Solutions for SAP and other Business Applications. Aside from the rating overview, we provide additional comparisons that put Product Leadership, Innovation Leadership, and Market Leadership in relation to each other. These allow identifying, for instance, highly innovative but specialized vendors or local players that provide strong product features but do not have a global presence and large customer base yet.
Based on our evaluation, a comparative overview of the ratings of all the products covered in this document is shown in Table 1.
| Product | Security | Functionality | Interoperability | Usability | Deployment |
|---|---|---|---|---|---|
| akquinet SAST Suite |  |
 |
 |
 |
 |
| Appsian Security |  |
 |
 |
 |
 |
| Compliance Now |  |
 |
 |
 |
 |
| CSI tools GRC Suite |  |
 |
 |
 |
 |
| Fastpath Assure |  |
 |
 |
 |
 |
| Pathlock Control Platform |  |
 |
 |
 |
 |
| SailPoint Access Risk Management |  |
 |
 |
 |
 |
| SAP Access Control & Identity Access Governance |  |
 |
 |
 |
 |
| Saviynt Security Manager |  |
 |
 |
 |
 |
| Sivis Suite |  |
 |
 |
 |
 |
| Soterion SAP Access Risk Manager |  |
 |
 |
 |
 |
| wikima4 mesaforte Compliance Suite |  |
 |
 |
 |
 |
Table 1: Comparative overview of the ratings for the product capabilities
In addition, we provide in Table 2 an overview which also contains four additional ratings for the vendor, going beyond the product view provided in the previous section. While the rating for Financial Strength applies to the vendor, the other ratings apply to the product.
| Vendor | Innovativeness | Market Position | Financial Strength | Ecosystem |
|---|---|---|---|---|
| akquinet |  |
 |
 |
 |
| Appsian Security |  |
 |
 |
 |
| Compliance Now |  |
 |
 |
 |
| CSI tools |  |
 |
 |
 |
| Fastpath |  |
 |
 |
 |
| Pathlock |  |
 |
 |
 |
| SailPoint |  |
 |
 |
 |
| SAP |  |
 |
 |
 |
| Saviynt |  |
 |
 |
 |
| Sivis |  |
 |
 |
 |
| Soterion |  |
 |
 |
 |
| Wikima4 |  |
 |
 |
 |
Table 2: Comparative overview of the ratings for vendors
5 Product/Vendor evaluation
This section contains a quick rating for every product/service we've included in this KuppingerCole Leadership Compass document. For many of the products there are additional KuppingerCole Product Reports and Executive Views available, providing more detailed information.
Spider graphs
In addition to the ratings for our standard categories such as Product Leadership and Innovation Leadership, we add a spider chart for every vendor we rate, looking at specific capabilities for the market segment researched in the respective Leadership Compass. For the Leadership Compass Access Control Solutions for SAP and other Business Applications, we look at the following eight categories:
- Support for SAP business applications: In this area, we focus on the support for the SAP ecosystem, encompassing both traditional SAP environments and S/4HANA as the SaaS solutions provided by SAP.
- Support for non-SAP business applications: Here, we focus on the non-SAP line of business applications such as Oracle, Salesforce, Workday, and others, and the level of integration provided for these LoB solutions.
- Entitlement & Risk Analytics: The focus in this area is on the analytical capabilities for the state of entitlements and risk, i.e., identifying critical assignments of entitlements and other risks.
- Role & Entitlement Management: Managing roles and entitlements is another key capability of solutions, including support for role modeling and other related capabilities.
- SoD Controls Management: In this area, we focus on the level of management provided for SoD controls and critical access. This also covers aspects such as the rule books provided for SoD matrixes or critical access.
- User Lifecycle Management: Managing the users lifecycle and accounts in the systems as well as integration to IGA solutions is another set of capabilities we are rating.
- Emergency Access Management: Managing, controlling, and analyzing firefighter access also counts amongst the common and expected capabilities of solutions in this market segment.
- Advanced Capabilities: This is an amalgamation of various other capabilities extending the core scope of this analysis, such as system hardening, data governance, and other features.
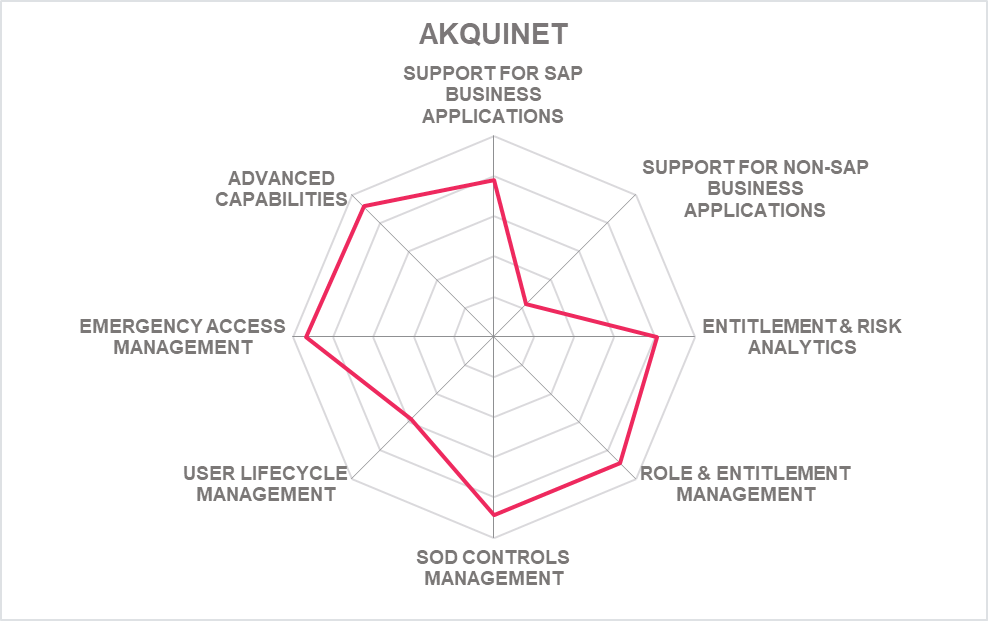
5.1 akquinet - SAST Suite
Akquinet is a German software vendor, consultancy, and managed services provider focused on the SAP market. They have developed their own solution for managing access control and identities, platform security, and security monitoring in SAP environments, providing one of the most comprehensive solutions, when it comes to SAP integration, in this market segment with their SAST Suite.
SAST Suite is structured into three areas, Platform Security, Security Intelligence, and Identity and User Access Management. The latter is in scope of our ratings. However, some aspects of their security capabilities also have a direct impact on access controls, such as events and alerts from the critical events monitoring in contrast to interval-based and thus infrequent access reviews.
The platform is tightly integrated with SAP Business Suite and S/4HANA, supporting all current versions. It runs as SAP Add-On. Most capabilities also are available via Fiori tiles. The SAST Suite still is limited in the support for other SaaS-based SAP business applications, with Ariba being implemented and SucccesFactors on the roadmap, or business applications provided by other vendors. Integration to non-SAP systems is already supported via APIs.
Within the Identity and User Access Management capabilities, SAST Suite comes with a range of modules for managing authorizations, user access and lifecycles, roles, and superuser (emergency) access. Additional capabilities include support for efficient go-live-management e.g., of updates, and read access monitoring of HCM data.
SAST Suite comes with more than 4,000 automated checks plus additional information, but also a range of rule set for authorizations including role templates. These are based on the long experience of SAST in SAP security consulting. Other capabilities include logging of downloads, incident information, and others. Most parts of the user interface are still in traditional SAP GUI layout, with some Fiori-based dashboards. Strategy is to gradually modernize the UI.
Akquinet SAST Suite counts amongst the leading solutions in this market segment when the focus is primarily on SAP environments, offering a broad range of features. Akquinet is expanding within Europe and beyond, but still has only a small partner network. We recommend Akquinet growing their partner network in other geographies, modernizing their user interface, and broadening support for non-SAP business applications.

| Ratings | Security |  |
| Functionality |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Deployment |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
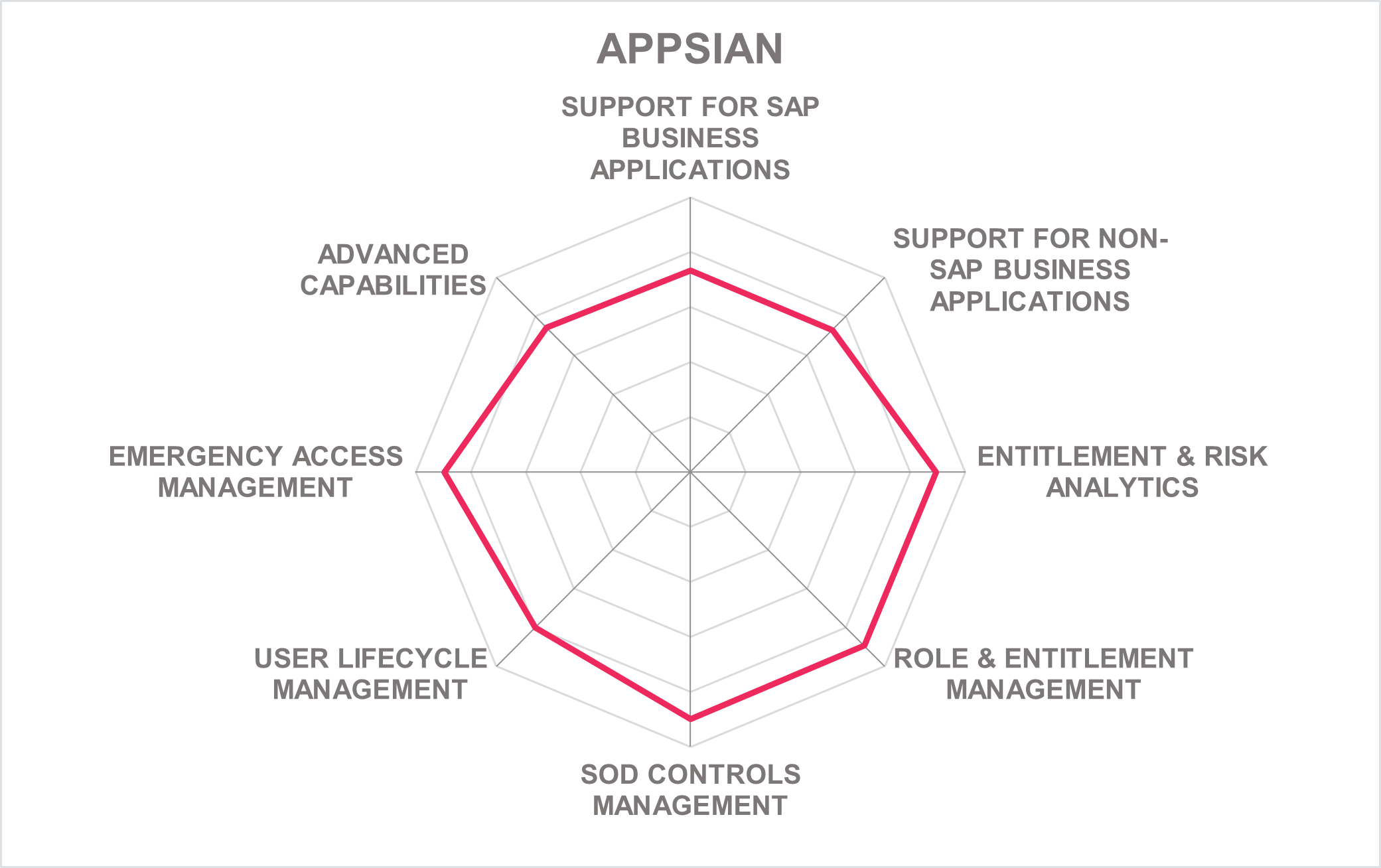
5.2 Appsian Security - ProfileTailor
Appsian has acquired Xpandion. It provides GRC solutions for SAP and other business applications as well as IAM capabilities, cybersecurity and fraud management capabilities, and license management as part of its broad portfolio of solutions. This includes the capability of managing not only SAP environments, but a range of other solutions including non-Line of Business applications such as Microsoft Office 365, with an extensive set of features.
The solutions come with a modern web-based user interface, allowing easy access to all capabilities. These include e.g. SoD monitoring and the management of SoD rule sets, even across multiple applications. Appsian's ProfileTailor allows harmonizing terminology across applications, simplifying use by end users, managers, and auditors, when it comes to requesting, approving, and managing access across various applications.
Other capabilities include managing emergency access to SAP environments, authorization reviews, and HCM specific capabilities such as restricting read access to exports from HCM systems. Other features include securing the SAP environments, license management and a range of other capabilities. ProfileTailor also supports a range of capabilities based on AI (Artificial Intelligence) and ML (Machine Learning). These include, amongst others, the analysis of user behavior and providing recommendations, e.g., for role design. It allows for continuous monitoring of risks.
Appsian offers hosted deployments as well as local installs of ProfileTailor and is investing into a unified platform that supports both on-premises and cloud deployments. While the partner ecosystem is rather small, the company provides services in all major regions, thus being able to serve also large multi-national corporations.
The solution is well-thought-out and proven and, as mentioned below, easy-to-use also in comparison to many of the other products in this market segment. In sum, Appsian ProfileTailor counts amongst the leading-edge products for managing access in SAP environments and beyond.

| Ratings | Security |  |
| Functionality |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Deployment |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
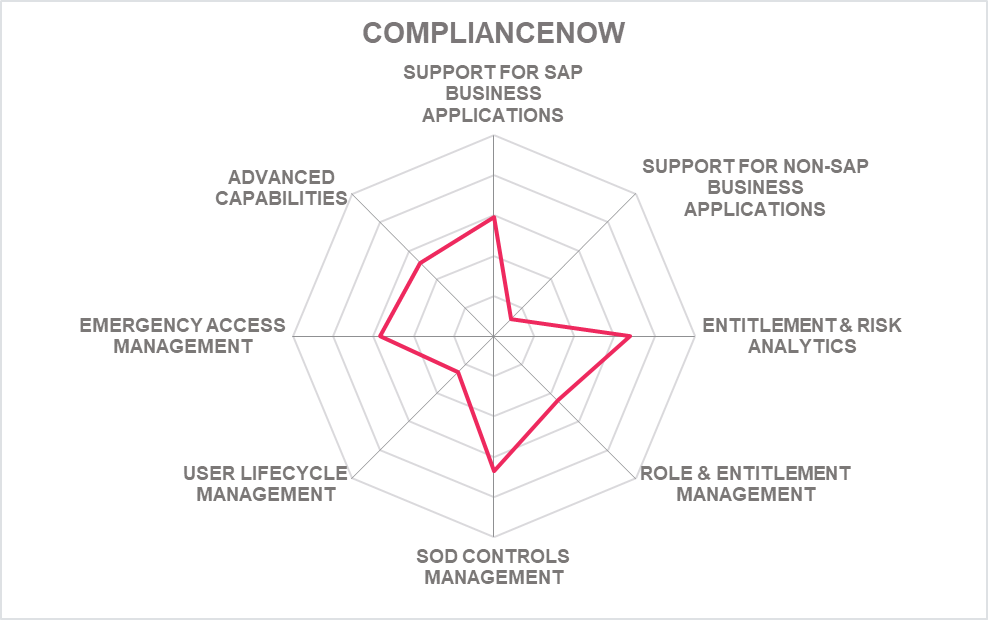
5.3 Nagarro - ComplianceNow
ComplianceNow is a unit of Nagarro ES. The solution was created back in 2008 and focuses on the core SAP platforms ECC and S/4HANA. It is built in a mix of SAP Add-Ons and an external application server. This allows the solution for being delivered as SaaS, where all communication from the internal SAP systems is outbound to the application server, but never inbound from an external entity to the SAP systems.
The solution covers a broad range of capabilities, ranging from access control and emergency user access to internal controls, testing and management for process authorizations, usage monitoring, and self-service password reset. ComplianceNow is delivered with a risk library. The risk management capabilities also support solutions that are outside of the core focus and is positioned as an alternative to SAP Process Control. Risks are managed manually.
The user interface is primarily based on SAP GUI, with ComplianceNow being focused on customers that primarily use SAP systems. It supports them in improving the authorization concepts and user provisioning as well as emergency access concepts and SoD management. Features include role simulation, license impact analysis based on roles, and various other solutions.
The firefighter/emergency access capabilities also are focused on the SAP ABAP core. It supports starting emergency sessions, automatically closing such sessions, and auditing the session based on the relevant SAP logs.
Support for other systems is currently lacking. Nagarro intends adding support for SAP SaaS solutions such as SuccessFactors, Concur, or Ariba based on customer request. Roadmap planning also includes increased support for Fiori.
Nagarro offers a rapid deployment approach for ComplianceNow based on fixed price installations. This allows for a fast installation of the solution in SAP environments, demonstrating the strength and experience of the vendor in these environments. As one of the solutions in the market targeted at the core SAP environments and partially relying on SAP Add-Ons, it is well-suited for organizations that rely heavily on SAP, but are noch focusing on support for SaaS services or non-SAP line of business applications.

| Ratings | Security |  |
| Functionality |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Deployment |  |
| Strengths |
|
| Challenges |
|
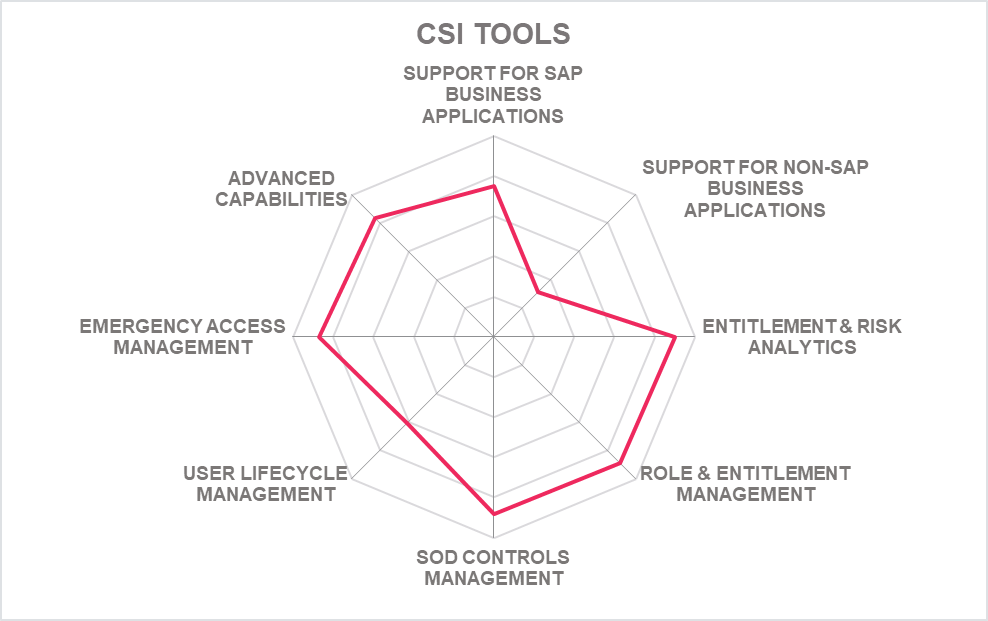
5.4 CSI tools - GRC Suite
CSI tools is a specialized provider of software solutions for access control and audit in SAP environments, based in Belgium. They offer a range of modules for providing access control and governance for SAP environments, targeting SAP Business Suite and S/4HANA. However, the solutions run as external applications on Windows servers. All solutions are offered as on-premises applications as well as cloud solutions.
CSI tools provides a set of modules covering the core requirements for access control in SAP environments. CSI Authorization Auditor is the main product, being used for analyzing the current state of authorizations in SAP environments and identifying weaknesses in the authorization concept such as the accumulation of access rights and SoD conflicts.
With CSI Automated Request Engine, there is added support for access request & approval workflows, including SoD checks and fulfillment in the supported SAP systems. This adds to the security by moving from manual fulfillment to automated processes. The workflow can also be integrated with other workflow and IGA solutions such as SAP, SailPoint IdentityIQ, Omada, or ServiceNow. CSI Role Build & Manage supports the role creation and management process, as well as automated assignments of entitlements, e.g. when onboarding large numbers of users.
Further modules support emergency requests, privileged access management, automation, and data extraction from SAP platforms. The solution also allows for migrating security concepts to S/$ HANA. As mentioned above, CSI tools works with a separate solution not running within the SAP environment, but interfacing with the SAP environments via the defined APIs.
CSI tools focuses on providing a holistic perspective and analysis on access entitlements in SAP environments. They provide insight into who finally can access which data and perform which activities, by understanding, analyzing, and optimizing the complex relationship between transaction codes, authorization objects, and the various applications within the SAP environment. This reflects the reality of having various access paths to the same ABAP code, transactions, and data. At the center of the analysis are authorization objects, which map all elements and thus must be analyzed, beyond just restricting the use of transaction codes.
CSI tools provides a solution for managing access controls and user access in SAP environments that is targeted at the key requirements. It is easy to install and can be quickly used for both audits and continuous management of authorizations in the traditional SAP environments, as well as for S/4HANA. Out-of-the-box support for SAP cloud services beyond S/4HANA or other vendor's solution is lacking, but a connector kit is available for integration to other services.
CSI tools comes with an efficient, modern architecture and rapid deployment of new releases. Beyond that, CSI tools has converged various of the former components into a smaller set of solutions, which again are tightly integrated. In sum, CSI tools delivers a modern, efficient solution approach on managing access controls and SoD rules for SAP environments, with a strong and modern user experience.

| Ratings | Security |  |
| Functionality |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Deployment |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
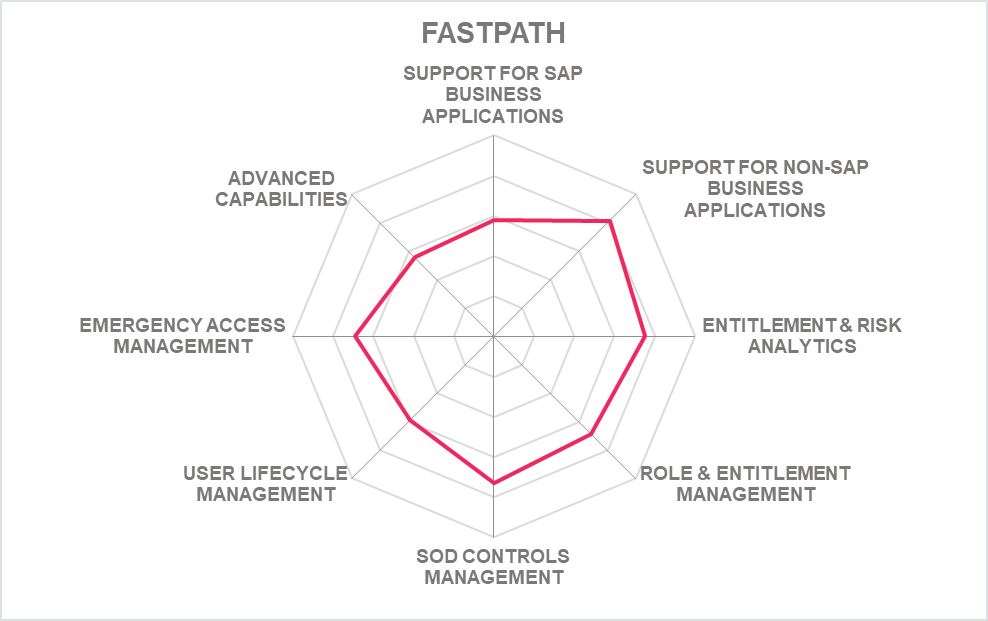
5.5 Fastpath - Assure
Fastpath provides a compliance platform that, in contrast to many of the other offerings in the market, has a core focus on cross-application capabilities. Within the solutions in this market segment that are covered in this document, Fastpath Assure counts amongst the vendors delivering the broadest support for non-SAP systems, but also good capabilities for SAP environments. The company is backed by private equity funding and shows strong growth.
Fastpath Assure provides a range of features, including access certifications, access approvals, audit analytics, the analysis of SoD conflicts, and user provisioning from Microsoft Active Directory. As indicated, these capabilities are not only available for SAP environments, but for a comprehensive list of business systems, including such as Oracle eBusiness Suite, Salesforce, ServiceNow, Microsoft Dynamics, and many more.
For access control and management within SAP environments, Fastpath Assure comes with a good set of capabilities that cover all common requirements. This includes pre-defined rule sets for SoD controls for the SAP Business Suite as well as for S/4HANA and Fiori. Fastpath Assure also supports mapping access controls to business processes. Simulation of changes to access entitlements is supported for SAP and various others of the supported systems.
Fastpath Assure delivers good capabilities for SAP environments, even while sometimes lacking the level of depth some of the specialized vendors are delivering. Integration to SAP is done via the common interfaces, but also – where required – via ABAP components. It also supports a range of innovative capabilities such as a Custom Code Checker for review custom codes in the context of access controls, and strong support for managing Fiori environments.
The solution is provided as a SaaS solution, allowing rapid deployment and easy interoperability with the various business applications that shall be managed. However, customers can opt for an on-premises deployment. The user interface is leading-edge in this market segment.
Fastpath Assure is a solution that reflects the evolution of the market for business software towards a more flexible use of SaaS solutions provided by different vendors. For businesses that run a heterogeneous set of business applications, this solution is well-suited. However, it also provides a good foundation for SAP-centric businesses, specifically when these are opening up towards other providers of SaaS solutions.

| Ratings | Security |  |
| Functionality |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Deployment |  |
| Strengths |
|
| Challenges |
|
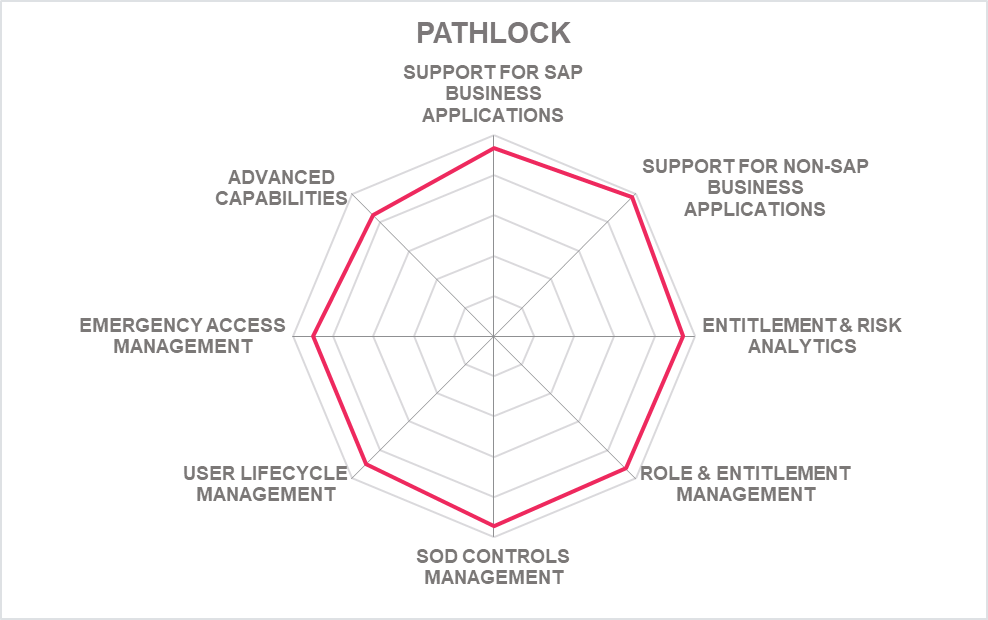
5.6 Pathlock - Control Platform
Pathlock is probably known to most as Greenlight GRC. The company has changed its name a while ago and extended its product portfolio from delivering integration between SAP Access Control and non-SAP line of business applications to a broader set of offerings, comprising the Control Platform as an access control solution for both SAP and non-SAP environments. Pathlock is backed by Venture Capital and has shown strong growth in the recent years.
Pathlock provides support across a range of areas, from access analytics and user management to governance capabilities. The areas include User Lifecycle Management, automated provisioning and access request & approvals, privileged access management, and cross-application SoD controls. It also covers user behavior analytics and risk scoring of applications. Additionally, Pathlock also supports data governance with features such as dynamic data masking and data access management.
A well-known strength of Pathlock is their broad support for business applications beyond the SAP ecosystem, with a coverage of over 140 applications. It can monitor the user activity and risk across these applications continuously and alert on actual violations. It also maps data to business applications.
The solution comes with a modern user interface and dashboards. It is deployed as SaaS service. Risk mitigations can be handled by transaction monitoring controls, which can be enforced for defined periods across all systems.
Aside of providing a stand-alone solution, Pathlock continues to integrate and extend SAP Access Control and SAP Process Control, giving customers the choice over their preferred approach. For mixed environments, a Fiori-style interface is provided as well.
Recently, Pathlock also has announced a partnership with Microsoft for extending Microsoft Azure Active Directory to line of business applications and providing SoD across all supported solutions. This allows managing, e.g., access in SAP environments down to authorization objects and transaction codes.
Pathlock has evolved from a partner delivering added capabilities to SAP Access Control to a major player in this market, delivering broad support across a wide range of applications and a broad set of capabilities.

| Ratings | Security |  |
| Functionality |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Deployment |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
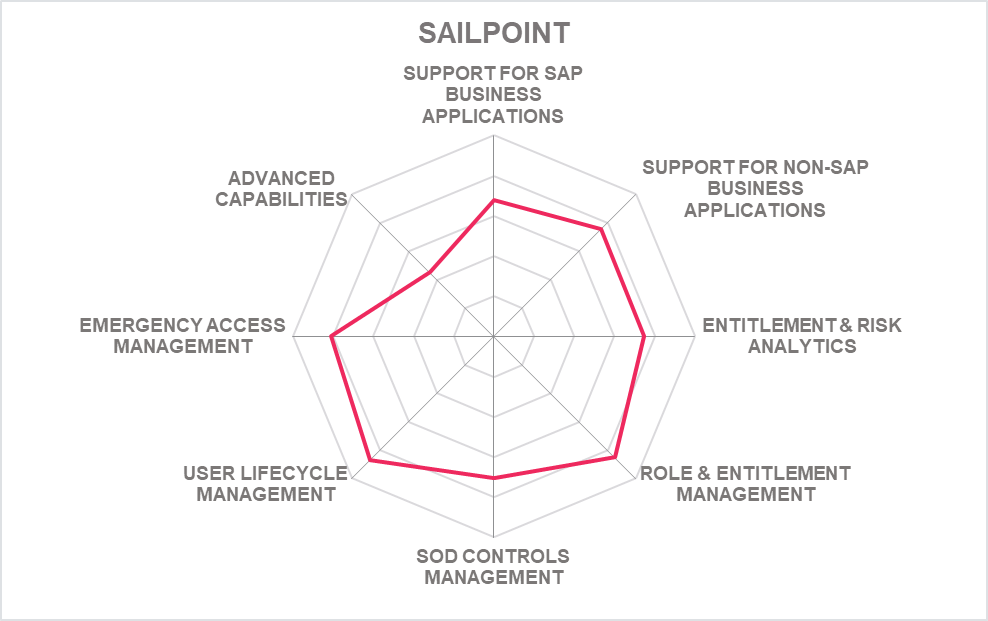
5.7 SailPoint - Access Risk Management
SailPoint Access Risk Management is a solution for managing users, their access entitlements, and the related access risk across a range of Line of Business applications, including SAP. SailPoint Access Risk Management delivers in-depth control about these environments, but also integrates neatly with the IGA (Identity Governance & Administration) solutions provided by SailPoint for cross-system controls across the entire breadth of critical business applications.
SailPoint Access Risk Management delivers a series of capabilities, centered around three main areas. Unified Risk Management focuses on delivering comprehensive insights across all types of applications and unifying ARM and SoD management with IGA across various LoB (Line of Business) applications and beyond. Enterprise-wide visibility is closely related to Unified Risk Management, but focuses on multi-application SoD controls and risk visibility, as well as cross-application risk simulation ahead of granting access. Compliance and Audit delivers unified access reviews and reporting across the full range of applications complements the proactive parts of SailPoint ARM.
As it is common for modern solutions, the entry point for users are dashboards, delivered as pre-defined part of the SaaS solutions. These dashboards allow for drill-down into details, can be filtered and flexibly customized. Thus, users at various levels, be it more technically oriented application owners, risk managers, or managers, can get the insights they require to understand the risk status and posture for LoB applications and beyond.
For some of the LoB applications such as SAP ECC, there are out-of-the-box rule books with audit-compliant controls, allowing for a quick start in implementing SailPoint Access Risk Management. For Access Review, SailPoint Access Risk Management supports common review campaigns, but also dashboards for administrators, risk managers, and reviewers showing the status of current review campaigns. Being an Access Risk Management solution focusing on LoB applications, there is also the depth for reviews at various levels, such as roles, transaction codes, or risks, including contextual enrichment features that inform the reviewer of actual usage and a simulated impact on risk should the access in question be removed.
Last not least, SailPoint Access Risk Management benefits from the analytics capabilities of the SailPoint Identity Platform. It delivers advice for remediations, allows to discover risks from various perspectives such as roles, users, or business processes, and immediately identifies SoD conflicts.
Regarding support for other LoB applications, the main focus for now is on ABAP-based SAP applications and SuccessFactors, plus the SAP S4/HANA environment. Other applications including Oracle EBS (Enterprise Business Suite), Workday, Salesforce, or ServiceNow are currently added to the list. Additionally, the SailPoint Identity Platform provides integration to the full range of other business applications via their native connectors., thus delivering capabilities, e.g., for user lifecycle management and baseline access risk management to a broad variety of products. We expect to see a significant broader native in-depth support for LoB applications in the SailPoint ARM solution, building on the experience in both IGA and Access Risk Management coming together.
The solution is of specific interest to organizations looking for deeper integration between the management of risks in line of business applications, and between cross-platform IGA solutions.

| Ratings | Security |  |
| Functionality |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Deployment |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
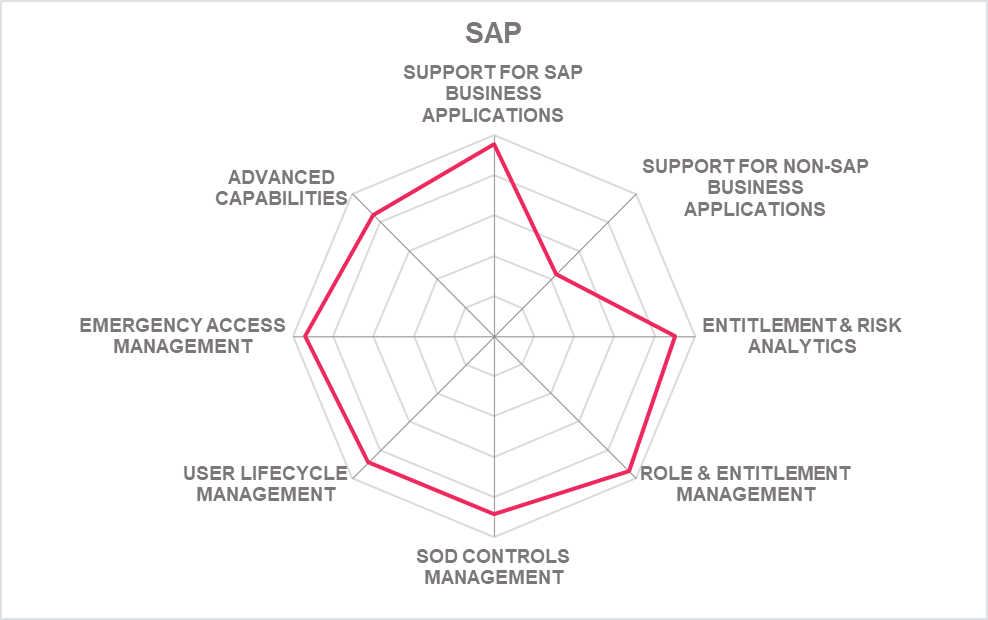
5.8 SAP - Access Control & Identity Access Governance
SAP Access Control is the market-leading solution in the market for access control solutions for SAP environments – which is not a surprise given that it is SAP's own solution in this market segment. SAP Access Control is complemented and can be also replaced by SAP Identity Access Governance (IAG), which adds support for other SAP SaaS services. Customers currently have the choice between both solutions, with SAP IAG being the solution that is easier to customize and to extend towards other platforms.
SAP Access Control comes with strong support for all major features to be expected in that type of solutions. It provides support for managing roles and authorization objects, has strong features in SoD management, and provides proven emergency access/firefighter support. SAP Cloud IAG comes with a rather similar set of features, but provided in a SaaS deployment model and simpler in configuration and customization. New features include capabilities such as a workflow designer for access requests or the ability for linking request tickets to firefighter log entries for review.
The solutions also integrate with SAP Identity Management for user lifecycle management and with other solutions of the SAP GRC solutions for managing risks. For integration with SAP SaaS solutions such as SuccessFactors, it requires SAP IAG. This might cause the need for upgrading to the latest version of SAP Access Control, which requires customers to operate a mixed environment of SAP solutions.
SAP as the undisputed market leader has the largest partner ecosystem of all vendors in that market segment, providing services in every region globally. This differentiates SAP from many other vendors that are limited to certain regions.
SAP Access Control and SAP IAG as the solutions provided by SAP itself are a logical option for any shortlist in this market segment. While SAP Access Control counts amongst the more heavyweight solutions, SAP IAG as a SaaS services provides simplified deployment and customization. A major challenge for the SAP solutions is their limited support for non-SAP business applications. However, aside of relying on partners such as PathLock (formerly Greenlight GRC), SAP has added additional integration points to SAP Cloud IAG, such as the SCIM (System for Cross-Domain Identity Management) support and an API library for easier integration with other applications. Both SAP solutions can work together seamlessly.

| Ratings | Security |  |
| Functionality |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Deployment |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
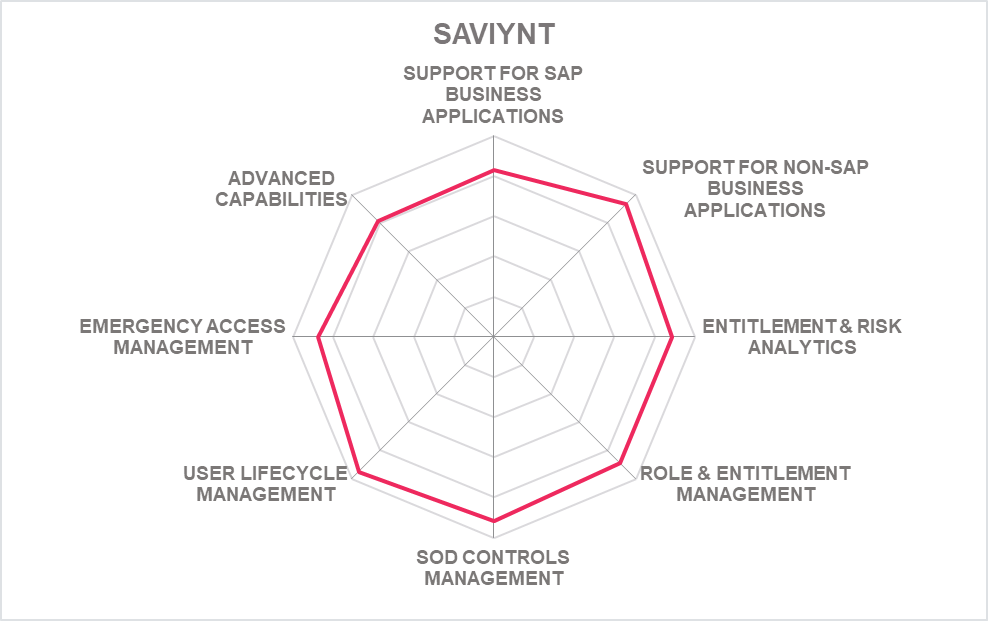
5.9 Saviynt - Security Manager
Saviynt differs from most other vendors in this market segment by their focus on delivering security and access governance solutions for a broad variety of systems, including full support for IGA (Identity Governance and Administration). However, they provide also in-depth support for SAP environments, qualifying them for this analysis. Saviynt provides it solutions as SaaS service, but also allows them being run in other deployment models.
As a provider of a solution that supports the full breadth of IGA capabilities, Saviynt supports a broad set of target environments. SAP is only one of these. However, Saviynt comes with deep expertise and integration for SAP environments, provided in their specific Saviynt for SAP solutions.
Features include pre-defined controls for compliance management, role management and role engineering, and other capabilities. Support is provided for all levels of SAP authorizations and access controls down to transaction codes, i.e., not limited to the high-level business role view most other IGA tools provide. They deliver preventative risk analysis for access provisioning. Saviynt also supports access reviews and can manage temporary, just-in-time (JIT) assignments of entitlements, in contrast to common standing privileges.
Out-of-the-box rule sets are provided for a range of business applications, including SAP, Oracle, Infor, Epic, and Microsoft Dynamics. Another interesting capability is their support for activity monitoring, allowing to implement a CCM approach, also based on out-of-the-box controls for a range of regulations where Saviynt delivers up to the minute status information.
Furthermore, Saviynt comes with some advanced capabilities such as the management of SAP licenses and emergency management capabilities supporting both SAP environments and non-SAP environments, based on their privileged access management capabilities. The latter include comprehensive traceability of firefighter access. However, in contrast to some of the specialized vendors, their support for certain specialized capabilities adding to access control solutions are not their primary focus. Saviynt can address many of these use cases anyway, e.g. via reporting.
Saviynt successfully combines two sets of capabilities. On the one hand, they provide strong support for SAP specifics in access control and management. On the other hand, Saviynt is not limited to SAP environments, but delivers services for a broad range of target systems, plus comprehensive IGA capabilities. This allows to build a central solution for IGA and business software access control. Saviynt also excels with innovation and a strong, global partner ecosystem.

| Ratings | Security |  |
| Functionality |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Deployment |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
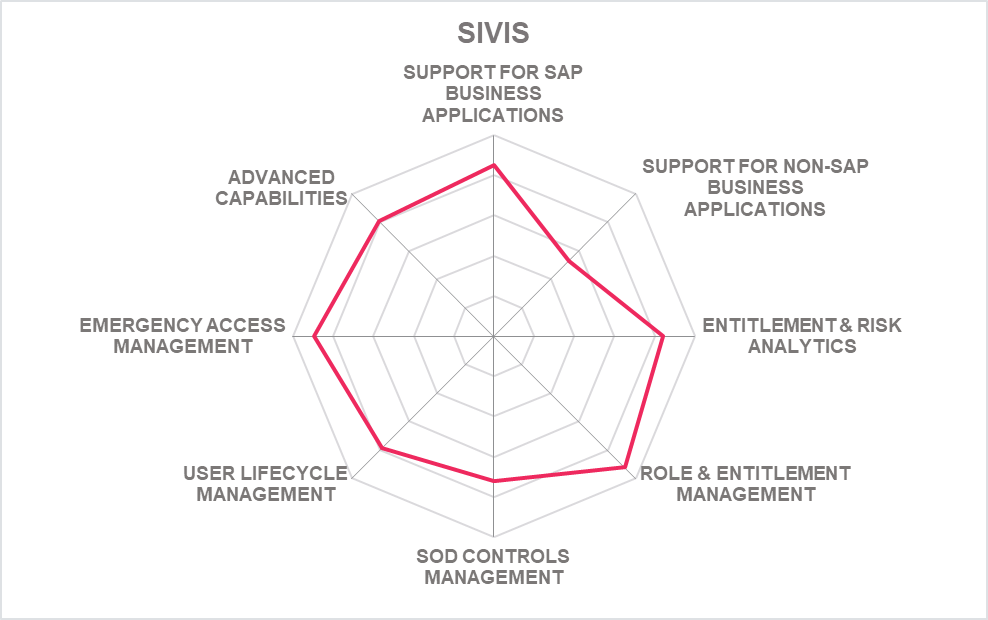
5.10 SIVIS - Suite
SIVIS is a German provider of a solution for managing access control and related settings in SAP environments, with their SIVIS Suite of products. As the name indicates, the company delivers a set of modules that can be selected by the customer depending on its requirements. The SIVIS Suite runs as a container-based solution in Docker, but still utilizes some components running in the SAP landscape and using the SAP transport system.
While having been focused on traditional SAP environments, the scope is extending beyond SAP ECC and S/4HANA. Frontends are provided as web applications, including the ones for user self-services. Furthermore, SIVIS just release a cloud connector, which allows integrating SaaS solutions as well. Available integrations include SAP Ariba and Jira, and will be further extended in future.
Overall, there are close to 20 separate modules which can be used. This includes capabilities such as the Identity Manager for managing user profiles, the Role Manager for role management including a separate module providing more than 1,000 pre-defined roles, the Compliance Manager for SoD management, altogether with pre-defined SoD controls, and many more. They also focus on optimization of entitlements in SAP environments, following a model that in future can be extended to other business applications.
Beyond the common capabilities found in most products in that market such as recertification management, alerting, and emergency access management, there are others such as the Concept Manager for automated documentation of the SAP access entitlement model. SIVIS also provides a license manager for SAP environments.
Furthermore, there are several connectors for integration with other systems for both user lifecycle management and analytics, and for integrating further SAP platforms. SIVIS Suite can work with HR systems and Microsoft Active Directory, and it can connect e.g. to SAP BI and HANA. With the new cloud connector, they also can integrate to other SaaS services of both SAP and other vendors.
SIVIS currently primarily targets the German-speaking countries, but has successfully expanded in the French speaking market over the last two years, partnering with major local SAP Partner and increasing their customer base in this region. They provide a good set of capabilities, and they are opening up from a SAP-only focus towards supporting a broader range of applications. SIVIS also comes with a well-integrated, modular and easy-to-use solution for SAP environments, providing a strong alternative to other offerings in that market.

| Ratings | Security |  |
| Functionality |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Deployment |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
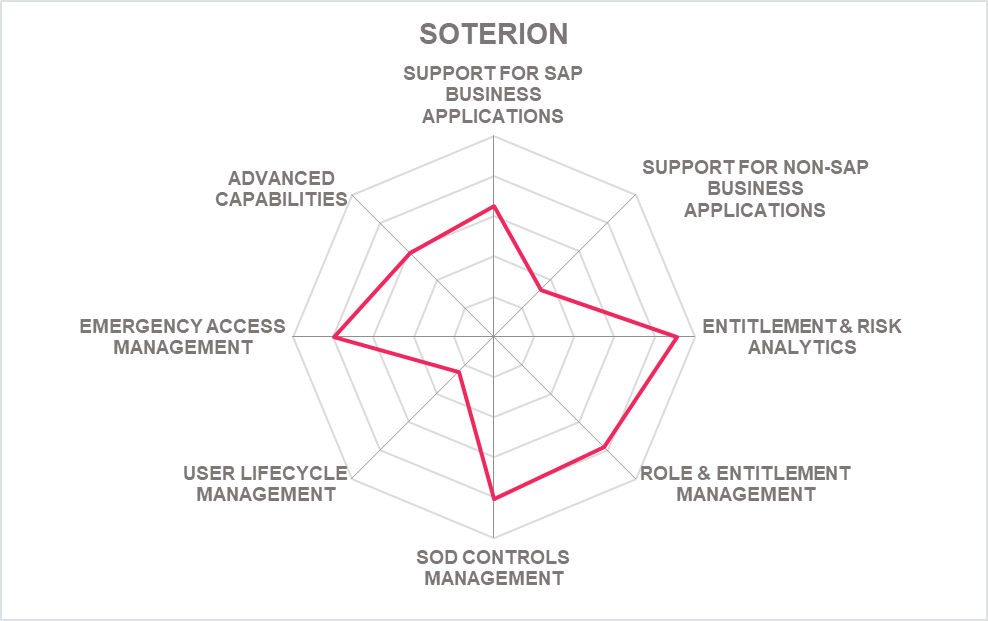
5.11 Soterion - SAP Access Risk Manager
Soterion's SAP Access Risk Managera GRC (Governance, Risk & Compliance) solution targeted at SAP environments and delivering major capabilities in that space. The solution is available as both on premises solution and in an as-a-service model. Soterion has put specific emphasis on delivering a solution for GRC and access control in SAP environments that is easy-to-use, coming with a business-friendly user interface.
Soterion is able offering this range of deployment options due to a major difference compared to several of the other vendors in the market, which is that Soterion SAP Access Risk Manager isn't an ABAP application that is locked into the SAP ecosystem, but runs as an independent application interfacing to the SAP ecosystem. This approach has the additional benefit that Soterion has far more flexibility in building a modern, intuitive, and business-centric user interface (UI). It also simplifies the extension of Soterion for SAP to other solutions, specifically the SAP SaaS services such as Ariba or SuccessFactors, which are newly supported, as there are interfaces to Microsoft Dynamics and Salesforce.
Soterion SAP Access Risk Manager consists of several modules, all sharing the same UI. The main module is the Access Risk Manager, which provides insight into current access risks in the SAP environment. It analyzes the user authorizations, also incorporating historical transaction usage data, to analyze the current status of authorization and their usage in the past. While analysis of the static authorizations within SAP environments is common, adding the historical usage data provides better insight into the real access risks, but also identifies excessive entitlements that aren't used in practice. Other important modules include the new Data Discovery and Classification module for identifying PII (Personally Identifiale Information) and other sensitive in SAP systems, and the Elevated Rights Manager for managing firefighter access. A specific strength is their ability to map risks to business process flows, so that users can easily understand where risks derive from.
All data is displayed in dashboards, supporting drag-and-drop capabilities for grouping, filtering, and re-arranging data. Thus, users can easily identify high-risk areas and other relevant information. Based on that, authorizations can be optimized. One of the capabilities of the Soterion Access Risk Manager is focused on reducing redundant access. Risk clean-up wizards support the users in mitigating access related risks, but also in optimizing the role model. The tool also provides a risk clean-up projection, indicating which amount of authorizations could be removed without impacting business operations.
Soterion SAP Access Risk Manager is a user-friendly, well-thought-out solution for managing authorizations, critical/emergency access, and licenses in SAP environments. It is targeted at efficient usage, supporting business users that don't come with a deep understanding of SAP specifics in performing both their routine jobs such as approving access as in the regular access reviews. With its innovative user interface and focus on business processes, Soterion SAP Access Risk Manager is an interesting alternative to some of the established solutions in this market segment.

| Ratings | Security |  |
| Functionality |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Deployment |  |
| Strengths |
|
| Challenges |
|
| Leader in |  |  |  |  |
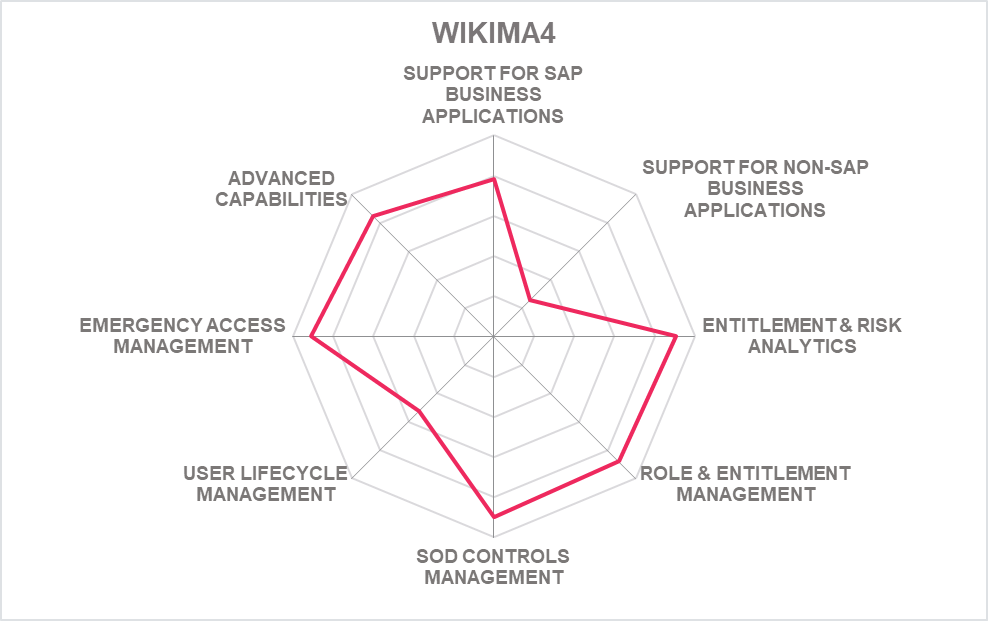
5.12 Wikima4 - mesaforte Compliance Suite
Wikima4 is a Swiss-based provider of SAP Security Consulting, also offering its own GRC and access control solution for SAP environments. The core module of what Wikima4 has named GRC-in-a-box is mesaforte Compliance Suite. Altogether with rolebee for role design and role management, the solution provides support for all core requirements we expect to see in such solutions.
While the solution is offered as an integrated suite, it consists of nine separate modules, which can be licensed separately. Wikima4 not only offers generic best practice rule sets and templates, but also industry-specific ones. This allows for more efficient implementation, because the rule sets, controls catalogs, and templates are already targeted at the specific use cases within the industries.
The modules provide range from compliance and SoD rule sets and monitoring to automated analysis and monitoring of SAP security settings, usage analysis and license optimization to a range of capabilities around managing users and their access. The latter include role design and optimization as well as temporary access, e.g., for emergency access, and automated entitlement management. Furthermore, there is module targeting the specific requirements of GDPR (General Data Protection Regulation).
Recent additions include improvements in the Compliance/SoD and the firefighter module. For compliance and SoD management, Wikima4 introduced a simulation component, an improved dashboard with drill-down functionality, and an advanced risk analysis including a wizard for efficient processing of violations. For the firefighter modules, specific emphasis was on improved forensics for identifying changes made during emergency access.
The Wikima4 solutions are tightly integrated into SAP environments and benefit from the consulting practice of the organization, such as with the industry-specific catalogs. The main focus is on traditional, homogeneous SAP environments. This might impose a restriction for customers that run an environment with a heterogeneous set of business applications, or which increasingly build on SaaS services. However, Wikima4 can integrate on demand with further applications, including homegrown applications.
The solution is focused on key requirements of customers, for rapid implementation, not overloaded with specialized capabilities. Wikima4 currently is primarily focused on the German-speaking countries, with only few customers outside that region. The partner network is very small. However, Wikima4 offers its own consulting services in their core region, being able to directly serve the customers.

| Ratings | Security |  |
| Functionality |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Deployment |  |
| Strengths |
|
| Challenges |
|
6 Vendors to Watch
6.1 EmpowerID
EmpowerID is one of several IGA vendors that provide a strong and deep integration to SAP applications and thus can provide access control, entitlement management, and risk analysis for these environments as part of their IGA offering.
Why worth watching: Option if cross-platform IGA capabilities are in focus and some good level of support or access control management for SAP is required.
6.2 IBM
IBM provides with its ISIGI (IBM Security Identity Governance & Intelligence) and cloud-based Security Verify (Identity Governance & Administration) solutions that are primarily targeted at the IAM market. However, the solutions come with well-above average capabilities in managing SAP environments, including authorization objects, and thus exceeding what is commonly found in that type of tools. With its strong support for heterogeneous environments, it might become an option to specialized solutions, despite not offering the same level of specialization.
Why worth watching: Option if cross-platform IGA capabilities are in focus and some good level of support or access control management for SAP is required.
6.3 IBS Schreiber
IBS Schreiber delivers a solution for analyzing authorizations in SAP environments with their CheckAud product. The focus is primarily on read-only access, i.e., a rapid analysis e.g. for consultants and auditors. Thus, it is not a full-featured solution for managing access controls in SAP environments. On the other hand, the product benefits from the extensive knowledge on SAP audits IBS Schreiber has accumulated since the 1990s. CheckAud is a strong solution for a rapid analysis of the status of SAP systems and for auditors that require a lean solution for either auditing SAP systems themselves or delivering the required information to external auditors. While some of the other vendors provide audit-only options, IBS Schreiber CheckAud is one of the few targeted solutions on that segment.
Why worth watching: Solution that is targeted on analyzing the security status of SAP environments and thus well-suited for audit-centric use cases.
6.4 NTT Managed Services
NTT Managed Services has acquired ControlPanelGRC from Symmetry. The product is an easy-to-use solution covering the major aspects of managing access control and access-related GRC requirements in SAP environments. It comes with a modern UI and is well-integrated into the SAP ecosystem. It also can integrate with SAP GRC solutions to complement these.
ControlPanelGRC consists of a number of modules, covering the major areas within this market segment. This includes SAP SoD Risk analysis and management of SoD controls, monitoring SAP Transaction Usage and thus adding an element of Continuous Controls Monitoring, plus using such information for SAP license management, and SAP Audit Management.
The solution also provides the full breadth of user provisioning and role management capabilities for SAP environments, as well as user access reviews. It also can integrate with SAP HCM in such processes, but also by securing HCM data in compliance with relevant regulations.
Why worth watching: Interesting alternative to the solutions in scope of this rating, in particular for customers focusing on SAP ecosystems.
6.5 One Identity
One Identity is one of several IGA vendors that provide a strong and deep integration to SAP applications and thus can provide access control, entitlement management, and risk analysis for these environments as part of their IGA offering.
Why worth watching: Option if cross-platform IGA capabilities are in focus and some good level of support or access control management for SAP is required.
6.6 Protect4S
Protect4S is a security add-on for SAP environments. The solution targets at security scans of SAP environments and lesser to the specific challenges around access controls and auditing. Protect4S can complement most of the solutions covered in this Leadership Compass with its additional capabilities.
Why worth watching: Add-on for further increasing security in SAP environments by adding scanning and analysis of security-related events.
6.7 SafePaaS
SafePaas is an established vendor in this market segment, providing good support for both SAP and non-SAP environments. A specific strength is their ability to normalize data from different sources and apply common rule sets. Additional business applications are easy to connect, and the set of out-of-the-box integrations is constantly growing.
Why worth watching: Good support for non-SAP business applications and straightforward approach for adding further integrations.
6.8 SecurEnds
Solution for analyzing and monitoring user access and entitlements, supporting capabilities such as user access reviews, access certifications, and entitlement audits for a range of applications, including Workday, PeopleSoft, Oracle, but also certain SAP components. SecurEnds is an interesting alternative specifically for customers where SAP plays a minor role in the environment, but that are focusing on modern SaaS services for delivering their business applications.
Why worth watching: Alternative to the solutions in this Leadership Compass specifically for cross-platform requirements and managing access risks in modern SaaS solutions, but also delivering some level of SAP support.
6.9 SecurityWeaver
Security Weaver is a vendor entirely focused on delivering solutions for the market of access control and compliance, with specific focus on SAP environments, but growing support for non-SAP business applications. Their solution offering also is named Security Weaver. It covers all major areas we expect to see in SAP access control. Security Weaver is focused on solving challenges of large, global customers.
Why worth watching: Strong support for SAP environments and adding more and more support for non-SAP environments. Proven support for large-scale environments.
6.10 Valantic
Valantic is a SAP consultancy and solution provider, delivering a broad range of services and solutions in the SAP market segment. With apm Suite, Valantic also offers a solution for managing authorizations in SAP environments. Other modules of apm include emergency access management, biometric access control, or password self service. Valantic apm is another solution in this market segment that might be evaluated, beyond the products covered in this Leadership Compass.
Why worth watching: Solution specialized on improving SAP entitlement management, provided by a SAP solution provider.
6.11 Xiting
Xiting provides its XAMS (Xiting Authorizations Management Suite) as an add-on for managing authorizations in SAP environments. They are focused on managing roles and other authorizations, as well as analyzing ABAP code. Thus, they might be a lean option to many of the solutions covered more in-depth of this report, while being highly specialized on a subset of the capabilities analyzed.
Why worth watching: Good coverage of a range of specialized requirements in SAP environments, while not being as feature-rich as some of the other vendors.
7 Related Research
Executive View Report SAP Cloud Identity Access Governance
Executive View Report Soterion for SAP
Executive View Report SAP HANA Platform Security
Executive View Report SAP Data Custodian
Executive View Report SailPoint Access Risk Management
Executive View Report CSI tools
Executive View Report SAST Suite by akquinet
Leadership Compass Identity as a Service (IDaaS) IGA
Leadership Compass Identity Governance & Administration
Executive View Report Saviynt Security Manager for Enterprise IGA
Executive View Report Saviynt Enterprise Identity Cloud
8 Methodology
8.1 About KuppingerCole's Leadership Compass
KuppingerCole Leadership Compass is a tool which provides an overview of a particular IT market segment and identifies the leaders within that market segment. It is the compass which assists you in identifying the vendors and products/services in that market which you should consider for product decisions. It should be noted that it is inadequate to pick vendors based only on the information provided within this report.
Customers must always define their specific requirements and analyze in greater detail what they need. This report doesn’t provide any recommendations for picking a vendor for a specific customer scenario. This can be done only based on a more thorough and comprehensive analysis of customer requirements and a more detailed mapping of these requirements to product features, i.e. a complete assessment.
8.2 Types of Leadership
We look at four types of leaders:
- Product Leaders: Product Leaders identify the leading-edge products in the particular market. These products deliver most of the capabilities we expect from products in that market segment. They are mature.
- Market Leaders: Market Leaders are vendors which have a large, global customer base and a strong partner network to support their customers. A lack in global presence or breadth of partners can prevent a vendor from becoming a Market Leader.
- Innovation Leaders: Innovation Leaders are those vendors which are driving innovation in the market segment. They provide several of the most innovative and upcoming features we hope to see in the market segment.
- Overall Leaders: Overall Leaders are identified based on a combined rating, looking at the strength of products, the market presence, and the innovation of vendors. Overall Leaders might have slight weaknesses in some areas, but they become Overall Leaders by being above average in all areas.
For every area, we distinguish between three levels of products:
- Leaders: This identifies the Leaders as defined above. Leaders are products which are exceptionally strong in certain areas.
- Challengers: This level identifies products which are not yet Leaders but have specific strengths which might make them Leaders. Typically, these products are also mature and might be leading-edge when looking at specific use cases and customer requirements.
- Followers: This group contains vendors whose products lag in some areas, such as having a limited feature set or only a regional presence. The best of these products might have specific strengths, making them a good or even best choice for specific use cases and customer requirements but are of limited value in other situations.
Our rating is based on a broad range of input and long experience in that market segment. Input consists of experience from KuppingerCole advisory projects, feedback from customers using the products, product documentation, and a questionnaire sent out before creating the KuppingerCole Leadership Compass, and other sources.
8.3 Product Rating
KuppingerCole Analysts AG as an analyst company regularly evaluates products/services and vendors. The results are, among other types of publications and services, published in the KuppingerCole Leadership Compass Reports, KuppingerCole Executive Views, KuppingerCole Product Reports, and KuppingerCole Vendor Reports. KuppingerCole uses a standardized rating to provide a quick overview on our perception of the products or vendors. Providing a quick overview of the KuppingerCole rating of products requires an approach combining clarity, accuracy, and completeness of information at a glance.
KuppingerCole uses the following categories to rate products:
- Security
- Functionality
- Deployment
- Interoperability
- Usability
Security is primarily a measure of the degree of security within the product/service. This is a key requirement. We look for evidence of a well-defined approach to internal security as well as capabilities to enable its secure use by the customer, including authentication measures, access controls, and use of encryption. The rating includes our assessment of security vulnerabilities, the way the vendor deals with them, and some selected security features of the product/service.
Functionality is a measure of three factors: what the vendor promises to deliver, the state of the art and what KuppingerCole expects vendors to deliver to meet customer requirements. To score well there must be evidence that the product / service delivers on all of these.
Deployment is measured by how easy or difficult it is to deploy and operate the product or service. This considers the degree in which the vendor has integrated the relevant individual technologies or products. It also looks at what is needed to deploy, operate, manage, and discontinue the product / service.
Interoperability refers to the ability of the product / service to work with other vendors’ products, standards, or technologies. It considers the extent to which the product / service supports industry standards as well as widely deployed technologies. We also expect the product to support programmatic access through a well-documented and secure set of APIs.
Usability is a measure of how easy the product / service is to use and to administer. We look for user interfaces that are logically and intuitive as well as a high degree of consistency across user interfaces across the different products / services from the vendor.
We focus on security, functionality, ease of delivery, interoperability, and usability for the following key reasons:
- Increased People Participation: Human participation in systems at any level is the highest area of cost and the highest potential for failure of IT projects.
- Lack of excellence in Security, Functionality, Ease of Delivery, Interoperability, and Usability results in the need for increased human participation in the deployment and maintenance of IT services.
- Increased need for manual intervention and lack of Security, Functionality, Ease of Delivery, Interoperability, and Usability not only significantly increase costs, but inevitably lead to mistakes that can create opportunities for attack to succeed and services to fail.
KuppingerCole’s evaluation of products / services from a given vendor considers the degree of product Security, Functionality, Ease of Delivery, Interoperability, and Usability which to be of the highest importance. This is because lack of excellence in any of these areas can result in weak, costly and ineffective IT infrastructure.
8.4 Vendor Rating
We also rate vendors on the following characteristics
- Innovativeness
- Market position
- Financial strength
- Ecosystem
Innovativeness is measured as the capability to add technical capabilities in a direction which aligns with the KuppingerCole understanding of the market segment(s). Innovation has no value by itself but needs to provide clear benefits to the customer. However, being innovative is an important factor for trust in vendors, because innovative vendors are more likely to remain leading-edge. Vendors must support technical standardization initiatives. Driving innovation without standardization frequently leads to lock-in scenarios. Thus, active participation in standardization initiatives adds to the positive rating of innovativeness.
Market position measures the position the vendor has in the market or the relevant market segments. This is an average rating over all markets in which a vendor is active. Therefore, being weak in one segment doesn’t lead to a very low overall rating. This factor considers the vendor’s presence in major markets.
Financial strength even while KuppingerCole doesn’t consider size to be a value by itself, financial strength is an important factor for customers when making decisions. In general, publicly available financial information is an important factor therein. Companies which are venture-financed are in general more likely to either fold or become an acquisition target, which present risks to customers considering implementing their products.
Ecosystem is a measure of the support network vendors have in terms of resellers, system integrators, and knowledgeable consultants. It focuses mainly on the partner base of a vendor and the approach the vendor takes to act as a “good citizen” in heterogeneous IT environments.
Again, please note that in KuppingerCole Leadership Compass documents, most of these ratings apply to the specific product and market segment covered in the analysis, not to the overall rating of the vendor.
8.5 Rating Scale for Products and Vendors
For vendors and product feature areas, we use a separate rating with five different levels, beyond the Leadership rating in the various categories. These levels are
- Strong positive: Outstanding support for the subject area, e.g. product functionality, or outstanding position of the company for financial stability.
- Positive: Strong support for a feature area or strong position of the company, but with some minor gaps or shortcomings. Using Security as an example, this can indicate some gaps in fine-grained access controls of administrative entitlements. For market reach, it can indicate the global reach of a partner network, but a rather small number of partners.
- Neutral: Acceptable support for feature areas or acceptable position of the company, but with several requirements we set for these areas not being met. Using functionality as an example, this can indicate that some of the major feature areas we are looking for aren’t met, while others are well served. For Market Position, it could indicate a regional-only presence.
- Weak: Below-average capabilities in the product ratings or significant challenges in the company ratings, such as very small partner ecosystem.
- Critical: Major weaknesses in various areas. This rating most commonly applies to company ratings for market position or financial strength, indicating that vendors are very small and have a very low number of customers.
8.6 Inclusion and Exclusion of Vendors
KuppingerCole tries to include all vendors within a specific market segment in their Leadership Compass documents. The scope of the document is global coverage, including vendors which are only active in regional markets such as Germany, Russia, or the US.
However, there might be vendors which don’t appear in a Leadership Compass document due to various reasons:
- Limited market visibility: There might be vendors and products which are not on our radar yet, despite our continuous market research and work with advisory customers. This usually is a clear indicator of a lack in Market Leadership.
- Declined to participate: Vendors might decide to not participate in our evaluation and refuse to become part of the Leadership Compass document. KuppingerCole tends to include their products anyway if sufficient information for evaluation is available, thus providing a comprehensive overview of leaders in the market segment.
- Lack of information supply: Products of vendors which don’t provide the information we have requested for the Leadership Compass document will not appear in the document unless we have access to sufficient information from other sources.
- Borderline classification: Some products might have only small overlap with the market segment we are analyzing. In these cases, we might decide not to include the product in that KuppingerCole Leadership Compass.
The target is providing a comprehensive view of the products in a market segment. KuppingerCole will provide regular updates on their Leadership Compass documents.
We provide a quick overview about vendors not covered and their offerings in chapter Vendors and Market Segments to watch. In that chapter, we also look at some other interesting offerings around the market and in related market segments.
9 Copyright
© 2024 KuppingerCole Analysts AG all rights reserved. Reproduction and distribution of this publication in any form is forbidden unless prior written permission. All conclusions, recommendations and predictions in this document represent KuppingerCole's initial view. Through gathering more information and performing deep analysis, positions presented in this document will be subject to refinements or even major changes. KuppingerCole disclaims all warranties as to the completeness, accuracy and/or adequacy of this information. Even if KuppingerCole research documents may discuss legal issues related to information security and technology, KuppingerCole does not provide any legal services or advice and its publications shall not be used as such. KuppingerCole shall have no liability for errors or inadequacies in the information contained in this document. Any opinion expressed may be subject to change without notice. All product and company names are trademarks ™ or registered trademarks ® of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
KuppingerCole Analysts support IT professionals with outstanding expertise in defining IT strategies and in relevant decision-making processes. As a leading analyst company, KuppingerCole provides first-hand vendor-neutral information. Our services allow you to feel comfortable and secure in taking decisions essential to your business.
KuppingerCole Analysts AG, founded in 2004, is a global, independent analyst organization headquartered in Europe. We specialize in providing vendor-neutral advice, expertise, thought leadership, and practical relevance in Cybersecurity, Digital Identity & IAM (Identity and Access Management), Cloud Risk and Security, and Artificial Intelligence, as well as for all technologies fostering Digital Transformation. We support companies, corporate users, integrators and software manufacturers in meeting both tactical and strategic challenges and making better decisions for the success of their business. Maintaining a balance between immediate implementation and long-term viability is at the heart of our philosophy.
For further information, please contact clients@kuppingercole.com.










































